
Customer Story: Bucket Half Empty? Half Full? Fully Public?
In the days we live, security means not just physical security, especially in the business world. The protection of digital assets is now one of the priorities of every company, and reaching those assets without authorization is the aim of every cybercriminal. Cybersecurity companies are trying to help organizations protect their assets and prevent cybercriminals from reaching their targets.
SOCRadar, coining the Extended Threat Intelligence and one of these cybersecurity companies in between, aims to prevent cyberattacks before they happen by providing fast, relevant, and actionable cyber threat intelligence. However, our job does not only consist of providing IOCs, threat feeds, blogs, and reports robotically.
We, as a company, do care not only about our customers but also about making the cyber world a safer place for everyone. Our vision is the democratization of threat intelligence, meaning that SOCRadar wants everyone to be able to reach our fast, relevant, and actionable cyber threat intelligence by reducing the price involving machine learning and AI. And, of course, we strive for excellence; we try to stay a couple of steps ahead of the bad guys. We want to make a difference, and we will.
So, we decided to share how we made a difference for some people and organizations and how we could make a difference for you. As a result, we will share some stories we observed firsthand or made happen.
Our first case is from Europe. A case shows that our physical safety and digital safety go hand-and-hand from now on.
Who: A subsidiary of a holding company
Region: Europe
Industry: Digital media
Challenge: Personally Identifiable Information leak in the cloud environment
Solution: Automated cloud storage monitoring
One of SOCRadar’s customers, active in the European digital media industry, was challenged with leaked sensitive information issues.
In this case, a third party, an insurance company, stored the official documents, including contracts with all the related details, in publicly available cloud storage. The company provided insurance services for our customers’ cars, which were given to senior managers, a detail which increases the risk of data exposure even more critically.
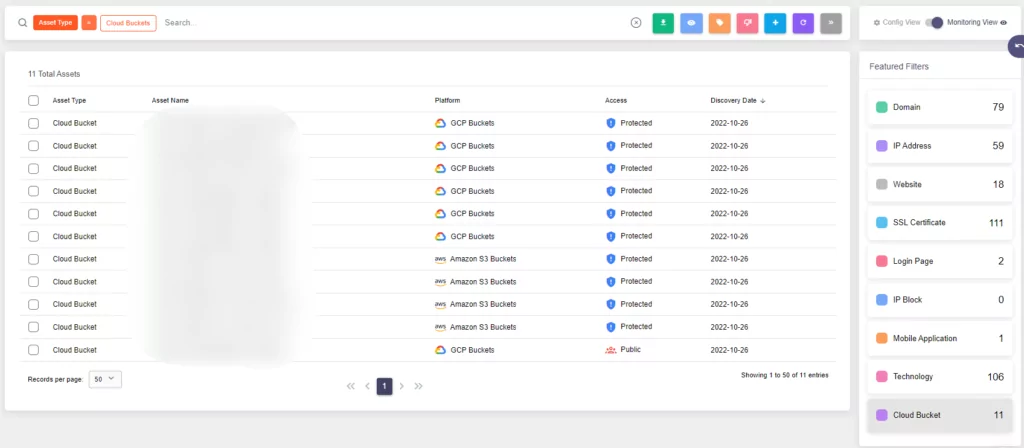
After SOCRadar’s Cloud Security Module (CSM) detected that the insurance documents containing sensitive information were stored in a publicly available cloud bucket belonging to the insurance company, the customer was immediately alerted to take necessary precautions.
The information included several Personally Identifiable Information (PII) along with the plate number and vehicle type, which could cause physical and cyber security issues.
Why is This Important?
PII is quite important to threat actors in several ways. Cybercriminals frequently sell this data in forums on the dark web where other threat actors are looking for information for entry points to launch attacks against their targets. A sophisticated cyberattack may target your company due to this type of data exposure.
The Cloud Security Module (CSM) of SOCRadar’s External Attack Surface Management (EASM) services strive to shield our clients’ data from exposure in cloud computing environments. Our customers will receive a notification when sensitive data is discovered in any public cloud storage.
The CSM services offered by SOCRadar also keep track of our customers’ own cloud buckets and alert them when any of those buckets’ statuses change, allowing our customers to avoid any security problems resulting from misconfigurations of the cloud buckets.
This module also found the buckets causing one of the biggest B2B leaks, BlueBleed.
As seen above, only searching and indexing the dark web, social media accounts, and hacker communications are great but not enough. Companies need to know what has been put in public buckets about them and need solutions like our CSM module to do it for them.




































