
SMS Bomber: How Dangerous Can a Text Be?
Among the ever-evolving threats in the world of cybersecurity, SMS Bomber attacks are emerging as a modern danger that can have significant and disturbing consequences. Recently, almost all of us have received SMS or calls from unknown numbers on our phones. Almost all of these numbers are from businesses, sales companies or illegal betting sites that receive SMS permission from their customers.
SMS Bomber attacks typically target a victim’s phone number and send a large volume of text messages over a period of time. These messages can make the victim’s phone constantly vibrate, play alert tones or flood it with notifications. Such attacks can render the victim’s phone non-functional and prevent normal communication.
There are basically two common ways for attackers to use if they want to start an SMS Bomber attack. One of them is the SMS marketing services that have loose restrictions. They allow attackers’ requests without sound questioning.

An SMS Bomber advertisement on a dark web forum monitored by SOCRadar
The SMS Bomber above can be an example of the misuse of various marketing services with loose restrictions. According to that post, the tool can spam the target with SMS and calls, but there are time restrictions, and the spamming will stop. After that, a restart is mandatory to continue the attack. There are also additional hourly pay. The tool also can direct calls from call center operators during the business hours. According to the post, it is also possible to understand whether the target phone is turned on or not.
These additional capabilities suggest that a marketing service with loose restrictions could be behind this SMS Bomber tool, and attackers are exploiting that service. The boundaries of this tool are not limited to sending only an OTP.
The other way is related to API security. When you need to login to your account, depending on your security settings or the platform, you might get a password you will use only one time. Platforms use APIs to send these OTPs. And sometimes these APIs can have certain vulnerabilities, allowing attackers to exploit them and send lots of SMS.
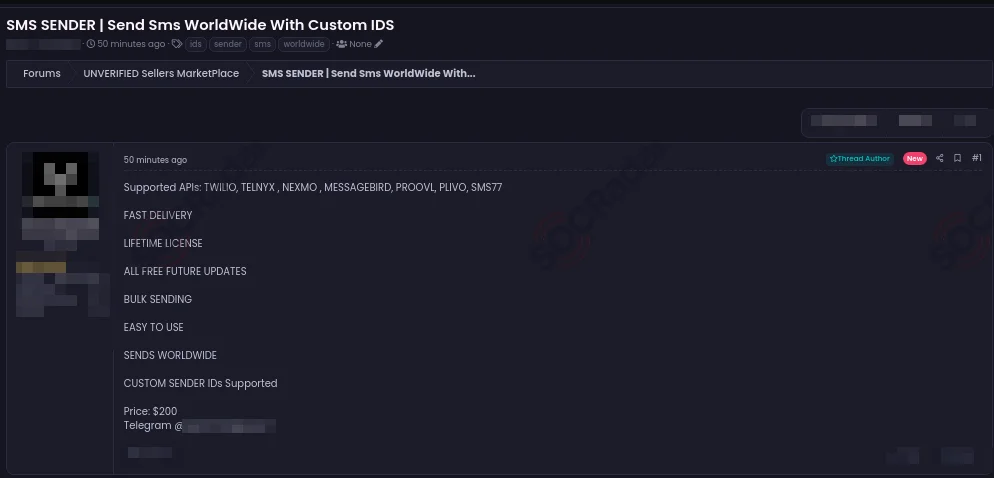
SMS Sender sale on a dark web forum monitored by SOCRadar
The SMS Sender above is a tool priced at $200 that supports various APIs. These kinds of tools benefit from weak API security measures. The tool features fast delivery and bulk sending capabilities. It also supports worldwide message sending and allows custom sender IDs.
SMS Bomber attacks can serve different purposes. For instance, they may encompass trolling, cyberbullying, or diverting the target’s attention. Simple scripts can be employed for such attacks. Underground forums, messaging platforms like Telegram, ICQ, and Discord, as well as open-source code sharing platforms such as GitHub and Replit, can yield considerable results. Throughout our research, our aim was to maintain a wide scope in our field of study.
The Underground SMS Bomber Market and Pricing
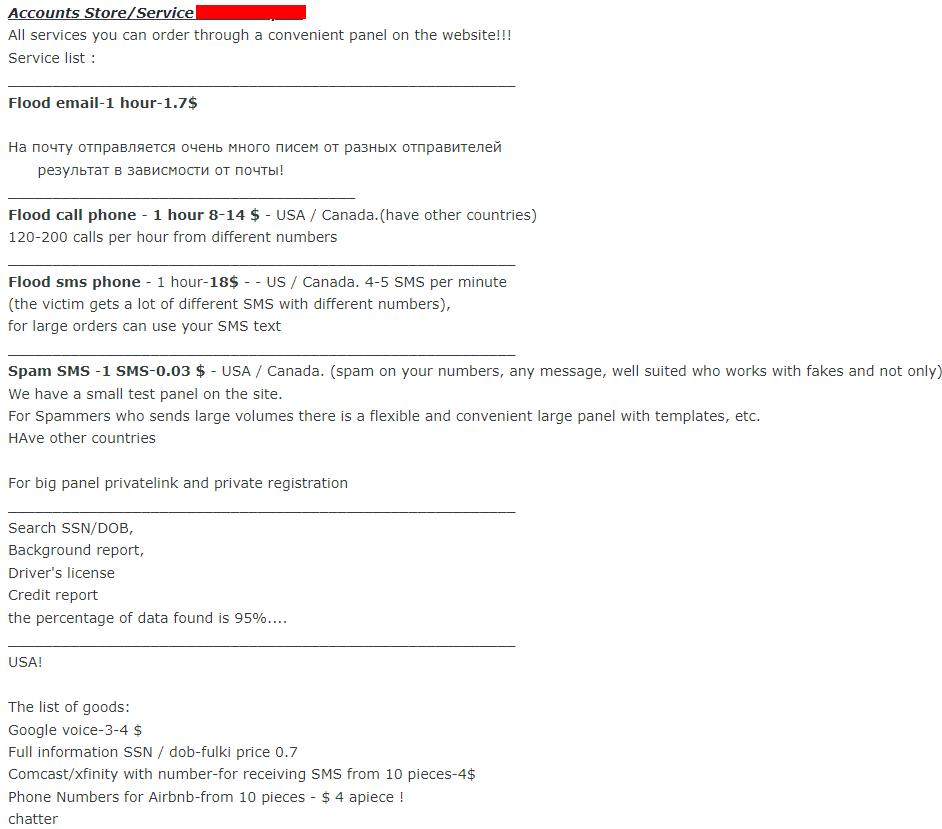
In one of the underground forums we monitor, we have deduced from the comments that this particular post is frequently favored. Apart from SMS, this post also provides services related to email and phone calls. The pricing details for the services offered are as follows:
- Flood email 1 hour: 1.7$
- Flood phone call 1 hour: 8-14$ (120 – 200 calls per hour from different numbers)
- Flood sms phone 1 hour: 18$ (4-5 sms per minute)
- Spam sms 1 sms 0.03$
Except for pricing, the targeted country is US / Canada.
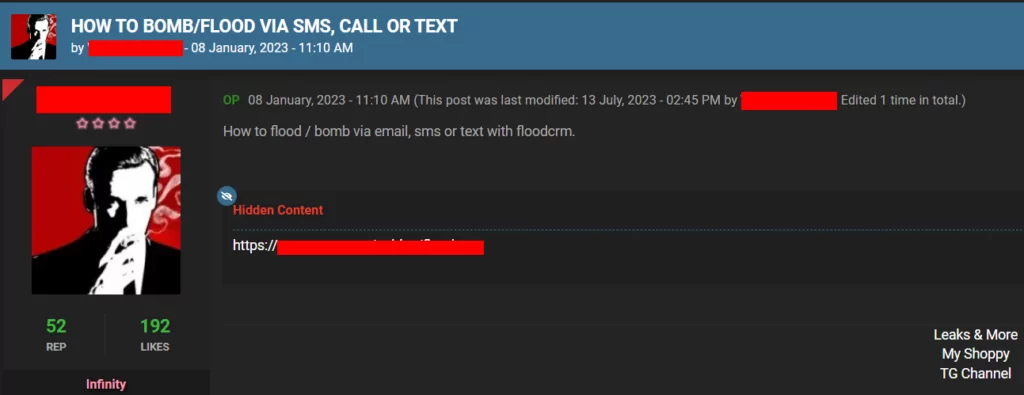
In another underground forum we track, there is a post with significant engagement that includes a URL capable of being used for SMS bomber and other malicious purposes.
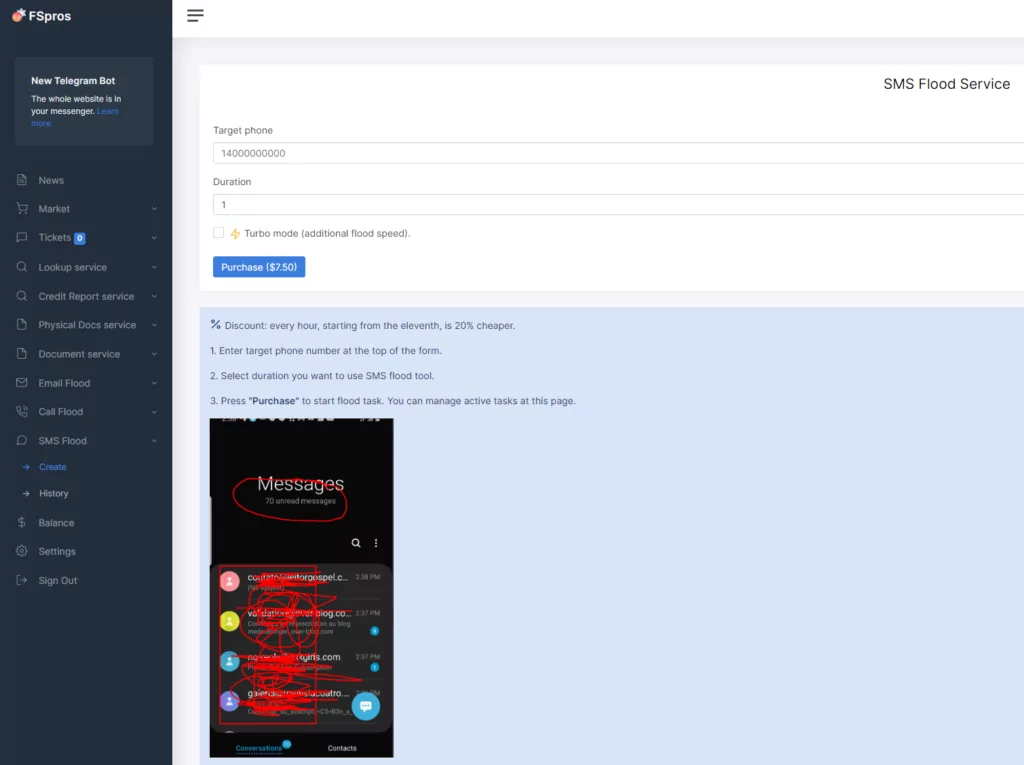
In the redirected link, we encountered a panel that provides arange of services beyond SMS attacks. Accessible through free membership, the panel offers SMS attack services for a specified fee. Attackers can determine the attack duration, and the pricing increases as the duration extends. For instance, a 1-hour attack costs $7.50, while a 100-hour attack demands a payment of $615. Additionally, attackers can activate the turbo mode for a quicker attack, which incurs an extra charge for targeting a specific individual. This mechanism enables attackers to easily initiate an SMS attack and inflict harm upon target systems.
Telegram Channels: SMS Bomber Shares and Sales
As a result of our research on Telegram channels, we encountered a channel that was established on December 16, 2022, and caught our attention due to its substantial subscriber count and provision of paid services. This channel, boasting 94,925 subscribers, lacks any conversation history. Communication is conducted directly with a bot, necessitating us to interact with the bot for transactional activities.

We contacted the bot and proceeded in line with certain steps and got information about prices.
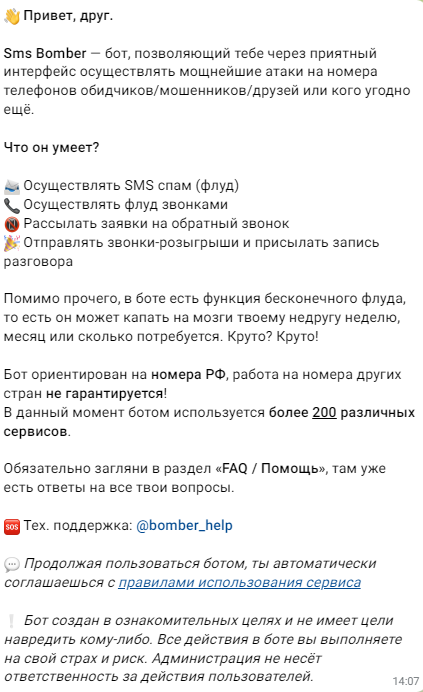
Here are the bot’s answers:
What can it do?
- Perform SMS spamming (flooding)
- Make flood calls.
- Send callback requests
- Send prank calls and send a recording of the call.
According to the message, the attackers plan to specifically target Russian numbers in this SMS attack. However, they do not guarantee that it will work on phone numbers from other countries. This means that the success or failure of the attack depends on the targeted country, and the attackers do not offer any guarantees in this regard.
“The bot is designed for Russian Federation cell phone numbers; its functionality on numbers from other countries is not guaranteed! Currently, the bot is utilized by more than 200 distinct services.”

The pricing details are as follows:
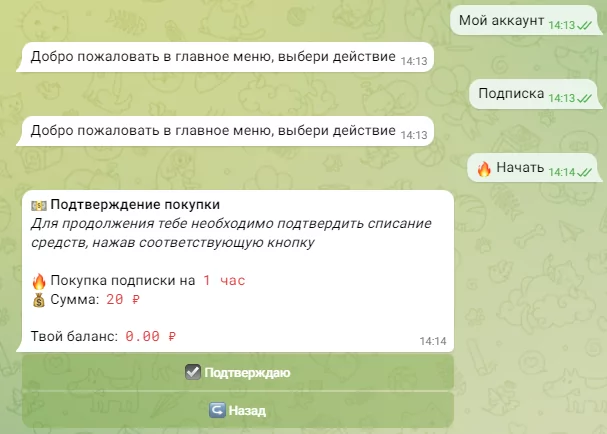
In the continuation of our research on Telegram channels, we came across another interesting post on a different channel with 352 subscribers. An SMS Validator application, which is an SMS bomber and released under a different name, can attack users with the same methods.
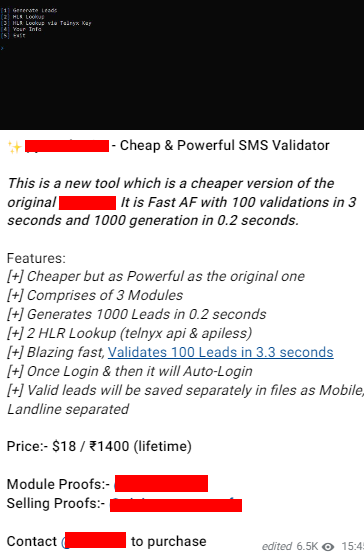
According to their explanation, they do not possess the original SMS validator. Instead, they offer the lite version for sale at a more budget-friendly price, which is indistinguishable from the original. This lite version is available for $18 for a single use and at a price of 1400₹ (Indian Rupees) for lifetime use.
GitHub & Replit Repo Research
We obtained a large number of results from the open source sharing platforms GitHub and Replit, using only a few search words. You can see the results of the queries we made especially for Replit in the table below.
| Search Strings | Code Count |
| SMS bomb | 1K Code |
| SMS bomber | 4.9K Code |
| SMS bombing | 341 Code |
Just by tweaking the word “bomb” we got quite a lot of results, but the total value of these results does not give us the actual number, because there are also scripts in the repositories that are triggered at the same time. The important point to focus on here is that there are many ready-made scripts for SMS Bombing available on the Replit platform.
As part of our research process, while examining these codes, we also came across a newly created repo that will probably be continued. We followed the repo published on 25.07.2023 and left only as “Test”.
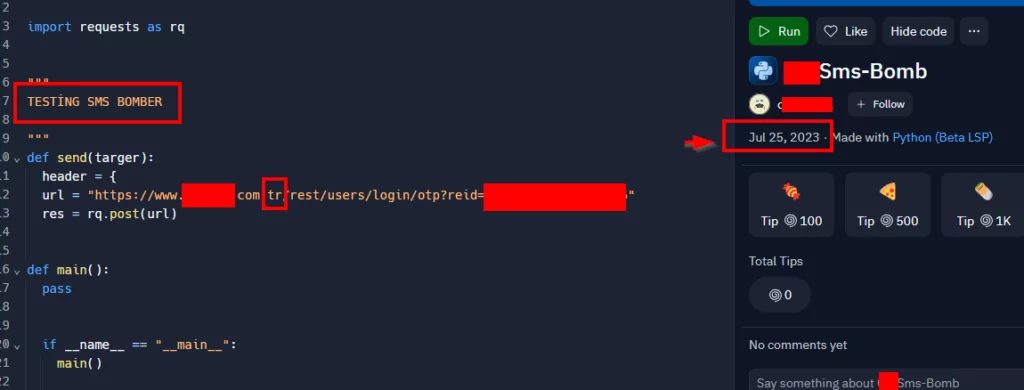
As can be seen from the screenshot, the repo owner added a company belonging to the “TR” domain to its first target and left it as such. Considering that the code will bring continuity, as the SOCRadar Treat Research team, we always follow such detections in a controlled manner.
After conducting research on other repositories, we successfully acquired definitive results that address the question of ‘How are SMS Bombing attacks executed?’. In the screenshot below, we can observe a straightforward Python script that facilitates request submission via an API, targeting the ‘register’ pages of domains and subdomains associated with Russia and Ukraine.
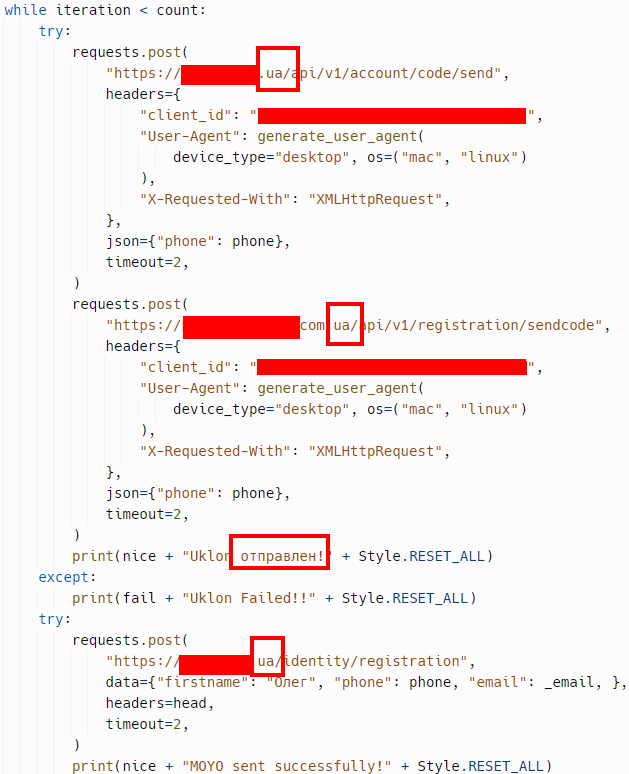
To provide a rough explanation of the code, it enters a conditional loop and sends requests to the ‘register’ pages, one by one, for the phone number provided as input, as can be seen in the ‘try’ section of the code. If the request process succeeds,
print(nice + ‘MOYO sent successfully!’ + Style.RESET_ALL) is executed, allowing us to display the string ‘MOYO sent successfully!’. In case of failure, the ‘except’ section triggers another print function to display the text ‘MOYO Failed!о!‘ on the screen.
In this SMS Bomber script, created by a Russian user to carry out SMS Bomber attacks by exploiting the vulnerabilities of Russian and Ukrainian domains and subdomains, we were able to identify a total of 52 domains and subdomains.

The results we obtained from analyzing just one of the SMS Bomber scripts bring its threat potential to the forefront. The related Python script can excessively burden communication infrastructure and lead to service interruptions by flooding the targeted individual(s) with a large volume of spam SMS. These types of attacks can become even more harmful due to weak security measures, particularly on registration pages, and the absence of secure API integrations.
Websites should be more sensitive to security vulnerabilities, especially in registration pages and APIs. One effective way to enhance security is by implementing CAPTCHA challenges on registration pages. This proactive step can significantly mitigate the risk of fake account creation by distinguishing between automated bots and genuine users. Strengthening verification processes alongside CAPTCHA integration becomes essential in thwarting potential threats. Additionally, securing APIs is a critical step to reduce the risk of unauthorized access and maintain system integrity. Such measures are important both to ensure the security of user data and to strengthen defenses against cyberattacks.
In line with our investigations for a different repository (repo), we noticed that one of the domains with a Russian Top-level domain (TLD) provides payment systems services.
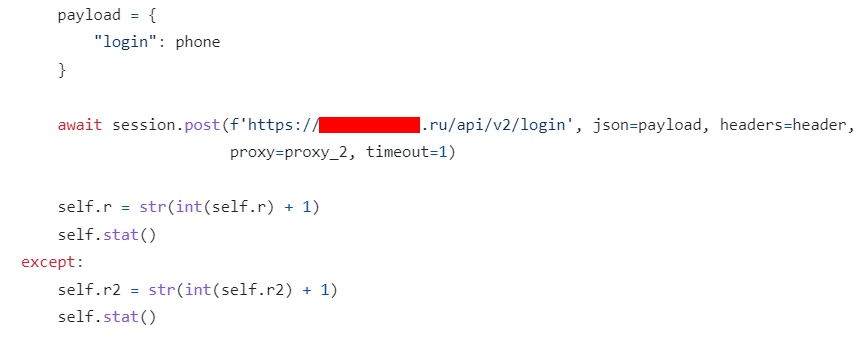
When we queried the domain query for the web address we obtained from the Threat Hunting module of the SOCRadar XTI platform, we received results indicating that quite a lot of data leaks were made.
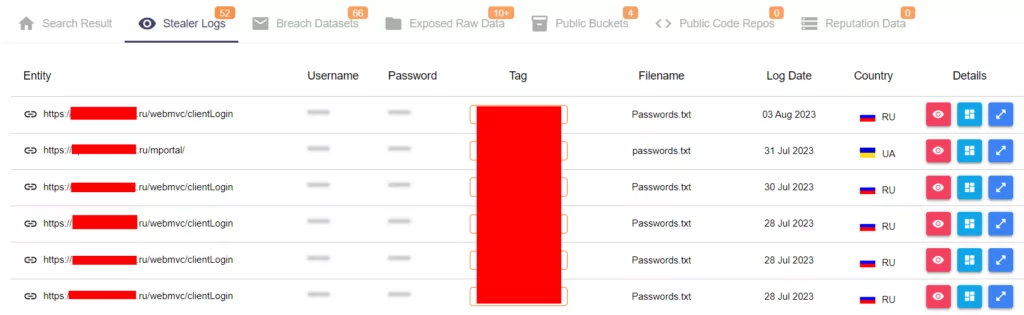
Some results from SOCRadar’s Threat Hunting, Stealer Logs
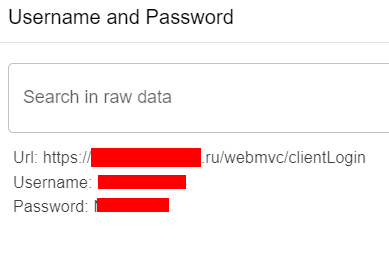
Username and password information in the logs
As a result, a total of 52 Stealer Logs, 66 Breach Datasets and more than 10 Exposed Raw Data were detected for the domain. In addition, 4 Public Buckets were found.
When we look at the profile of the repo owner for an SMS Bomber Python script published 6 years ago among the most copied (forked) and starred repos on Github, there is also his LinkedIn profile. When we visited his LinkedIn profile, we observed that he works as a Senior Security Analyst at HackerOne.
Google Dorks & Country Research
Through research on underground forums, Telegram channels, Github and Replit, we identified the web addresses used for the SMS Bomber attack and the country of origin of the web addresses. We then continued our research using Google Dorks to find more information.
Before we share the Google Dorks results, here is a diagram of the web addresses, countries of affiliation and sectoral information we have identified.
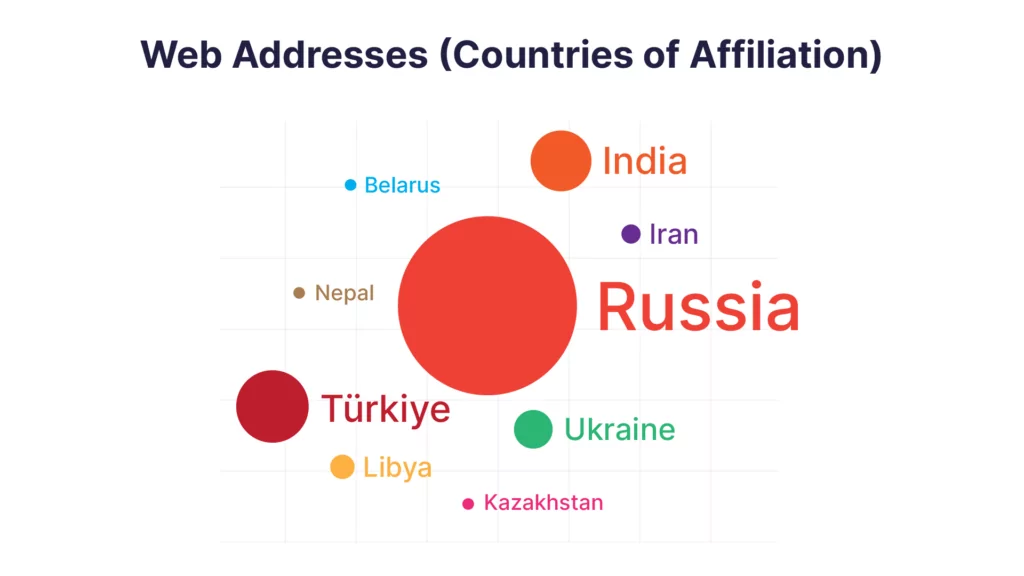
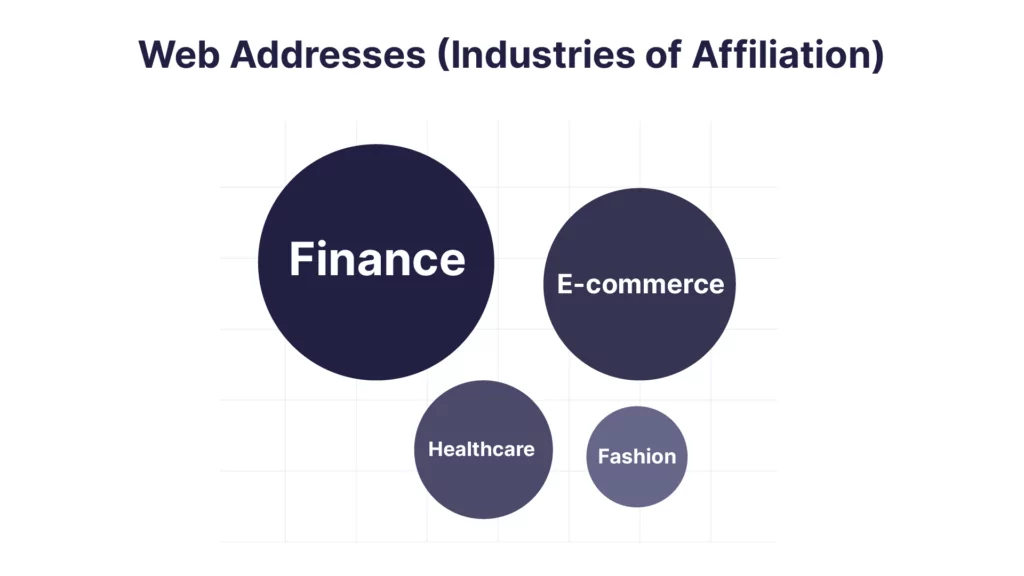
When we looked at the country-based results of the web addresses used for SMS Bombing, we saw that the most detection was made in Russia. Then we obtained quite a lot of results in Turkey, India and Ukraine. The most common ones by sector are as follows: Food and Beverage (21), Finance (20), E-commerce (15), Health (12), Fashion (10).
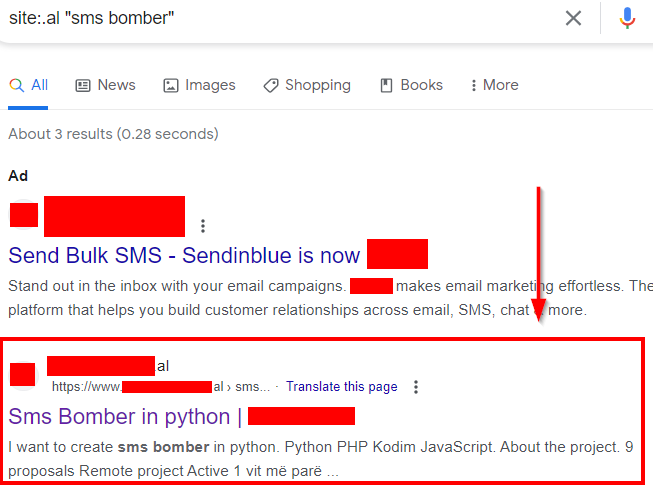
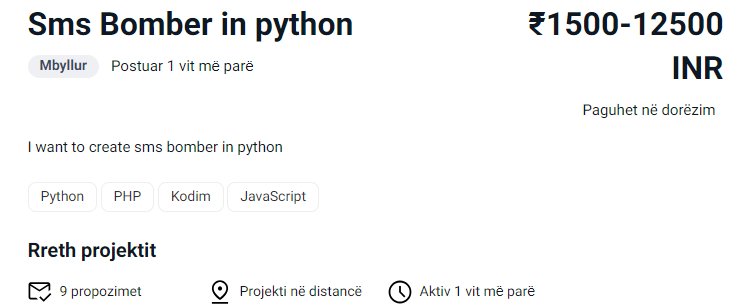
For the countries not on our list, we used a simple Google dorks to list the results with the word “sms bomb” in the country area codes. For Albania, we came across a rather surprising result; a Python-based SMS Bomber advertisement created on a Freelancer website.
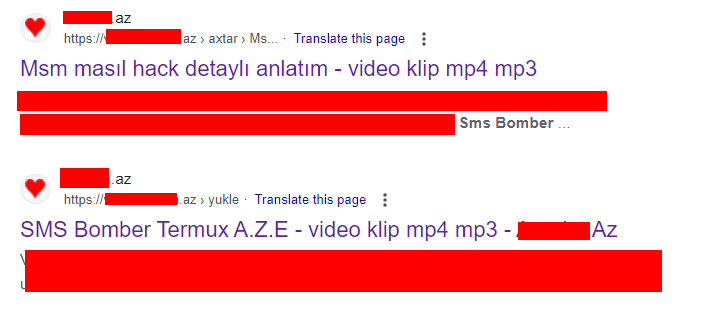
Continuing to use Google dorks, we continue to find surprising results, including for Azerbaijan.
Lessons Learned
SMS Bomber activities have been around since the 1990s, when cell phones and SMS services became widespread. At that time, when phone numbers were easy to obtain and SMS sending was widespread, such attacks were carried out to harass users and disrupt services. With the advancement of technology and the internet, the use and impact of SMS Bomber scripts has increased and has continued to this day. For this reason, cybersecurity experts and service providers are constantly updating and improving security measures to combat such attacks.
Protection Methods:
- Spam Filters: Carriers and messaging apps can detect and block spam messages using spam filters. You can protect yourself from spam messages by enabling these filters.
- Number Hiding: Avoid sharing your personal phone number online. By not publicly posting your number on social media and other platforms, you are less likely to be the target of spam attacks.
- Reliable Sources: Beware of messages from unknown or unreliable sources. Try not to respond to messages from unknown numbers or people you do not know.
- Countermeasures to be taken by SMS Service Providers: Companies should implement strong control mechanisms, including rate limiting and captcha methods, to prevent message bombardment and monitor suspicious patterns.
How to Protect Yourself from SMS Bomber Attacks
Whether you are an individual or a company, it is important to maintain digital hygiene in order to protect yourself from malicious activities such as SMS Bomber attacks. These attacks can disrupt your daily operations, but by reporting incidents promptly and seeking assistance from law enforcement, you can mitigate the risks up to a certain degree. There are a couple of things you can do to minimize the impact of this annoying attack type:
- If you are an individual suffering from SMS Bomber attacks:
- Report each SMS to the company from which it is being sent, ensuring they are aware of the misuse of their service. This is a very tiring process, considering all the messages you will receive. But if you invest the time to contact the companies and let them know about the situation they will both increase their security measures and can also block your number from receiving such messages in the future.
- Report this malicious activity as a cybercrime to your local law enforcement authorities. Law enforcement might have similar cases already, and they might be following the attackers. Giving them additional information can help them with their investigation.
- If you are a company discovering that your APIs are being exploited:
- Either switch to a different service with better security measures or promptly fix the vulnerabilities in your existing system.
- Contact law enforcement authorities to report the exploitation and seek assistance in preventing further attacks.
How SOCRadar is Responding?
As the Threat Research team, we meticulously evaluate current or potential threats, analyze them logically and then initiate research and prevention processes. Thanks to this research, we are constantly expanding the frameworks we need to follow in order to inform our customers on every issue and increase their security levels.
Even issues that are not often brought to the surface for security research, such as SMS Bomber, can actually have serious impacts and vulnerabilities on companies. For this reason, we identify the necessary updates and provide important information to our customers without disregarding any detail. By keeping our customers informed about threats, we help them protect their security at the highest level. Our goal is to minimize the risks to our customers’ security and IT infrastructures and help them create a safer digital environment with the valuable information we provide them.
Conclusion
As a result of this research, it was determined that the attackers used the registration pages of the companies and sent spam messages to the victims via API request. The measures that can be taken to protect against such attacks can be listed as follows:
- API Security: Regularly check your APIs for vulnerabilities and only allow access to trusted users.
- Education: Educate your employees about spam and phishing attacks. Make them aware not to click on messages and links from unknown sources.
- Spam Filters: Enable and regularly update spam filters in email, SMS and messaging apps.
- Authentication Layers: Block automated attacks using additional security measures such as two-factor authentication and CAPTCHA.
- Data Breach Monitoring: Set up a data breach monitoring mechanism that tracks suspicious or anomalous traffic and enables rapid response.
- Web Security: Conduct regular security scans and apply timely updates to secure your website.
- Authorization and Access Controls: Grant access to certain features only to the necessary people and roles, and strictly control privileges.
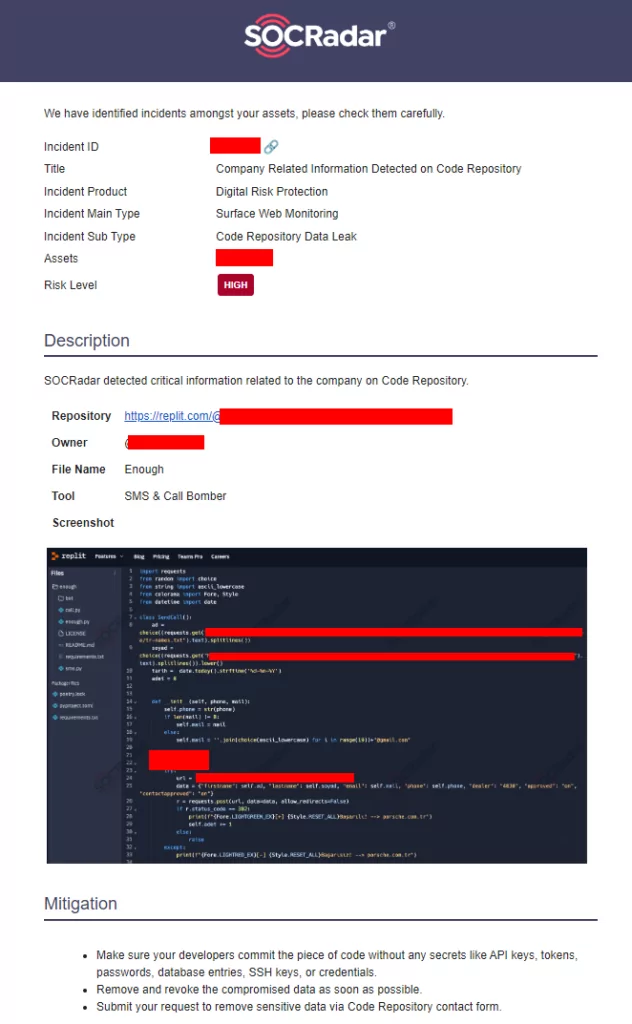
Ensure that your developers process the code fragment without any confidential information such as API keys, tokens, passwords, database entries, SSH keys or credentials. Remove and revoke compromised data as soon as possible. By implementing these measures, companies can create a more secure environment against spam and other attacks and better protect their customers’ data.




































