ESXiArgs Ransomware Attack Targets VMware Servers Worldwide
[February 9, 2023] Update: Ransomware is updated to prevent recovery solutions. Added the subheading “New Version of ESXiArgs Ransomware Prevents Recovery.”
The vulnerability, tracked as CVE-2021-21974, is caused by a stack overflow issue in the OpenSLP service that unauthenticated threat actors in low-complexity attacks can exploit.
According to available research, CERT-FR claims that this attack exploits the CVE-2021-21974 vulnerability that has been present since February 23, 2021.
Currently, targeted systems are considered version 6. x and ESXi hypervisor version before 6.7.
Vulnerable Systems
Systems affected by the CVE-2021-21974 vulnerability:
- ESXi versions 7.x prior to ESXi70U1c-17325551
- ESXi versions 6.7.x prior to ESXi670-202102401-SG
- ESXi versions 6.5.x prior to ESXi650-202102101-SG
New ESXiArgs Ransomware
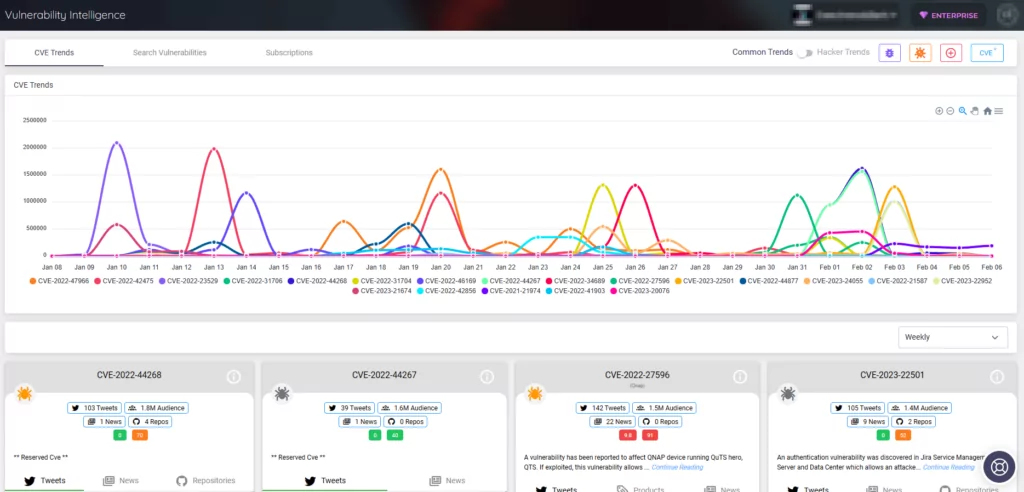
At least 120 VMware ESXi servers worldwide vulnerable to CVE-2021-21974 have already been compromised in this ransomware campaign, according to a Shodan search.
The origin of the attacks is believed to be from a new ransomware group based on the analysis of the ransom notes seen in the attacks.
OVHcloud, a French cloud provider, has also released a report connecting the large-scale attacks on VMware ESXi servers with the Nevada ransomware operation. The investigation is ongoing to confirm these assumptions.
The primary target of the attack is VMware ESXi servers before version 7.0 U3i, which are being compromised through the OpenSLP port (427).
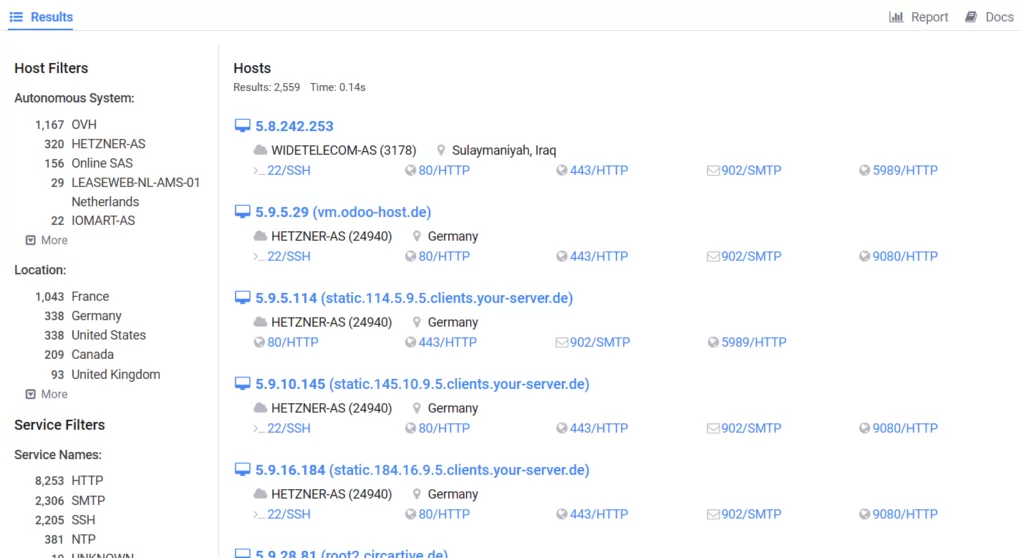
A Censys search reveals that around 2,500 VMware ESXi servers globally have been affected by the ESXiArgs ransomware campaign.
About the Ransomware
Ransomware infects ESXi servers and encrypts files with extensions such as .vmxf, .vmx, .vmdk, .vmsd, and .nvram. For each encrypted file, the ransomware creates a .args file that contains metadata necessary for decryption.
The attackers claim to have stolen data, but one victim reported otherwise. The victim found no evidence of data theft as the infected machine had low daily usage, and no outbound data transfer was seen in the last 90 days.
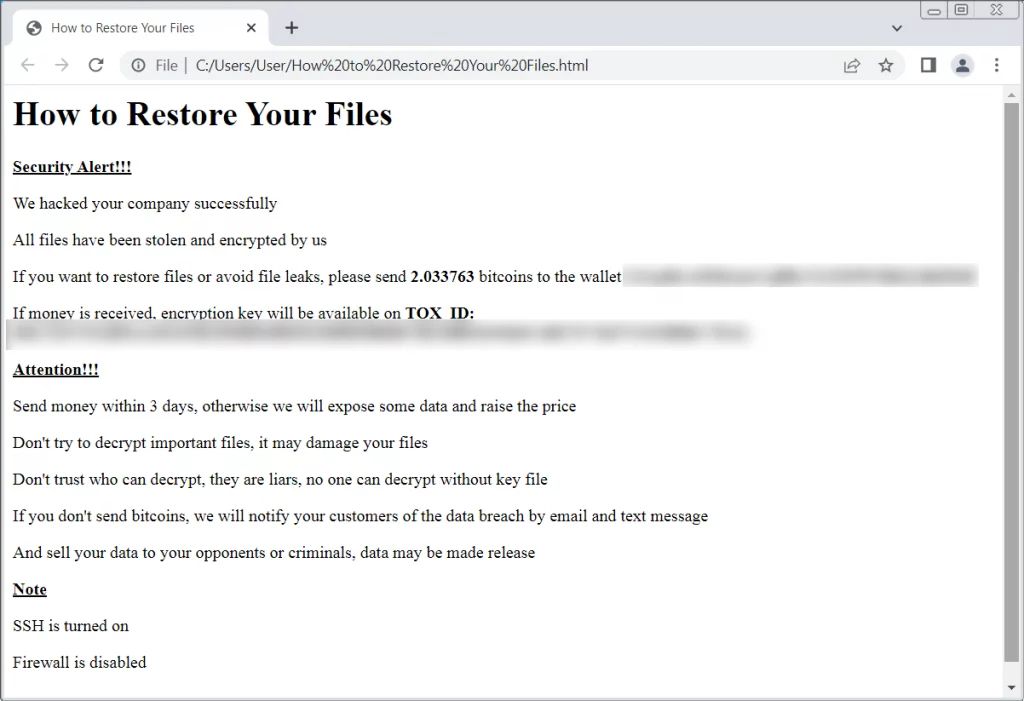
Ransom notes named “ransom.html” and “How to Restore Your Files.html” were discovered on affected systems. Others claimed that the notes they took were plaintext files.
Security researcher Michael Gillespie confirmed that the encryption is secure and cannot be easily decrypted. The encryptor uses the Sosemanuk algorithm, which is uncommon in ransomware and was modified to use RSA instead of Babuk’sCurve25519 implementation.
Attack Explanation
The encryptor is launched using a shell script file, and command line arguments and the ransomware attacks on ESXi virtual machines use the following steps:
- The script runs a command to change the strings “.vmdk” and “.vswp” in the virtual machine’s configuration files (.vmx) to “1.vmdk” and “1.vswp“. It then force-terminates all processes that contain the string “vmx” in order to terminate all running virtual machines.
- The command below is run to obtain a list of ESXi volumes:
- esxcli storage filesystem list | grep “/vmfs/volumes/” | awk -F’ ‘ ‘{print $2}’
- The script will create a [file name].args file in the same folder for each found file with target extensions, which contains the computed size step, ‘1’, and the file size. The script will then use the “encrypt” executable to encrypt the files based on the computed parameters.
- Following encryption, the script will replace the ransom notes in the ESXi index.html file and the server’s motd file.
- Lastly, the script removes a backdoor installed in /store/packages/vmtools.py and deletes various lines from the following files:
- /var/spool/cron/crontabs/root
- /bin/hostd-probe.sh
- /etc/vmware/rhttpproxy/endpoints.conf
- /etc/rc.local.d/local.sh
ESXi Virtual Machines Become Common Target
Because virtual machines provide improved device and resource management, many organizations are migrating to them. Ransomware actors are aware of the transition and are shifting their focus to ESXi virtual machines. After deploying their payloads on ESXi hosts, the ransomware operators encrypt multiple servers with a single command.
Royal Ransomware, as well as other ransomware operations, have been discovered targeting VMware ESXi servers running on Linux; Royal Ransomware has recently added support for these attacks in new variants.
The new Royal Ransomware variant is command line-based and includes several features. It can stop virtual machines before beginning encryption and can specify virtual machines as a target. The ransomware will attach the .royal_u extension to the encrypted files.
New Version of ESXiArgs Ransomware Prevents Recovery
The attack affected over 3,000 VMware ESXi servers connected to the internet. Threat actors hacked devices through vulnerabilities in VMware SLP, but some victims have reported that their devices were breached even though SLP was disabled.
In a new version, the encrypt.sh script’s size_step routine is removed and set to 1, so the ESXiArgs ransomware attacks can encrypt more data and make recovering much more difficult.
We detailed the recovery phase and availability of a decryptor on another blog.
The encrypt.sh script, which searches for target file types, would also examine the file size of each discovered file. If the file size were smaller than 128MB, it would encrypt the file in 1MB increments; if the file size were greater than 128MB, it would compute a size step to alternate between encrypting 1 MB of data and not encrypting chunks.
Changing it to 1 causes the encryptor to encrypt 1MB of data and then skip another 1MB each time, resulting in half of all files larger than 128MB being encrypted. This will also result in previous recovery tools being unable to recover machines because the flat files used for recovery will be encrypted too.
Additionally, the latest wave of the attack made a small alteration to the ransom message. It no longer contains the bitcoin addresses. Attackers probably did this because security researchers had started gathering these addresses to monitor the ransom payments.
Although it is suggested to restore encrypted ESXi servers using the recovery script provided by CISA, it will probably be ineffective if your system was infected during the second wave of attacks that employed the latest encryption method.
Recommendations
To prevent such attacks, system administrators must disable the Service Location Protocol (SLP) service on vulnerable ESXi hypervisor products that are not yet updated.
CERT-FR strongly recommends applying the update as soon as possible. It also reports that systems that have not been updated require scanning to find signs of breaches.
All administrators should ensure that vmtools.py is removed, as its cleanup is very similar to a customized Python backdoor for the ESXi server discovered by Juniper in December 2022.
SOCRadar is a useful threat intelligence tool for staying up to date on current threats and vulnerabilities. It continuously scans your online defenses from a hacker’s perspective in order to identify serious, exploitable vulnerabilities. Using the Vulnerability Intelligence feature, you can easily search and access comprehensive information about vulnerabilities, allowing you to effectively address and prioritize necessary fixes.