
Zimbra Zero-Day Vulnerability Actively Exploited, Apply the Fix Now
[Update] November 17, 2023: See the subheading: “Google Reports Four Campaigns Exploiting the Zimbra Zero-Day: CVE-2023-37580.”
Zimbra is urging its customers to manually apply fixes for a recently discovered zero-day vulnerability. This vulnerability, which does not yet have a CVE identifier, is actively exploited to compromise Zimbra Collaboration Suite (ZCS) email servers.
Zimbra Collaboration Suite is a widely used open-source email and collaboration platform with a user base of 200,000 businesses across 140 countries.
Critical Zero-Day Vulnerability in Zimbra Collaboration Suite Raises Data Security Concerns
According to Zimbra’s advisory, the zero-day vulnerability impacts Zimbra Collaboration Suite version 8.8.15 and poses potential risks to the confidentiality and integrity of organizations’ data. While Zimbra planned to roll out the fix in the July patch release, the advisory fails to mention that threat actors currently exploit the vulnerability in real-world attacks.
What Is the Zero-Day Vulnerability in Zimbra Collaboration Suite (ZCS)?
Clément Lecigne, a security researcher from Google Threat Analysis Group (TAG), discovered and reported this vulnerability as a reflected Cross-Site Scripting (XSS) issue. In XSS attacks, malicious actors can steal sensitive user information or execute malicious code on vulnerable systems.
Although Zimbra has not disclosed any information regarding the exploitation of this vulnerability, Maddie Stone from Google TAG revealed that they discovered the vulnerability while it was being actively exploited in the wild.
Manual Mitigation Steps for Zimbra’s Zero-Day Vulnerability
Zimbra has provided a fix that administrators can manually apply to eliminate the attack vector until the patch is released. “To ensure the highest level of security, we kindly request your cooperation in manually applying the fix to all of your mailbox nodes,” stated the company.
To mitigate the vulnerability manually, administrators need to follow these steps:
- Create a backup of the file /opt/zimbra/jetty/webapps/zimbra/m/momoveto.
- Edit the file and navigate to line number 40.
- Update the parameter value to:
name=”st” type=”hidden” value=”${fn:escapeXml(param.st)}”/>
- Prior to the update, the line appeared as:
name=”st” type=”hidden” value=”${param.st}”/>
By including the escapeXml() function, user-inputted data is now sanitized by escaping special characters used in XML markup to prevent XSS vulnerabilities.
The fix can be implemented without causing any downtime since a Zimbra service restart is not required.
Recent Zimbra Breaches
Given that numerous Zimbra vulnerabilities have been exploited to breach vulnerable email servers worldwide in recent years, administrators should prioritize mitigating this zero-day vulnerability.
For example, in June 2022, Zimbra’s authentication bypass and remote code execution vulnerabilities were exploited to compromise over 1,000 servers.
Since February 2023, the Winter Vivern Russian hacking group has been using exploits targeting another reflected XSS bug to breach webmail portals belonging to NATO-aligned governments. They have been stealing email mailboxes of officials, governments, military personnel, and diplomats.
Also, starting in September 2022, hackers exploited an unpatched remote code execution vulnerability, CVE-2022-41352, in Zimbra Collaboration Suite, compromising nearly 900 vulnerable servers within two months.
Google Reports Four Campaigns Exploiting the Zimbra Zero-Day: CVE-2023-37580
Google has discovered four different campaigns exploiting the vulnerability in Zimbra Collaboration Suite. The vulnerability has since been patched, and assigned a CVE identifier: CVE-2023-37580.
Threat groups exploited CVE-2023-37580 to steal email data, user credentials, and authentication tokens. Exploitation was mostly observed after a hotfix was disclosed on Github on July 5, 2023, underscoring the urgency for organizations to swiftly apply fixes.
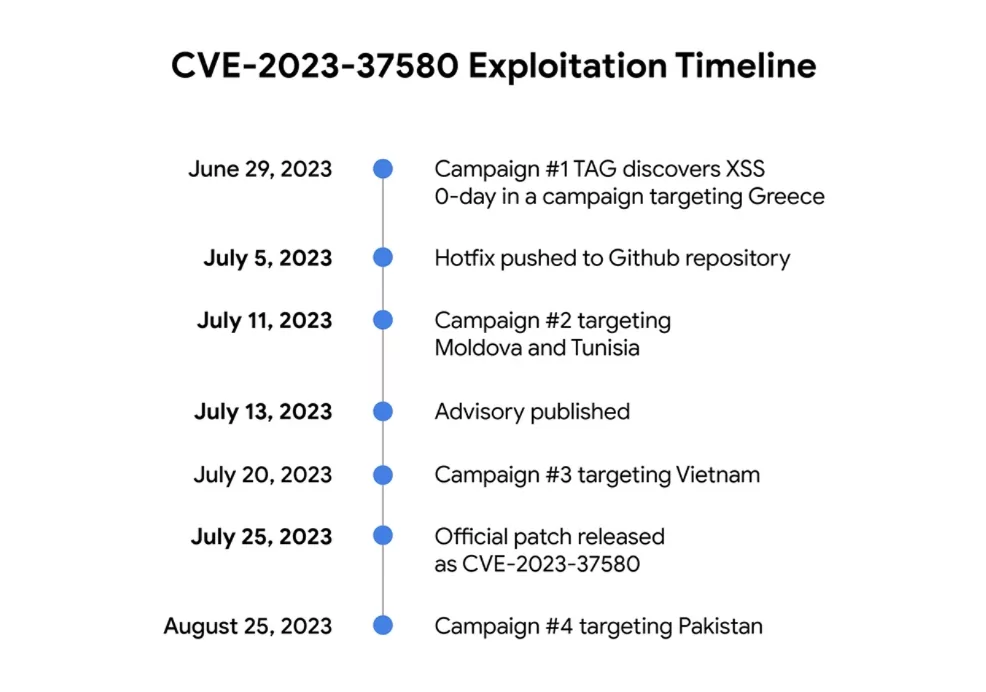
Google has provided descriptions for the four campaigns, outlined as follows:
- Campaign 1: The initial exploitation targeted a government organization in Greece, utilizing an email-stealing framework. Attackers sent emails with exploit URLs, triggering the loading of a known framework that uses XSS to steal information during a Zimbra session. This framework stole mail data and set up auto-forwarding to an attacker-controlled email address.
- Campaign 2: Following the patch’s initial release on Github, another actor exploited the vulnerability for two weeks before the official fix was available. Targeting government organizations in Moldova and Tunisia, the actor utilized exploit URLs containing unique official email addresses. This activity was attributed to Winter Vivern APT group (UNC4907), known for exploiting XSS in Zimbra and Roundcube.
- Campaign 3: A third, unidentified group exploited the vulnerability days before Zimbra’s official patch release, engaging in a credential phishing campaign against a government organization in Vietnam. The exploit URL directed targets to a phishing page for webmail credentials, with stolen data posted to a compromised government domain.
- Campaign 4: In August 2023, post-patch release, a fourth campaign targeted a government organization in Pakistan. This campaign aimed to steal Zimbra authentication tokens, with the exfiltration of tokens to ntcpk[.]org.
For additional details and Indicators of Compromise (IOCs), refer to Google’s blog.
Strengthen Your Security with SOCRadar’s Attack Surface Management and Vulnerability Intelligence
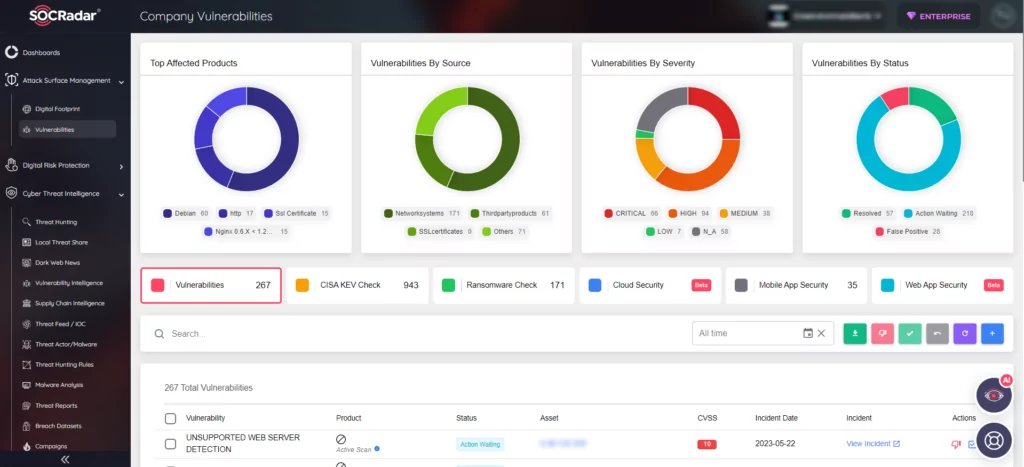
In the realm of security research, the discovery of vulnerabilities plays a crucial role in safeguarding applications and data. SOCRadar’s Extended Attack Surface Management (ASM) actively identifies vulnerabilities across your organization’s digital assets and promptly alerts you, empowering you to take swift action in response. You can see security alerts in the platform’s Company Vulnerabilities tab.
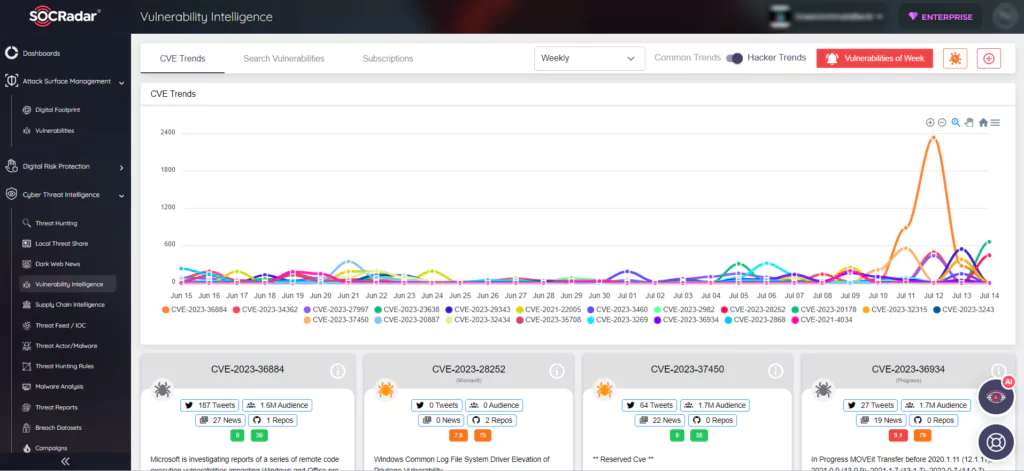
Moreover, SOCRadar’s Vulnerability Intelligence provides in-depth information on vulnerabilities, ensuring you stay informed about the latest exploitation trends. By gaining visibility into your company’s vulnerabilities, you can prioritize patches, effectively bolstering your organization’s overall security posture.
Sign up now for a free edition of the SOCRadar platform to gain more knowledge and stay up to date on the newest vulnerabilities.



































