
Atlassian’s Confluence Data Center and Server Affected by Critical RCE Vulnerability, CVE-2023-22527: Patch Now
[Update] August 29, 2024: “Cryptojacking via CVE-2023-22527”
[Update] January 25, 2024: “CVE-2023-22527 Has Been Listed in CISA KEV”
[Update] January 23, 2024: “Exploitation Attempts for Atlassian Confluence Data Center and Server RCE Vulnerability, CVE-2023-22527”
[Update] January 19, 2024: “CISA Urges Organizations to Apply Atlassian Security Patches for Vulnerabilities in Confluence Data Center and Server”
Atlassian is advising its customers to update their Confluence Data Center and Server to prevent the exploitation of a critical vulnerability that could potentially result in Remote Code Execution (RCE).
What Is the New Atlassian Vulnerability About?
The critical vulnerability, identified as CVE-2023-22527 and assigned a maximum severity rating of 10.0, constitutes a template injection vulnerability present in older versions of Confluence Data Center and Server.
This security vulnerability could enable unauthenticated attackers to achieve Remote Code Execution (RCE) on affected instances.
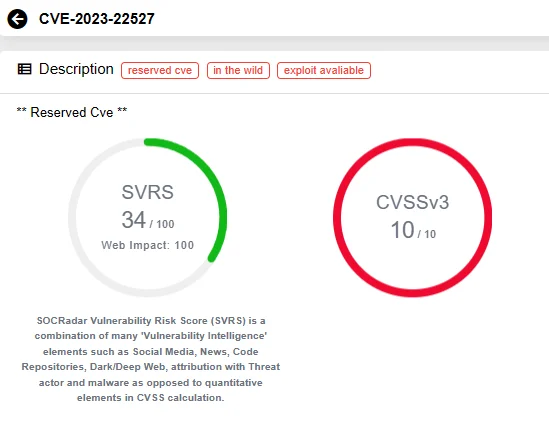
SOCRadar Vulnerability Intelligence: CVE-2023-22527
The vulnerability significantly impacts all aspects of the CIA triad (Confidentiality, Integrity, and Availability).
Threat actors have previously targeted vulnerabilities in various Atlassian products, as evidenced by CISA’s inclusion of a Confluence Data Center and Server vulnerability in its Known Exploited Vulnerabilities Catalog in November 2023. Atlassian’s CISO had issued a warning about this vulnerability in October 2023.
In late November 2023, the company addressed a series of RCE vulnerabilities in Bamboo & Crowd Data Center and Server, posing serious security threats.
Moreover, in December, CISA emphasized the need for prompt action to address another set of critical vulnerabilities affecting different Atlassian products.
Given the widespread use of Atlassian products in business environments, the severity of the new vulnerability (CVE-2023-22527) is also likely to attract attention from threat actors.
Stay informed about vulnerability details and trends by utilizing SOCRadar’s Vulnerability Intelligence. Access the latest updates on identified vulnerabilities, including exploits and mentions through the module on the platform:
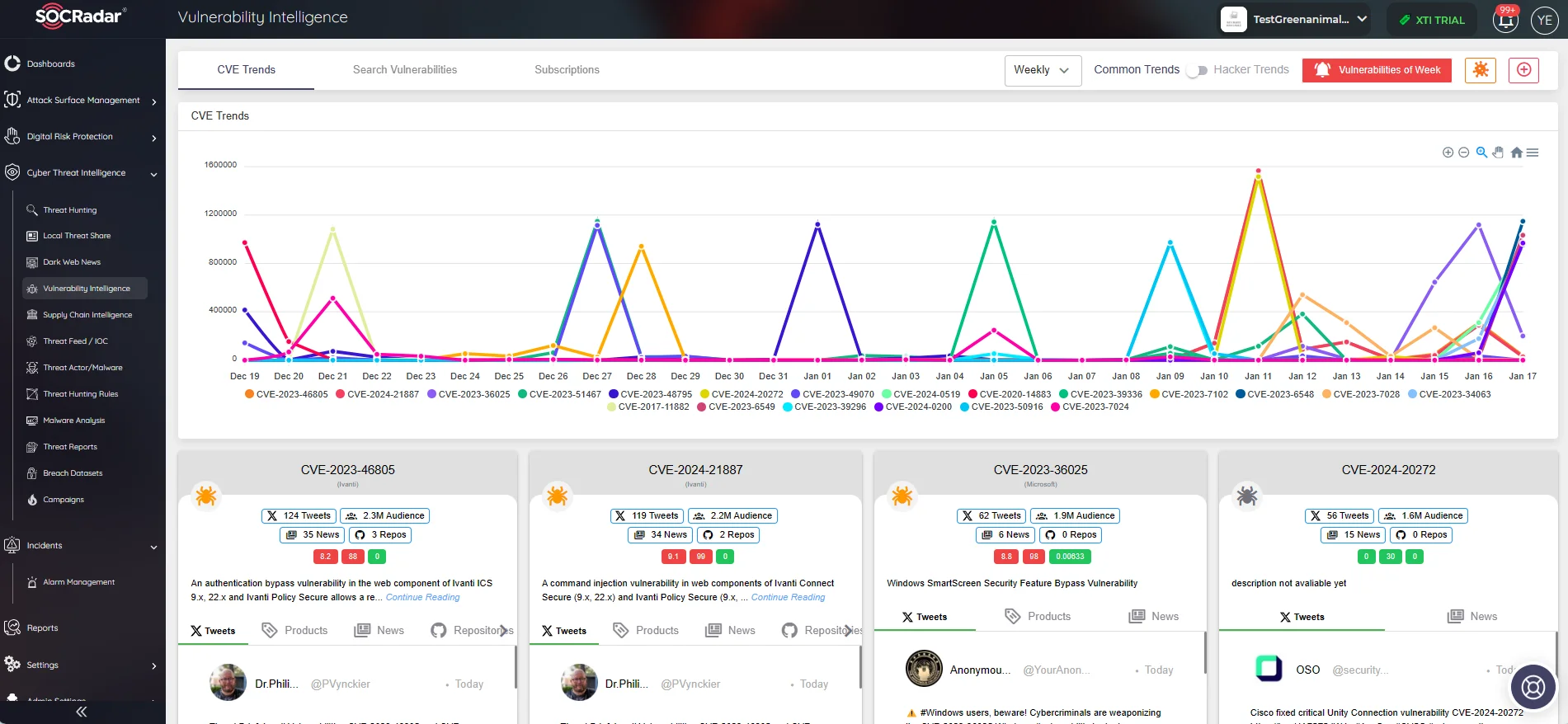
You can monitor CVE trends and access detailed information on vulnerabilities with SOCRadar’s Vulnerability Intelligence
Which Confluence Data Center and Server Versions Are Affected by CVE-2023-22527?
The CVE-2023-22527 vulnerability affects the following versions of Confluence Data Center and Server:
- 8.0.x
- 8.1.x
- 8.2.x
- 8.3.x
- 8.4.x
- 8.5.0 – 8.5.3
According to Atlassian’s advisory, most recent supported versions remain unaffected by this vulnerability; the issue specifically affects outdated Confluence Data Center and Server 8 versions released before December 5, 2023, and version 8.4.5 – which no longer receives backported fixes.
Atlassian further states that the 7.19.x LTS versions, Atlassian Cloud sites, and Confluence sites hosted by Atlassian are not vulnerable to CVE-2023-22527.
Are There Any Workarounds Available?
There are no workarounds available for the vulnerability, making the application of available updates the recommended course of action. Atlassian advises customers to install the latest version, which also offers protection against non-critical vulnerabilities outlined in Atlassian’s January Security Bulletin.
Noteworthy high-severity vulnerabilities from the bulletin include:
- CVE-2018-10054 (CVSS: 8.8): The vulnerability was found in H2 1.4.197, used in Datomic and other products. It allows RCE through CREATE ALIAS which allows the execution of arbitrary Java code.
- CVE-2020-26217 (CVSS: 8.8): It affects XStream (before 1.4.14), allowing a remote attacker to run arbitrary shell commands by manipulating the input stream. Only users relying on blocklists are impacted, while those using XStream’s Security Framework allowlist remain unaffected.
- CVE-2024-21674 (CVSS: 8.6): This vulnerability is also identified as an RCE issue, introduced in version 7.13.0 of Confluence Data Center and Server.
CISA Urges Organizations to Apply Atlassian Security Patches for Vulnerabilities in Confluence Data Center and Server
CISA has issued an alert, emphasizing the importance of promptly reviewing and applying recently released patches by Atlassian.
The alert highlights the risks posed by the critical CVE-2023-22527 vulnerability, along with other vulnerabilities addressed in the January 2024 Security Bulletin, cautioning that threat actors could exploit these vulnerabilities to gain control over affected systems.
For additional information and guidance on updating, refer to Atlassian’s security advisory.
Exploitation Attempts for Atlassian Confluence Data Center and Server RCE Vulnerability, CVE-2023-22527
Security researchers are monitoring exploitation attempts targeting the CVE-2023-22527 vulnerability.
Shadowserver shared on Twitter (X) that the exploitation attempts date back to January 19, 2024, with more than 600 IPs engaging in attacks thus far. The attackers are conducting tests, including callbacks and executing ‘whoami’ commands, gathering information about the targeted systems.
With over 39,000 exploitation attempts, the majority of them trace back to Russia. Additionally, there are over 11,400 Atlassian Confluence instances exposed to the internet.
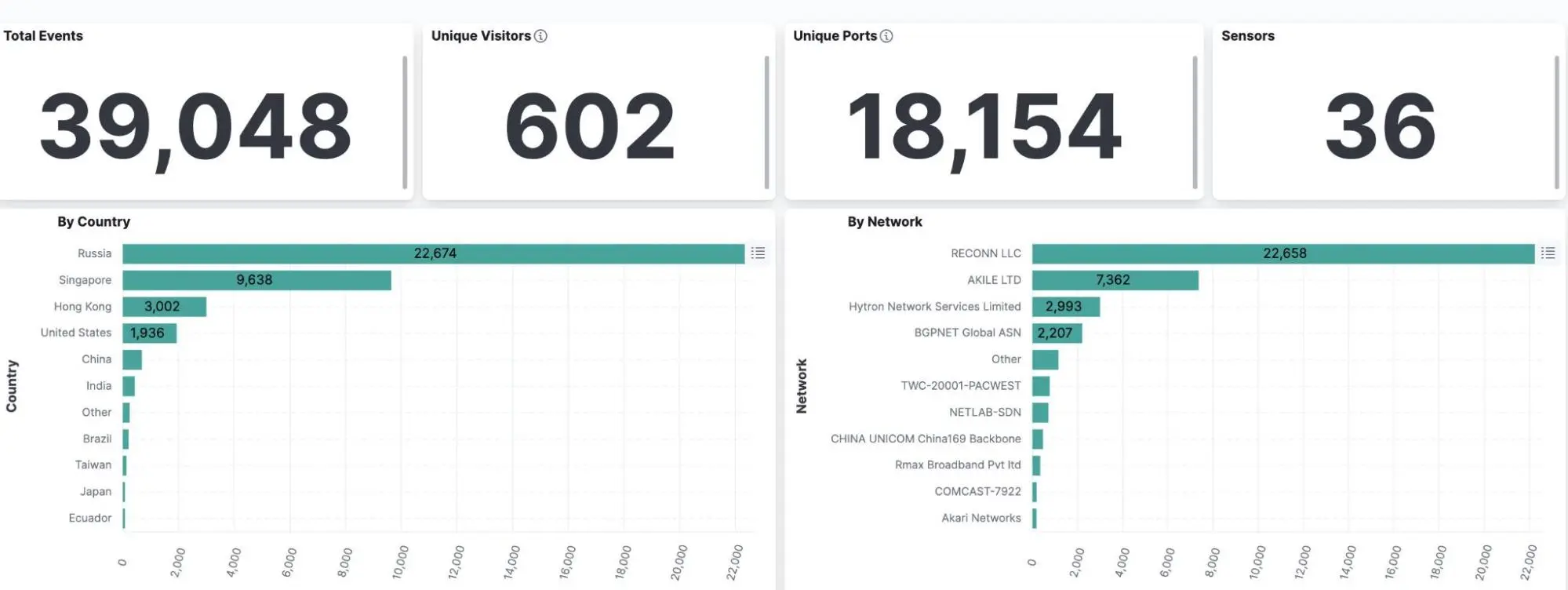
Exploitation attempts observed for the Atlassian RCE vulnerability (Shadowserver)
CVE-2023-22527 Has Been Listed in CISA KEV
CISA added CVE-2023-22527 to its Known Exploited Vulnerabilities (KEV) Catalog being that it is actively exploited. CISA stresses the severity of such vulnerabilities to the federal enterprise and cautions them to patch the vulnerability by the deadline of February 14, 2024.
You can enhance your vulnerability management strategy by monitoring digital assets, identifying potential vulnerabilities affecting your organization, and receiving crucial security alerts through SOCRadar’s Attack Surface Management (ASM) module. In addition, the Company Vulnerabilities page includes a CISA KEV Check feature that lets you see if a vulnerability found in your assets has been added to the KEV Catalog.
Cryptojacking via CVE-2023-22527
Since our initial coverage of the critical vulnerability CVE-2023-22527, which affects Atlassian’s Confluence Data Center and Server, there have been significant developments that highlight the importance of patching this flaw.
Trend Micro researchers discovered that CVE-2023-22527 is now actively used by threat actors to launch cryptojacking attacks. These attacks use the vulnerability to infiltrate systems and turn them into massive cryptomining networks.
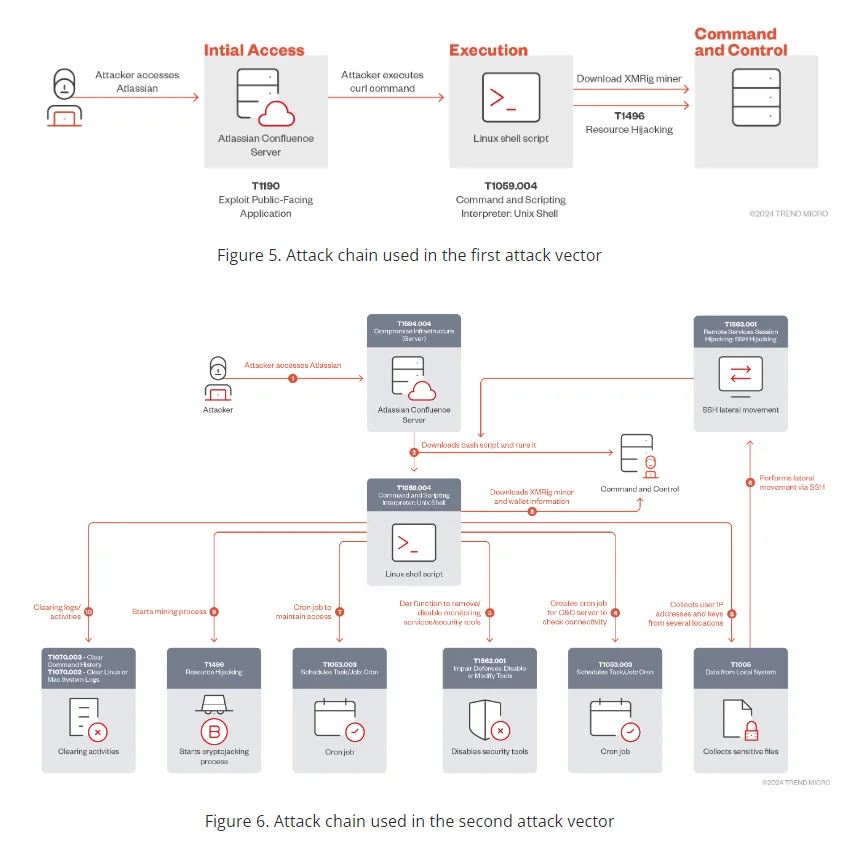
Attack chains used in the attack (Source: Trend Micro research)
Malicious shell scripts and XMRig miners are typically used to target SSH endpoints during the exploitation process.The analyzed script aggressively optimizes cryptojacking on compromised systems by disabling key security services such as Alibaba Cloud Shield. It then establishes persistence via cron jobs that keep a connection to the command-and-control server, allowing the attacker to continue cryptomining operations.
The script uses the gathered SSH credentials to disperse the cryptomining activities across the network, strengthening the attack. Before beginning mining with XMRig, it disables all security tools and then clears logs and bash history to cover its tracks, allowing cryptomining operations to continue undetected.
Sign up for a free edition to experience the full capabilities of SOCRadar XTI and take a proactive step towards a robust security posture.
View Company Vulnerabilities via SOCRadar’s Attack Surface Management




































