
10 Essential Strategies to Protect Your Business from Cyber Threats
In today’s digital age, businesses are increasingly exposed to a growing number of cyber threats. The complexity and frequency of these attacks are rising, impacting organizations of all sizes. This is where Cyber Threat Intelligence (CTI) comes into play. CTI allows businesses to take a proactive stance by identifying, analyzing, and mitigating risks before they become significant issues. With CTI, companies gain early insights into emerging threats, empowering them to strengthen their defenses.
As cyber threats continue to rise, it’s essential to take a closer look at some of the risks businesses face. For instance, in 2023, MGM Resorts and in 2022, NVIDIA both fell victim to ransomware attacks. These types of attacks not only result in financial losses but also lead to operational disruptions and reputational damage.
The potential financial impact of these attacks is substantial. According to IBM’s 2024 Cost of a Data Breach Report, the global average cost of a data breach in 2024 reached $4.88 million. The following chart illustrates the upward trend in the cost of data breaches over recent years:
These costs encompass more than just data recovery; they also include customer loss, fines, and compensation. For more detailed information and statistics, you can refer to our IBM’s 2024 Cost of a Data Breach Report.
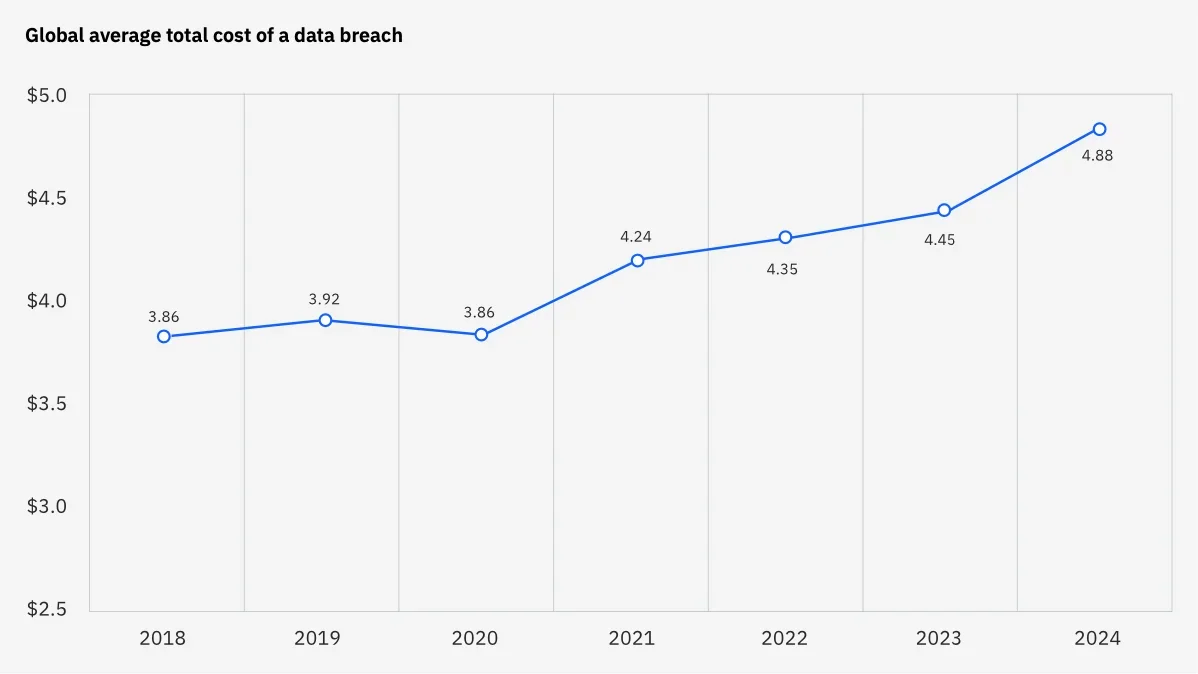
Global Average Total Cost of a Data Breach – Source: IBM Cost of a Data Breach 2024
Here are 10 crucial strategies to protect your business from cyber threats:
1. Implement Cyber Threat Intelligence (CTI) Solutions
Cyberattacks are occurring more often, and attackers are employing increasingly advanced techniques. With the rising frequency and sophistication of cyber threats, it is crucial for businesses to implement Cyber Threat Intelligence (CTI) solutions. These tools empower organizations by providing insights into potential attacks, monitoring the evolving threat landscape, and offering early warnings. By leveraging CTI, businesses can stay ahead of advanced cyber threats and fortify their defenses in real time.
2. Real-Time Threat Detection
Early detection of cyber threats is critical to minimizing damage, but simply having a detection system isn’t enough. With the rising complexity of attacks, real-time threat detection must be agile and deeply integrated into the organization’s infrastructure. By continuously monitoring systems for abnormal behaviors such as irregular login attempts or unapproved file transfers, real-time detection tools can pinpoint threats before they escalate. A notable example is the 2023 MOVEit data breach, where attackers exploited vulnerabilities and exfiltrated sensitive information. Had there been a more robust real-time detection system in place, earlier intervention could have limited the damage. SOCRadar’s Extended Threat Intelligence product offers an Threat Hunting module that continuously monitors and detects threats with proactive alerts, enabling faster responses to potential attacks.
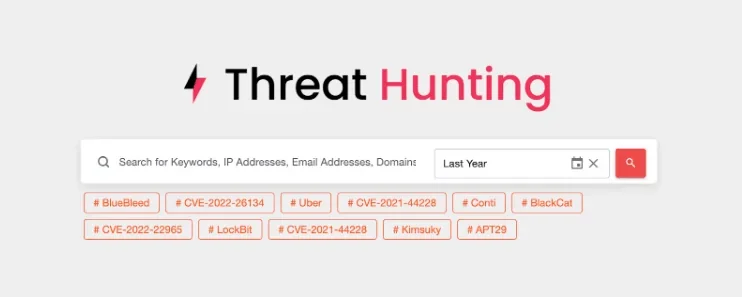
SOCRadar Threat Hunting Module
3. Securing the Supply Chain
The importance of securing your supply chain cannot be overstated, especially in an era where third-party attacks are growing more frequent. A notable example is the SolarWinds breach, which exploited supply chain weaknesses to compromise thousands of businesses. Supply Chain Security involves not just monitoring your own network but also evaluating the cyber hygiene of vendors and partners. Without such evaluations, you may be exposed to risks outside of your control. With SOCRadar’s Supply Chain Intelligence product, businesses can gain deep visibility into the security posture of their partners, helping identify and mitigate vulnerabilities across the entire supply chain ecosystem.
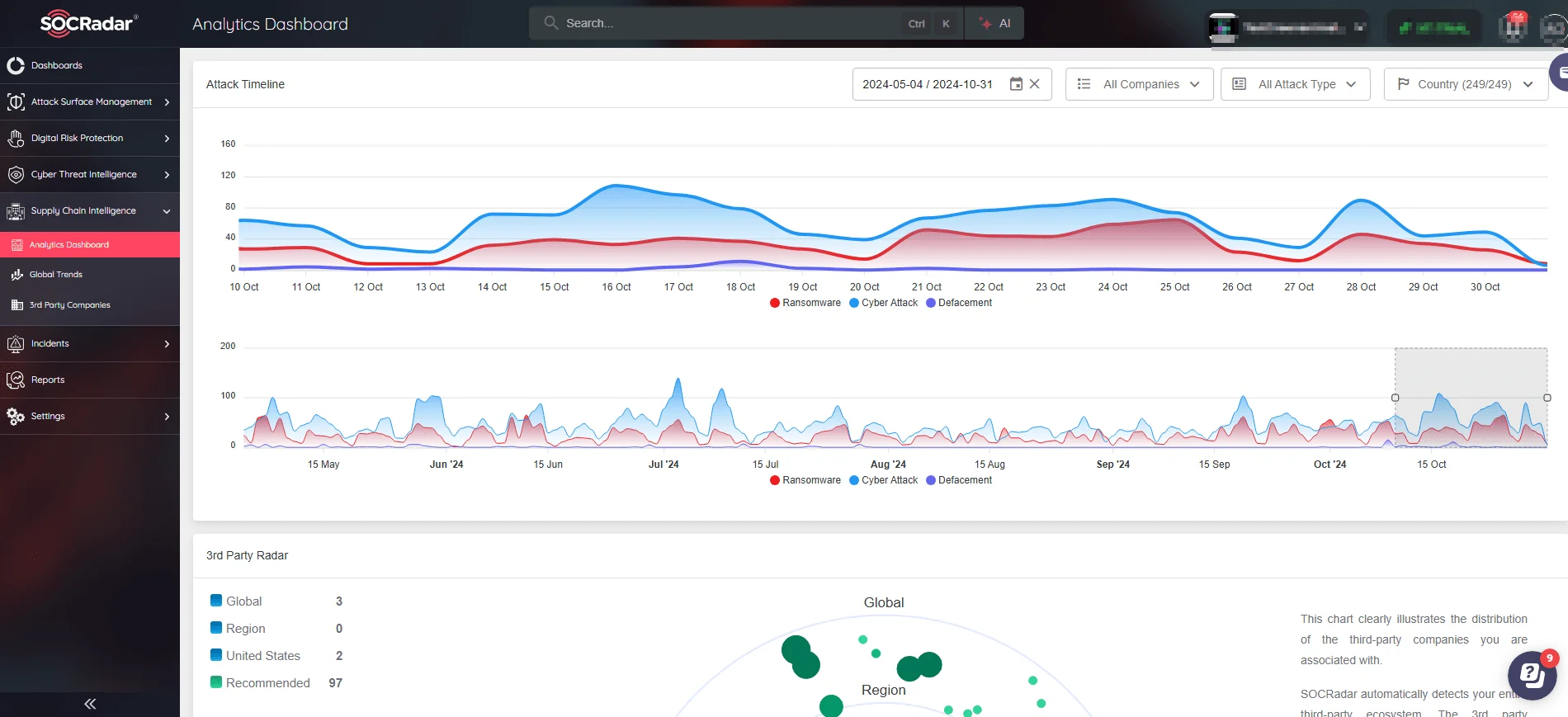
Analytics Dashboard in SOCRadar’s Supply Chain module
4. Regular Security Assessments
Cybersecurity is never a “set it and forget it” practice. Regular security assessments are critical to ensuring your defenses evolve as threats do. These assessments help businesses uncover latent vulnerabilities, some of which can be exploited by sophisticated attackers. A comprehensive assessment also provides a fresh perspective on internal risks that might go unnoticed. For instance, the infamous Equifax breach could have been prevented with better vulnerability assessments. SOCRadar’s External Threat Assessment report provides an in-depth review of potential vulnerabilities and weaknesses, helping businesses stay one step ahead of attackers by offering actionable insights based on real-time intelligence.
Free External Threat Assessment Report from SOCRadar Labs
5. Implementing Access Controls
Access control systems are essential for protecting sensitive data, but traditional methods are no longer sufficient. Modern threats like privilege escalation attacks can exploit weak access controls. A recent example is the Okta breach, where attackers leveraged weak access policies to infiltrate systems. Implementing strong Identity and Access Management (IAM) practices can help limit unauthorized access. SOCRadar’s Attack Surface Management product works alongside IAM solutions, providing businesses with comprehensive insights into access points, monitoring abnormal behaviors, and ensuring that access policies are enforced across all systems.
6. Keeping Systems Updated
One of the most common yet avoidable causes of cyberattacks is outdated software. Attackers often exploit known vulnerabilities in unpatched systems, as seen in the WannaCry ransomware attack, which took advantage of organizations failing to update their software. System updates should be a top priority, and businesses must implement automated patch management to avoid these risks. SOCRadar’s Brand Protection solution can be integrated with your patch management systems, offering insights into which patches are most critical based on real-time threat intelligence.
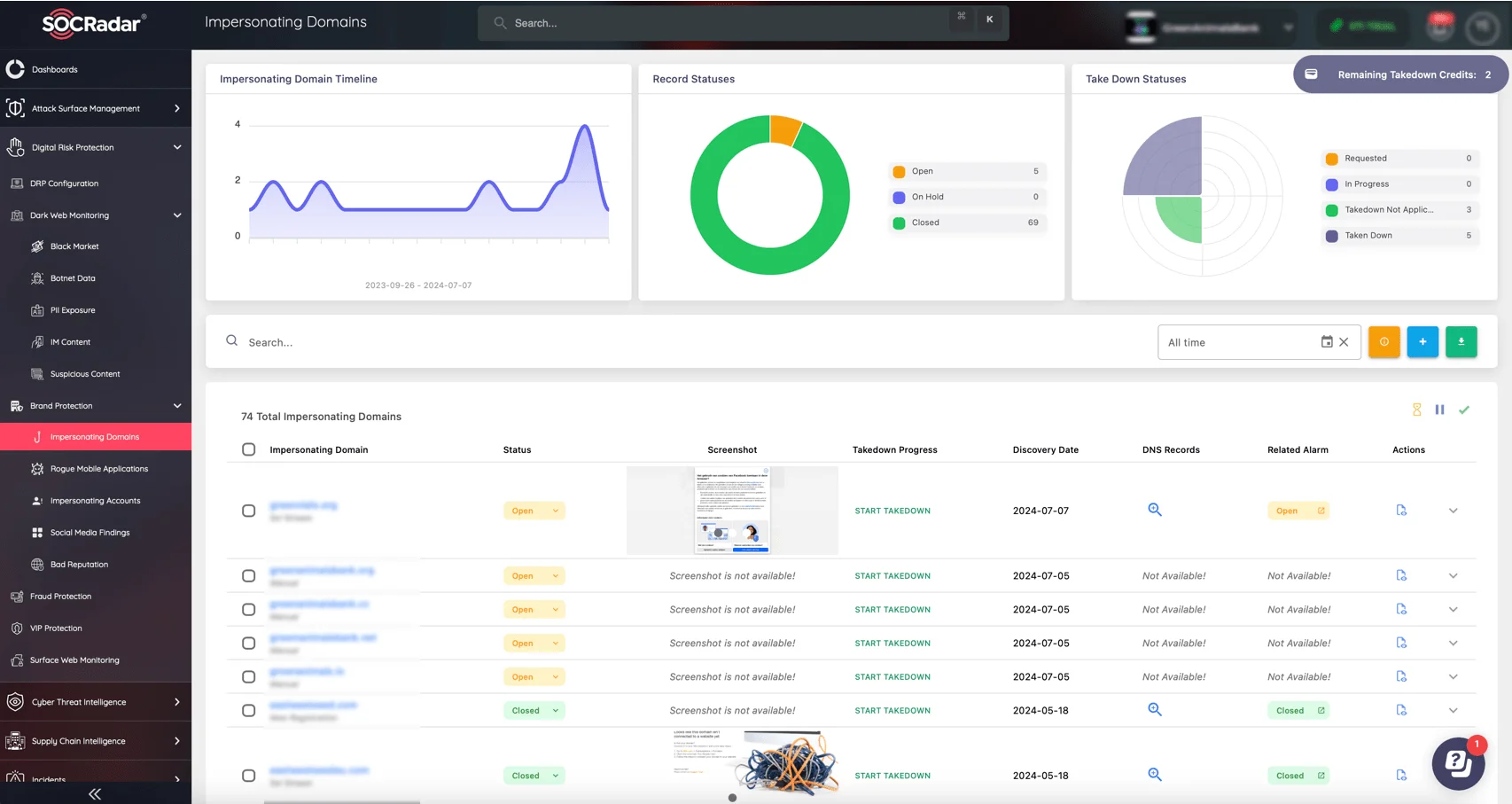
SOCRadar Brand Protection Module
7. Monitoring Vulnerabilities
Tracking vulnerabilities is no longer just a periodic exercise—it must be continuous. A lapse in monitoring can result in devastating attacks, such as the Apache Log4j vulnerability that affected thousands of organizations. Vulnerability tracking tools allow businesses to stay ahead of newly discovered vulnerabilities. SOCRadar’s Vulnerability Intelligence module offers advanced vulnerability monitoring and real-time alerts, providing businesses with the necessary information to address critical issues before they are exploited by attackers.
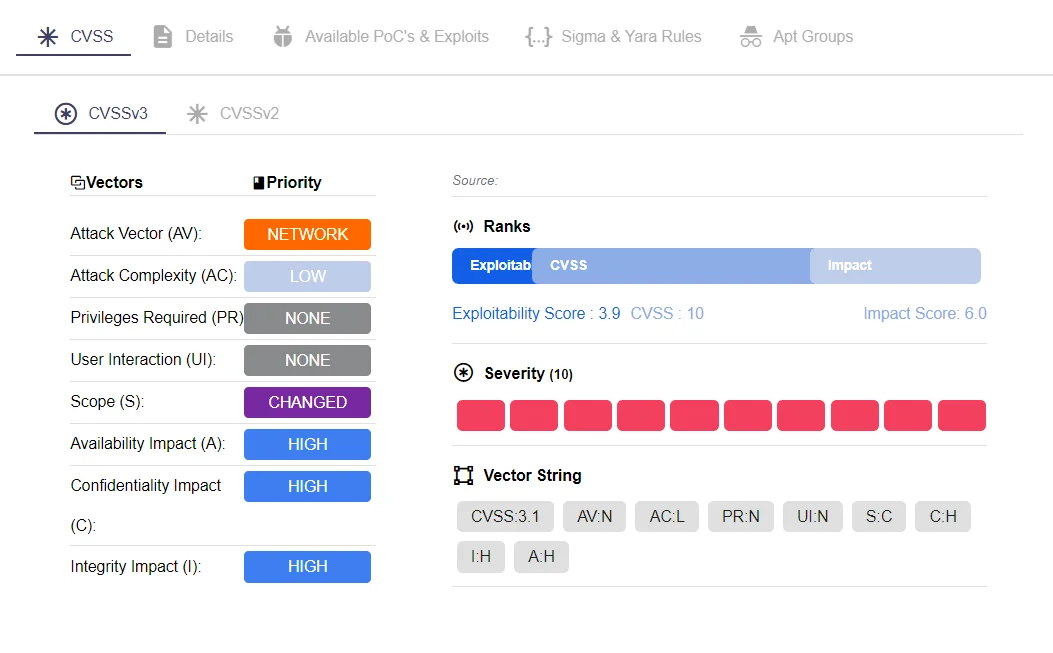
Insights into Exploited Vulnerabilities From SOCRadar
8. Creating an Incident Response Plan
Despite the best preventative measures, cyber incidents will happen, and having a comprehensive Incident Response Plan is vital. The plan should outline step-by-step actions to take when a breach occurs, ensuring roles and responsibilities are clear. The Colonial Pipeline ransomware attack in 2021 highlighted the importance of having a robust incident response plan, as delays in response can exacerbate the impact. SOCRadar’s Incident Response Support integrates directly into your workflows, helping businesses quickly mitigate the impact of cyberattacks by offering real-time guidance and intelligence.
9. Employee Training and Awareness
Human error remains one of the leading causes of cybersecurity breaches, with phishing and social engineering tactics becoming more sophisticated. Training programs must go beyond basic knowledge and continuously educate employees on evolving threats. A notable case is the 2020 Twitter hack, where attackers exploited employee credentials via social engineering tactics. SOCRadar’s Advanced Certified Training Programs are designed to help businesses educate their workforce, reducing risks from phishing, social engineering, and other human-related vulnerabilities by providing ongoing and up-to-date training modules.

SOCRadar Advanced Certified Training Program
10. Digital Risk Protection (DRP)
As businesses increasingly rely on digital platforms, they become more vulnerable to external threats such as brand impersonation, phishing attacks, and data leaks on the dark web. Digital Risk Protection (DRP) is essential for monitoring and mitigating these risks by providing visibility into threats that extend beyond your internal systems. For example, during the recent Marriott data breach, sensitive customer information was leaked on the dark web, highlighting the importance of proactive monitoring. SOCRadar’s Digital Risk Protection product continuously monitors the surface, deep, and dark web for mentions of your brand, credentials, and intellectual property, offering actionable alerts to help businesses mitigate external threats before they cause harm.

SOCRadar Digital Risk Protection
Conclusion: Enhancing Your Cybersecurity Strategy
As cyber threats continue to grow in complexity, businesses need to be proactive in their defense strategies. Cyber Threat Intelligence (CTI) can help strengthen your organization’s security posture by providing early detection and insights into emerging threats. By implementing these strategies, you can build a robust defense against cyber threats and safeguard your organization’s digital assets.
Every business has unique security needs, so it’s essential to regularly review your cybersecurity approach and adjust it to address specific challenges. Investing in CTI solutions and following these key practices will help protect your business in today’s rapidly evolving cyber landscape. Free Threat Intelligence for Cyber Security Professionals. Ready to Start? Get free access now and arm yourself with actionable, contextualized intelligence.
Also, would you like to check out our Free Dark Web Report? Then find out how popular you are on the dark web.




































