
LockBit Shares Boeing Data, Software Company and US Database Leaks, Dutch RDP Sale
The SOCRadar Dark Web Team has diligently documented a series of unsettling activities within the depths of the dark web. Among them is a fresh update on the Boeing data leak orchestrated by the LockBit ransomware gang, along with database leaks of the RingCentral software company and a U.S. wireless database. Notably, a sale related to Remote Desktop Protocol (RDP) associated with a Dutch company adds to the complex tapestry of cyber threats.
Now, let’s explore the latest activities on the dark web that have captured our attention.
Find out if your data has been exposed.
Alleged Boeing Files are Published
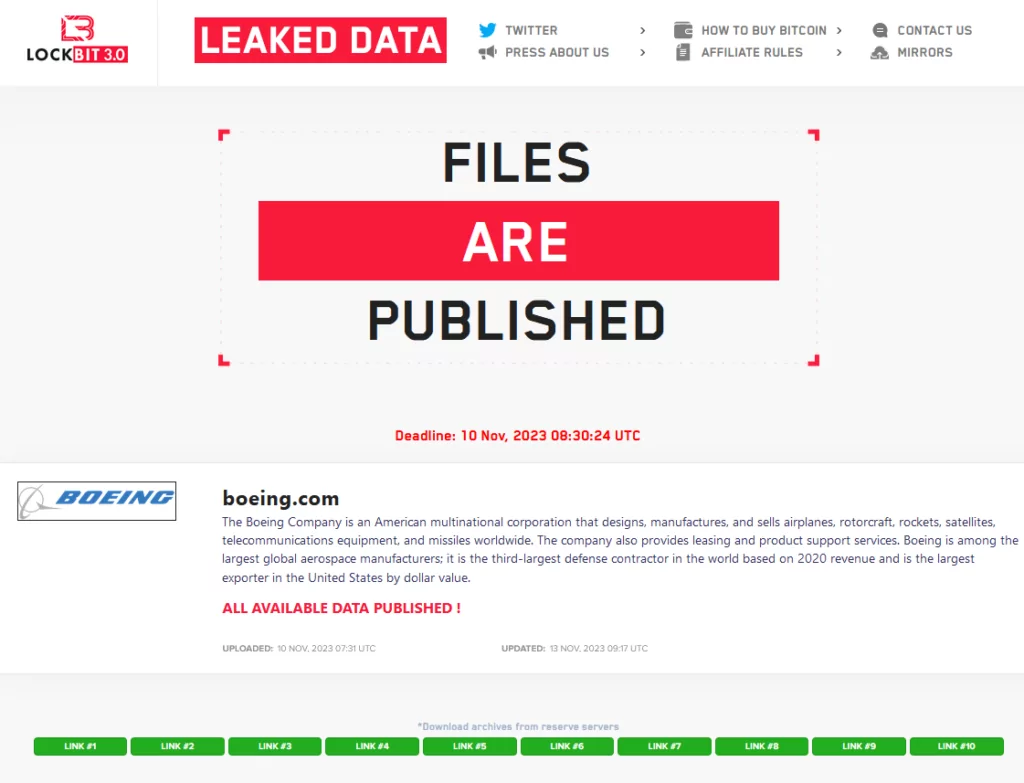
The SOCRadar Dark Web Team has unveiled further developments involving the notorious hacker group LockBit‘s latest major operation, allegedly victimizing Boeing. On November 10, in their leak site, they disclosed backups of various systems, the most recent one stamped on October 22.
Previously, the aerospace giant Boeing allegedly fell victim to LockBit on October 27, with the group setting a November 2 deadline for negotiations after claiming to have obtained a substantial amount of sensitive data. Until November 10, LockBit repeatedly added and removed Boeing from its victim list. On November 10, LockBit, probably for the last time, listed Boeing as “data published,” along with 40GB data leak and download links.
Because the data published so far are generally records between 2017 and 2019, some researchers say that LockBit may still have further data but is pushing to get payment in the negotiation. Still, there is no official statement or evidence yet.
Wireless Database of the United States is Leaked
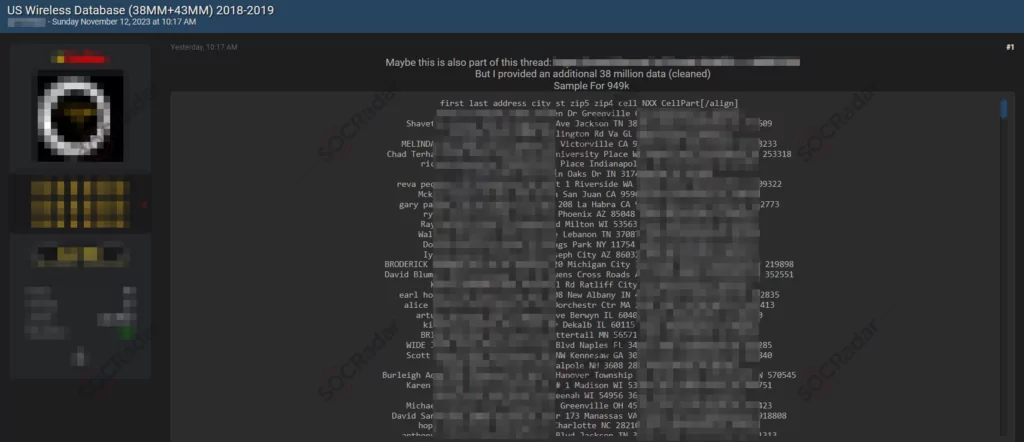
In a recent post on a hacker forum closely monitored by SOCRadar, a potential security breach has been identified, involving a wireless database leak within the United States. The threat actor has claimed to possess a substantial amount of data, totaling 38 million records (cleaned). As a sample, the threat actor has provided details for 949,000 individuals, including their full names, addresses, phone numbers, and other personally identifiable information. The motive behind this data leak and its potential impact on the affected individuals and entities are currently under investigation.
The provided sample data includes diverse geographical locations and demographic information, raising concerns about the scope and scale of the potential breach. SOCRadar analysts are actively working to ascertain the authenticity of the leaked data to mitigate any potential risks associated with this incident.
Alleged Database Leak of a Software Company
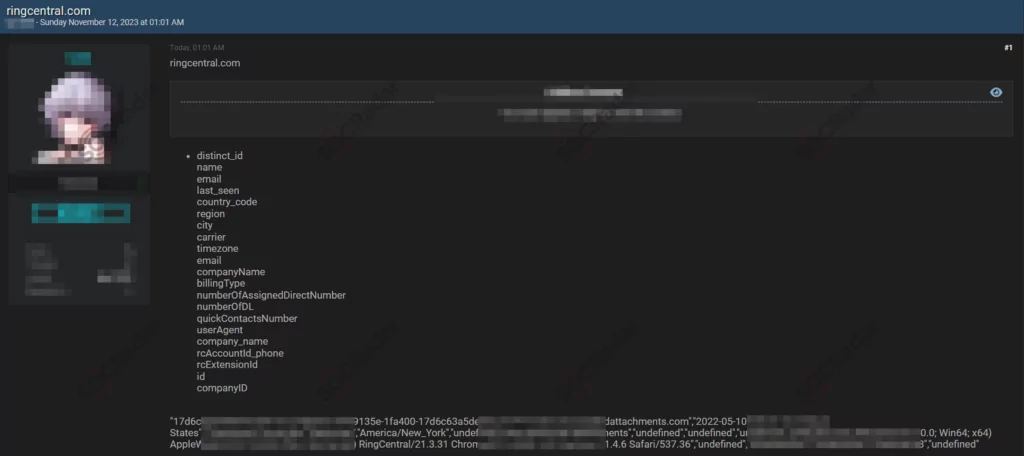
In a recent discovery on a hacker forum under SOCRadar’s surveillance, a suspected database leak for RingCentral, a prominent software company, has been detected. The alleged leaked data, originating from ringcentral.com, includes information such as distinct IDs, names, email addresses, and additional details like last-seen timestamps and geographic information. The alleged data breach appears to expose users’ sensitive information associated with company, potentially impacting their privacy and security.
RDP Sale Related to a Dutch Company
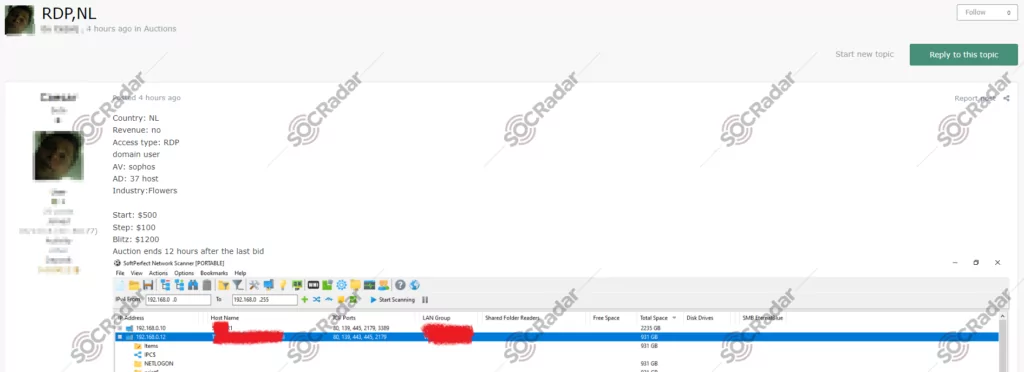
During routine monitoring of a hacker forum, SOCRadar has identified an unauthorized RDP access sale related to a Dutch flower company. The offering discloses details like the country (NL), access method (RDP), and the use of Sophos antivirus (AV) on the compromised system. The auction starts at $500, with bidding increments of $100 and a blitz option at $1,200. The auction is scheduled to conclude 12 hours after the last bid.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































