
MOVEit Data Leak Exposes Employee Data of Amazon, HSBC & More – What You Need to Know
[Update] December 10, 2024: “Nam3L3ss Denies Cl0p Ties While Highlighting Avaddon’s 2020 Data on American Bank Systems”
[Update] December 4, 2024: “Alleged Cl0p-Linked Leaks Continue with Release of Patient Records from 17 Organizations”
[Update] December 3, 2024: “Threat Actor Releases JLL Data, Claims to Target Other Major Companies”
[Update] December 2, 2024: “Bank of America Allegedly Targeted in Leak Linked to a Cl0p Ransomware Breach”
A new wave of data leaks tied to the infamous MOVEit vulnerability has rattled the cybersecurity landscape once again. Different from last year’s Cl0p ransomware-led attacks, this latest MOVEit data leak is attributed to a new threat actor, “Nam3L3ss.” Targeting major organizations, this actor has released vast amounts of sensitive employee data on a Dark Web forum.
Among the affected organizations are notable names like Amazon, HSBC, British Telecom, and McDonald’s. Altogether, the leaked records reveal sensitive employee directories, spanning thousands of entries per company, containing contact information, job titles, and even internal structures.
For affected organizations, the threat is real and significant: this level of exposure provides a potential roadmap for attackers aiming to exploit the stolen data in future targeted phishing campaigns or other social engineering attacks.
In this article, we will outline the key details of the breach, affected organizations and the threat actor’s claims, and examine possible implications.
What Happened? Background of the MOVEit Data Leak
The recent data breach attributed to the threat actor “Nam3L3ss” unfolded on the well-known hacking forum, BreachForums. Through a series of posts, Nam3L3ss exposed extensive employee directories, including personal details, organizational hierarchies, and additional internal files.
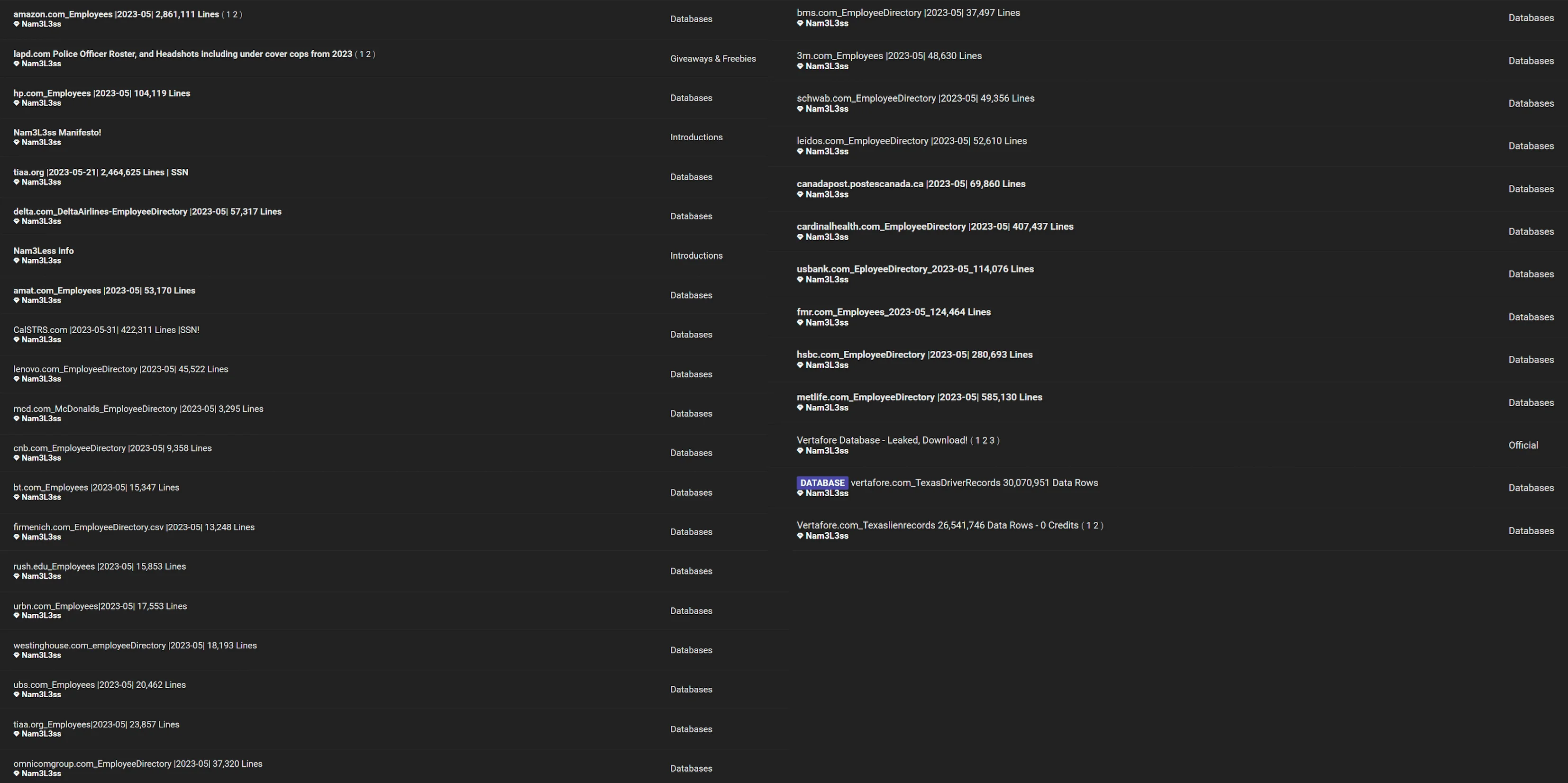
The leak posts by the threat actor, including the latest MOVEit related databases
On November 8, 2024, SOCRadar’s Dark Web News module alerted our customers to the threat actor’s leak-related posts. According to the details shared in these posts, the data source is MOVEit, suggesting that the data exposure leverages the same MOVEit Transfer vulnerability exploited in last year’s Cl0p ransomware attacks.
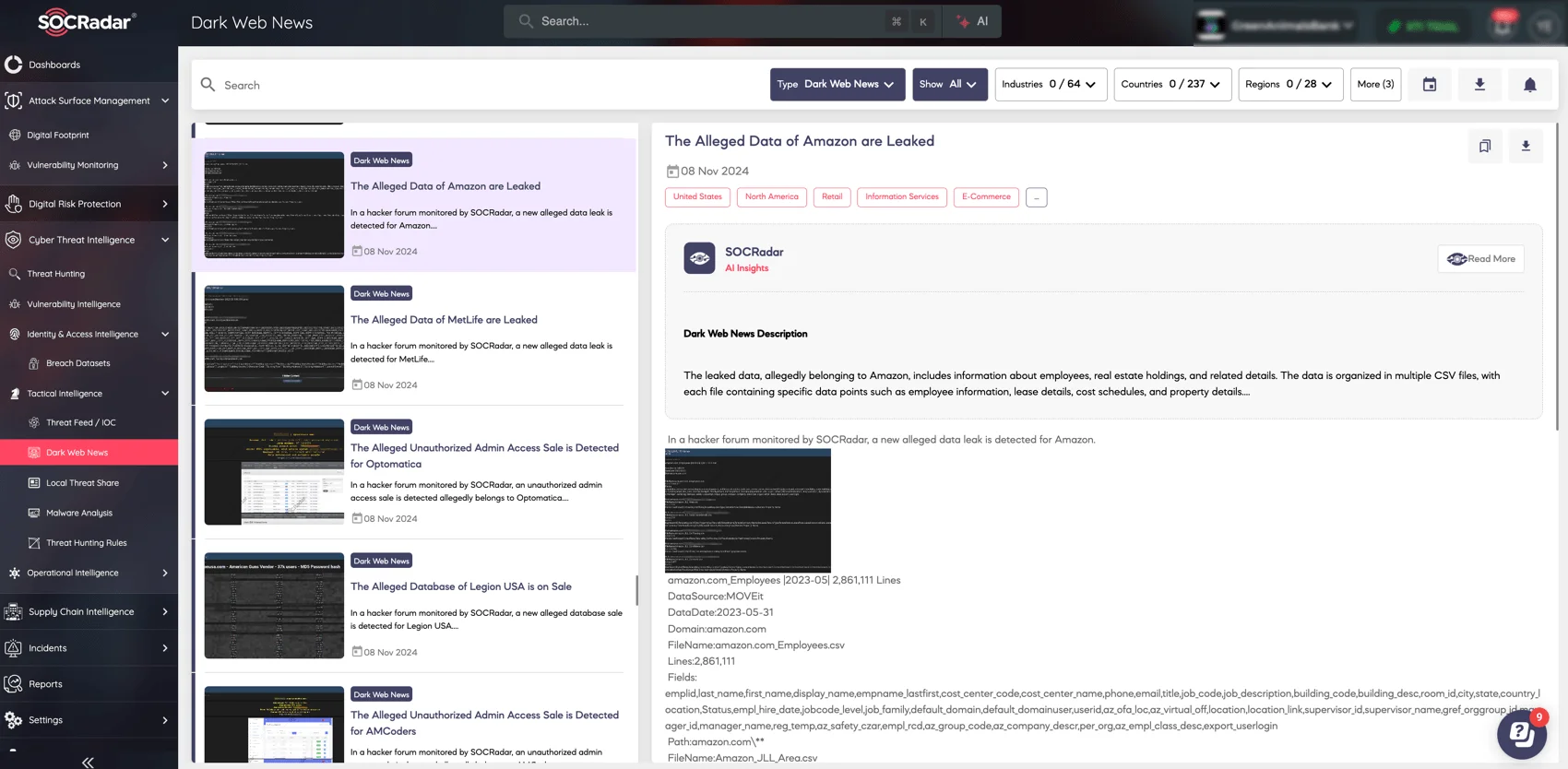
The leak posts, viewed on SOCRadar’s Dark Web News module
In the latest leaks by Nam3l3ss, affected entities reportedly include industry leaders like Amazon, HSBC, MetLife, Cardinal Health, Fidelity, U.S. Bank, HP, Canada Post, Delta Airlines, Leidos, Lenovo, McDonald’s, and others. Following these high-profile leaks, customers of the affected organizations could face an increased risk of social engineering and fraud schemes.
Also notably, while the breach spans many companies, data leaks have been verified for Amazon and HSBC, where HR/accountant records have been exposed, but no customer information appears to have been compromised. It was assessed that these breaches occurred around May 31, 2023.
Leaks Tied to the MOVEit Vulnerability (CVE-2023-34362); Is Nam3l3ss Related to Clop Ransomware?
This latest breach appears tied to the critical MOVEit Transfer vulnerability identified in 2023, designated CVE-2023-34362, which allowed unauthorized access by bypassing security controls in the file transfer software. Exploited by various threat actors in the past (such as Cl0p and LockBit), this flaw has impacted major industries worldwide.
Nam3L3ss lists MOVEit as the data source in their posts, leading researchers to suggest that the vulnerability might be involved in this exposure. However, it’s still uncertain if Nam3L3ss directly exploited MOVEit themselves or leveraged data exposed by earlier attackers.
An Infostealers blog further details that while the notorious Cl0p ransomware group previously used this exploit, many companies in this breach, such as Amazon and McDonald’s, were not previously associated with Cl0p. Additionally, in the threat actor’s “manifesto,” they deny any connection to ransomware groups, claiming instead to expose systemic security weaknesses; they also state they are not a hacker.
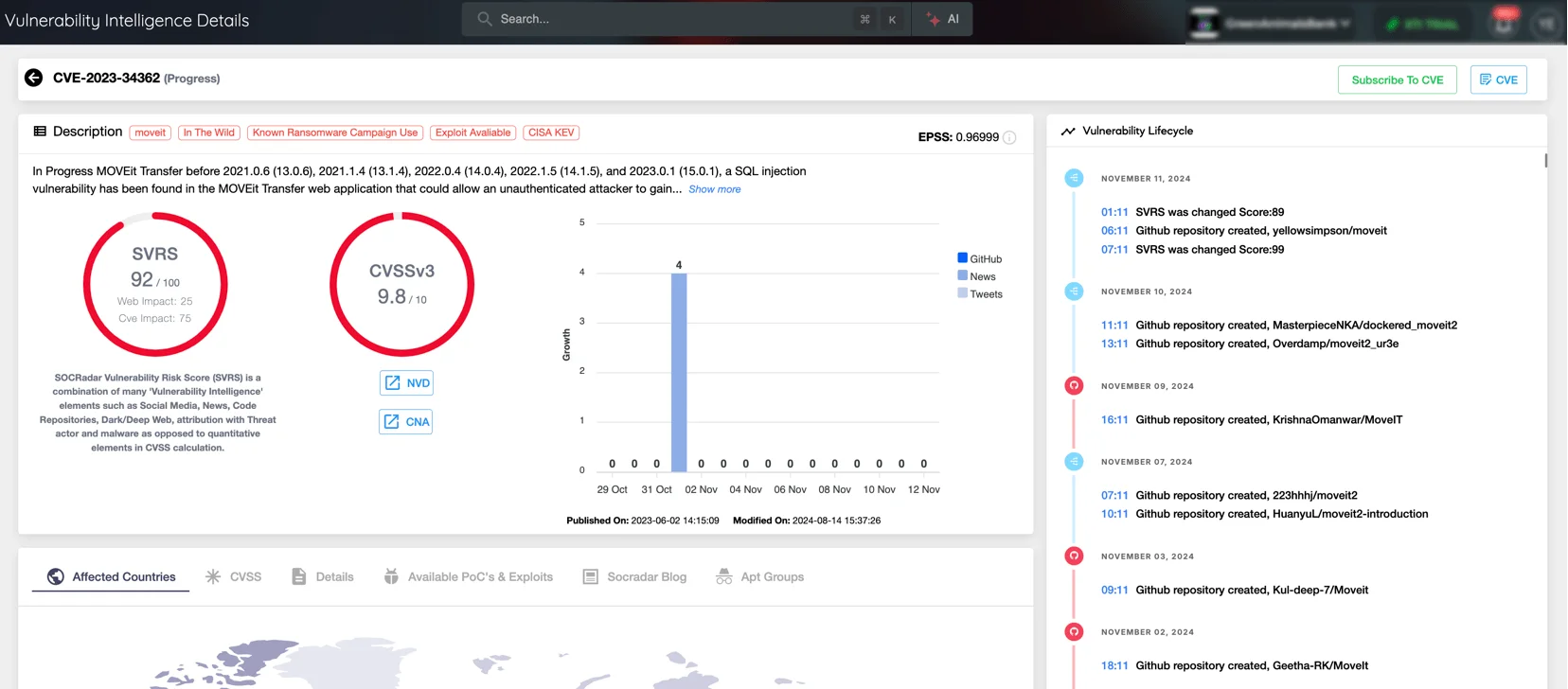
Details of CVE-2023-34362 (Source: SOCRadar Vulnerability Intelligence)
For the latest insights into vulnerabilities like CVE-2023-34362 in MOVEit Transfer and emerging threats, SOCRadar’s Vulnerability Intelligence module provides detailed updates on active CVEs and threat trends.
Threat Actor’s Intentions and Approach – A Self-Described Watcher, Not Hacker
In the manifesto we mentioned, which was released alongside the data leak, Nam3L3ss claims they do not actively hack organizations but “simply monitor the dark web and exposed online cloud services.”
Denying the title of ‘hacker’, Nam3L3ss said they target misconfigured and publicly accessible cloud storage services such as AWS buckets, Google Cloud, and FTP servers, along with open databases on platforms like MongoDB.
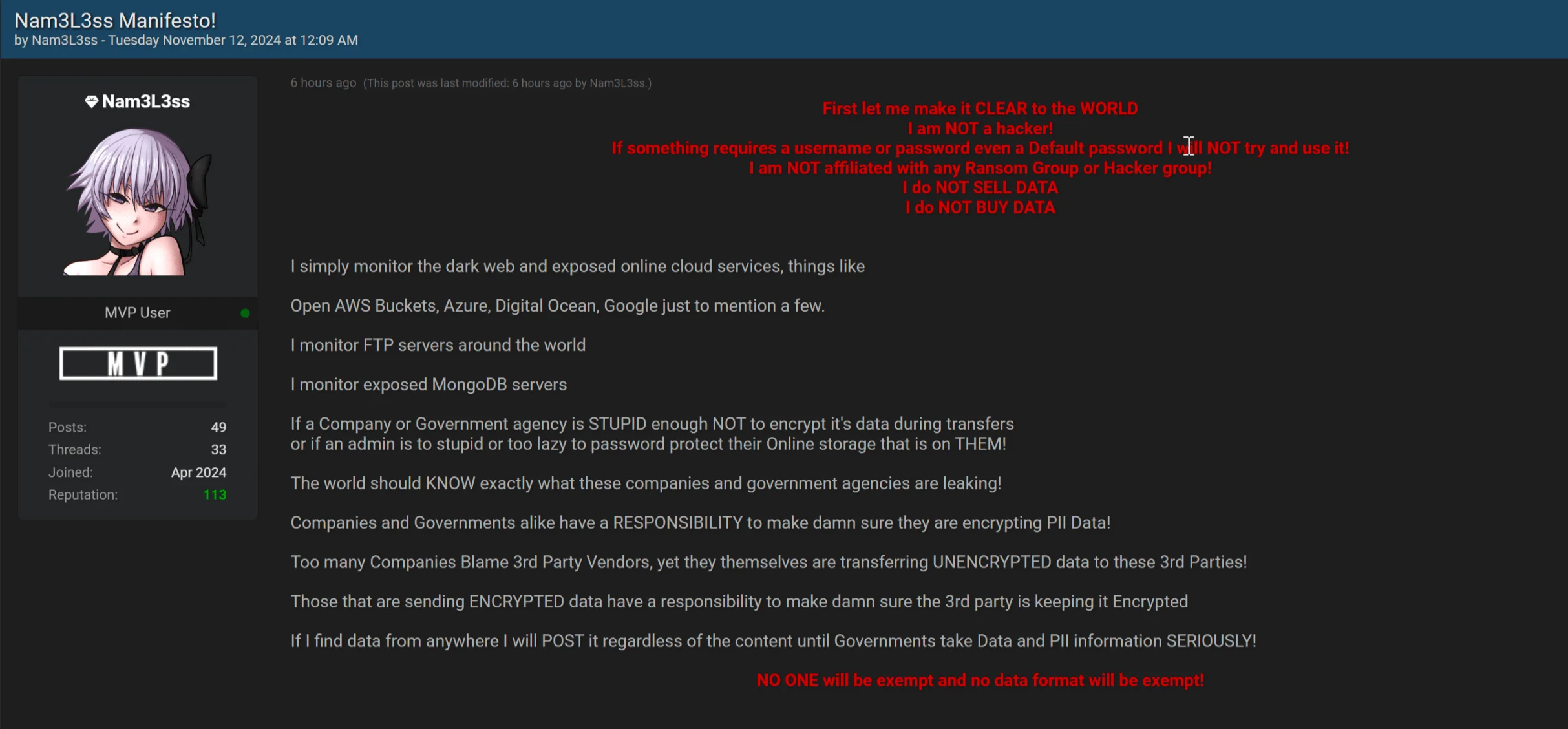
A manifesto posted by the threat actor along MOVEit data leak posts
The manifesto further notes a blame game, as Nam3L3ss argues that if companies or government agencies fail to secure sensitive information through encryption or other safeguards, they are responsible for any breaches that occur, not their third-parties. They insist they will continue to post any unprotected data they find “until governments take data and PII security seriously.”
In light of the MOVEit data leak, SOCRadar’s Dark Web Monitoring module offers your organization a proactive edge by keeping tabs on such threats on Dark Web forums, markets, and underground networks. With timely alerts, you’ll know immediately if sensitive information or assets tied to your brand surface in Dark Web spaces. Here are the key features of SOCRadar’s Dark Web Monitoring module:
- Instant Threat Alerts: Get notified whenever your organization’s assets are mentioned on the dark web.
- Compromised Credential Detection: Stay aware of exposed credentials linked to your company.
- Early Data Breach Indicators: Spot warning signs to prevent unauthorized access before it becomes a larger issue.
With these capabilities, SOCRadar helps you stay ahead, safeguarding your organization from emerging dark web threats and protecting your brand’s reputation.
Top Companies Impacted by the Recent MOVEit Leaks
Among the compromised organizations, the following companies have the highest number of exposed records, each surpassing 100,000 entries:
| Company | Records Exposed |
| Amazon | 2,861,111 |
| MetLife | 585,130 |
| Cardinal Health | 407,437 |
| HSBC | 280,693 |
| Fidelity | 124,464 |
| U.S. Bank | 114,076 |
| HP | 104,119 |
These vast datasets expose employee information on a significant scale, underscoring the depth of this latest breach and heightening concerns over potential exploitation, such as phishing, social engineering, and identity fraud.
Insights from the Amazon and HSBC Data Breaches
As the data leaks from Amazon and HSBC have been confirmed, the scope of the exposed information reveals significant internal details about both organizations. Researchers authenticated these datasets by cross-referencing email addresses with LinkedIn profiles and other sources.
It was revealed that HSBC’s dataset spans its global operations, including fields such as user IDs, employee names, email addresses, and location details. In parallel, Amazon’s dataset contains information like employee names, contact details, job titles, and internal department codes—exposing sensitive organizational structures that could be vulnerable to social engineering attacks.
Amazon confirmed the breach on November 11, 2024, clarifying that only work-related contact information was compromised, with no exposure of Social Security numbers (SSNs) or financial data.
Bank of America Allegedly Targeted in Leak Linked to a Cl0p Ransomware Breach
The threat actor behind the recent MOVEit leaks, Nam3L3ss, has made a new claim on the hacker forum, this time alleging a breach involving Bank of America. According to their post, over 288,000 rows of sensitive employee information have been exposed. The data reportedly includes numerous files and potential intelligence on the bank.
What’s more concerning is that the threat actor stated that Bank of America’s data would be leaked for free after January 20, 2025, putting pressure on the company.
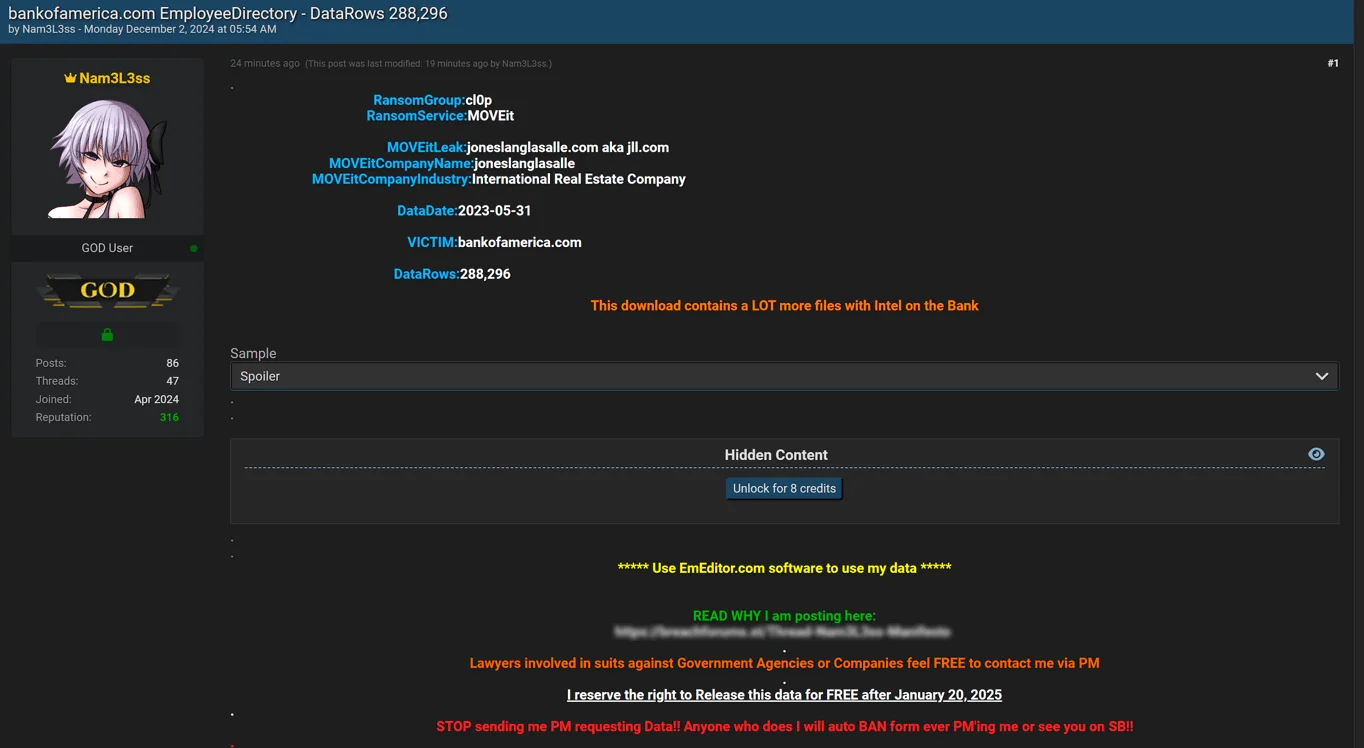
Threat actor claims to leak data from bankofamerica.com Employee Directory
Nam3L3ss maintains their stance of not being a hacker and links this latest breach to a previous one by the Cl0p ransomware group, which targeted Jones Lang LaSalle (JLL), a U.S.-based international real estate company. The data is dated May 31, 2023.
It remains unclear how the threat actor accessed Bank of America’s employee information via JLL’s breach. However, if confirmed, this breach may highlight ongoing third-party security issues.
In their post, the threat actor also requests forum users to stop sending private messages asking for data, implying their data leaks are in high demand. This heightened interest could add pressure to organizations already dealing with previous security breaches.
Threat Actor Releases JLL Data, Claims to Target Other Major Companies
As of December 2, 2024, the threat actor behind the recent MOVEit leaks has expanded their activities, releasing data allegedly belonging to Jones Lang LaSalle (JLL). According to their post, the first part of this release contains 12,352,524 rows of data from 73 files, organized in original directories.
They noted that the data includes numerous employee directories with domains like jll.com and others. Despite some files being deemed less desirable by general users, the threat actor emphasized their appeal to those interested in commercial property intelligence.
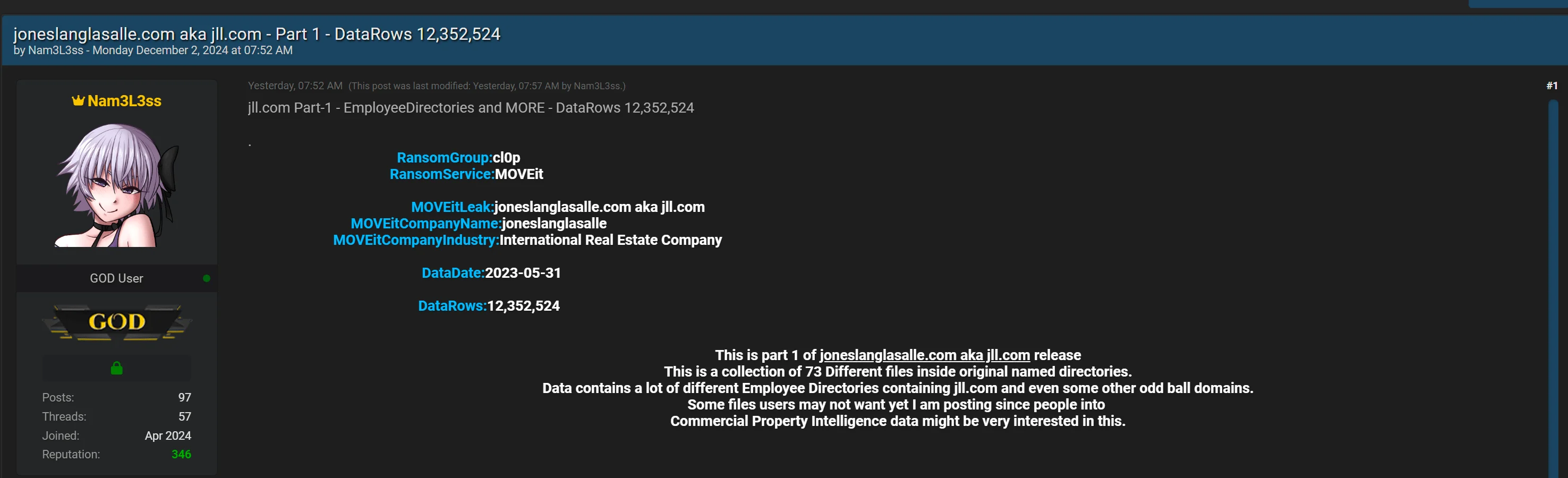
Threat actor’s post about jll.com
The released data is dated May 31, 2023, and is again linked to the Cl0p ransomware group, similar to the breach claims concerning Bank of America.
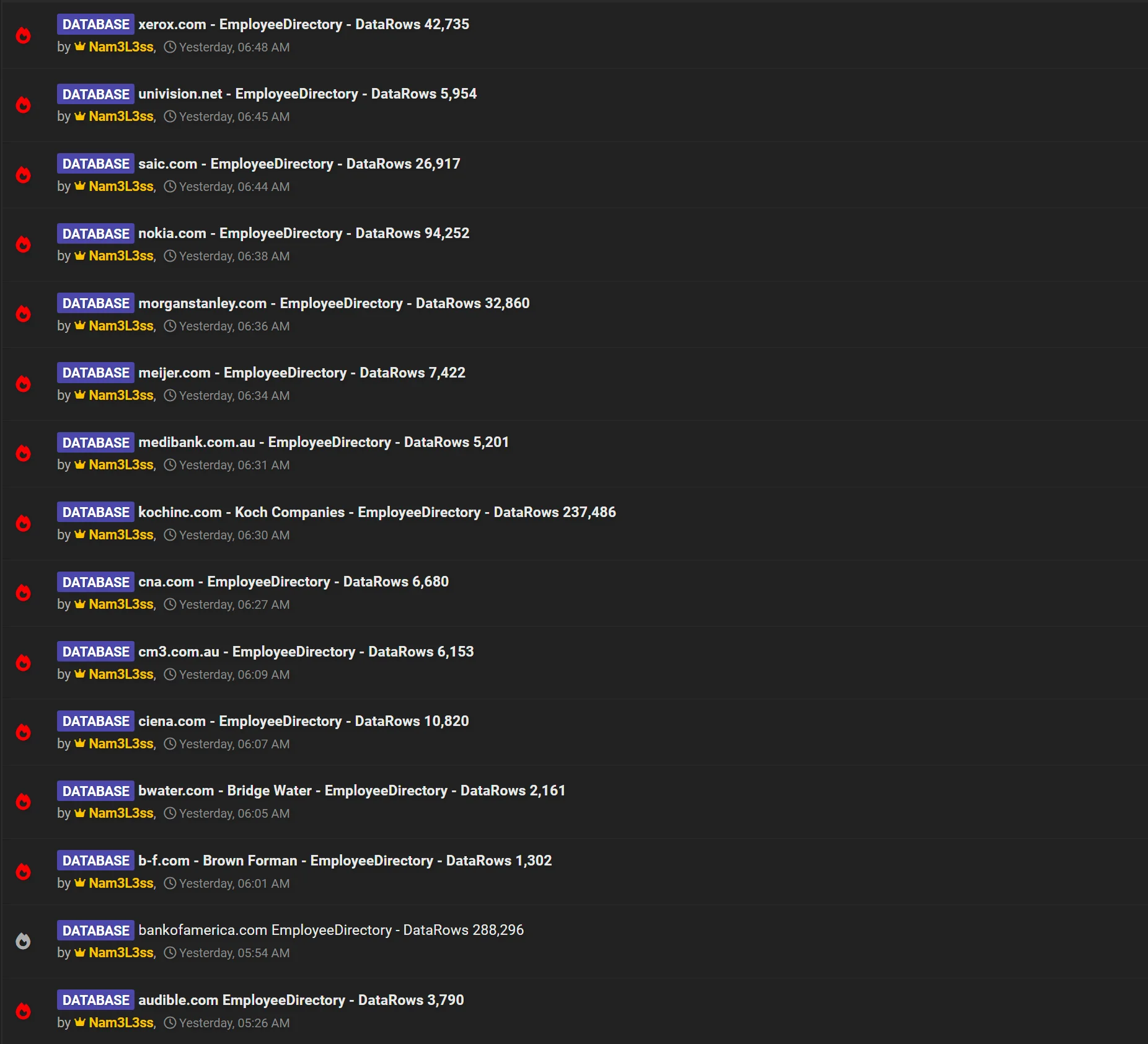
The threat actor’s recent posts on the hacker forum
In the last 24 hours, the threat actor has also posted additional employee directory data reportedly from major companies, including:
- Audible (audible.com)
- Brown Forman (b-f.com)
- Bridgewater (bwater.com)
- Ciena (ciena.com)
- CM3 (cm3.com.au)
- CNA (cna.com)
- Koch Companies (kochinc.com)
- Medibank (medibank.com.au)
- Meijer (meijer.com)
- Morgan Stanley (morganstanley.com)
- Nokia (nokia.com)
- SAIC (saic.com)
- Univision (univision.com)
- Xerox (xerox.com)
Alleged Cl0p-Linked Leaks Continue with Release of Patient Records from 17 Organizations
SOCRadar has detected new activity by the threat actor Nam3L3ss, who alleges to have exposed sensitive patient and employee health data from 17 additional organizations.
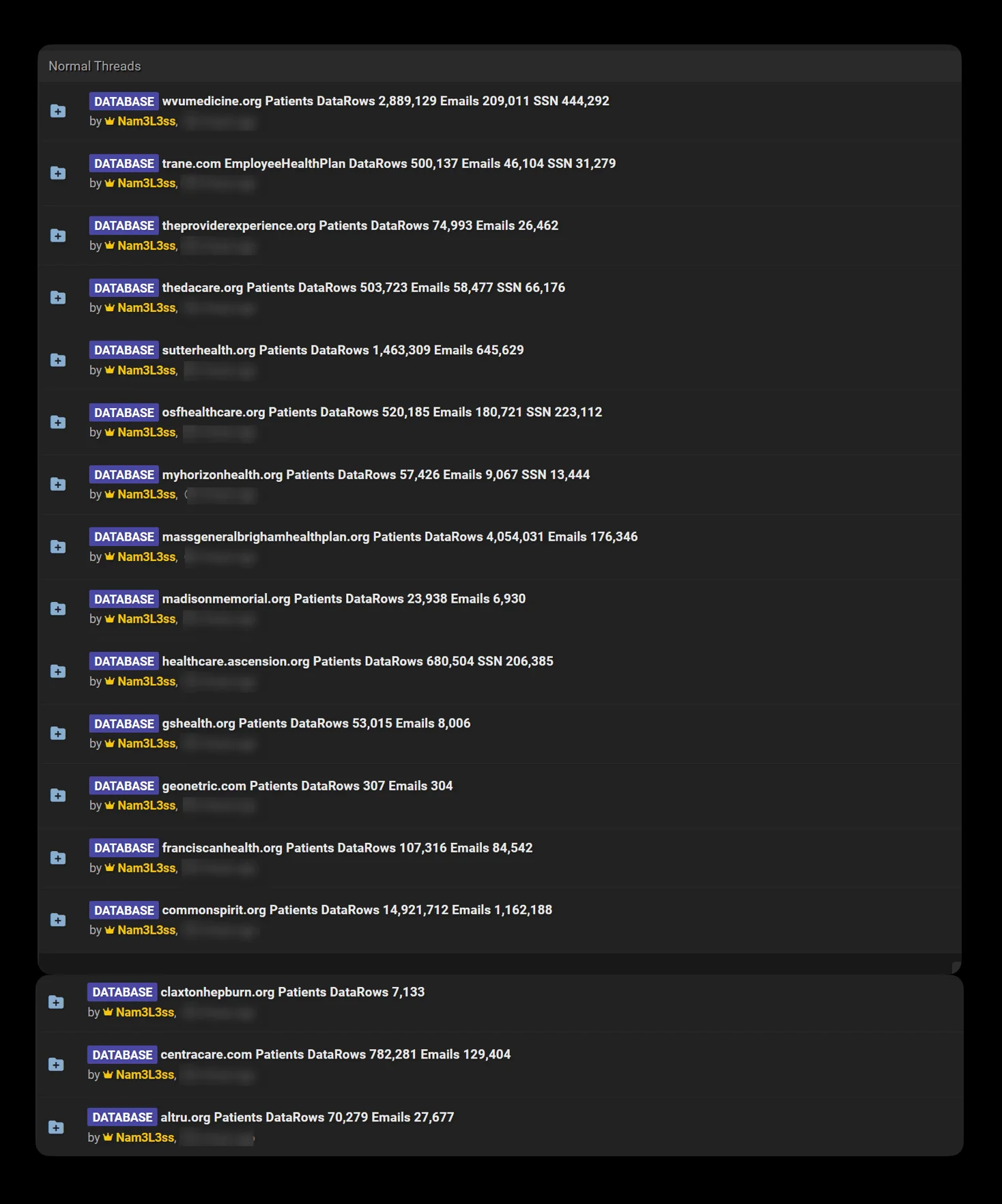
List of additional companies involved in data leaks
The leaked data includes millions of patient records, email addresses, and Social Security Numbers (SSNs), presenting significant risks to both the organizations and impacted individuals. Alarmingly, the data allegedly features over 14 million patient records from multiple entities. Here is the list of companies involved:
- WVU Medicine (wvumedicine.org)
- Trane (trane.com)
- The Provider Experience (theproviderexperience.org)
- ThedaCare (thedacare.org)
- Sutter Health (sutterhealth.org)
- OSF Healthcare (osfhealthcare.org)
- My Horizon Health (myhorizonhealth.org)
- Mass General Brigham Health Plan (massgeneralbrighamhealthplan.org)
- Madison Memorial (madisonmemorial.org)
- Ascension Healthcare (healthcare.ascension.org)
- GS Health (gshealth.org)
- Geonetric (geonetric.com)
- Franciscan Health (franciscanhealth.org)
- CommonSpirit (commonspirit.org)
- Claxton-Hepburn (claxtonhepburn.org)
- CentraCare (centracare.com)
- Altru Health System (altru.org)
While some organizations reportedly faced leaks involving over 4 million records, others saw smaller subsets of patient or employee data exposed.
Nam3L3ss Denies Cl0p Ties While Highlighting Avaddon’s 2020 Data on American Bank Systems
In a new post on December 9, 2024, the threat actor Nam3L3ss, tied to the recent MOVEit data leaks, denied involvement with the Cl0p ransomware group, asserting instead that they only “download their stuff.”
Nam3L3ss also stated that they are working on a data release from the Avaddon ransomware group’s activity in 2020, showcasing a database tied to American Bank Systems, Inc. Despite the data’s age, the actor emphasizes its continued value.
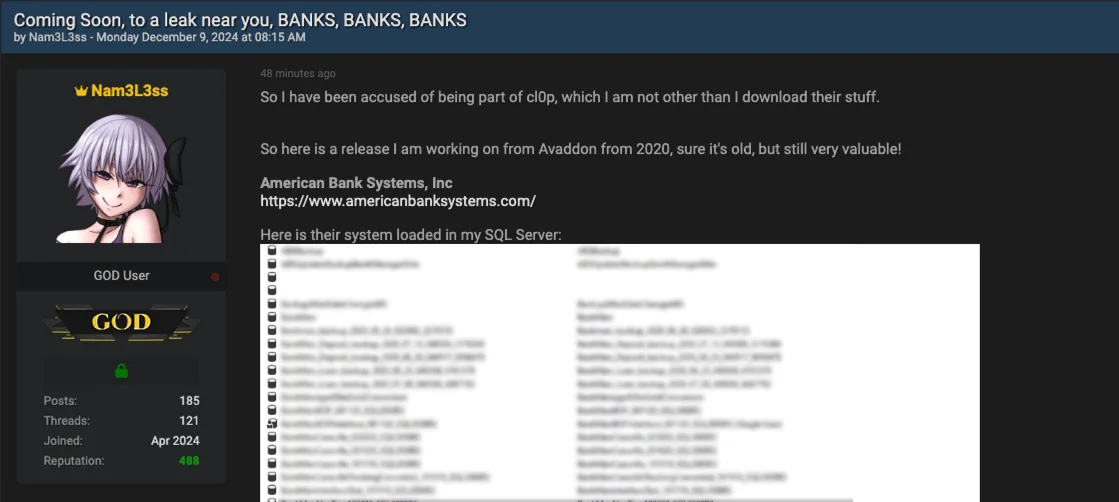
Nam3L3ss denies Cl0p affiliation while showcasing a database tied to Avaddon’s 2020 activity
The post includes screenshots of an SQL server loaded with files allegedly linked to American Bank Systems, leading to concerns about the longevity and residual risks of previously leaked ransomware data.
Nam3L3ss’s public denial of any Cl0p affiliation aligns with their self-proclaimed role as a “watcher” rather than an active hacker, though this release suggests ongoing leverage of past ransomware operations to maintain influence.
Conclusion
The recent MOVEit data leaks pose serious risks for the affected companies, exposing them to potential phishing attacks, fraud schemes, and social engineering tactics that malicious actors can exploit using the stolen employee information. With sensitive internal details such as employee names, contact information, and more now accessible, cybercriminals have the resources needed to craft highly targeted phishing campaigns and impersonation attempts, putting both employees and company data at risk.
The reputational damage following such breaches can be significant. High-profile companies like Amazon and HSBC could face increased scrutiny, as these incidents undermine public trust and raise questions about their data security measures.
To further protect against these risks, companies must employ proactive monitoring and defensive measures. SOCRadar’s Brand Protection service, served under the Digital Risk Protection (DRP) module provides a comprehensive defense, tracking potential impersonators across domains, mobile apps, and social media platforms.
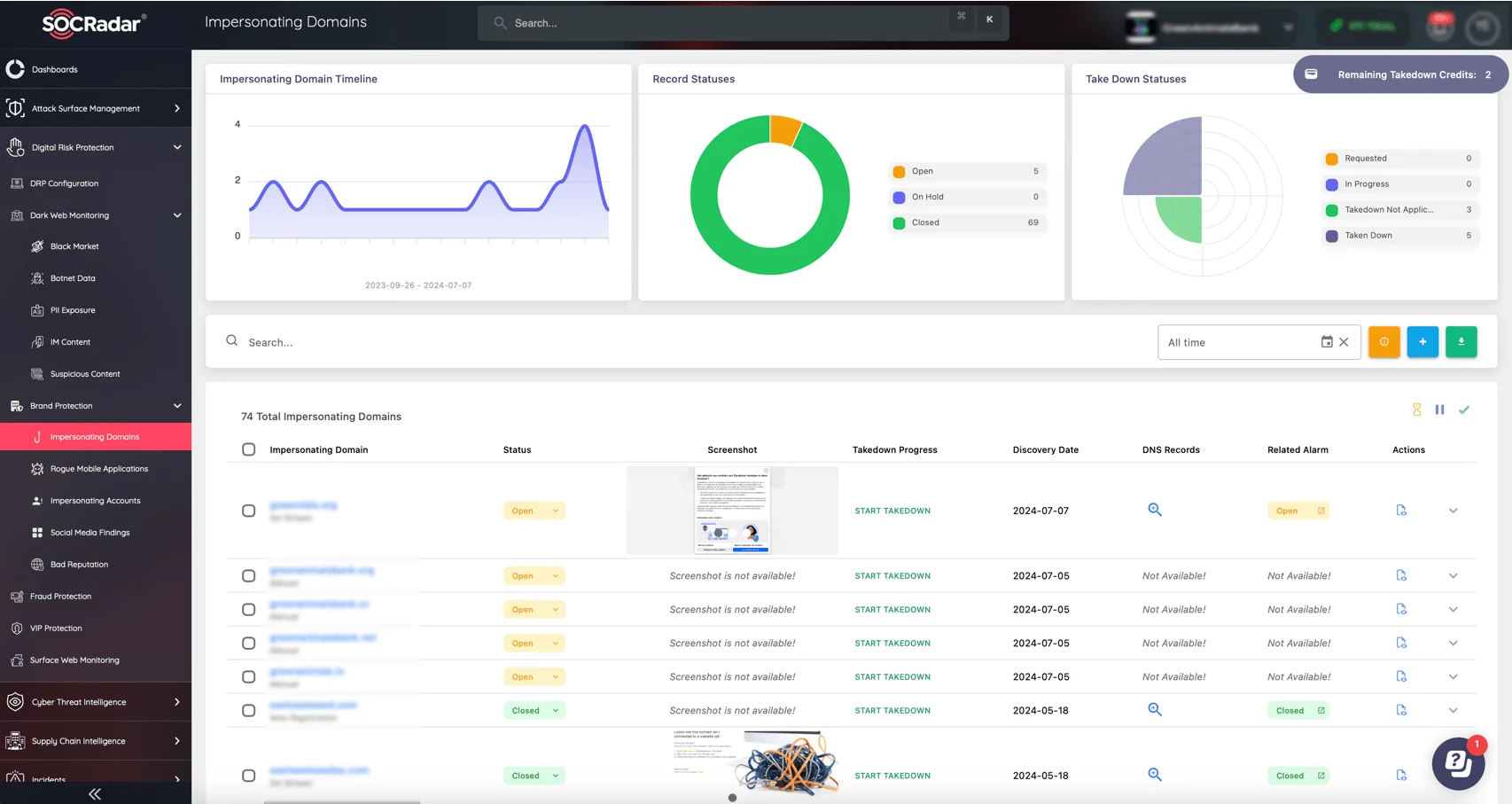
Track phishing and fraud attempts with SOCRadar’s Brand Protection
This tool helps your organization identify fake accounts, phishing schemes, and fraud attempts, as well as neutralize them with the Integrated Takedown feature, reducing the likelihood of successful social engineering attacks. In today’s threat landscape, leveraging these protective measures is essential to maintaining customer trust and resilience against targeted attacks.




































