Zero-Day Vulnerabilities in Exim Email Server: Risk of RCE (CVE-2023-42115, CVE-2023-42116, CVE-2023-42117, and More)
Zero Day Initiative disclosed a total of six zero-day vulnerabilities in the Exim Internet Mailer, which potentially make thousands of email servers worldwide vulnerable to exploitation.
Exim, a widely used free mail transfer agent (MTA) software on Unix-like operating systems, currently boasts over 342,000 servers worldwide, according to the latest survey.
Exim has previously fallen victim to many attacks due to vulnerabilities. In 2020, researchers revealed that Russian GRU threat actors, “Sandworm Team,” had actively exploited a vulnerability (CVE-2019-10149) in Exim since 2019 to compromise US government networks. Also, in August 2022, researchers reported two critical vulnerabilities in Exim, complete with Proof-of-Concept (PoC) exploits.
It is highly likely that threat actors will also attempt to exploit these recent Exim vulnerabilities.
What Are the Vulnerabilities in Exim About?
The vulnerabilities’ severity scores range from 3.1 to a critical 9.8. Significantly, some of these vulnerabilities even permit remote code execution, while all of them are exploitable without authentication.
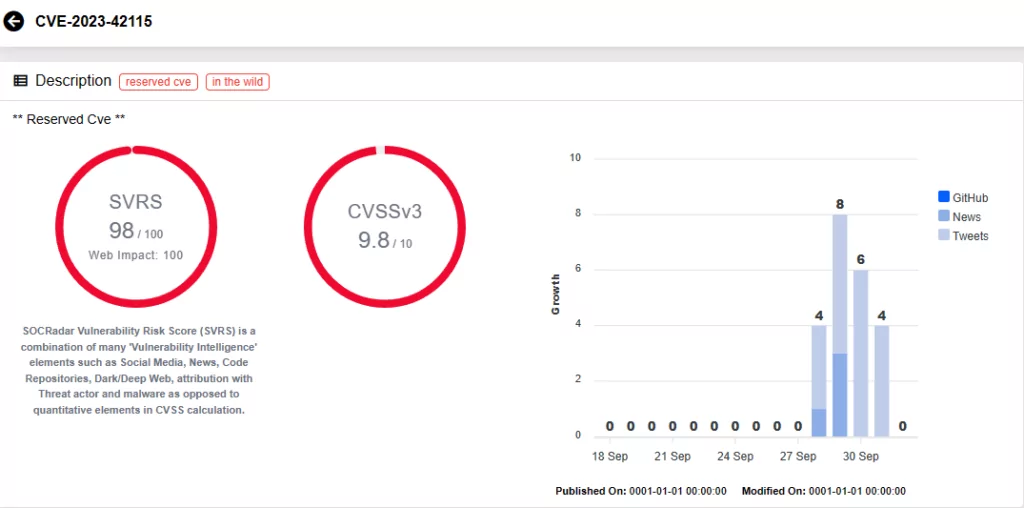
CVE-2023-42115 (CVSS score: 9.8, Critical): The vulnerability resides within the SMTP service, and arises due to lack of proper validation of user-supplied data, which may ensue a write past the end of a buffer. Exploiting this vulnerability can enable a remote attacker to execute arbitrary code within the service account’s context.
CVE-2023-42116 (CVSS score: 8.1, High): It is a stack-based overflow vulnerability within the Exim SMTP challenge component. It is caused by a lack of proper validation of user-supplied data length before copying it into a fixed-length stack-based buffer when handling NTLM challenge requests. An attacker can exploit this vulnerability to execute code within the context of the service account.
CVE-2023-42117 (CVSS score: 8.1, High): This vulnerability stems from the lack of proper validation for user-supplied data in the SMTP service, potentially leading to a memory corruption. An attacker can exploit this vulnerability to execute code within the current process’s context.
CVE-2023-42118 (CVSS score: 7.5, High): Due to the vulnerability, user-supplied data is not properly validated during the parsing process of SPF macros, and it can lead to an integer underflow before writing to memory. An attacker can exploit this vulnerability to execute code within the service account’s context.
CVE-2023-42114 (CVSS score: 3.7, Low): A vulnerability in the handling of NTLM challenge requests, arising from the lack of validation of user-supplied data. It can allow to read beyond allocated data structures, potentially enabling an attacker to disclose information within the service account’s context.
CVE-2023-42119 (CVSS score: 3.1, Low): Another vulnerability in the SMTP service, due to lack of proper validation of user-supplied data. It can allow to read past the end of an allocated buffer. An attacker can potentially combine CVE-2023-42119 with other vulnerabilities to execute arbitrary code within the service account’s context.
Are Fixes Available?
On September 29, 2023, Heiko Schlittermann, a member of the Exim project team, stated that fixes for three of the vulnerabilities (CVE-2023-42114, CVE-2023-42115, and CVE-2023-42116) are now accessible in a secured repository, ready for distribution maintainers to implement.
Schlittermann explained that following a contact from ZDI in June 2022, team members had requested details but had not received answers they could work with, he then further added:
“Next contact with ZDI was in May 2023. Right after this contact we created project bug tracker for 3 of the 6 issues. 2 high scored of them are fixed (OOB access). A minor scored (info leak) is fixed too. Fixes are available in a protected repository and are ready to be applied by the distribution maintainers. The remaining issues are debatable or miss information we need to fix them.”
The remaining fixes for these vulnerabilities are scheduled for release today, on October 2, 2023. In the meantime, ZDI recommended mitigations that include refraining from using vulnerable components or configurations when utilizing Exim.
How Can SOCRadar Help?
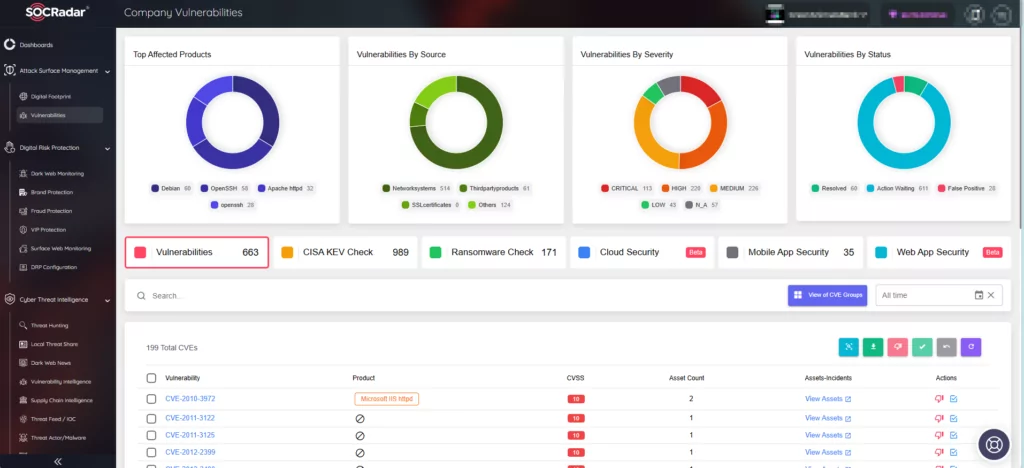
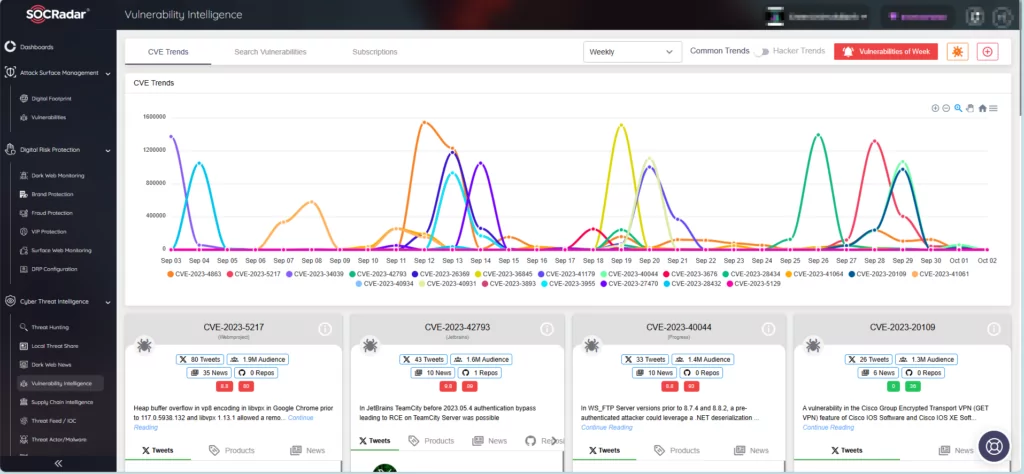
SOCRadar serves as an efficient threat intelligence platform that aids organizations in keeping abreast of the most recent vulnerabilities and risks. Through its Vulnerability Intelligence module, users can effortlessly locate and access comprehensive data on all documented vulnerabilities, simplifying the task of prioritizing actions and patch management.
Furthermore, SOCRadar’s Attack Surface Management (ASM) module empowers users to uncover their digital assets and receive notifications about emerging concerns. The platform utilizes alerts to promptly notify potential threats to your organization, allowing you to take precautions to avert any potential harm.