
Top Software Weaknesses of 2024 by MITRE (Critical Insights for Every Organization)
The 2024 CWE Top 25 Most Dangerous Software Weaknesses list provides an essential roadmap for identifying the most pervasive and severe software flaws in modern systems. Published by MITRE in collaboration with the Department of Homeland Security (DHS) in November 2024, the list highlights vulnerabilities that can lead to significant security risks if left unaddressed.

Top 25 CWE – Most Dangerous Software Weaknesses
By analyzing recent data and evolving threats, this annual report guides developers, security teams, and organizations toward better mitigation strategies. With a focus on prioritizing these weaknesses, the 2024 list serves as a vital resource for improving software security, reducing risks, and protecting digital environments. In this blog, we’ll explore the insights from the 2024 CWE Top 25, focusing on key trends and notable changes to provide critical insights for your organization.
Overview of the Top 25 CWE List
The 2024 CWE Top 25 list highlights critical software weaknesses by analyzing vulnerabilities published between June 2023 and June 2024. The process involved extensive data collection, scoping, and scoring to ensure precision and relevance. This year’s dataset included over 31,000 CVE records, narrowed down through a comprehensive review that corrected high-level mappings and normalized data to improve accuracy.
Collaborating with experts from hundreds of CVE Numbering Authorities (CNAs), the CWE Team ensured that mapping discrepancies were addressed where possible, enhancing the reliability of the final dataset.
Below is the 2024 list of the CWE Top 25 Most Dangerous Software Weaknesses, showcasing the latest rankings, therefore offering insights into the vulnerabilities that demand immediate attention from organizations worldwide.
| Rank | ID | Name | Score | Rank Change vs. 2023 |
| 1 | CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) | 56.92 | +1 |
| 2 | CWE-787 | Out-of-bounds Write | 45.20 | -1 |
| 3 | CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) | 35.88 | 0 |
| 4 | CWE-352 | Cross-Site Request Forgery (CSRF) | 19.57 | +5 |
| 5 | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) | 12.74 | +3 |
| 6 | CWE-125 | Out-of-bounds Read | 11.42 | +1 |
| 7 | CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) | 11.30 | -2 |
| 8 | CWE-416 | Use After Free | 10.19 | -4 |
| 9 | CWE-862 | Missing Authorization | 10.11 | +2 |
| 10 | CWE-434 | Unrestricted Upload of File with Dangerous Type | 10.03 | 0 |
| 11 | CWE-94 | Improper Control of Generation of Code (‘Code Injection’) | 7.13 | +12 |
| 12 | CWE-20 | Improper Input Validation | 6.78 | -6 |
| 13 | CWE-77 | Improper Neutralization of Special Elements used in a Command (‘Command Injection’) | 6.74 | +3 |
| 14 | CWE-287 | Improper Authentication | 5.94 | -1 |
| 15 | CWE-269 | Improper Privilege Management | 5.22 | +7 |
| 16 | CWE-502 | Deserialization of Untrusted Data | 5.07 | -1 |
| 17 | CWE-200 | Exposure of Sensitive Information to an Unauthorized Actor | 5.07 | +13 |
| 18 | CWE-863 | Incorrect Authorization | 4.05 | +6 |
| 19 | CWE-918 | Server-Side Request Forgery (SSRF) | 4.05 | 0 |
| 20 | CWE-119 | Improper Restriction of Operations within the Bounds of a Memory Buffer | 3.69 | -3 |
| 21 | CWE-476 | NULL Pointer Dereference | 3.58 | -9 |
| 22 | CWE-798 | Use of Hard-coded Credentials | 3.46 | -4 |
| 23 | CWE-190 | Integer Overflow or Wraparound | 3.37 | -9 |
| 24 | CWE-400 | Uncontrolled Resource Consumption | 3.23 | +13 |
| 25 | CWE-306 | Missing Authentication for Critical Function | 2.73 | -5 |
The ranking of CWEs on this list relies on a scoring formula that evaluates both the frequency of a weakness and its average severity when exploited. By combining these factors, the list emphasizes weaknesses that are both prevalent and impactful. This approach helps organizations identify vulnerabilities that pose the greatest risk and prioritize their mitigation efforts effectively.
In addition to traditional metrics like CVSS scores, most commonly used being CVSSv3 and the latest version CVSSv4, SOCRadar’s Vulnerability Risk Scoring (SVRS) provides an innovative alternative for prioritizing threats.
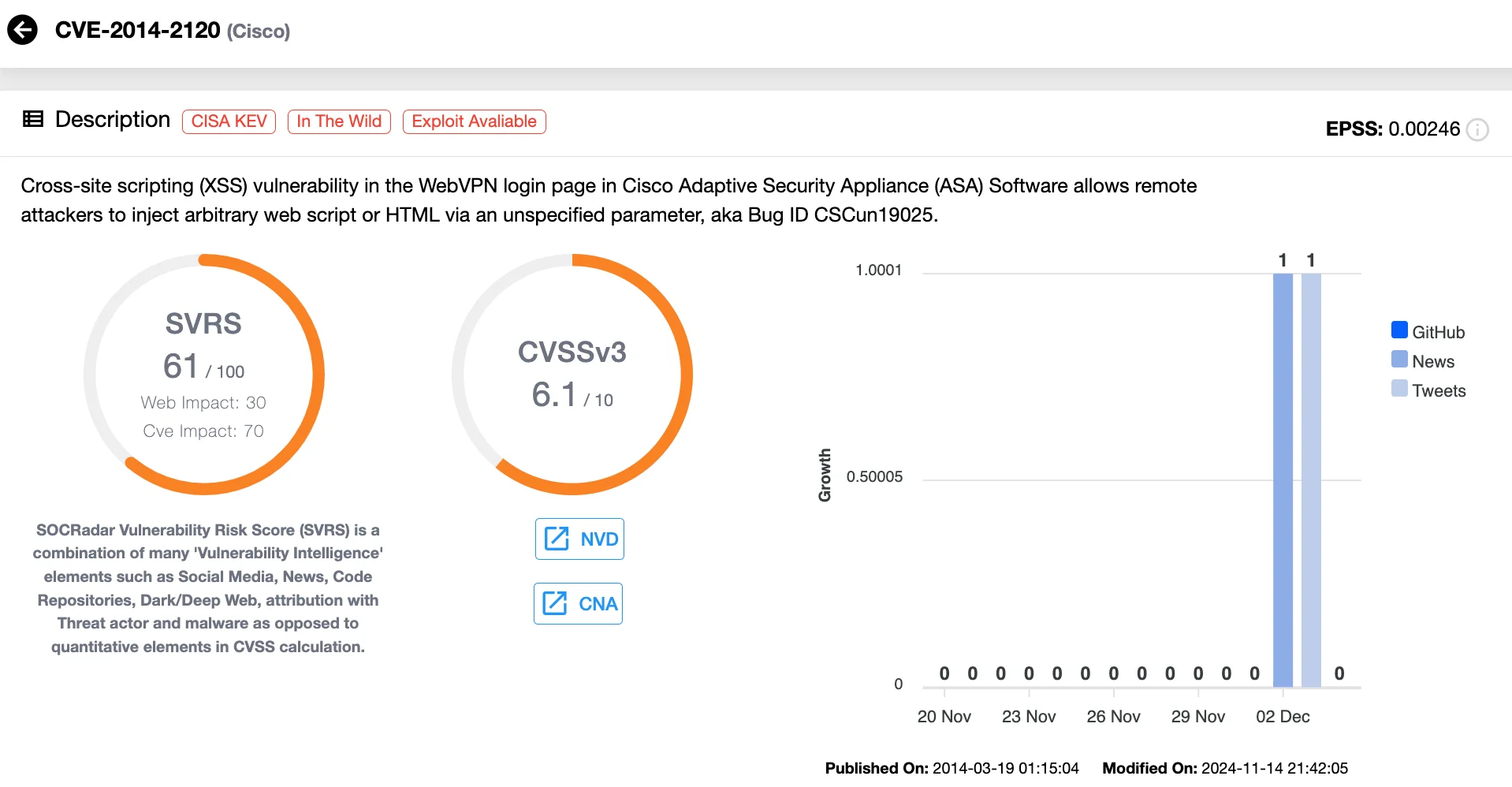
SVRS score shown on a SOCRadar vulnerability card (for the recently exploited CVE-2014-2120 flaw in Cisco)
Every CVE card on SOCRadar’s Vulnerability Intelligence module highlights the SVRS score, integrating elements like Social Media, News, Code Repositories, Dark Web activity, and threat actor attribution for a broader context compared to CVSS’s quantitative approach.
Comparison with the Previous Year (CWEs from 2023 to 2024)
The 2024 CWE Top 25 list reflects a dynamic landscape of software weaknesses, with significant shifts in rankings compared to 2023. Let’s explore the most notable rank changes, from weaknesses that climbed significantly to those that fell or dropped off the list entirely.
Several weaknesses made notable upward moves, underscoring their growing relevance:
- CWE-352: Cross-Site Request Forgery (CSRF) rose from 9th to 4th place. This rise emphasizes the increasing focus on web application vulnerabilities as more services move online. Exploits targeting CSRF can bypass user authentication, potentially leading to unauthorized actions.
- CWE-94: Improper Control of Generation of Code (‘Code Injection’) jumped 12 spots to 11th place. Its rise reflects growing concerns about weaknesses exploited during software development or runtime environments, where injecting harmful code remains a significant risk.
- CWE-269: Improper Privilege Management moved from 22nd to 15th place. As organizations increasingly rely on complex access controls, mismanagement of privileges becomes a critical attack vector.
- CWE-863: Incorrect Authorization climbed from 24th to 18th. This highlights the rising need to enforce proper role-based access and ensure users operate within their allowed permissions.
Conversely, some weaknesses have seen reduced attention, likely due to improved mitigation strategies or shifts in focus:
- CWE-20: Improper Input Validation dropped six places, from 6th to 12th. While still critical, this decline may reflect better developer practices in validating user inputs.
- CWE-476: NULL Pointer Dereference fell from 12th to 21st. Such vulnerabilities, though serious, are less frequently exploited in newer software.
- CWE-190: Integer Overflow or Wraparound saw a similar decline, dropping from 14th to 23rd, perhaps due to advancements in secure coding techniques and automated testing.
- CWE-306: Missing Authentication for Critical Function slipped five spots, from 20th to 25th, remaining in the list as its last contributor. This could indicate improvements in enforcing basic authentication measures across systems.
Two weaknesses that previously made the list have dropped out entirely:
- CWE-362: Concurrent Execution using Shared Resource (‘Race Condition’), which fell from 21st to 34th.
- CWE-276: Incorrect Default Permissions, dropping from 25th to 36th.
These weaknesses likely saw reduced prevalence or severity in the analyzed dataset, leading to their exclusion.
The list also welcomed two newcomers, reflecting emerging challenges in software security:
- CWE-400: Uncontrolled Resource Consumption, debuting at 24th. This rise signals growing concerns over resource management in increasingly complex systems.
- CWE-200: Exposure of Sensitive Information to an Unauthorized Actor, which entered the 17th position. This underscores the critical importance of protecting sensitive data amid rising data breaches and leaks.
Why These Shifts Matter
The movements in the 2024 CWE rankings illustrate the dynamic nature of software security, shaped by evolving attack methods and the shifting priorities of organizations. Weaknesses like Cross-Site Request Forgery (CSRF) and Code Injection have surged in prominence, likely driven by the increasing reliance on web applications and the complexity of securing them against malicious inputs. As digital systems grow more interconnected, the potential for exploiting these vulnerabilities has expanded, making them critical areas of focus.
A notable riser, Improper Privilege Management (CWE-269), underscores the challenges organizations face with Identity and Access Management (IAM). As more businesses migrate to cloud infrastructures, the complexity of managing user roles and permissions grows exponentially. Misconfigured IAM systems can inadvertently grant unauthorized access, making privilege management a vital security concern. Similarly, Incorrect Authorization (CWE-863) reflects the need for strong role-based access controls to prevent privilege escalation and ensure users operate within their intended boundaries.
On the other hand, the decline of vulnerabilities like NULL Pointer Dereference (CWE-476) and Integer Overflow (CWE-190) suggests that secure coding practices and advanced development tools are proving effective. Automated testing, better static code analysis, and education on secure software development are likely contributing to this shift.
The introduction of newcomers like Uncontrolled Resource Consumption (CWE-400) and Exposure of Sensitive Information (CWE-200) highlights emerging risks tied to resource management and data security. These changes point to the growing importance of protecting sensitive information as data breaches become more frequent and costly. Also, the resource management concerns seen in CWE-400 reflect the challenges of scaling systems efficiently while defending against attacks like Denial of Service (DoS).
To effectively address these dynamic risks, your organization needs reliable monitoring systems that not only detect vulnerabilities but also enable timely and efficient responses with actionable Cyber Threat Intelligence, helping to mitigate threats before they escalate. You can respond to threats faster with precise, real-time alarms provided by SOCRadar.
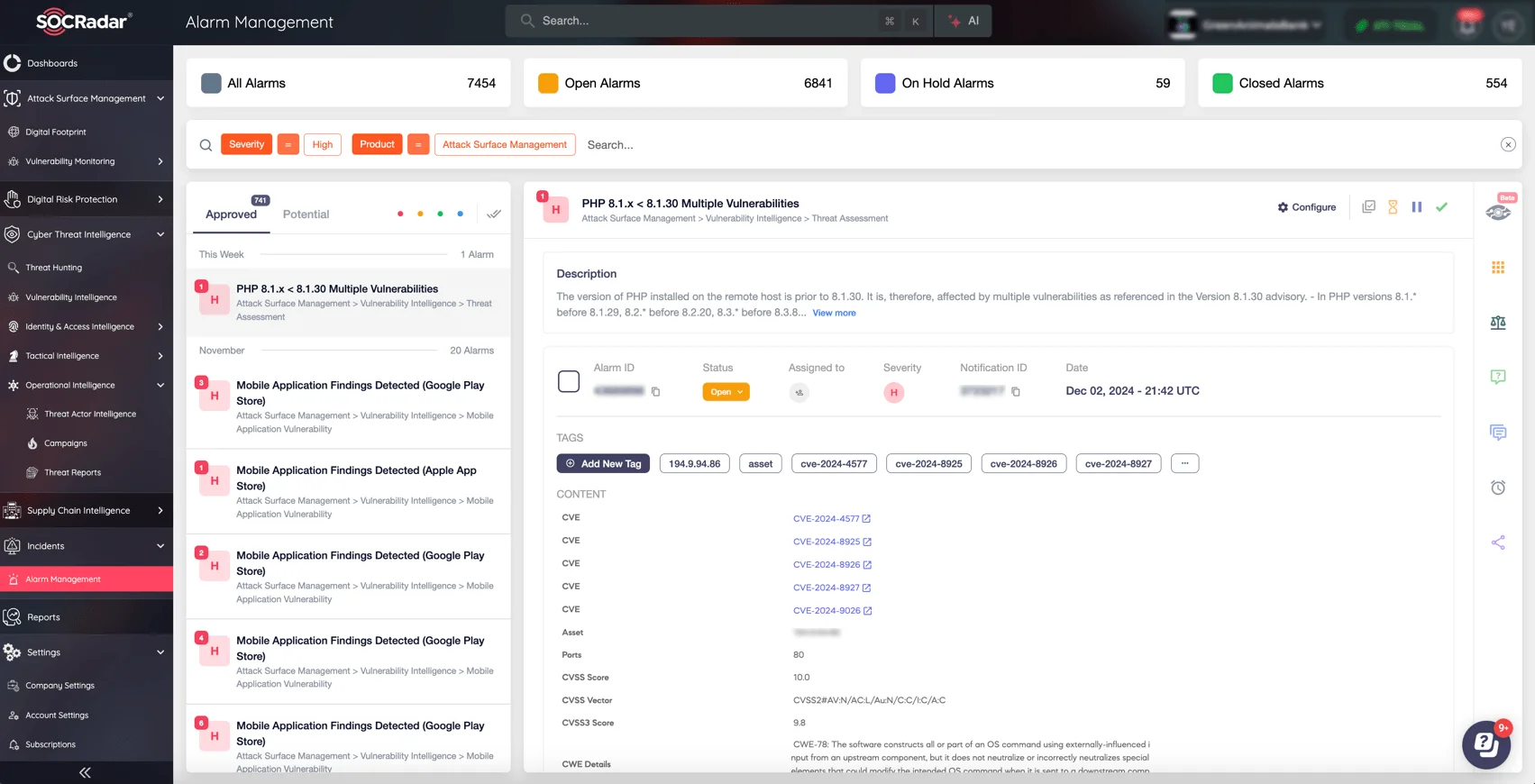
Alarm for multiple vulnerabilities found in a digital asset (SOCRadar XTI, Alarm Management)
SOCRadar’s alarm capabilities notify you of critical vulnerabilities, high-risk attack patterns, and any other weaknesses affecting your systems. By combining threat intelligence with advanced algorithms, SOCRadar delivers tailored alerts to your security team, supporting your proactive defense strategy.
What Are the Top 5 Software Weaknesses (CWEs) in 2024?
The list of top software weaknesses for 2024 assists organizations in prioritizing vulnerabilities that pose the greatest risk. Each of the top five CWEs showcases unique security challenges and their real-world impacts.
It is important to note that the example CVEs provided in the next sections are sourced from the CISA Known Exploited Vulnerabilities (KEV) Catalog, offering insights into vulnerabilities actively exploited in 2024. Notably, some of the vulnerabilities exemplified were disclosed in previous years but remain highly relevant due to continued exploitation or newly discovered attack methods.
Without further delay, here are the top five software weaknesses from the 2024 CWE Top 25 list.
1. CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Cross-site scripting (XSS) vulnerabilities occur when web applications fail to properly sanitize user input before rendering it in a web page. Attackers exploit this flaw to inject malicious scripts into the browser of an unsuspecting user, potentially leading to credential theft, session hijacking, or the deployment of harmful payloads.
In 2024, XSS vulnerabilities surged, earning CWE-79 the top spot on the CWE list, moving up from second place in 2023. This rise highlights the persistent threat XSS poses to modern web applications.
Numerous vulnerabilities tied to CWE-79 were exploited in 2024, including:
- CVE-2014-2120: A decade-old flaw in Cisco Adaptive Security Appliance (ASA) that allows attackers to inject scripts through the WebVPN login page. Despite its age, Cisco updated its advisory in December 2024, warning of active exploitation, which is tied to Androxgh0st botnet activity by researchers.
- CVE-2024-37383: Found in Roundcube Webmail, this flaw in handling SVG animate attributes enabled attackers to execute JavaScript, targeting government agencies in the Commonwealth of Independent States (CIS) region with malicious email attachments.
2. CWE-787: Out-of-bounds Write
Out-of-bounds write vulnerabilities take place when a program writes data outside the boundaries of an allocated memory buffer. This flaw can lead to unexpected behaviors such as program crashes, data corruption, or even the execution of malicious code. Having dropped from first to second place in the 2024 CWE list, CWE-787 continues to pose a substantial threat.
Prominent examples of CWE-787 exploitation in 2024 include:
- CVE-2024-21762: A vulnerability in Fortinet FortiOS that allows remote unauthenticated attackers to execute arbitrary code via crafted HTTP requests. This flaw has been leveraged by the Chinese APT group Volt Typhoon, which used it to deploy custom malware.
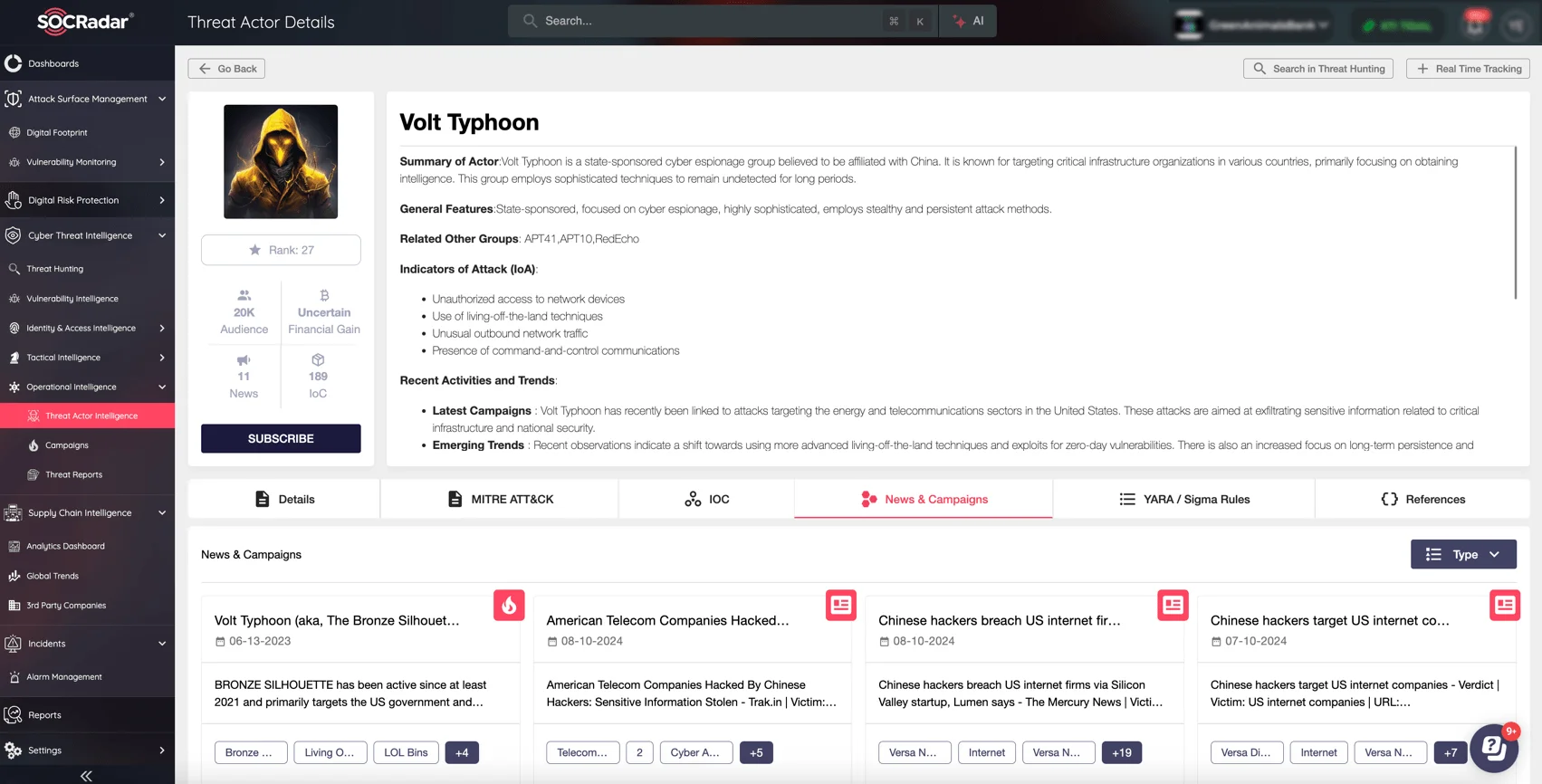
Volt Typhoon details on SOCRadar Threat Actor Intelligence – the module delivers insights into adversary TTPs and operations, helping you understand their focus and identify IOCs to strengthen defenses.
- CVE-2023-34048: A VMware vCenter Server vulnerability in the DCERPC protocol. Exploited in January 2024, attackers used this flaw to compromise credentials and deploy backdoors like VirtualPita and VirtualPie on ESXi hosts, enabling privilege escalation and data harvesting.
Other notable vulnerabilities in this category:
- Apple products (e.g., iOS, macOS, and watchOS) suffered memory corruption issues, including CVE-2024-23225 and CVE-2024-23296, which allow attackers to bypass kernel memory protections.
- Google Chromium-related weaknesses like CVE-2024-0519, CVE-2023-7024, and CVE-2024-4761 were exploited in popular web browsers, exposing millions of users to risks such as heap corruption and remote code execution.
Out-of-bounds write flaws are particularly dangerous due to their potential for remote code execution and memory corruption. They affect a wide range of software, from enterprise solutions to consumer-facing applications. Addressing these vulnerabilities requires diligent patch management and the use of tools to monitor and prioritize threats.
3. CWE-89: Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’)
SQL injection vulnerabilities arise when attackers manipulate input fields to execute unauthorized SQL queries. By exploiting applications that fail to properly sanitize user inputs, attackers can gain access to databases, retrieve sensitive information, or execute administrative operations. These weaknesses remain critical, with CWE-89 holding its third-place rank on the 2024 CWE Top 25 list, as it did in 2023.
Here are several SQL Injection vulnerabilities that saw active exploitation in 2024:
- CVE-2023-48788: Found in Fortinet FortiClient EMS, this vulnerability allowed unauthenticated attackers to execute system-level commands via specially crafted requests. Exploited in the Connect:fun campaign, attackers targeted media companies, leveraging this flaw to infiltrate networks.
- CVE-2024-6670: This vulnerability in Progress WhatsUp Gold enabled attackers to retrieve encrypted user passwords. Attackers exploited it to achieve Remote Code Execution (RCE) by abusing the Active Monitor PowerShell Script.
- CVE-2024-9379 and CVE-2024-29824: Both found in Ivanti products, these flaws were exploited by a nation-state adversary for chain attacks, enabling lateral movement within networks.
- CVE-2024-9465: In Palo Alto Networks Expedition, attackers used this flaw to access sensitive database contents, including password hashes, usernames, and device configurations.
Recalling last year’s mass exploitation of MOVEit Transfer vulnerability (CVE-2023-34362) by the Cl0p ransomware group underlines the scale of damage SQL Injection flaws can cause. The ordeal affected over 95 million individuals and 2,770 organizations globally.
4. CWE-352: Cross-Site Request Forgery (CSRF)
When hackers deceive authenticated users into taking unwanted actions on web applications without their permission, this is known as a Cross-Site Request Forgery (CSRF) vulnerability. By exploiting the trust between the user and the web application, attackers can execute unauthorized actions, such as changing account settings or transferring funds. In 2024, CWE-352 leaped five spots to rank fourth on the CWE Top 25 list, reflecting the growing attention on this critical web vulnerability.
Despite its high ranking, only one vulnerability assigned to CWE-352 made it to the 2024 CISA KEV Catalog, and it was addressed in 2014:
- CVE-2014-100005: This legacy flaw in D-Link DIR-600 routers allows attackers to hijack administrator sessions and change router configurations. Though old, it still affects end-of-life devices that should be retired or replaced as per vendor guidance.
Although many CSRF vulnerabilities emerged in 2024, including critical ones affecting Cisco Express Gateways, Cisco IOS/IOS XE, Jenkins, and a popular WordPress plugin, they have not yet met the criteria for inclusion in the KEV Catalog. For more information, you can explore the SOCRadar articles on Cisco Express Gateways, Cisco IOS/IOS XE, Jenkins, and the WordPress plugin vulnerabilities.
As with other types of flaws, CSRF vulnerabilities have also gained attention in underground forums. For example, SOCRadar’s Dark Web News module identified a hacker forum post claiming the discovery of a new CSRF vulnerability affecting the State of Washington website.
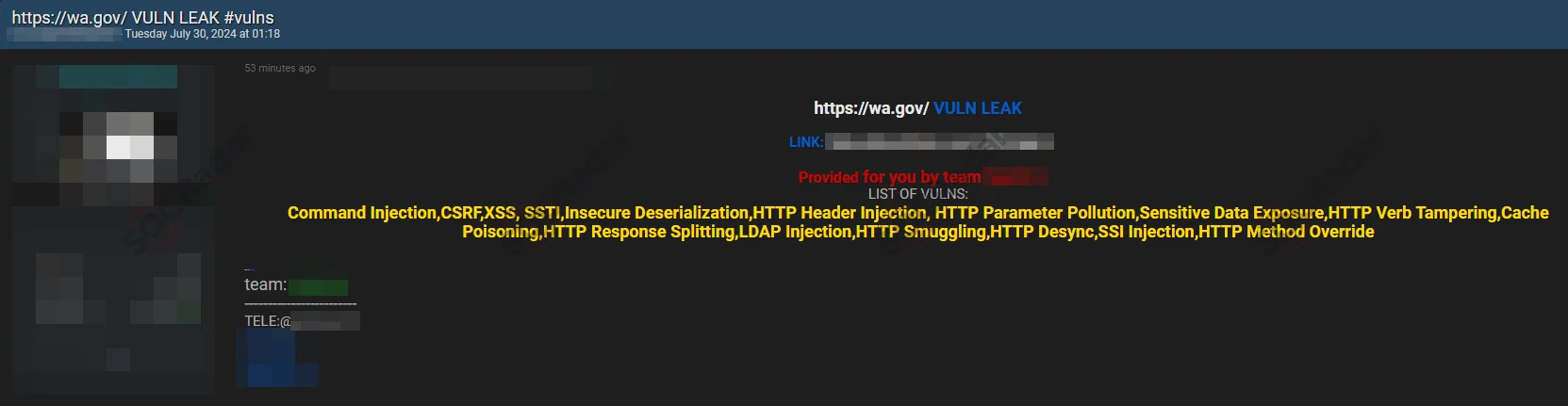
Threat actor claims to have found vulnerabilities in the State of Washington website (Source: SOCRadar Dark Web News)
SOCRadar’s Dark Web Monitoring provides actionable intelligence by monitoring underground forums and marketplaces. It helps your organization identify and address emerging threats before they are exploited. By delivering timely alerts and insights, SOCRadar can help mitigate risks effectively and protect your digital environments.
SOCRadar’s Dark Web Monitoring module, Black Market monitoring page
5. CWE-22: Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’)
Applications that improperly validate user input may be vulnerable to path traversal, which lets attackers change file paths to access files and directories outside of the designated boundaries. Exploiting this flaw may result in unauthorized access to sensitive files, data leakage, or even the execution of arbitrary code. In 2024, CWE-22 moved up three ranks to claim the fifth spot on the CWE Top 25 list, underlining the ongoing risks posed by improperly managed file paths.
Several vulnerabilities categorized under CWE-22 have been exploited in 2024, including:
- CVE-2024-11667: A vulnerability in Zyxel firewalls that allows attackers to download or upload files via crafted URLs. Threat actors actively targeted this flaw, using it as an entry point for Helldown ransomware campaigns.
- CVE-2021-26086: Found in Atlassian Jira Server and Data Center, this vulnerability enables attackers to read restricted files, such as those in the /WEB-INF/web.xml endpoint.
- CVE-2024-8963: Affecting Ivanti Cloud Services Appliance (CSA), this flaw can be exploited to bypass admin authentication and execute arbitrary commands, especially when combined with other vulnerabilities like CVE-2024-8190.
- CVE-2024-32113: Present in Apache OFBiz, this vulnerability exposes systems to remote code execution risks through improper file path validation.
- CVE-2024-28995: SolarWinds Serv-U also suffered from a path traversal vulnerability, allowing attackers to access sensitive files on the host machine.
Path Traversal vulnerabilities affect diverse systems, from enterprise tools to critical infrastructure devices like firewalls. The rise of CWE-22 in the rankings highlights the need for rigorous validation of file paths and consistent patching practices. Left unaddressed, these vulnerabilities can provide attackers with a direct path to critical resources, amplifying the impact of their campaigns.
CISA KEV Catalog Representation of the 2024 CWE Top 5
Building on the top five software weaknesses we just discussed, it is insightful to analyze how many of the 2024 vulnerabilities have been included in the CISA Known Exploited Vulnerabilities (KEV) Catalog.
Among the top five CWEs:
- Out-of-bounds Write (CWE-787) leads the KEV inclusion with 18 vulnerabilities, reflecting its widespread exploitation.
- SQL Injection (CWE-89) and Path Traversal (CWE-22) follow with 4 vulnerabilities each, showcasing their criticality in various attack campaigns.
- Cross-site Scripting (CWE-79) has 3 vulnerabilities included, emphasizing the ongoing relevance of XSS exploits.
- Cross-Site Request Forgery (CSRF) has no 2024 vulnerabilities included in the KEV Catalog despite its rank, highlighting a gap between the criticality of the CWE and its documented exploitation so far.
This distribution underscores the varying levels of attention these weaknesses receive from attackers and defenders alike. Addressing vulnerabilities across all these categories is vital to reduce exposure to real-world threats.
Protect your external-facing digital assets by identifying vulnerabilities before attackers exploit them. SOCRadar’s Attack Surface Management (ASM) module continuously monitors your attack surface to detect exposed assets, misconfigurations, and exploitable vulnerabilities. It provides visibility into your digital footprint, tracks associated CVEs, and delivers actionable intelligence to prioritize remediation.
SOCRadar’s Attack Surface Management module
Key Capabilities of the ASM module:
- External asset discovery and monitoring.
- Contextual insights on associated vulnerabilities.
- Real-time alerts on exposure risks.
- CISA KEV Check for actively exploited vulnerabilities.
Conclusion
The 2024 CWE Top 25 Most Dangerous Software Weaknesses list underscores the importance of staying vigilant against software vulnerabilities that could lead to significant security risks. With categories like Cross-site Scripting (CWE-79) and Out-of-bounds Write (CWE-787) dominating the rankings, this year’s list reflects the evolving threat landscape and the increasing exploitation of both new and legacy weaknesses.
With the inclusion of real-world examples from the CISA Known Exploited Vulnerabilities (KEV) Catalog, this blog post highlights how attackers continue to leverage these flaws, causing widespread disruptions. For organizations, this serves as a call to action to prioritize patching efforts, implement secure coding practices, and leverage advanced threat intelligence tools like SOCRadar to stay ahead of any threats.
By proactively addressing these top weaknesses, you can reduce the attack surface of your organization, protect critical assets, and enhance overall cybersecurity resilience. As the nature of vulnerabilities evolves, staying informed and adapting defense strategies will remain key to mitigating future risks.
For more information, you can view all CWE Top 25 lists and their methodology on MITRE’s CWE website.





































