
AUTOSUR Breach, FiveM Database Leak, Disney+ Account Checker, Crypto Leads & Forex Scams Exposed
Cybercriminals continue to target industries worldwide, with SOCRadar’s Dark Web Team uncovering a range of threats this week.
A hacker claims to have leaked millions of customer records from AUTOSUR, while another is selling personal and financial data of U.S. citizens. Unauthorized access to Lenovo and HP’s shipping portals raises concerns over supply chain security, and a breach of the National Telecommunications Commission of the Philippines reportedly exposes sensitive infrastructure details. Meanwhile, cybercriminals are exploiting the gaming and entertainment sectors with a Disney+ credential checker and a leaked FiveM database. Additionally, a massive dataset of crypto and forex leads is up for sale, posing risks of fraud and financial scams.
Receive a Free Dark Web Report for Your Organization:
Alleged Database of AUTOSUR is on Sale
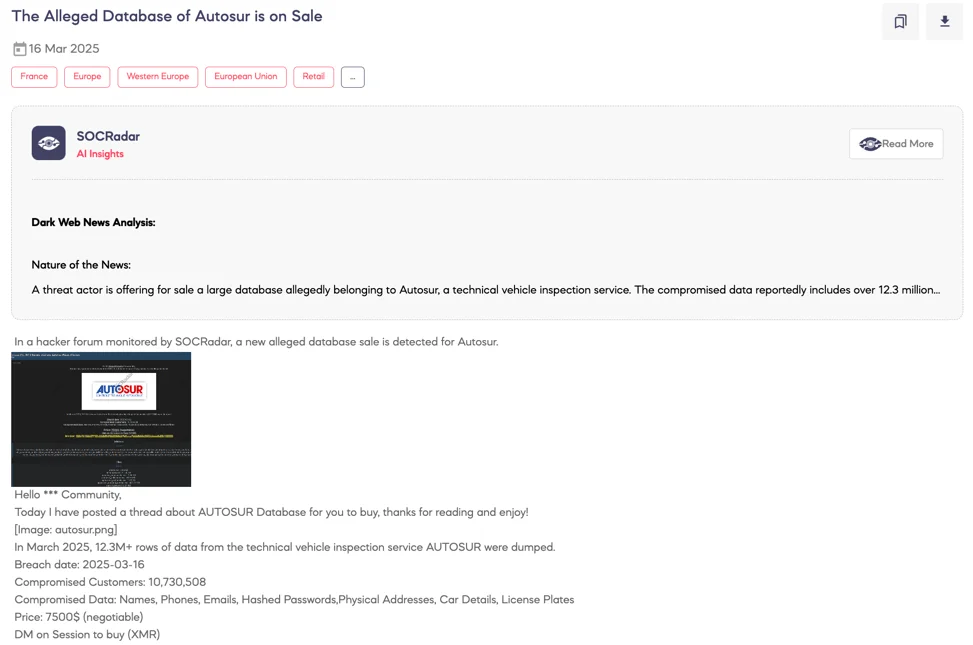
SOCRadar’s Dark Web Team discovered a hacker forum post where a threat actor claims to have leaked approximately 10.7 million customer records from the French vehicle inspection company, AUTOSUR.
According to the post, the breach occurred on March 16, 2025, and exposed highly sensitive data such as customer names, emails, phone numbers, hashed passwords, home addresses, vehicle information, and license plate numbers.
The actor responsible is demanding $7,500 in Monero (XMR) for the complete 12 million record database. The large volume of exposed data poses significant risks, including identity theft, targeted phishing attacks, and financial fraud.
If validated, this breach may also trigger substantial regulatory and compliance repercussions, including potential GDPR investigations, impacting AUTOSUR’s reputation significantly.
Alleged Unauthorized Shipping Portal Access Sale is Detected for Lenovo and HP
SOCRadar Dark Web Team identified a hacker forum post advertising unauthorized access to a shipping portal associated with Lenovo and HP, specifically targeting shipment tracking activities in India. The seller claims the compromised access allows real-time monitoring of Return Merchandise Authorizations (RMAs) and related logistics details.
This breach represents a significant threat to the supply chain, as it could expose sensitive information such as shipment contents, customer identities, and delivery destinations. Exploitation of this data can enable targeted theft, fraudulent redirection of shipments, or social engineering attacks. Additionally, the specific regional focus on India highlights potential vulnerabilities in local logistics infrastructures, potentially damaging the reputations of Lenovo and HP in the affected market.
Alleged Data of American Citizens are on Sale
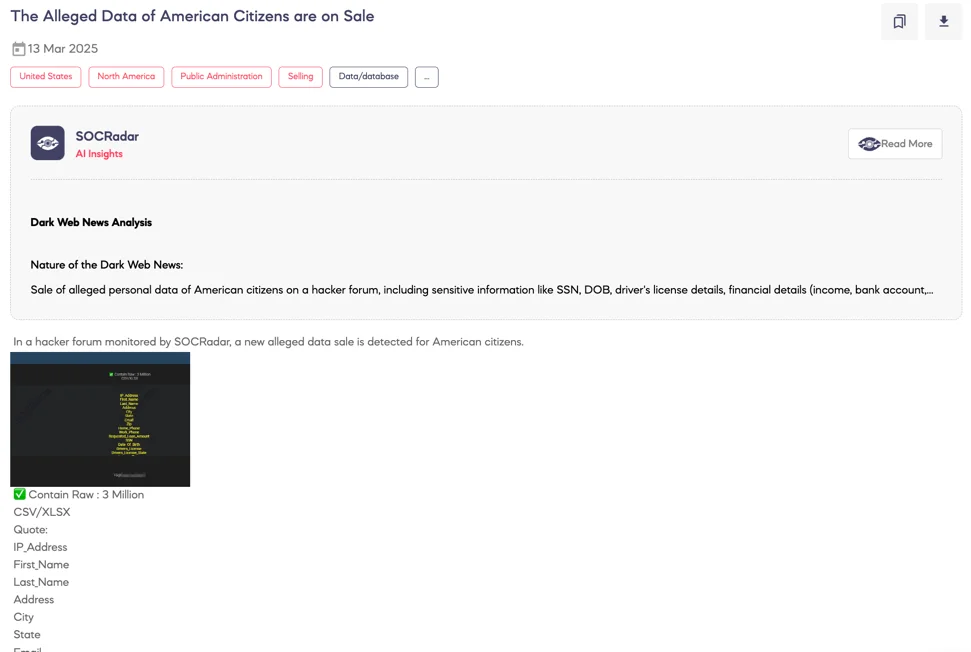
SOCRadar Dark Web Team identified a hacker forum post offering a database allegedly containing detailed personal and financial data of approximately 3 million American citizens. The threat actor provided samples as proof, indicating the legitimacy of the breach. The leaked dataset reportedly includes Social Security numbers (SSNs), bank account details, routing numbers, driver’s licenses, employer information, income details, and other critical personal identifiers.
The extensive and recent nature of the data significantly increases the risk of identity theft, financial fraud, and targeted phishing attacks. Given the volume and sensitivity of the information, the potential for widespread misuse is considerable, highlighting urgent risks to affected individuals and financial institutions alike.
Alleged Database of National Telecommunications Commission of Philippines is Leaked
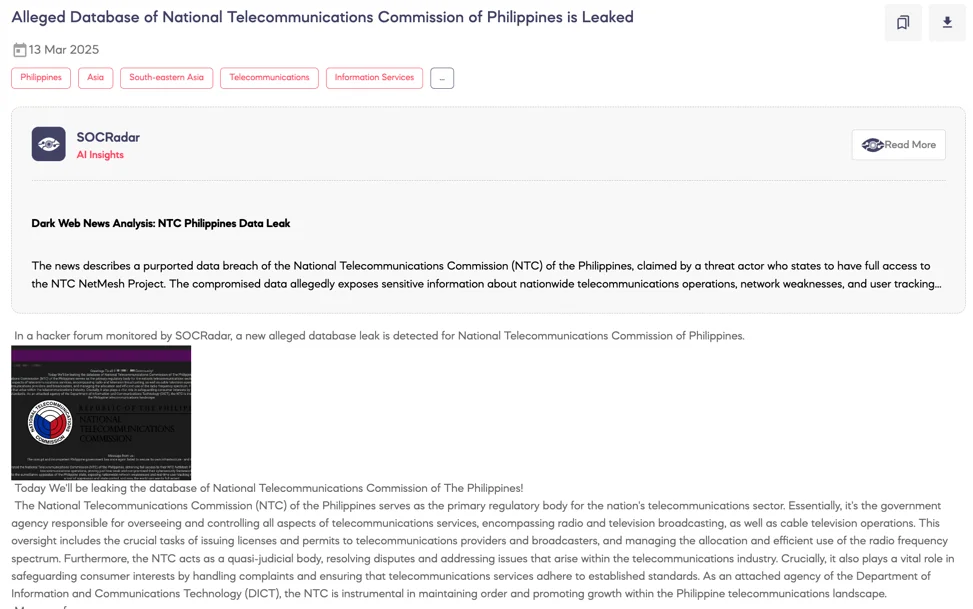
SOCRadar Dark Web Team detected a threat actor claiming to have breached the National Telecommunications Commission (NTC) of the Philippines, allegedly obtaining comprehensive access to the commission’s infrastructure.
According to the actor’s statement, the stolen dataset contains critical information, including nationwide network vulnerabilities, user tracking mechanisms, and operational details concerning broadcasting licenses, telecom permits, and frequency allocations.
The threat actor explicitly framed the breach as politically motivated, criticizing the Philippine government’s cybersecurity practices and branding the NTC’s tracking mechanisms as oppressive. If confirmed, the leak could have severe implications, impacting national security, economic stability, and the privacy of millions of citizens.
Atlantis Checker Tool for Disney+ is Shared

SOCRadar Dark Web Team detected a threat actor sharing a tool named “Atlantis Checker,” designed specifically to verify stolen Disney+ credentials. According to the post, this tool enables rapid credential stuffing, allowing threat actors to test large numbers of leaked account credentials for validity.
The availability of this tool indicates active targeting of streaming platforms, exploiting previously compromised credentials available from data breaches. Successful use could lead to account takeover, unauthorized streaming access, financial fraud, and personal data exposure.
Alleged Crypto Forex Leads Data of Many Countries Are on Sale
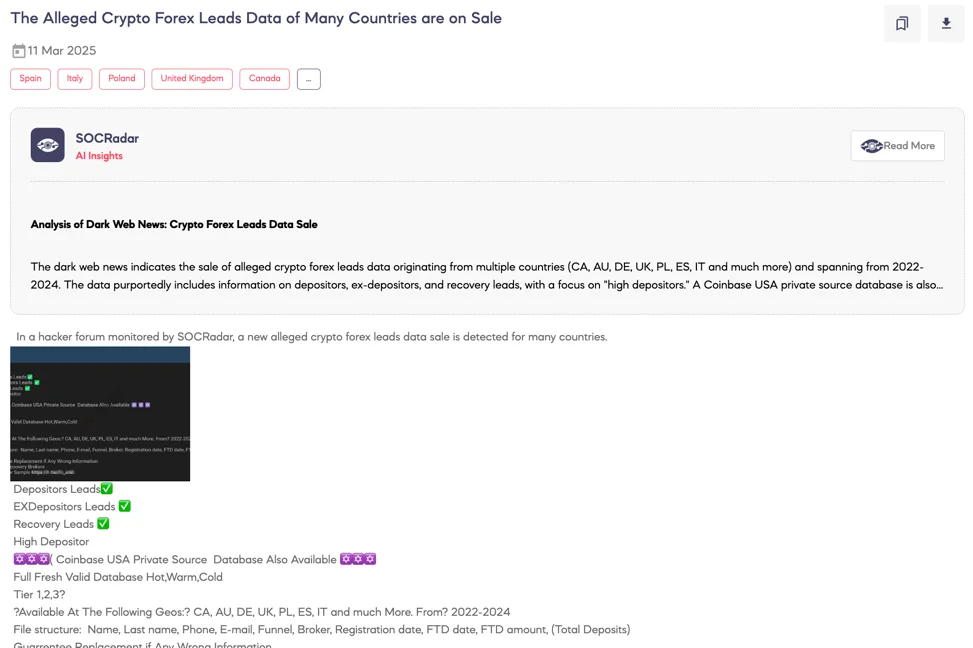
SOCRadar Dark Web Team detected a forum post where a threat actor advertises the sale of an extensive crypto and forex leads database, allegedly sourced from various countries including Canada, Australia, Germany, the UK, and Italy.
The data reportedly spans from 2022 to 2024 and contains detailed information on depositors, former depositors, and individuals targeted for recovery scams, particularly emphasizing high-value depositors.
The advertised dataset includes full names, phone numbers, email addresses, broker information, deposit amounts, and dates of initial deposits (FTD). Additionally, the threat actor highlights a supposed private database specifically related to Coinbase USA. A replacement guarantee is offered for invalid data, indicating confidence in data accuracy.
This leak significantly increases risks of targeted phishing, account takeovers, and recovery scams, exploiting individuals previously impacted by financial losses in crypto and forex trading. The widespread geographic scope further suggests serious regulatory implications under GDPR and other international privacy laws.
Alleged Database of FiveM is Leaked
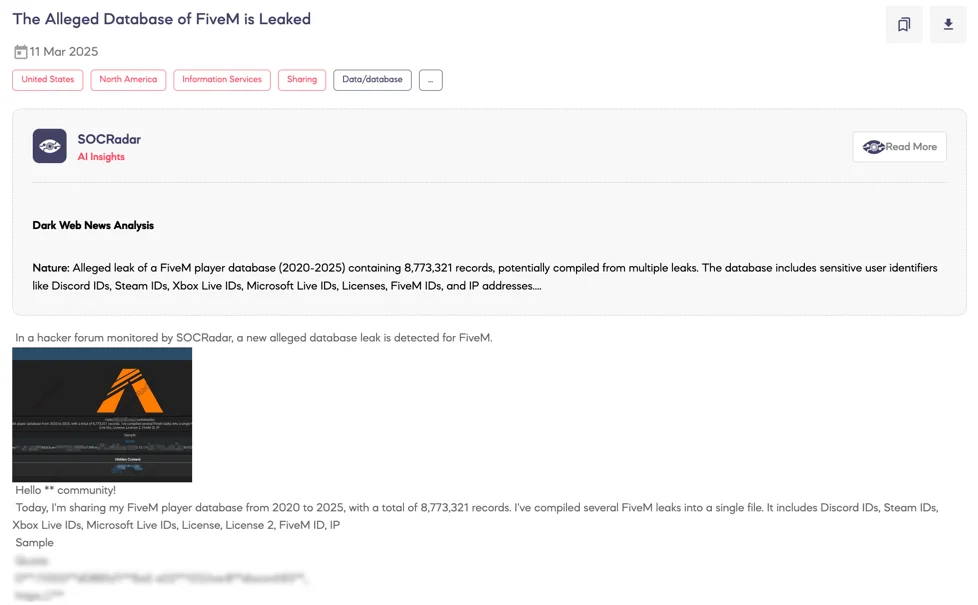
SOCRadar Dark Web Team detected a threat actor claiming to have leaked a comprehensive database allegedly containing over 200,000 records from FiveM and related gaming platforms. According to the actor, the data includes sensitive identifiers such as Discord, Steam, Xbox, Microsoft Live IDs, licenses, FiveM IDs, and associated IP addresses.
The extensive range of identifiers significantly increases the risk of identity correlation, allowing cybercriminals to connect user identities across multiple platforms. The leak raises concerns of identity theft, targeted phishing, and credential stuffing attacks, posing serious risks to affected users. The dataset reportedly exposes licenses, unique user IDs, and IP addresses, enabling further exploitation and targeted cyber operations.
The scope and detail of this alleged leak underline potential privacy implications and increased risk for users across various gaming services.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































