
Severe Path Traversal Vulnerability in Adobe ColdFusion (CVE-2024-53961), Update Now
A critical vulnerability in Adobe ColdFusion versions 2023 and 2021 has prompted urgent security updates. Alarmingly, a Proof-of-Concept (PoC) exploit is already circulating, putting organizations at risk of immediate exploitation.
With attackers likely to weaponize this vulnerability, it’s essential for ColdFusion users to act fast and apply the latest patches to protect their systems.
CVE-2024-53961: Path Traversal Vulnerability in Adobe ColdFusion
Tracked as CVE-2024-53961, this vulnerability in Adobe ColdFusion has been categorized as a Path Traversal issue (CWE-22). It allows attackers to perform arbitrary file system reads, which can expose sensitive system files. While Adobe rates this vulnerability as ‘Critical’ in its advisory, the CVSS (v3.1) score is set at 7.4, indicating its high severity.
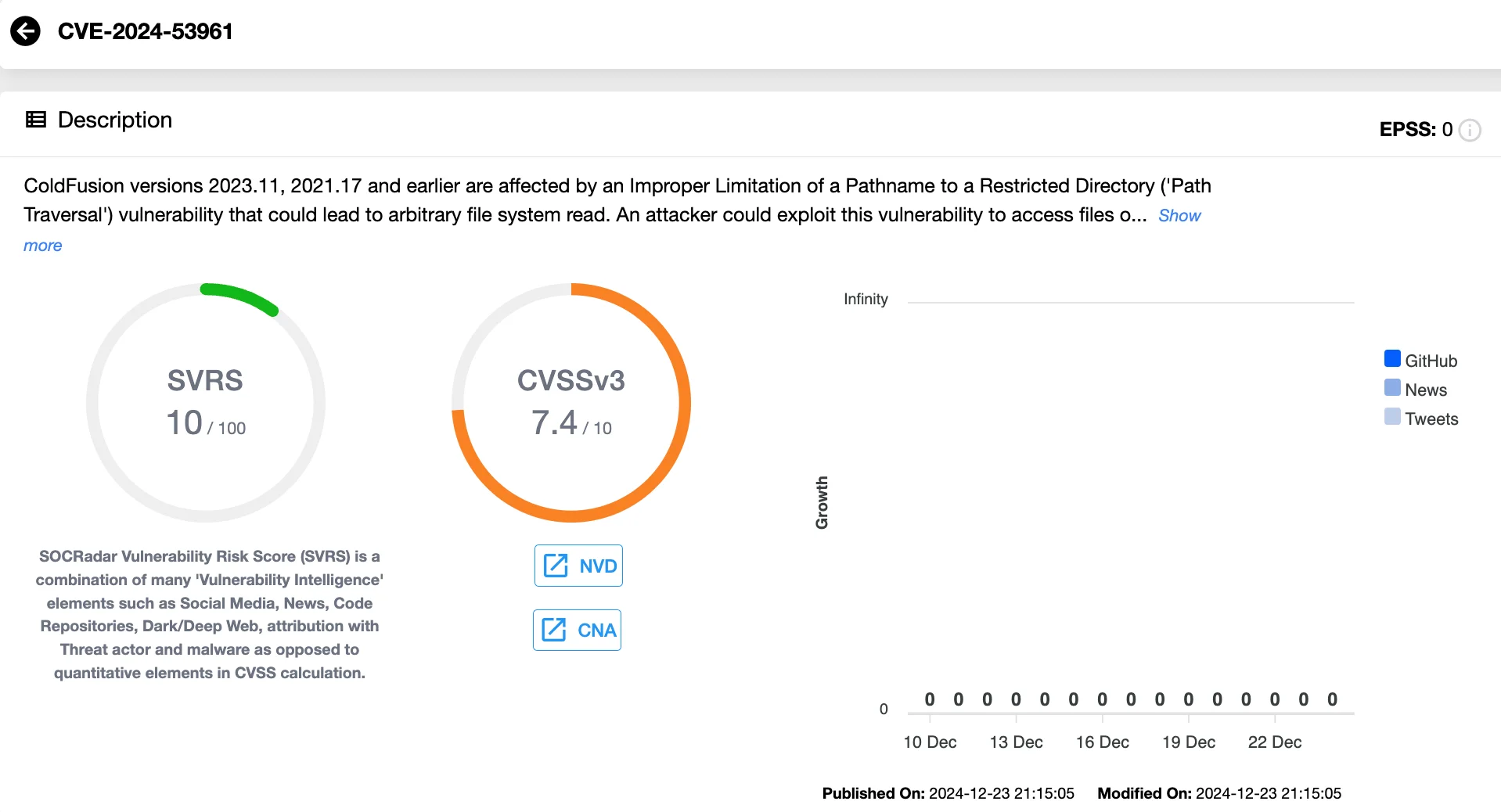
Vulnerability card of CVE-2024-53961 (SOCRadar Vulnerability Intelligence)
Despite its high attack complexity, CVE-2024-53961 does not require user interaction or privileges to be exploited. Also, there’s no direct impact on system availability, but the potential damage to confidentiality and integrity is significant as it could lead to unauthorized access to sensitive files.
Adobe has acknowledged the existence of a Proof-of-Concept (PoC) exploit for this vulnerability, raising concerns that attackers may quickly weaponize it in real-world scenarios.
Which Adobe ColdFusion Versions Are Affected?
The CVE-2024-53961 vulnerability impacts the following versions:
- ColdFusion 2023, update 11 and earlier
- ColdFusion 2021, update 17 and earlier
Users of these versions are strongly encouraged to apply the latest security updates to mitigate the risk associated with this vulnerability.
Exploitation Status of CVE-2024-53961
At present, Adobe has not reported any active exploitation of CVE-2024-53961. However, the vulnerability has been assigned a Priority 1 level in Adobe’s advisory, indicating that the company considers it critical.
Priority 1 vulnerabilities are either actively being targeted or have a high likelihood of being targeted by exploits in the wild. Adobe strongly recommends that users apply the necessary security updates within 72 hours to protect against potential threats.
In the continually shifting cyber threat scenery, vulnerabilities are a constant challenge, and early detection can make all the difference in preventing breaches. SOCRadar’s Vulnerability Intelligence module provides real-time insights into newly discovered vulnerabilities, tracking CVEs, and detecting trends related to exploits and emerging threats.
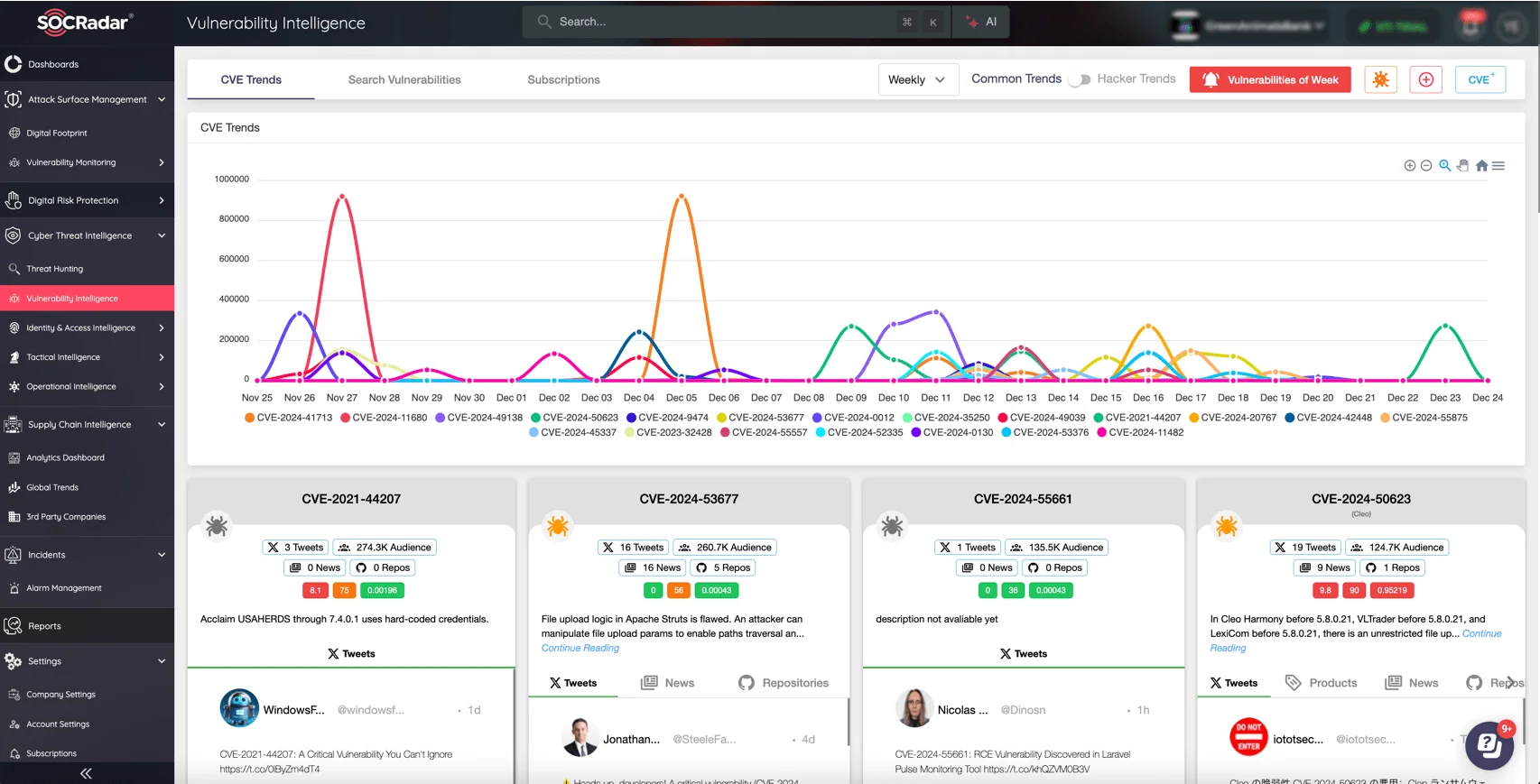
Access extensive details and updates on identified CVEs with SOCRadar’s Vulnerability Intelligence
By continuously monitoring vulnerabilities across multiple sources and providing actionable intelligence, SOCRadar enables your security team to stay ahead of attackers. Get notified of critical vulnerabilities in your ecosystem and access details on exploitation risks, including detailed remediation steps.
Adobe ColdFusion Updates to Address CVE-2024-53961
Adobe recommends updating to the latest versions of ColdFusion to address the new vulnerability, CVE-2024-53961. The fixed versions are:
- ColdFusion 2023, update 12
- ColdFusion 2021, update 18
For more details on available updates and further security recommendations, visit Adobe’s official security bulletin.
Additionally, Adobe advises reviewing the updated serial filter documentation to protect against insecure WDDX deserialization attacks.
Unseen vulnerabilities in your organization’s attack surface are prime targets for cybercriminals. By managing and reducing your attack surface, you reduce the opportunity for exploitation. SOCRadar’s Attack Surface Management (ASM) provides complete visibility into your digital footprint, identifying exposed assets, vulnerabilities, and potential weak points that attackers can exploit.
SOCRadar’s ASM continuously scans your infrastructure, mapping out publicly exposed digital assets, detecting vulnerabilities, and tracking them for real-time updates. With proactive alerts and actionable intelligence, your security team can address issues before attackers can exploit them. Defend your brand, systems, and customer data by knowing exactly where your attack surface lies.
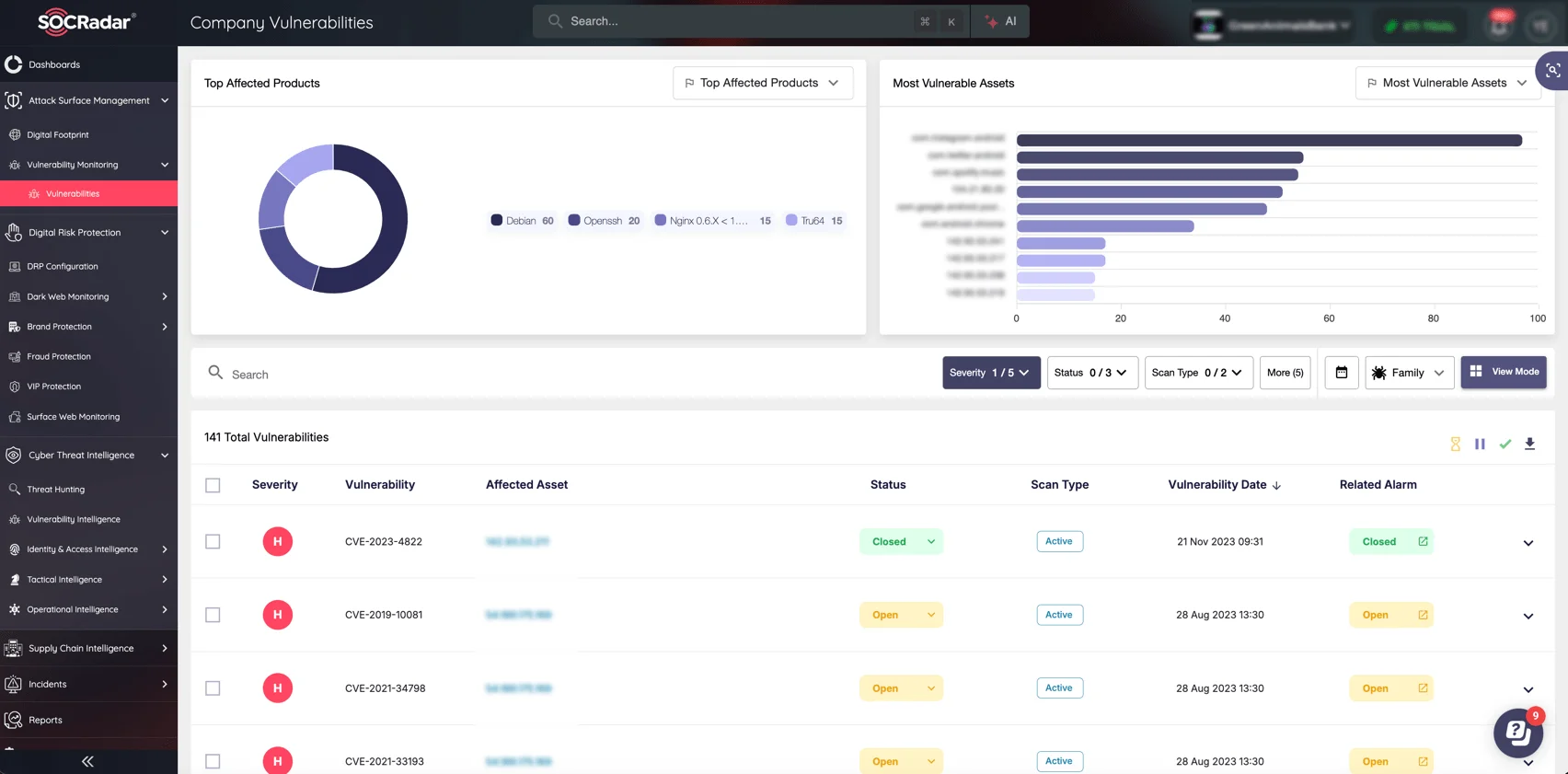
SOCRadar’s Attack Surface Management (ASM) module page, Company Vulnerabilities
In light of CVE-2024-53961, it is important to consider the broader context of ColdFusion vulnerabilities addressed previously. In July 2023, CISA added CVE-2023-29298 and CVE-2023-38205 to the KEV Catalog, citing their exploitation potential. This was followed by the inclusion of CVE-2023-29300 and CVE-2023-38203 in January 2024. These vulnerabilities were actively targeted by attackers, who employed techniques like chained exploits and reverse shells to gain unauthorized access.
Additionally, CISA issued further alerts in November 2023 and March 2024, raising concerns about other severe vulnerabilities in ColdFusion.
These vulnerabilities, including the one currently under discussion, highlight the need to apply security patches to ColdFusion systems without delay.




































