
What is DDoSia Project?
The DDoSia project is a cyber threat, a tool, leveraging the disruptive power of distributed denial-of-service (DDoS) attacks to target critical infrastructure and governmental bodies worldwide. DDoSia project was launched on Telegram in early 2022, managed by the pro-Russian hacktivist group NoName057(16), and has become a symbol of the growing intersection between cyber warfare and geopolitical conflict.

Logo of the DDoSia project on their Telegram channels
A Glimpse into DDoSia’s Operations
At its core, DDoSia functions as a decentralized DDoS-for-hire platform. Unlike traditional DDoS attacks, which rely on a centralized command-and-control structure, DDoSia empowers a diverse group of participants to contribute to attacks. Recruitment is done via social media channels like Telegram, where volunteers are equipped with the necessary tools to participate. In exchange, these individuals might receive monetary compensation or ideological satisfaction, further blurring the lines between hacktivism and state-sponsored cyber warfare. However, an interesting point is their loyalty check mechanisms for international recruits.
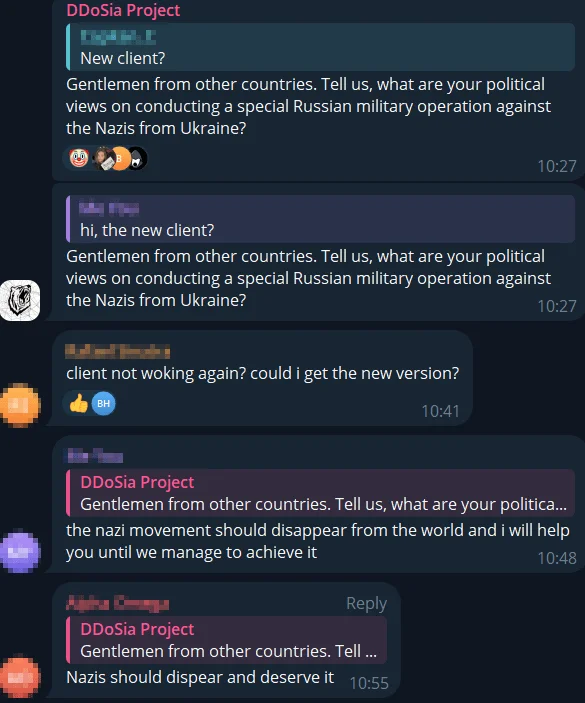
International participants were asked about their political views before further contact
Despite their strange way of checking loyalty, they may still get many international recruits as well. This decentralized model allows DDoSia to scale attacks rapidly, making it particularly dangerous. The project’s primary targets have included government websites, financial institutions, and critical infrastructure in nations that oppose Russia’s geopolitical interests. The attacks are designed to disrupt services, create economic damage, and foster a sense of instability—objectives that align closely with Russia’s broader strategic goals.
Explosive Growth and Evolution in 2024
The year 2024 has seen a significant evolution in DDoSia’s operational scope. Currently, with over 10,000 active users contributing to its DDoS campaigns according to their Telegram channel followers. This surge is partly due to Russia’s hacktivist alignments. These hacktivist groups, which did not have full coordination in the past year, began to act more jointly, especially with Ukraine’s counter offensive. Many significant Russian hacktivist groups like Cyber Army of Russia Reborn take part in NoName’s operations as of today.
The collective is ever growing
Moreover, DDoSia has expanded its focus beyond Ukrainian targets to include NATO member states and other Western countries. This shift reflects the group’s ambition to disrupt the operations of governments and organizations that support Ukraine in its ongoing conflict with Russia. The attacks are not only more frequent but also more complex, with multi-vector strategies that combine different types of DDoS techniques, making them harder to defend against.
An example was Spain. Spanish police have arrested three suspects linked to the pro-Russian hacker group NoName057(16), which is known for conducting distributed denial-of-service (DDoS) attacks against Ukraine’s allies. The arrests took place in Manacor, Huelva, and Seville, where police seized devices and other evidence from the suspects’ residences.
The suspects are believed to be involved in DDoS attacks targeting public institutions and strategic sectors in Spain and other NATO countries that support Ukraine. NoName057(16) emerged following Russia’s invasion of Ukraine in 2022 and has gained notoriety for its short-lived but disruptive DDoS attacks, often carried out by a large number of volunteers using a custom toolkit called DDoSia.
Spanish authorities have described NoName as one of the most active groups targeting Ukraine and its allies. While the investigation is ongoing, the police have not disclosed details about the suspects or other potential members of the group according to the news.
In response, NoName057(16) denied the arrests and accused the Spanish police of a “witch hunt.” The group claimed they are feared by EU and US authorities and vowed to launch a massive cyberattack on Spain’s internet infrastructure. Shortly after, the group published a list of alleged victims in Spain, and for many days the targeting of Spain by Russian groups continued.
The Technical Backbone of DDoSia
DDoSia, the proprietary tool employed by NoName057(16), is at the core of the group’s DDoS campaigns, enabling widespread participation in their cyber operations. Originally designed to facilitate distributed denial-of-service (DDoS) attacks, DDoSia has undergone significant updates that have enhanced its capabilities and broadened its appeal to a wide range of users, including those with minimal technical skills.
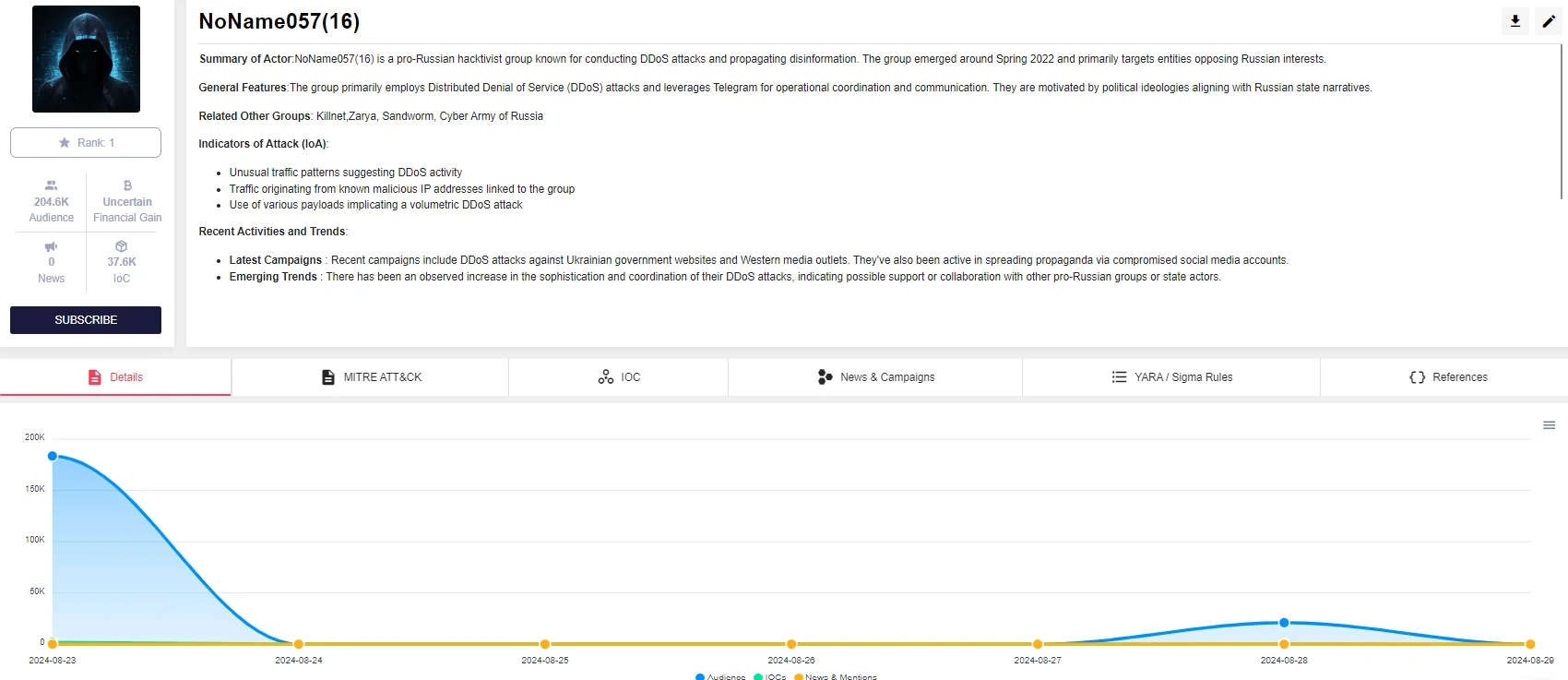
Threat actor intelligence for NoName057(16) on SOCRadar Platform
At its core, DDoSia functions by allowing users to generate and direct large volumes of junk traffic toward specified targets, overwhelming their servers and causing service disruptions. The tool’s architecture is modular, which allows the NoName057(16) group to frequently update it with new features and optimizations, making it more effective and harder to defend against. This modularity also simplifies the deployment of DDoSia across a variety of platforms, increasing the group’s operational flexibility.
One of the most critical aspects of DDoSia is its accessibility. The tool is designed to be user-friendly, enabling individuals without deep technical expertise to participate in complex cyberattacks. This ease of use is a strategic advantage for NoName057(16), as it allows the group to quickly mobilize a large base of volunteers who can contribute to their operations with minimal guidance. This is particularly evident in the way DDoSia integrates with communication platforms and social media, where NoName057(16) recruits and coordinates volunteers to target specific websites.
Moreover, DDoSia’s continuous evolution reflects NoName057(16)’s adaptability in response to cybersecurity defenses. The group has implemented behavioral shifts within the tool to counteract common mitigation strategies used by target organizations. This includes the introduction of more sophisticated attack vectors and the ability to switch between different attack modes, making it difficult for defenders to predict and counter the attacks effectively.
In summary, DDoSia is more than just a DDoS attack tool—it is a versatile and evolving platform that embodies NoName057(16)’s strategy of leveraging mass participation in cyber warfare.
What is to Come?
DDoSia’s rise underscores the growing role of cyberattacks in modern geopolitical conflicts. As state-sponsored and affiliated hacktivist groups become more sophisticated, the risk to global cybersecurity increases. The DDoSia project exemplifies how cyber warfare is evolving, with state-affiliated actors like NoName057(16) using relatively simple yet effective tools to achieve strategic objectives.
The success of DDoSia also highlights the need for enhanced cybersecurity measures, particularly in sectors that are frequent targets of such attacks. Governments and businesses alike must adapt to this new threat landscape, investing in advanced defense mechanisms capable of withstanding the scale and complexity of attacks orchestrated by projects like DDoSia.
In conclusion, the DDoSia project represents a significant escalation in the use of DDoS attacks as a tool of political warfare. Its growth and sophistication in 2024 make it a critical threat that requires a concerted response from the global cybersecurity community.
Explore the Threat Actors and Their Tactics With SOCRadar
SOCRadar’s Operational Intelligence Trends Dashboard delivers unparalleled, real-time insights to strengthen your defense strategies. Track the rise and fall of major ransomware groups, pinpoint geographical trends in threat actor activities, and focus on high-risk regions with precision. The dashboard also provides detailed threat reports, offering a broader view of the evolving threat landscape.
Check your domain’s DoS Resilience with SOCRadar Labs for free
In addition, it highlights the most frequently exploited vulnerabilities by cybercriminals, providing foresight into potential attack vectors. Stay updated on recent victims and ongoing campaigns to maintain an edge over threats. With SOCRadar, you gain critical intelligence to navigate today’s complex cyber threat environment. For more in-depth analysis and continuous updates, visit our Threat Actors page and enhance your cybersecurity posture.





































