
Microsoft’s August 2023 Patch Tuesday Fixes Six Critical Vulnerabilities and Two Exploited Zero-Days
Microsoft’s August 2023 Patch Tuesday has just arrived. The update addresses a total of 74 vulnerabilities, six of which have critical severity, and two zero-days that are actively exploited. Additionally, there are two security advisories: ADV230003 and ADV230004.
The ADV230003 advisory serves as an update regarding the zero-day issue identified as CVE-2023-36884 (initially disclosed in the July 2023 Patch Tuesday). The second zero-day concern tackled by August 2023 Patch Tuesday is labeled as CVE-2023-38180.
The following vulnerability types are included in August’s Patch Tuesday:
- 23 Remote Code Execution (RCE) Vulnerabilities
- 18 Elevation of Privilege (EoP) Vulnerabilities
- 12 Spoofing Vulnerabilities
- 9 Information Disclosure Vulnerabilities
- 8 Denial of Service (DoS) Vulnerabilities
- 4 Security Feature Bypass Vulnerabilities
We will highlight the addressed vulnerabilities, the risks associated with the zero-day exploits, and the steps organizations can take to safeguard their systems. Leveraging insights from SOCRadar Vulnerability Intelligence, we will navigate the complex landscape of cybersecurity to ensure your digital defenses are fortified.
Zero-Day Vulnerabilities Under Active Exploitation: CVE-2023-36884 and CVE-2023-38180
This month’s Patch Tuesday addresses two zero-day vulnerabilities that have been actively exploited:
CVE-2023-36884 (CVSS Score: 7.5): The vulnerability involves the exploitation of Microsoft Office and its defense mechanism. Originally thought to be a remote code execution vulnerability, and was addressed in Microsoft July 2023 Patch Tuesday. However, it was later classified as a security feature bypass.
The CVE-2023-36884 lets attackers craft specialized Microsoft Office documents to bypass Mark of the Web (MoTW) security feature, opening files without warnings and enabling remote code execution. The RomCom group, now called ‘Underground,’ actively exploited this vulnerability.
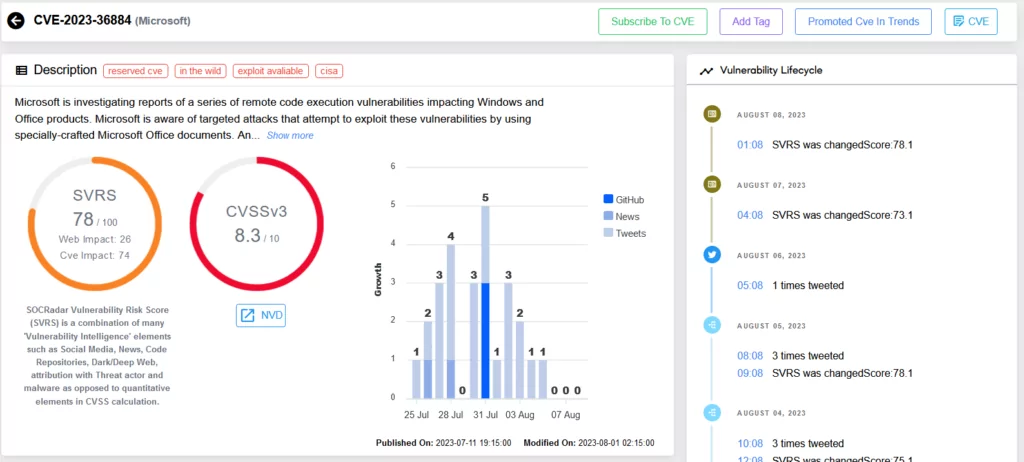
CVE-2023-38180 (CVSS Score: 7.5): This vulnerability targets .NET applications and Visual Studio, enabling attackers to launch Distributed Denial of Service (DDoS) attacks. While specific details regarding the exploitation remain undisclosed, its potential for widespread impact is concerning. These zero-day vulnerabilities underscore the urgency of applying updates promptly and the importance of advanced threat detection, such as SOCRadar’s Vulnerability Intelligence module, which can provide critical insights into emerging risks.
Critical Vulnerabilities of August 2023 Patch Tuesday
There are six vulnerabilities classified as critical, emphasizing the need for swift action.
A particular focus lies on vulnerabilities such as CVE-2023-35385, CVE-2023-36910, and CVE-2023-36911, which impact Microsoft Message Queuing. These remote code execution vulnerabilities highlight the importance of securing essential services that attackers could exploit to infiltrate systems.
CVE-2023-35385 (CVSS score: 9.8): If this vulnerability is successfully exploited, an unauthorized attacker could remotely execute code on the targeted server.
CVE-2023-36911 (CVSS score: 9.8): The vulnerability allows an unauthenticated attacker to remotely execute code on the target server.
CVE-2023-36910 (CVSS score: 9.8): An attacker could exploit this vulnerability by sending a specially crafted malicious MSMQ packet to an MSMQ server, allowing them to perform server-side remote code execution.
CVE-2023-29328 & CVE-2023-29330 (CVSS score: 8.8): An attacker could manipulate a victim into participating in a Teams meeting to achieve remote code execution. This enables the attacker to access the victim’s data, allowing them to both view and modify it. Moreover, this exploit has the potential to disrupt the client machine, leading to periods of downtime.
The threat group APT29 (aka Cozy Bear, Midnight Blizzard) likely exploited these vulnerabilities in their recent phishing attacks. For more information, refer to our blog post: APT Profile: Cozy Bear / APT29
CVE-2023-36895 (CVSS score: 7.8): The vulnerability allows for remote code execution within Microsoft Outlook. According to the advisory, the security update is not yet available for Microsoft Office 2019 for Mac and Microsoft Office LTSC for Mac 2021. Microsoft clarifies that customers will be notified of the update via the advisory.
We strongly advise you to apply the patches as soon as possible to protect your environment and improve your security posture. More information on the vulnerabilities covered in this update can be found in Microsoft’s Release Note.
Mitigate Vulnerability Risks with SOCRadar
To effectively navigate the evolving cybersecurity landscape, proactive defense is imperative. SOCRadar’s Vulnerability Intelligence and External Attack Surface Management solutions provide the tools to identify, assess, and address vulnerabilities in real time. By incorporating SOCRadar into your security strategy, you can bolster your defense mechanisms and stay one step ahead of emerging threats.
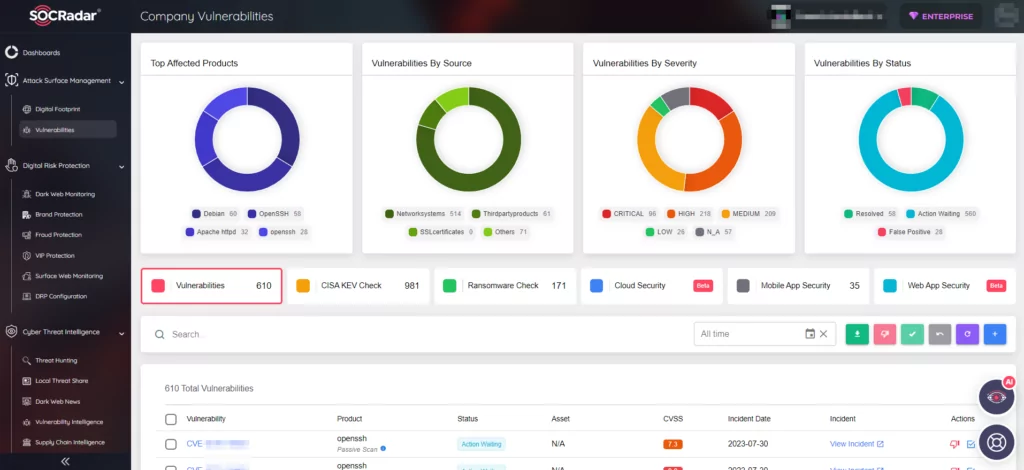
SOCRadar’s Vulnerability Intelligence enhances security measures by tracking security vulnerabilities. You can use the module to search for vulnerabilities, access their details and associated activities, and even observe the hacker trends.
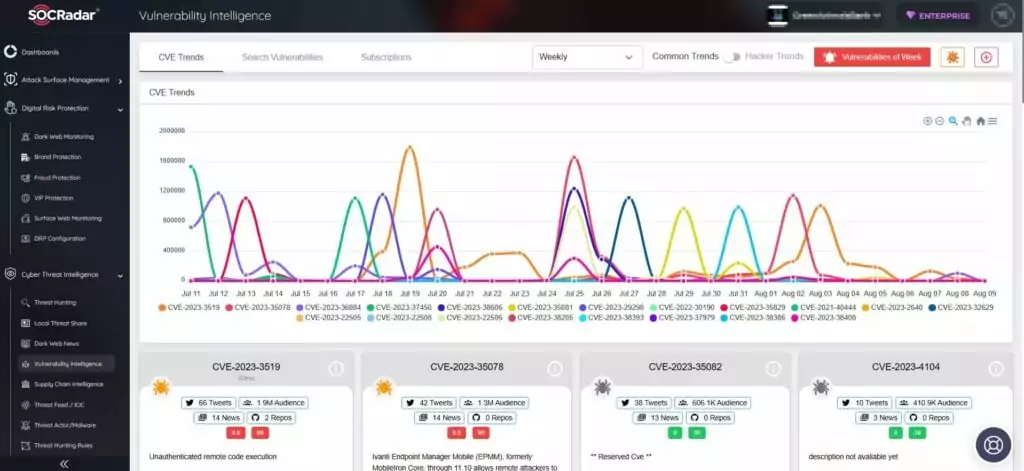
As the cyber landscape evolves, SOCRadar remains committed to helping you navigate these challenges, ensuring the integrity of your systems, data, and reputation. Embrace the power of advanced cybersecurity solutions to safeguard your digital assets and maintain a resilient defense posture against emerging threats.



































