
Attackers Actively Exploit Vulnerabilities in Unpatched Products: Zimbra, IBM Aspera Faspex, Cacti, Realtek
Threat actors are actively exploiting security vulnerabilities in Zimbra, IBM Aspera Faspex, Cacti, and Realtek products. Respective vendors have previously fixed the vulnerabilities used in attacks and have varying CVSS scores between 6.1 and 9.8.
Winter Vivern Phishing Campaign Targets European Governments via Zimbra Vulnerability
A group of Russian cyber attackers, Winter Vivern, has launched a new phishing campaign to hack the emails of government agencies in various European countries. They are exploiting a vulnerability in the Zimbra Collaboration software, a business email and collaboration platform.
Winter Vivern sends phishing emails pretending to be employees of the target organization or their parent company with political affiliations to the government.
These emails are sent from compromised domains or vulnerable WordPress websites and include a link to a resource on the target organization’s official website. The link is spoofed to lead the recipient to install a payload from an attacker domain.
Attackers now use this technique conjoint with a vulnerability found in Zimbra. The vulnerability is tracked as CVE-2022-27926. It allows cross-site scripting (XSS) and has a CVSS score of 6.1.
Zimbra fixed CVE-2022-27926 in Zimbra 9.0.0 Patch 24, released in March 2022. Still, researchers warn that the Winter Vivern group exploits the vulnerability on unpatched Zimbra instances by creating links with appended code to execute malicious JavaScript code inside the browser. The malicious JavaScript payload helps attackers to steal and exfiltrate usernames, passwords, and active anti-CSRF tokens from cookies. After acquiring login credentials and tokens, it hijacks the email gateway using hardcoded URLs.
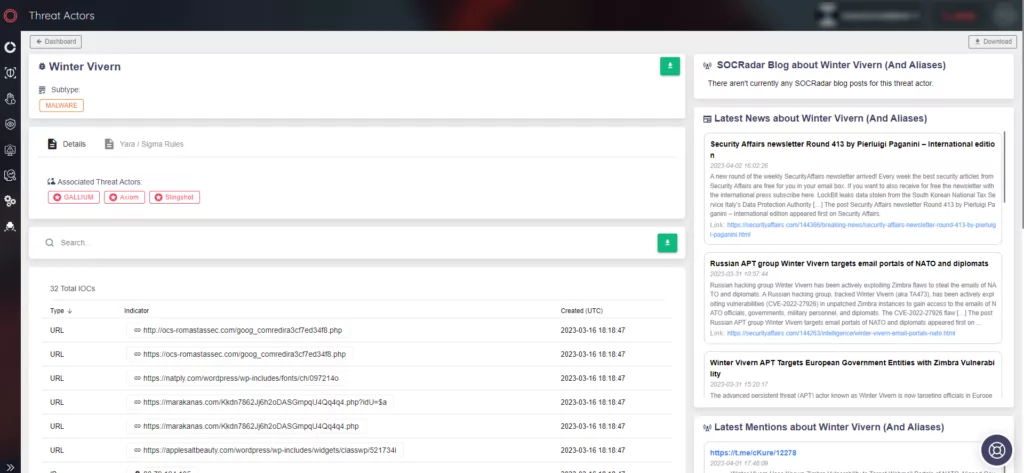
About Winter Vivern
Winter Vivern threat actor group is also known as TA473 and UAC-0114. Although it is not confirmed which nation-state is backing this APT group, security experts believe that their activities are in line with the interests of Russia and Belarus.
You can find out more about the threat actor on SOCRadar. The Threat Actor Tracking tab features details on threat actors, such as indicators of compromise (IoCs), latest activities, and mentions.
IBM Aspera Faspex Vulnerability Exploited in Ransomware Campaigns
A critical vulnerability in IBM’s Aspera Faspex file exchange app, CVE-2022-47986 (CVSS score: 9.8), has been actively exploited by cybercriminals in ransomware campaigns associated with Buhti and IceFire since February.
The bug, patched in December 2022, has been used in attacks shortly after the release of the proof-of-concept (PoC) exploit.
Rapid7 revealed that one of its customers was compromised by the security flaw and recommended taking the service offline if a patch cannot be installed immediately because the vulnerability is typically an internet-facing service.
Attackers Exploit Realtek Jungle SDK Vulnerability to Distribute MooBot
CVE-2021-35394 (CVSS score: 9.8) is a critical arbitrary command injection vulnerability fixed in 2021, affecting the Realtek Jungle SDK.
The CVE-2021-35394 vulnerability has been exploited to distribute several botnets in the past, including Mirai, Gafgyt, Mozi, and RedGoBot.
The attackers are now exploiting the vulnerability to deploy MooBot, which is a Mirai botnet variant that emerged in 2019. The Realtek Jungle SDK vulnerability has been targeted in large-scale attacks to disrupt supply chains and has received over 134 million exploit attempts so far.
Critical Vulnerability in Cacti Servers Exploited in ShellBot and MooBot Attacks
A critical authentication bypass and command injection vulnerability in Cacti servers, identified as CVE-2022-46169, allows unauthenticated attackers to execute arbitrary code.
Since January 2023, CVE-2022-46169 has been exploited in ShellBot (PerlBot) attacks as well as MooBot attacks.
Researchers discovered three versions of ShellBot, all of which can be used in distributed denial-of-service (DDoS) attacks. These versions are PowerBots (C) GohacK, and B0tchZ 0.2a, LiGhT’s Modded Perlbot v2. The first two versions also provide the backdoor capability.
Keep Your Business Secure: Monitor Vulnerability Trends with SOCRadar
To protect your business from attackers who actively exploit vulnerabilities in unpatched products, it’s essential to closely monitor vulnerability trends and stay alert to new critical vulnerabilities or exploits associated with your digital footprint.
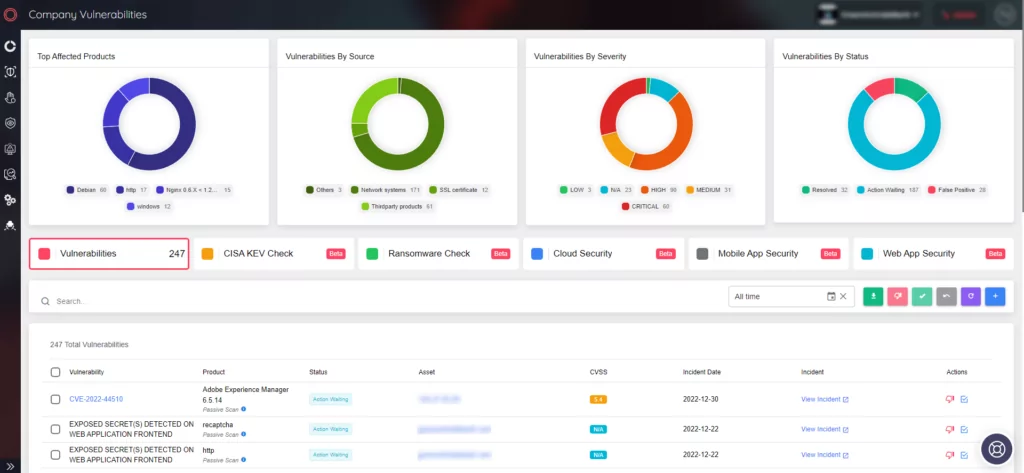
With SOCRadar, you can quickly identify potential vulnerabilities and take action to prevent disruption to your business. You can speed up the assessment and verification processes and prevent disruptive attacks by getting actionable insights and context on potentially vulnerable technologies.



































