
All You Need to Know About Endpoint Security
Endpoint Security products are responsible for a market size of approximately 14 million in 2021. Regarding this market’s compound annual growth rate (CAGR), it is estimated that the market will double in 9 years. According to the same Fortune Business report, which expresses the information above, the Covid pandemic and some popular policies like BYOD (bring your own device) are key factors that cause significant escalations in the market.
What Is Endpoint Security?
Endpoint Security systems aim to protect a network by securing the possible entry points on the attack surface (endpoints). These endpoints are devices that are connected to the target network. Endpoints can be any connected device, such as personal laptops and cellphones. Therefore, all the endpoints must be covered to ensure network safety.
The term endpoint can cover many devices, such as
- Personal devices
- Servers
- Cloud-based – servers
- Smart systems and devices that are connected to the internet
- IoT Devices
Unlike most of the former security tools, Endpoint Security is a cloud-based security system. Therefore, Endpoint Security applications require less CPU, are always up to date for recently emerged threats, and protect a larger number of devices.
Aside from monitoring a broad aspect of devices, Endpoint Security Systems also has additional advantages. Being a cloud-based system allows Endpoint Security systems to back up and encrypt the data in the network. Therefore, data loss and misuse of stolen data can be prevented. Also, reaching all endpoints remotely enables security administrators to react to all endpoints as long as they are connected to the internet.
How Does it Work?
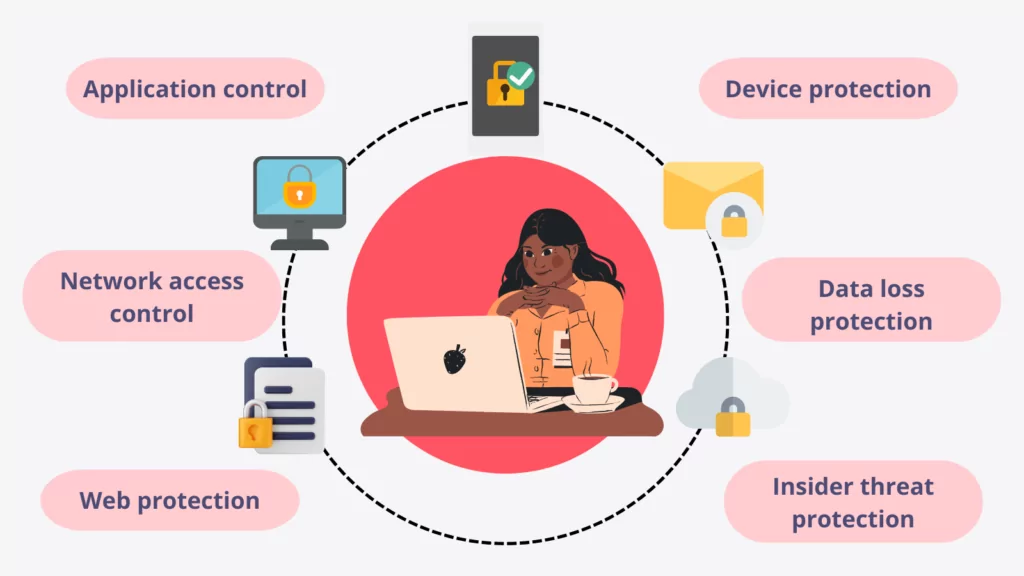
Like conventional security systems, Endpoint Security monitors all endpoints’ attack surfaces for detecting malware and threats to block further spread in the target network. It ensures the network’s safety by focusing on incoming data from the endpoints. Each file entered the network by the endpoint devices is analyzed. Also, these systems provide a control panel where security admins can monitor and react to each endpoint device. The panel allows administrators to isolate or wipe data remotely.
As a security system, it also constrains user activity and enables critical actions only with administrators’ permission. Owing to controlling security for all endpoint devices, which computers are only one part of them, they have a significant advantage over traditional security solutions.
As a modern and cloud-based application, Endpoint Security systems have advantages over conventional systems. Those are,
- Easy to set up on the target devices and apply on larger scales
- Requires less CPU power
- Automatically updates itself against the latest threats or malware
- Can back up and encrypt critical data (files, e-mail, devices)
- Zero-day threats can be detected by machine learning tools
- Additional firewall to ensure network’s safety even if one of the endpoint devices is breached
- E-mail gateway services
- Safe browsing
Why Has it Become Important?
For the last couple of years, many organizations have switched workstation preferences from desktops to laptops, leading to increased working from home. Furthermore, the integration of wearable smart devices and IoT increased the usage of cellphones, and new policies like BYOD caused an exponential increase in the endpoint devices connected to organizational networks. In a network that only protects its servers and computers by conventional systems, serious vulnerabilities allow hackers to exploit what can be located in these additional endpoint devices, especially when they are not protected.
Since they knew about this situation, threat actors have shifted their focus to endpoint devices that conventional security systems do not cover. This powerful shift to a new threat landscape where the attack surface is much more significant than before caused SOC teams to re-evaluate their needs. Endpoint Security systems are born to answer today’s landscape where threats can come from any device connected to the web.
Differences between Endpoint Security Systems Compare to Antivirus & Consumer Endpoint Security
To explain Endpoint Security systems elaborately, one must consider the differences between consumer (individual) and enterprise (organizational) versions. Also, former conventional security systems such as antivirus are another important benchmark. Below, there is a table that compares all three options:

Types of Endpoint Security
As a security tool, endpoint security systems can be found with many different options from different security organizations. The changing threat landscape may cause many modifications to Endpoint Security systems. Today it can be divided into three groups by looking at the services they provide
- Endpoint Protection Platform (EPP): EPP products are essential tools to secure endpoints. The product scans the files as soon as they get into the network. In that way, conventional antivirus solutions may be considered an EPP product for the device they set up. Yet, EPP does not provide any continuous monitoring to endpoint devices.
- Endpoint detection and Remediation (EDR): As an upgraded version of EPP, EDR products provide continuous monitoring and response actions. Therefore, EDR can detect harmful files and applications after they enter the network so that the breaches can be investigated conveniently. Also, EDR is not only limited to signature-based protection, but also it can detect polymorphic attacks, fileless malware, and ransomware.
- Extended Detection and Response (XDR): Like EDR, XDR is an upgraded version of its predecessor, EDR. As a next-generation security solution, XDR products provide extended protection by providing extra tools. XDR solutions can detect a broader range of threats. Also, XDR has extended capabilities to detect and respond to threats using machine learning and behavioral analytics, making it easier to maintain a safer network and eliminate internal vulnerabilities.
Endpoint Security systems are born to answer today’s threat landscape. The increasing usage of smart devices and recent technologies like IoT have made many networks vulnerable. Most of these additional devices have security weaknesses that can be exploited. As a cutting-edge security system, they are used to secure a huge number of endpoints against suspicious and harmful activity.



































