
Telekopye Telegram Bot: 8 Year Old Phishing Kit Mimicking eBay and Other E-Commerce Sites
Telekopye is a Telegram bot, named by combining the words Telegram and “kopye,” which means “spear” in Russian. The bot acts as an accomplice for threat actors, including those with limited technical knowledge. Its operation facilitates online phishing scams, primarily in Russia, while also reaching out to global targets.
With the help of predefined templates, the Telekopye Telegram bot automatically creates phishing web pages. Threat actors can then send potential targets the corresponding URLs that lead to malicious landing pages.
Various iterations of the Telekopye Telegram bot have been identified, with the earliest dating back to 2015. This indicates that the malicious bot has been around for at least 8 years.
Automating Multi-Scammer Fraud Campaigns with Telekopye Telegram Bot
Radek Jizba, an ESET researcher, elaborates on the Telekopye toolkit, describing it as a Telegram bot that, when activated, provides user-friendly menus. This allows for the streamlined engagement of multiple scammers simultaneously.
Telekopye, a fully-featured toolkit, empowers users with the means to carry out a range of fraudulent activities: sending phishing emails and SMS, generating QR codes and web pages, and producing convincing images and screenshots of checks and receipts.
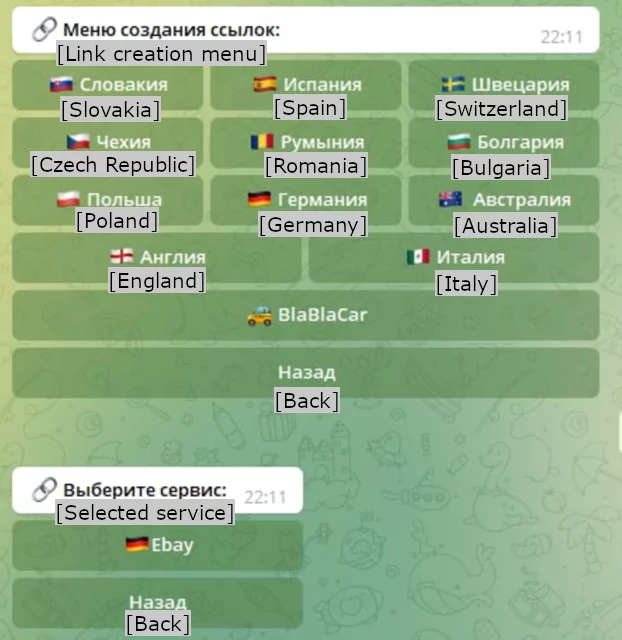
The phishing kit equips users with ready templates for emails, texts, HTML phishing pages, forms, and even images of financial documents. The templates for landing pages are tailored to websites in specific countries, with a global reach in mind.
Within its Telegram community, Telekopye is utilized to automate phishing campaigns against users of popular e-commerce platforms like eBay.
The Roles in a Telekopye Phishing Scam: Neanderthals and Mammoths
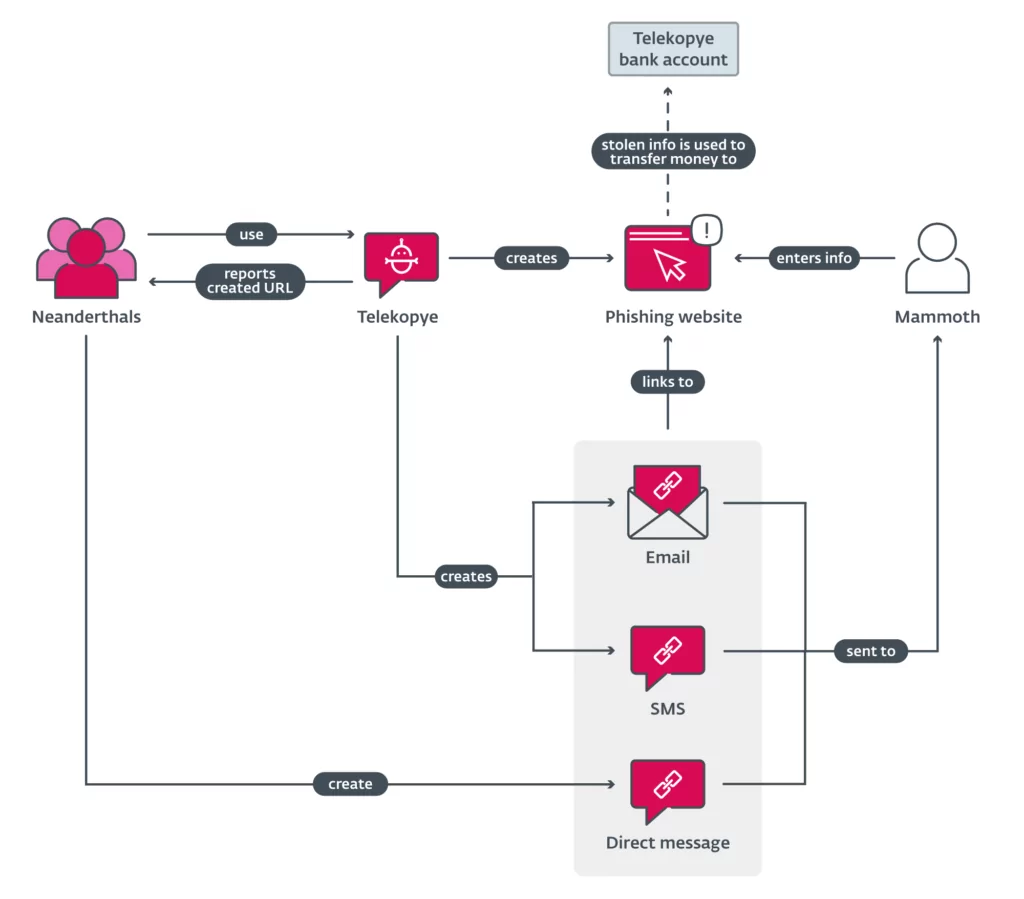
The attack begins with threat actors, which ESET researcher Jizba refers to as Neanderthals, identifying their targets. The Neanderthals label their victims as “Mammoths,” and try to build a connection. After that, they send fake links through email, SMS, or direct messages. These misleading links are created using the Telekopye phishing kit.
In the phishing domains, it is ensured that the URL commences with the expected brand name. This tactic is employed to make it harder to spot the scam, exemplified by following URLs:
- cdek.id7423[.]ru
- olx.id7423[.]ru
- sbazar.id7423[.]ru
Notably, after a successful scam, the stolen money is transferred to a shared account controlled by the Telekopye administrator rather than directly to the threat actors’ accounts. Using the toolkit, the Neanderthals request payment from the Telekopye administrator.
Phishing Techniques Used with Telekopye Telegram Bot
Jizba explains two key phishing methods:
Type 1.0 aims at online shoppers. When victims input their credit card details on the payment pages of the fake shopping sites, the threat actors use this information to withdraw funds. Subsequently, they launder the stolen amount through cryptocurrencies.
Type 2.0 targets sellers, luring them with deposit requests. A typical message might say, “Your item has been paid for,” followed by a phishing link.
The Telegram community of the Telekopye bot operates with a corporate structure, consisting of admins, moderators, skilled workers, and regular workers. A commission fee ranging from 5% to 40% is taken for each scam, as this fee is divided between the platform owner and the recommender.
Telekopye’s Possible Russian Connection
The origins of the threat actors behind the Telekopye Telegram bot are unknown; however, indications such as the use of Russian message templates and their focus on targeting popular Russian online marketplaces suggest that those who created and employ the bot are most likely Russian.
Jizba asserts that the best chance to spot a Telekopye phishing scam is when threat actors make an effort to appear trustworthy in their communications, frequently speaking a different language.
Unlock Comprehensive Dark & Deep Web Monitoring with SOCRadar
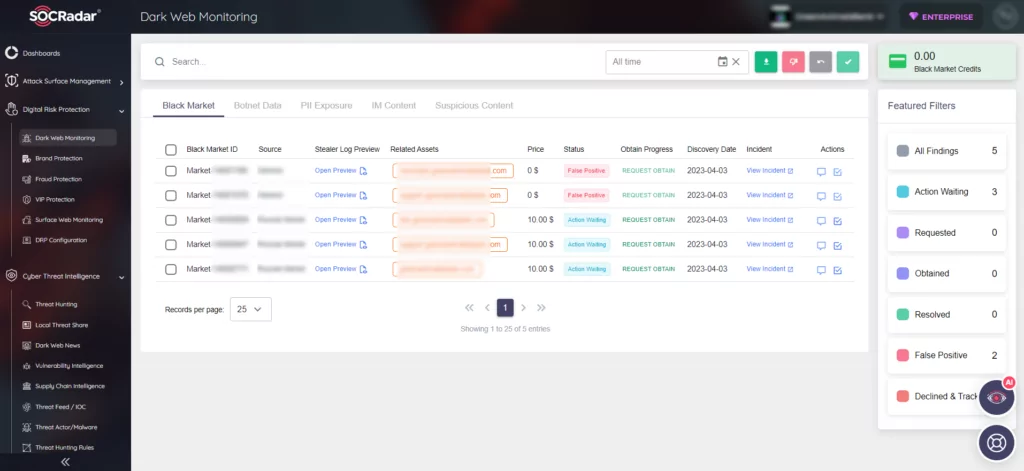
Our solution empowers organizations to spot and counter threats across the surface, deep, and dark web. Through cutting-edge reconnaissance and threat analysis, we provide actionable intelligence to proactively secure your organization.
By combining automated external cyber intelligence with expert analysts, SOC teams can extend their control beyond their traditional perimeters.
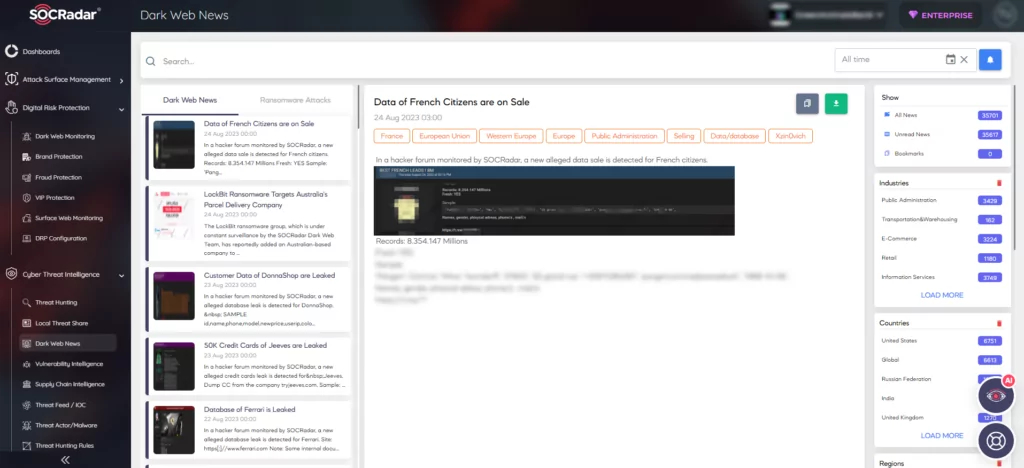
SOCRadar also provides sector-specific and regional dark web news to keep organizations informed about evolving threats.
As we conclude this eye-opening journey into the dark corners of the web, it is clear that cyber threats spare no one. From cutting-edge tools like Telekopye to exposed databases revealing sensitive information, the cyber underworld is thriving, attracting both criminals and potential victims.
Let this be a reminder of the vital importance of vigilance and robust cybersecurity in our digital age. Stay informed, stay secure, and let’s navigate this challenging cyber landscape together.



































