Almost Impossible to Detect Symbiote Linux Malware
The newly discovered Linux malware Symbiote can easily infect and hide in almost any process on compromised systems. The malware steals account credentials and gives malicious actors backdoor access.
Symbiote is stored in the system after injecting itself into all processes and cannot be detected with any signs of infection even during in-depth analysis.
Hides in Network Traffic
The most critical thing distinguishing Symbiote from other Linux malware is that it infects all processes instead of distributing a single executable file. Afterward, as the name suggests, it continues to exist as a symbiosis with transactions. Thus, it finds the opportunity to hide in network traffic and consumes all resources in the system like a parasite.
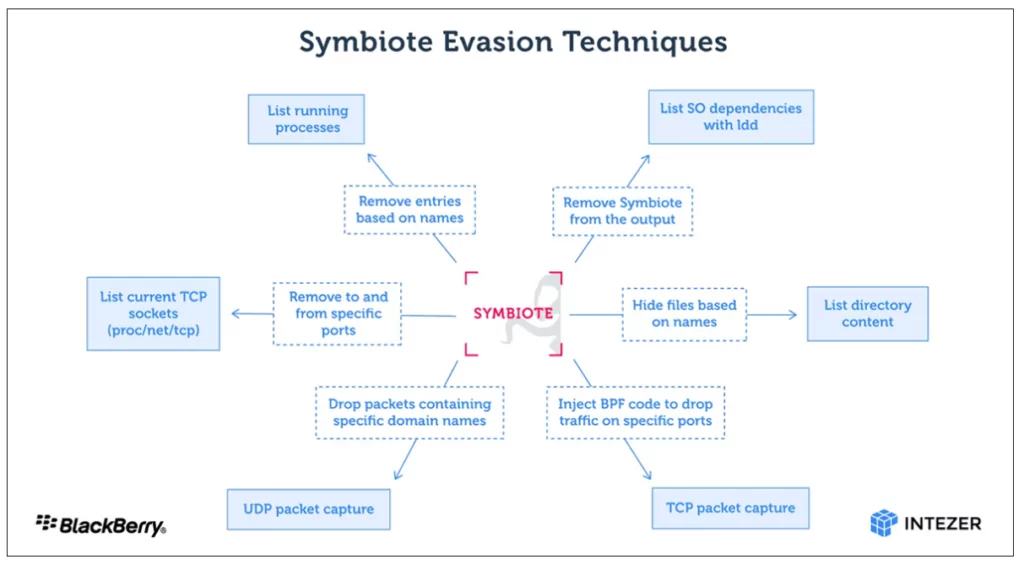
Symbiote comes as an SO (shared object), not an executable. It also uses Linux’s LD_PRELOAD (T1574.006) feature to take precedence over other shared objects while participating in other processes. Then it hides itself by changing the libc and libpcap functions. After Symbiote completes infecting all processes, it provides rootkit functionality, credential collection, and remote access capabilities.
Symbiote Hides Its Activity Using BPF
Symbiote malware infects the system and makes it almost impossible to detect itself and other malware used by the threat actor. It hides all files, programs, and network evidence, so forensics on infected devices are inconclusive.
The malware, which uses BPF (Berkeley Packet Filter) to hide network activity, is similar to the BPFdoor malware detected last month and has turned out to target Linux systems for five years.
Research made by BlackBerry and Intezer Labs indicates that a BPF bytecode is injected into the Kernel when the malware initiates a process that identifies which packets should be collected on the infected device. This filters out network traffic that packet capture software should not see.
Symbiote primarily targets the financial sector in Latin America, Brazilian banks, and federal police.
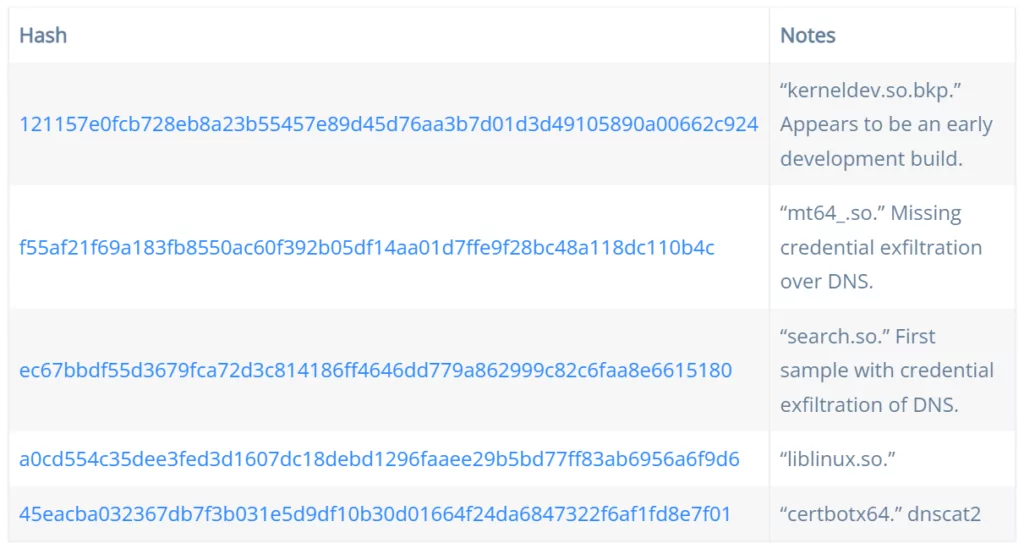
Symbiote IoCs
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.