Weekly Vulnerability Summary by CISA: Apache, Google Chrome, PrestaShop, WordPress, ZyXEL
The Cybersecurity and Infrastructure Security Agency (CISA) has once again issued a summary of the latest vulnerabilities. The latest CISA vulnerability summary lists vulnerabilities identified between November 24 and December 2, 2023.
In this blog post, we outline the critical and high-severity vulnerabilities included in the CISA vulnerability summary, that have the potential to impact organizations’ digital resilience. As we delve into this weekly roundup, we aim to spotlight the most pressing threats that demand immediate attention and proactive mitigation efforts.
Exploring the Latest Critical and High-Severity Vulnerabilities
Diverse products are currently grappling with a range of critical and high-severity vulnerabilities. In this overview of the weekly CISA vulnerability summary, we will delve into instances such as Apache Superset, facing an improper authorization flaw, Google Chrome encountering multiple vulnerabilities, PrestaShop dealing with SQL injection risks, critical vulnerabilities in WordPress plugins, and ZyXEL NAS firmware showcasing numerous security concerns.
Additionally, other organizations including Arcserve, ArslanSoft, Chamilo, Foxit Software, Layer5, Owncast, SourceCodester, Tenda, and Sapplica, as well as the Moses machine translation system and Univera computer system were also affected by significant vulnerabilities, and listed in CISA’s vulnerability summary.
Apache:
Apache Superset, an open-source software for handling big data, is vulnerable to an improper authorization check and possible privilege escalation.
The security vulnerability affects versions up to but excluding 2.1.2:
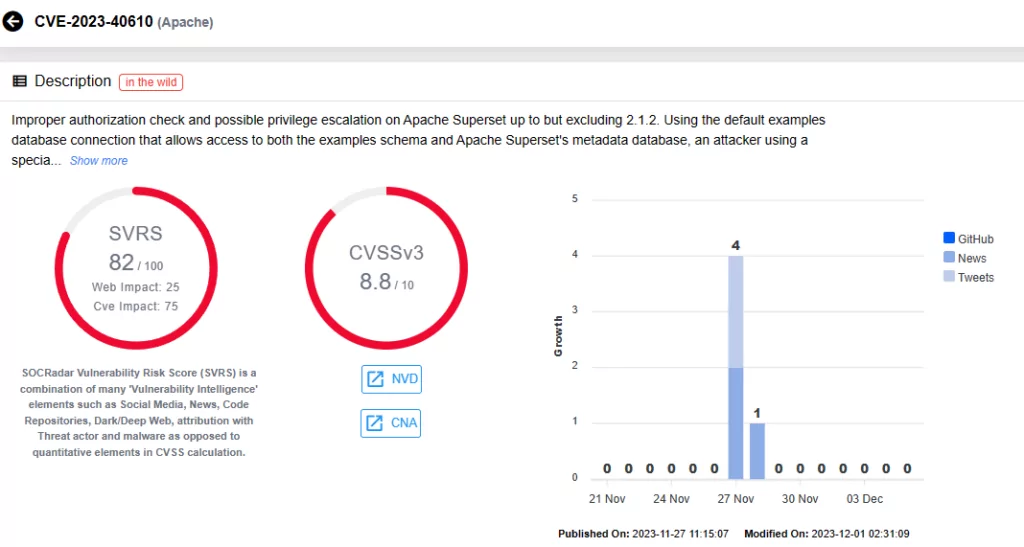
- CVE-2023-40610 (CVSS Score: 8.8): Exploiting the default example database connection, an attacker using a specially crafted CTE SQL statement could manipulate data on the metadata database, potentially tampering with authentication/authorization data.
Google Chrome:
Several vulnerabilities were identified in Google Chrome version 119.0.6045.199:
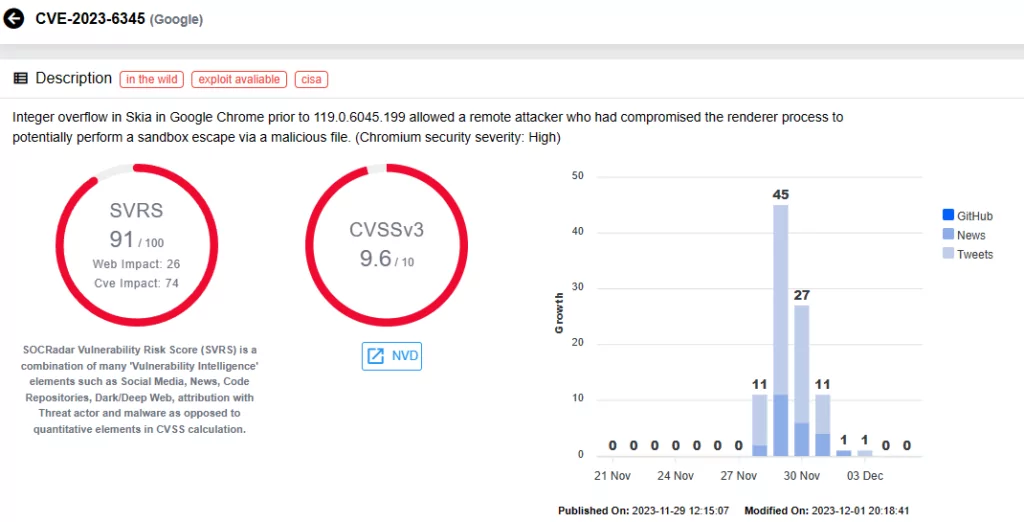
- CVE-2023-6345 (CVSS Score: 9.6): An integer overflow vulnerability in Skia may allow a remote attacker, compromising the renderer process, to execute a potential sandbox escape through a malicious file.
- CVE-2023-6346 (CVSS Score: 8.8): A use-after-free vulnerability in WebAudio could be exploited by a remote attacker via a crafted HTML page, potentially leading to heap corruption.
- CVE-2023-6347 (CVSS Score: 8.8): Another use-after-free vulnerability, this time in Mojo, could allow a remote attacker to exploit heap corruption through a crafted HTML page.
- CVE-2023-6350 (CVSS Score: 8.8): A use-after-free vulnerability in libavif might enable a remote attacker to exploit heap corruption via a crafted avif file.
PrestaShop:
Two significant SQL injection vulnerabilities have been identified, affecting PrestaShop, an e-commerce platform:
- CVE-2023-46349 (CVSS Score: 9.8): A security vulnerability in the “Product Catalog (CSV, Excel) Export/Update” module (< 3.8.5) for PrestaShop allows a guest to perform SQL injection through a simple HTTP call.
- CVE-2023-48188 (CVSS Score: 9.8): Another SQL injection vulnerability affecting PrestaShop (opartdevis v.4.5.18 – v.4.6.12) enables a remote attacker to execute arbitrary code. The risk is associated with a crafted script to the getModuleTranslation function.
WordPress:
Several critical vulnerabilities have been identified in different WordPress plugins:
- The WPB Show Core WordPress plugin through 2.2 is vulnerable to local file inclusion CVE-2023-4922andServer-Side Request Forgery (SSRF) CVE-2023-5974via the ‘path’ parameter. Both vulnerabilities have a CVSS score of 9.8.
- CVE-2023-5604 (CVSS Score: 9.8): The Asgaros Forum WordPress plugin before 2.7.1 allows forum administrators, who may not be WordPress (super-)administrators, to set insecure configurations, enabling unauthenticated users to upload dangerous files, potentially leading to remote code execution.
- CVE-2023-5559 (CVSS Score: 9.1): The 10Web Booster WordPress plugin before 2.24.18 does not validate the option name given to some AJAX actions, allowing unauthenticated users to delete arbitrary options from the database, leading to Denial-of-Service (DoS).
ZyXEL:
Multiple critical vulnerabilities have been identified in ZyXEL NAS (Network-Attached Storage) firmware versions V5.21(AAZF.14)C0 and V5.21(ABAG.11)C0, exposing these devices to security risks:
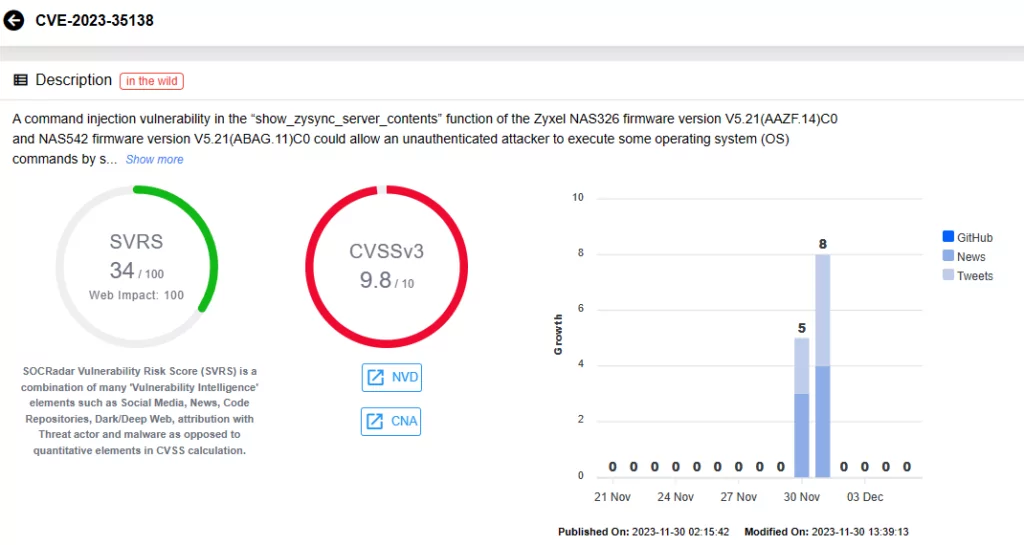
- CVE-2023-35138 (CVSS Score: 9.8): A command injection vulnerability in the “show_zysync_server_contents” function could allow an unauthenticated attacker to execute operating system (OS) commands through a crafted HTTP POST request.
The following vulnerabilities also enable the attacker to execute OS commands, but their exploitation requires an unauthenticated attacker to send a crafted URL to the vulnerable device:
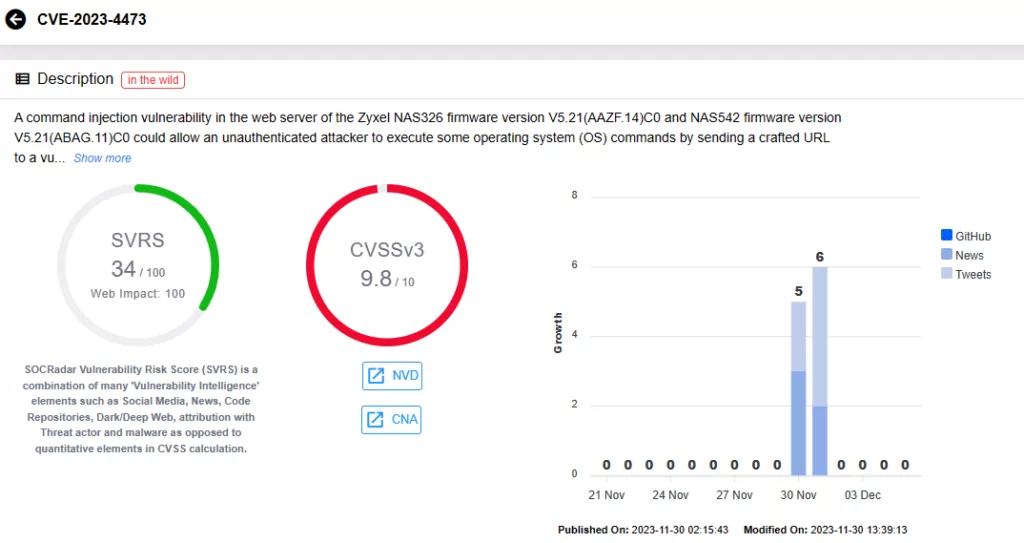
- CVE-2023-4473 (CVSS Score: 9.8): A command injection vulnerability in the web server.
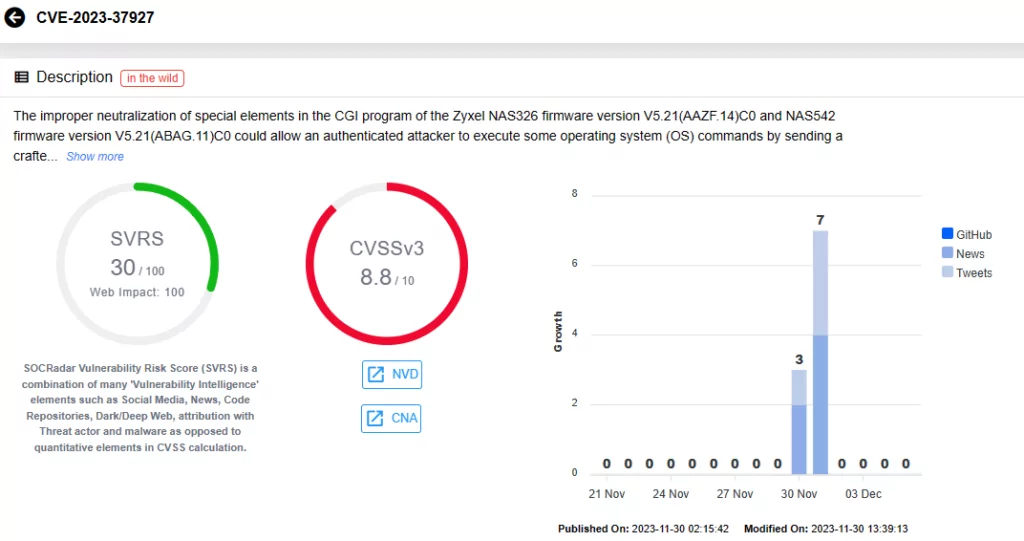
- CVE-2023-37927 (CVSS Score: 8.8): Improper neutralization of special elements in the CGI program.
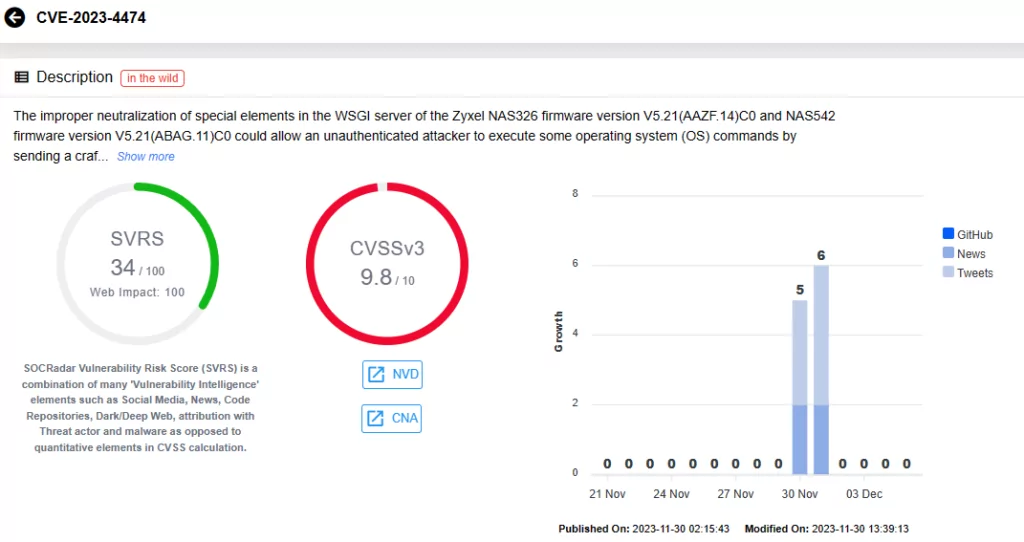
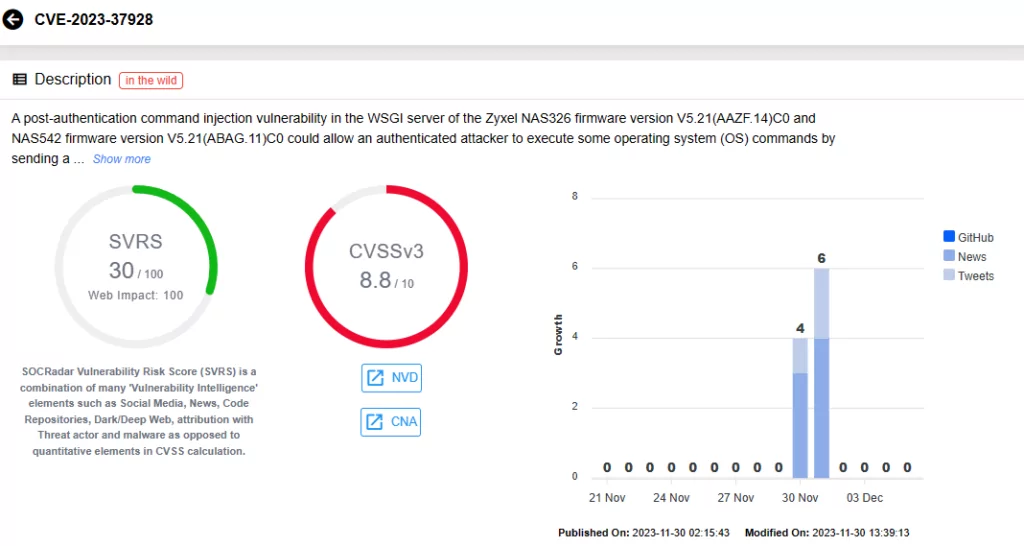
- Improper neutralization of special elements CVE-2023-4474 (CVSS Score: 9.8) andCVE-2023-37928 (CVSS Score: 8.8) a post-authentication command injection vulnerability in the WSGI server.
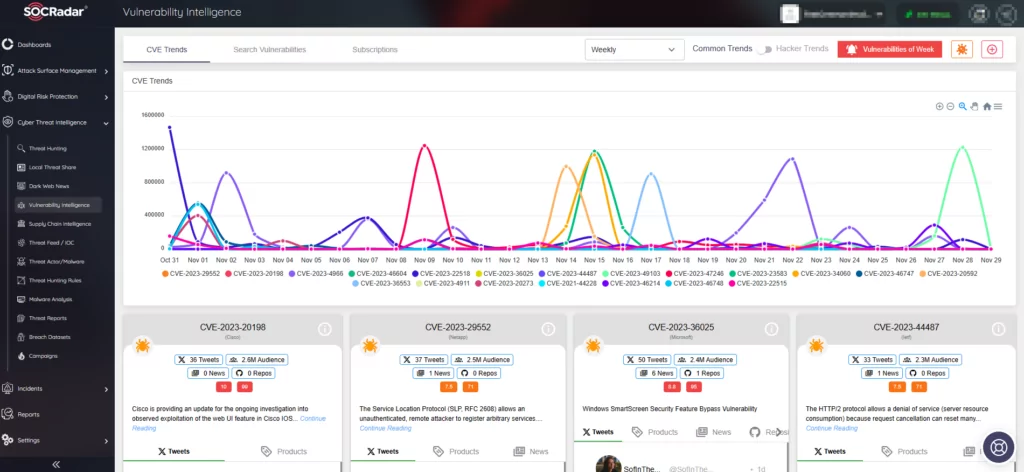
Empower Your Defense with SOCRadar’s Attack Surface Management and Vulnerability Intelligence
Utilize the Attack Surface Management (ASM) module to proactively monitor emerging vulnerabilities across your digital assets. With the ASM module, you can receive timely threat alerts and enhance your security posture, effectively managing patching efforts.
For deeper insights, real-time updates, and valuable information on hacker trends associated with identified vulnerabilities, you can leverage SOCRadar’s Vulnerability Intelligence feature. Vulnerability Intelligence delivers specific details about vulnerabilities and their SOCRadar Vulnerability Risk Score (SVRS), providing a comprehensive understanding of their popularity and potential for exploitation.