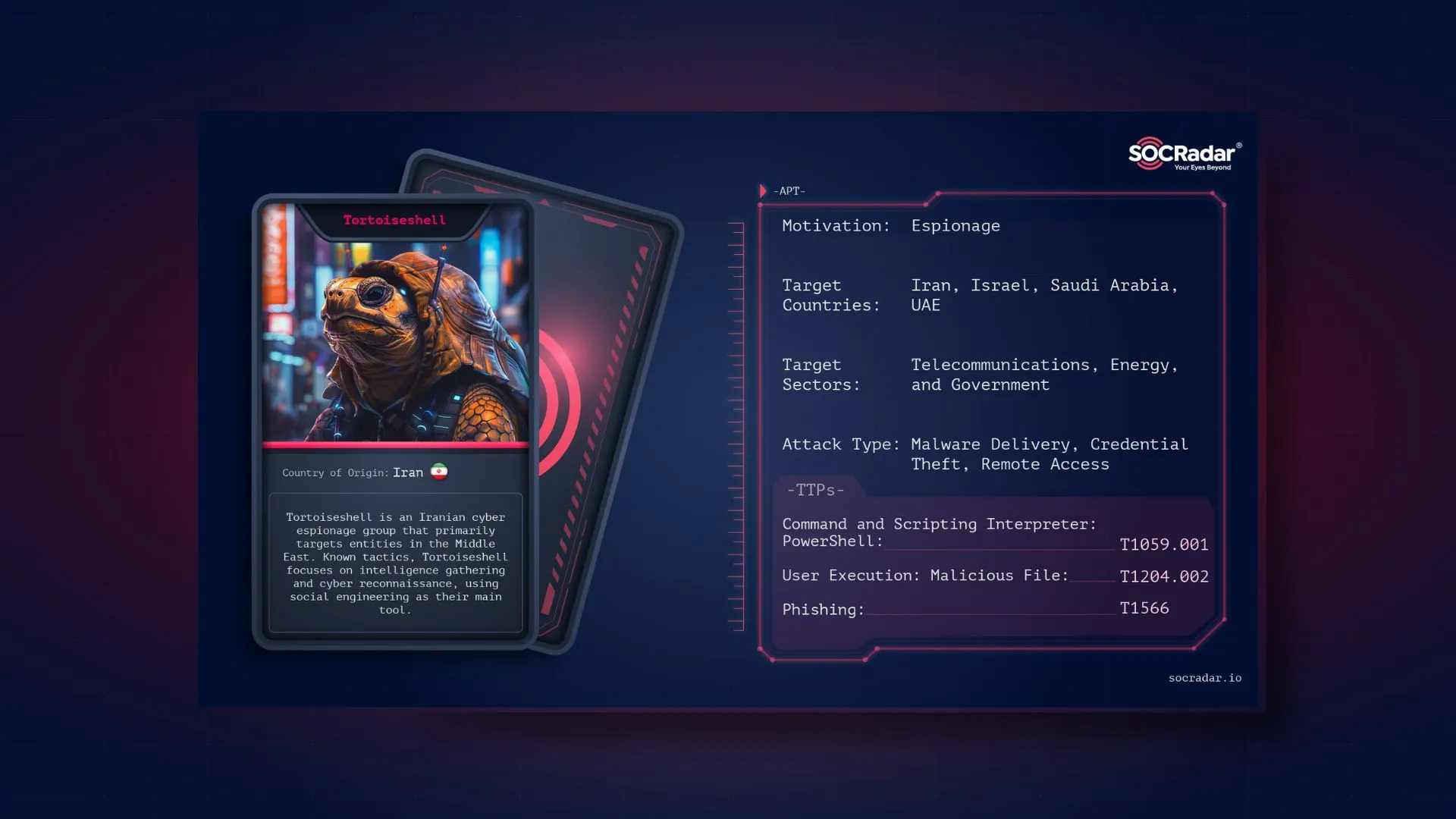
Dark Web Profile: Tortoiseshell APT
In recent years, Iran has ramped up cyber campaigns to safeguard national interests, deter adversaries, and conduct espionage. These operations are carried out by units within the IRGC and MOIS. One such Iranian advisory that is working towards Iran’s interest is Tortoiseshell.
Tortoiseshell, also known as TA456, Imperial Kitten, Crimson Sandstorm, or DustyCave, is a cyber-espionage threat actor believed to be backed by Iran’s IRGC. It primarily targets technology, defense, NGOs, government, financial, and transportation sectors in Israel, Saudi Arabia and other Middle Eastern countries.
Who is Tortoiseshell?
Tortoiseshell first emerged in 2019 as a previously undocumented attack group, primarily targeting IT providers inSaudi Arabia. Using a combination of custom and off-the-shelf malware, the group launched supply chain attacks aimed at compromising the IT providers’ customers. Active since at least July 2018, Tortoiseshell was linked to at least 11 organizations, mostly based in Saudi Arabia. In some cases, the attackers gained domain admin-level access to the targeted networks. This marked their first known appearance to the broader cybersecurity community.

Threat actor card for Tortoiseshell
More recently, Mandiant has linked Tortoiseshell to suspected Iranian espionage operations targeting aerospace, aviation, and defense sectors in the Middle East, including Israel, the UAE, and potentially Turkey, India, and Albania. This activity, ongoing since June 2022, continues into 2024. Tortoiseshell has used Microsoft Azure infrastructure and social engineering tactics to deploy the backdoors MINIBIKE and MINIBUS. With its evolving tactics and continued focus on defense-related targets amid regional tensions, Tortoiseshell remains an active and dangerous threat.
Whom Do They Target?
Tortoiseshell primarily focuses on defense contractors, aerospace firms, and military-linked organizations, with a strong emphasis on targets in the United States, Israel, and the broader Middle East. The group has also been observed targeting IT providers, energy companies, and other industries of strategic interest to Iran. Their operations frequently involve prolonged social engineering campaigns aimed at individuals with privileged access to sensitive systems or proprietary information. By leveraging fake social media personas and carefully crafted spear-phishing emails, Tortoiseshell seeks to establish trust with employees and infiltrate networks over time. Additionally, past campaigns indicate a particular interest in espionage against entities involved in geopolitical affairs, national security, and critical infrastructure, aligning with Iran’s broader cyber objectives.
How Do They Operate?
The group employs a blend of social engineering, custom malware, and strategic infrastructure to infiltrate and maintain access to high-value networks, particularly in the defense and aerospace sectors.
One of Tortoiseshell’s hallmark tactics is the use of long-term social engineering campaigns. The group creates and operates fake social media personas, often posing as young women to establish rapport with targeted individuals over weeks or even months. These fake profiles are used to engage with employees of defense contractors, gradually building trust before delivering malware-laced content, such as weaponized documents or malicious links. In one documented case, Tortoiseshell used a fabricated LinkedIn persona named “Marcella Flores” to interact with a U.S. defense contractor and eventually deliver the LEMPO malware.
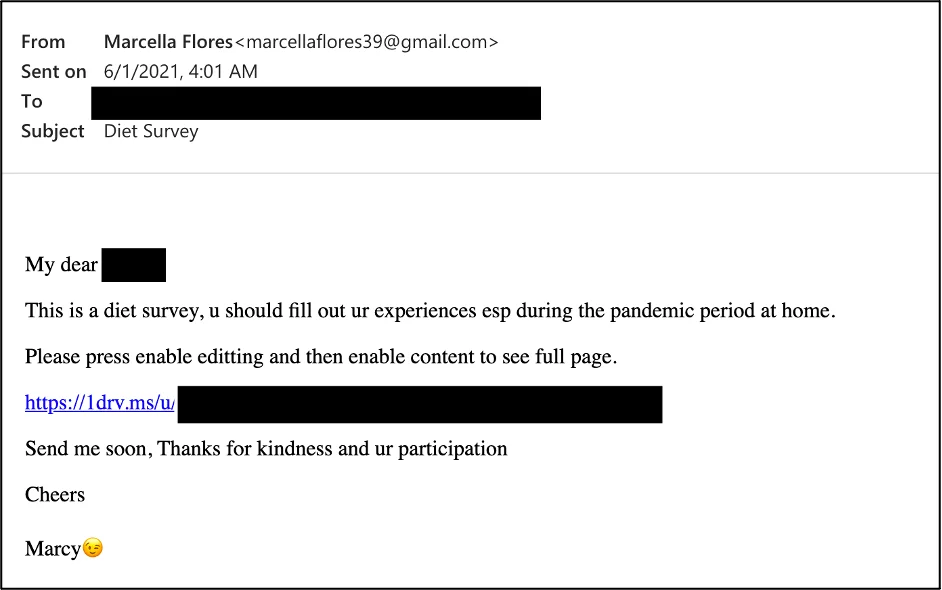
Phishing mail by Tortoiseshell in 2021, similar campaigns were continuing to this year (Proofpoint)
Tortoiseshell also utilizes spear-phishing as a primary infection vector. Their phishing emails typically contain malicious attachments, often disguised as job-related or business-relevant documents. These attachments exploit vulnerabilities in Microsoft Office or Adobe software to execute embedded payloads that establish persistence on the victim’s system. The group has been observed leveraging IMAPLoader, a custom implant designed to evade detection by using email protocols for command-and-control (C2) communication.
Beyond traditional phishing, Tortoiseshell integrates cloud-based services to enhance operational security. The group has been known to abuse platforms such as Dropbox and Google Drive to host payloads and exfiltrate stolen data, reducing the likelihood of immediate detection by network defenses. In addition, their malware employs various techniques to blend into legitimate network traffic, including encrypted communications and fileless execution methods.
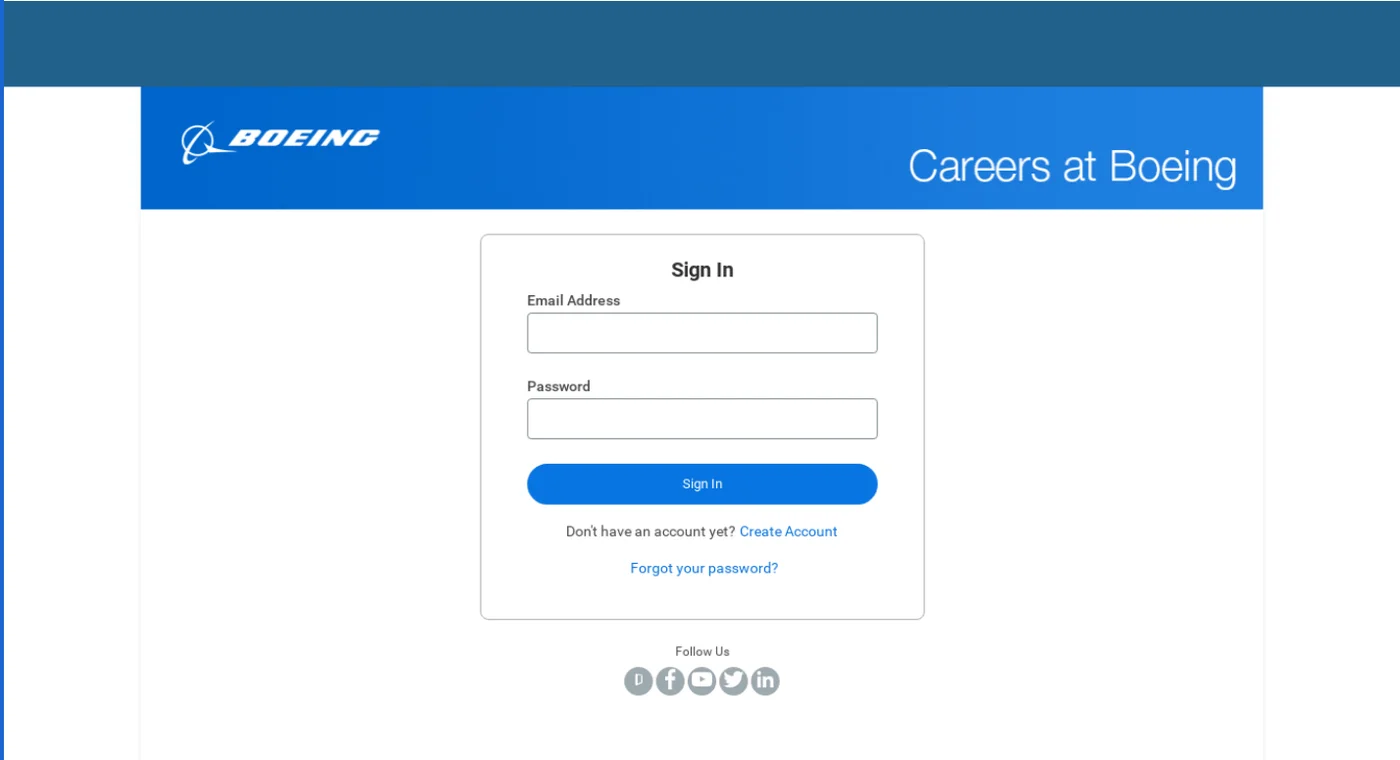
Fake login page masquerading as the aerospace company Boeing (Mandiant)
Back in 2021, Meta (Facebook) disrupted a Tortoiseshell campaign that used fake accounts to lure targets into downloading malicious software. The group set up fake recruitment websites mimicking legitimate companies, tricking victims into installing malware under the pretense of job application processes.
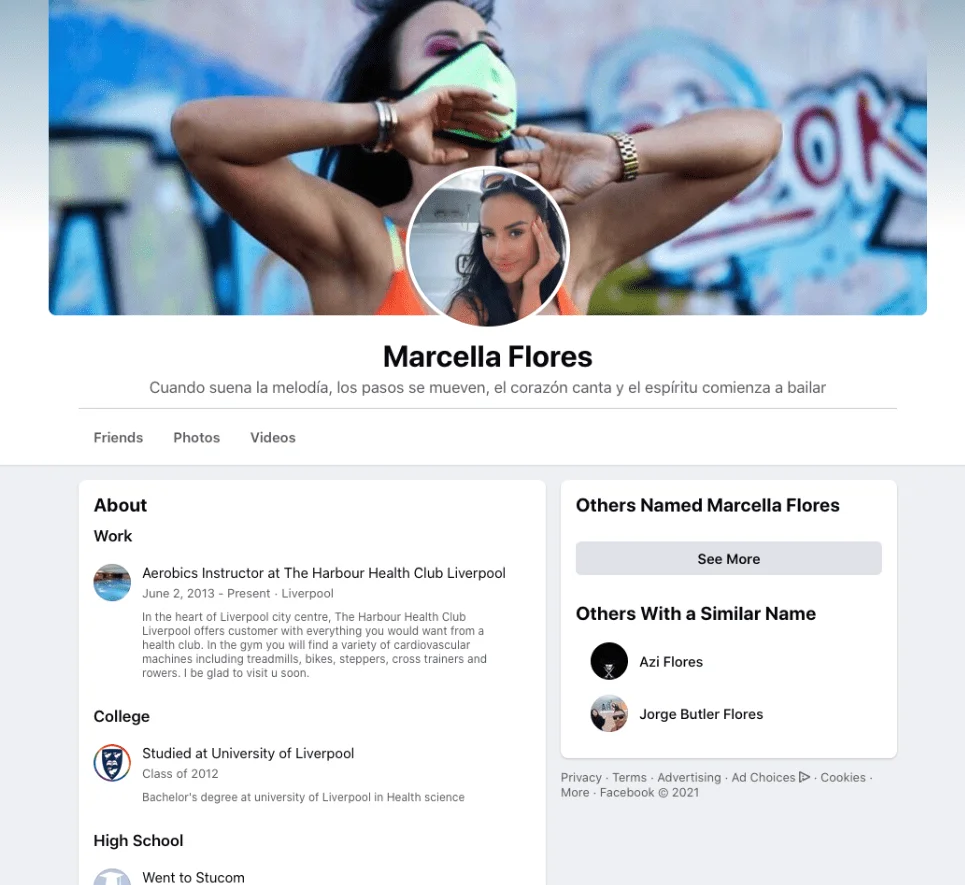
Fake Facebook profile used by Iranian actors (Proofpoint)
Tortoiseshell’s operations are characterized by their patience and precision, often tailoring each attack to its specific target. Their ability to establish relationships over extended periods, combined with the deployment of custom malware and cloud-based exfiltration techniques, underscores their effectiveness as an Advanced Persistent Threat (APT) conducting espionage on behalf of Iranian interests.
How to Defend Against Tortoiseshell and Iranian APT Threats?
Mitigating the threats of Tortoiseshell and related Iranian Advanced Persistent Threats (APTs) necessitates a comprehensive security strategy, with a particular emphasis on countering phishing and social engineering attacks. These groups are known for aggressively adopting such tactics to facilitate intrusions and credential theft. Implementing proactive defense measures, continuous monitoring, and leveraging advanced threat intelligence platforms are crucial steps in safeguarding your organization.
- Strengthen Phishing and Social Engineering Defenses
- Advanced Email Filtering: Utilize sophisticated email filtering solutions to detect and block phishing attempts. This includes scanning for malicious attachments, links, and suspicious sender addresses.
- Email Authentication Protocols: Implement Domain-based Message Authentication, Reporting & Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM) to prevent email spoofing and ensure the authenticity of incoming emails.
- Employee Training and Awareness: Conduct regular training sessions to educate employees on recognizing phishing emails and social engineering tactics. Simulated phishing exercises can help reinforce this training and assess employee readiness.
- Phishing Domain Detection: Employ solutions that monitor and analyze domain activity to proactively detect and mitigate phishing threats. For instance, SOCRadar’s Phishing Domain Detection feature analyzes millions of domains across major registrars to identify fakes and look-alikes, helping prevent phishing attacks by identifying malicious domains before they can be used against your organization.
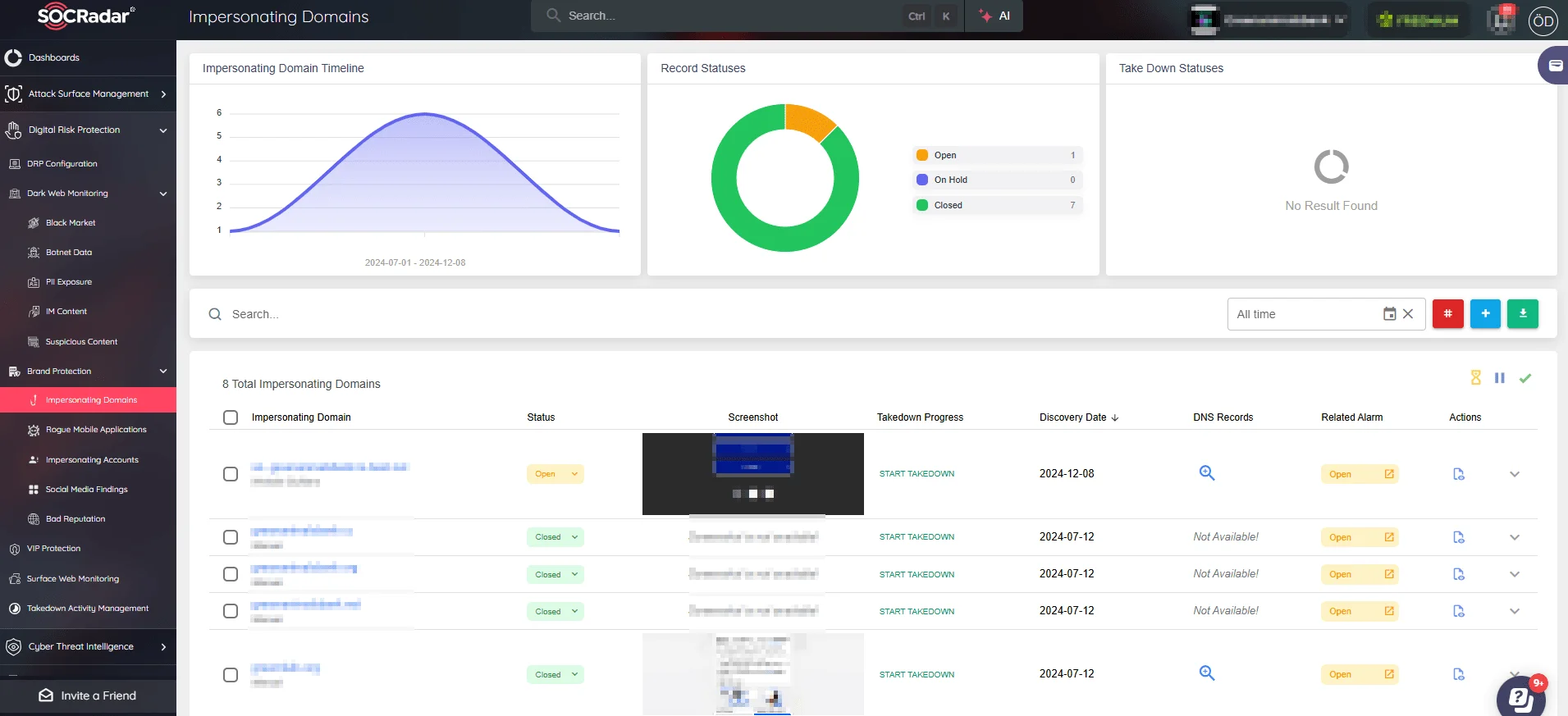
SOCRadar Brand Protection detects phishing threats, identifies compromised credentials, and helps remove fraudulent sites to safeguard your digital assets
- Enforce Strong Access Controls
- Multi-Factor Authentication (MFA): Require MFA for all user accounts, especially those with privileged access, to add an extra layer of security beyond just passwords.
- Zero Trust Security Model: Implement a Zero Trust architecture that verifies every access request, regardless of its origin, to limit lateral movement within the network.
- Regular Access Audits: Conduct periodic audits of user access levels and adjust permissions based on the principle of least privilege, ensuring users have only the access necessary for their roles.
- Patch and Update Systems Promptly
- Timely Software Updates: Regularly update operating systems, applications, and firmware to patch vulnerabilities that could be exploited by attackers.
- Vulnerability Management: Establish a vulnerability management program to identify, prioritize, and remediate security weaknesses in your systems.
- Monitor for New Threats: Stay informed about newly disclosed vulnerabilities and apply security updates promptly to mitigate potential exploitation.
- Monitor Network and Endpoint Activity
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints for signs of compromise, such as unusual processes or unauthorized access attempts.
- Intrusion Detection and Prevention Systems (IDPS): Utilize IDPS to monitor network traffic for malicious activity and block potential threats in real-time.
- Behavioral Analytics: Implement behavioral analytics tools to establish baselines of normal user activity and detect anomalies that may indicate a security incident.
- Secure Supply Chain and Third-Party Access
- Vendor Security Assessments: Conduct thorough security assessments of third-party vendors and partners to ensure they adhere to your security standards.
- Strict Access Controls for Third Parties: Limit third-party access to your systems and data, providing only the necessary permissions required for their functions.
- Continuous Monitoring: Monitor third-party activities within your network to detect any unauthorized or suspicious behavior promptly.
- Develop and Test Incident Response Plans
- Comprehensive Incident Response Plan: Develop a detailed incident response plan that outlines procedures for detecting, containing, eradicating, and recovering from security incidents.
- Regular Drills and Simulations: Conduct regular incident response drills and simulations to test the effectiveness of your plan and identify areas for improvement.
- Backup and Recovery Procedures: Ensure that you have secure, offline backups of critical data and systems, and regularly test your ability to restore from these backups in the event of a ransomware attack or data loss incident.
By implementing these measures, organizations can significantly enhance their defenses against Tortoiseshell and other Iranian APT threats, particularly those employing phishing and social engineering tactics. Leveraging advanced threat intelligence platforms like SOCRadar can provide real-time insights and proactive threat detection, further strengthening your security posture.
SOCRadar, Threat Actor Intelligence
In Summary
Tortoiseshell, also known as TA456, Imperial Kitten, Crimson Sandstorm, or DustyCave, is an Iranian cyber-espionage group linked to the IRGC. Since emerging in 2018, the group has primarily targeted defense, aerospace, and military-linked organizations in the U.S., Israel, and the broader Middle East. Their operations also extend to IT providers, energy companies, and geopolitical entities of interest to Iran.
Tortoiseshell is known for its long-term social engineering campaigns, often using fake social media personas to build trust with targets before deploying malware. The group employs spear-phishing, malicious attachments, and cloud-based services like Dropbox and Google Drive to evade detection. Their malware toolkit includes implants like IMAPLoader, and backdoors such as MINIBIKE and MINIBUS, used to establish persistence and steal sensitive data.
Their TTPs align with Iranian cyber objectives, focusing on espionage and intelligence gathering. Organizations can defend against Tortoiseshell by strengthening phishing defenses, enforcing access controls, monitoring networks, securing supply chains, and testing incident response plans. Advanced threat intelligence solutions like SOCRadar help detect and mitigate these threats proactively.
What are Tortoiseshell’s TTPs?
| Tactic | Technique ID | Technique Name |
| Reconnaissance | T1592 | Gather Victim Host Information |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Initial Access | T1566 | Phishing |
| T1189 | Drive-by Compromise | |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | |
| T1059.001 | Command and Scripting Interpreter: PowerShell | |
| T1204.002 | User Execution: Malicious File | |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1547.001 | Boot or Logon AutoStart Execution: Registry Run Keys / Startup Folder | |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| T1055.001 | Process Injection: Dynamic-link Library Injection | |
| Discovery | T1082 | System Information Discovery |
| T1016 | System Network Configuration Discovery | |
| T1033 | System Owner/User Discovery | |
| T1083 | File and Directory Discovery | |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |




































