
Major Cyber Attacks in Review: February 2025
In February 2025, several major cyber incidents demonstrated ongoing threats to industries worldwide. The Qilin ransomware attack disrupted operations at Lee Enterprises, severely impacting media distribution. Meanwhile, the FBI attributed a record-breaking $1.5 billion cryptocurrency theft from Bybit to North Korea’s Lazarus Group. Additionally, major breaches at DISA Global Solutions, telecommunications giant Orange, and Russian IT leader LANIT highlighted the breadth of risks facing finance, telecom, healthcare, media, and government sectors.
With this article, we review the major cyber attacks of February 2025, their effects, and essential insights for enhancing cybersecurity resilience.
Qilin Ransomware Group Targeted Lee Enterprises
In February 2025, Lee Enterprises, a major U.S. media company with ownership of 350 publications across 25 states, disclosed a significant cyberattack that affected its operations, both print and online. At least 75 local newspapers were impacted, with disruptions to business applications and a halt in production.
Following the attack, Lee Enterprises confirmed that files were encrypted and sensitive data was extracted, confirming the incident as a ransomware attack.

Lee Enterprises victim listing on Qilin’s site
On February 27, the Qilin ransomware group claimed responsibility for the breach via their Tor-based leak site, suggesting that ransom negotiations had either broken down or the company had refused to pay. The group asserted that they had stolen 350 GB of data, including confidential investor information, financial transactions, details about payments, and records of funding for news stories.
The attackers have warned that unless a ransom is paid by March 5, they will release the stolen information. To back up their claims, they have shared sample files, such as identification scans and internal corporate documents. As of now, Lee Enterprises is still investigating the breach and has yet to provide further updates.
DISA Global Solutions Data Breach Affected 3.3 Million Individuals
It was revealed that DISA Global Solutions, a provider of third-party employment screening services, suffered a significant data breach impacting over 3.3 million individuals.
The company, known for providing drug and alcohol testing as well as background checks, discovered the breach on April 22, 2024. The attack, which took place between February 9 and April 22, 2024, granted unauthorized access to personal information stored within DISA’s systems.
Although the company’s forensic investigation could not definitively confirm the exact data accessed, it is believed that sensitive information such as names, Social Security numbers (SSNs), driver’s license numbers, government ID numbers, and financial account details may have been compromised.
While the company reported that it had taken steps to contain the breach and notified the affected individuals, it has not found any evidence of misuse of the data so far.

Sample notification letter (maine.gov)
Orange Data Breach Exposed Customer Records
In February 2025, SOCRadar’s Dark Web team discovered a hacker forum post where a threat actor claimed responsibility for a data breach involving 600,000 customer records from Orange, a major global telecommunications provider.
The breach reportedly affected Orange Romania and involved additional data from multiple global divisions. The leaked data includes 380,000 unique email addresses, as well as internal documents, contracts, invoices, source codes, employee information, and project details.
The threat actor, Rey, claimed to have had access to Orange’s systems for over a month by exploiting compromised credentials and Jira software vulnerabilities. According to the hacker, they exfiltrated approximately 6.5GB of data in the three hours preceding detection. Then, following a failed ransom negotiation, the actor leaked the information.
Orange confirmed the breach, stating that it affected only a non-critical back-office application and had no impact on customer-facing services.
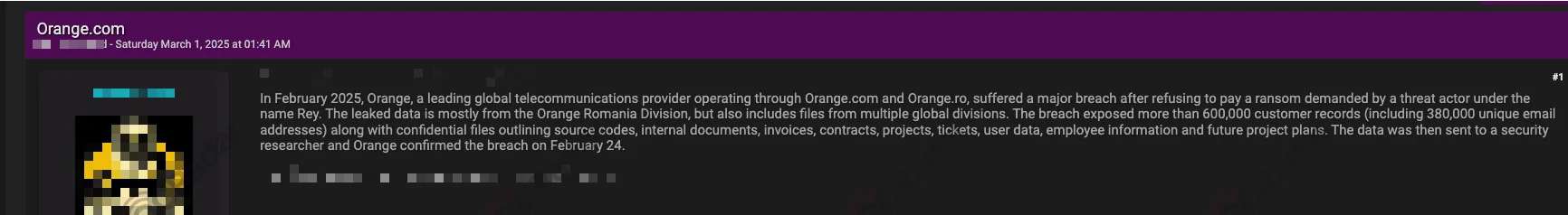
Hacker claims an Orange data breach with a forum post (SOCRadar Dark Web News)
Keep your finger on the pulse of the cyber underworld with SOCRadar Dark Web News. With Dark Web News, SOCRadar XTI uncovers and reports emerging threats, data leaks, cybercriminal trends, and threat actor announcements from hidden forums, Telegram channels, and ransomware leak sites. Stay one step ahead by knowing the threats before they become widespread.
Russian IT Giant LANIT Breached, Impacting Financial Services Subsidiaries
On February 21, 2025, Russia’s National Coordination Center for Computer Incidents (NKTsKI) reported a cyber attack targeting LANIT Group, the country’s largest IT system integrator. The incident affected two subsidiaries, LLC LANTER and LLC LAN ATMservice, which provide critical software for banking equipment, payment solutions, and ATM systems.

Russian IT Giant LANIT Breached (GennadyL, CC0, via Wikimedia Commons)
Due to LANIT’s pivotal role in Russia’s financial and defense sectors, NKTsKI warned that the breach could pose broader risks to other connected organizations.
To limit exposure, NKTsKI recommended that impacted organizations urgently rotate passwords, update remote access credentials, and implement heightened threat monitoring for systems previously managed by LANIT engineers.
Specific details about the attack method and extent of stolen data are currently unavailable.
Lazarus Group Behind $1.5 Billion Bybit Crypto Theft
On February 21, 2025, the FBI publicly attributed a massive cryptocurrency theft of approximately $1.5 billion from Bybit to North Korea’s Lazarus Group, also known as TraderTraitor or APT38. During a routine transfer between cold and hot wallets, the attackers intercepted and redirected the funds into wallets under their control. To conceal the theft, Lazarus quickly converted stolen assets into Bitcoin and other cryptocurrencies, distributing them across numerous blockchain addresses.
According to Bybit CEO Ben Zhou, the attackers exploited vulnerabilities associated with the multisig platform Safe{Wallet}. The Safe Ecosystem Foundation later disclosed the attackers gained unauthorized access to a developer’s machine, enabling them to approve fraudulent transactions that appeared legitimate.
The FBI responded by issuing an alert advising cryptocurrency services to monitor and block activity tied to TraderTraitor, releasing 51 Ethereum wallet addresses involved in money laundering operations.
Salt Typhoon Continues Targeting Global Telecom & ISP Providers
The Chinese threat group Salt Typhoon exploited two critical Cisco IOS XE vulnerabilities – CVE-2023-20198, a privilege escalation flaw, and CVE-2023-20273, which allows command injection – to breach more telecom and ISP companies across the United States, Italy, South Africa, and Thailand.
According to researchers, the attackers targeted over 1,000 Cisco devices, mostly in the U.S., South America, and India, between December 2024 and January 2025.
These vulnerabilities were first exploited two years ago, affecting devices globally, yet many remain unpatched and exposed online despite warnings from Cisco, underscoring ongoing security gaps.
These recent intrusions are part of a larger espionage campaign by Salt Typhoon, previously confirmed by U.S. authorities, involving breaches of private government communications and even infiltration of the U.S. law enforcement’s wiretapping platform.
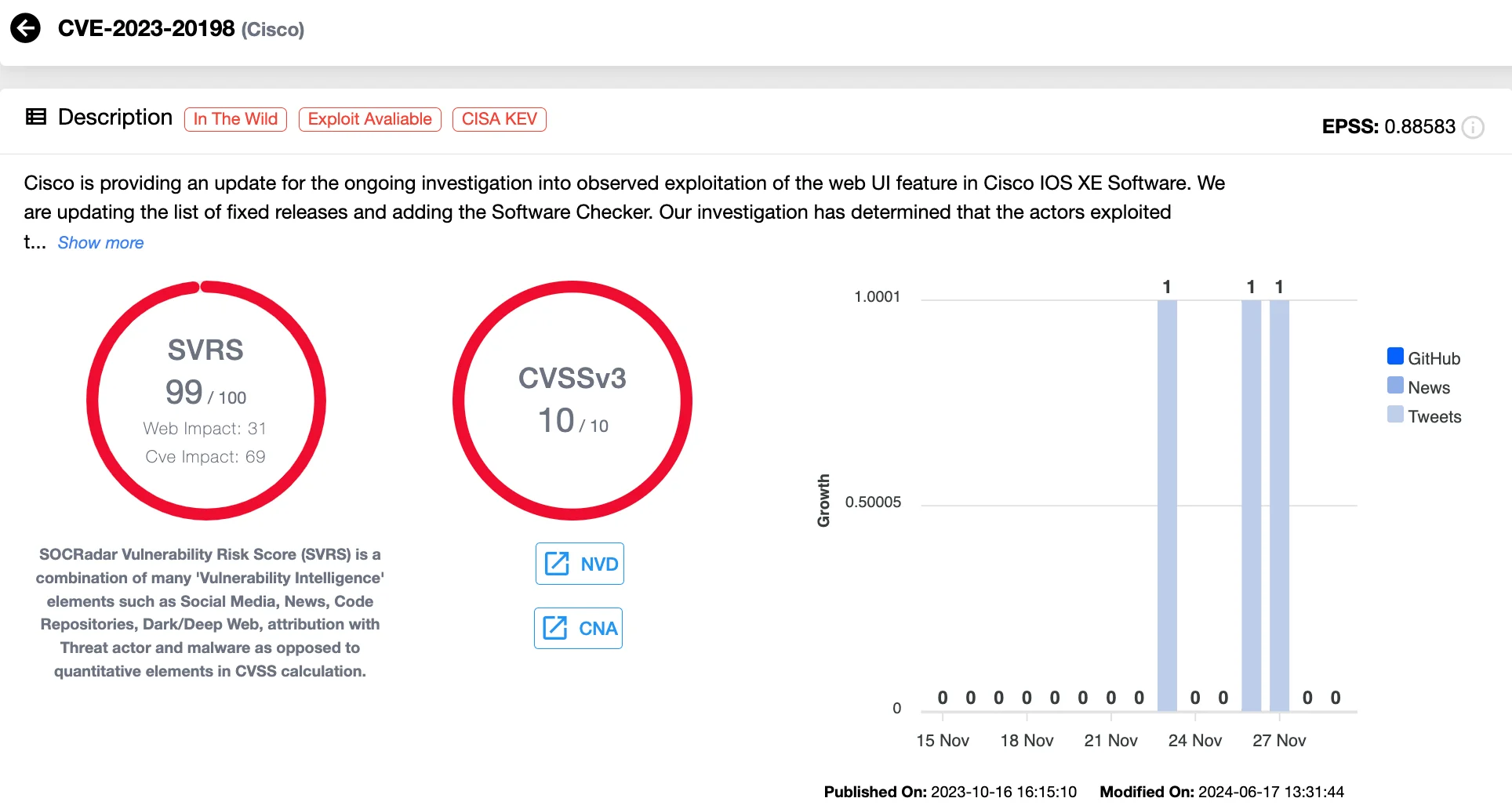
Vulnerability card of CVE-2023-20198 (SOCRadar Vulnerability Intelligence)
Identify vulnerabilities early and understand real-world exploitation trends with SOCRadar’s Vulnerability Intelligence, integrated within the Cyber Threat Intelligence module. Get timely alerts, track threat actor activities, and efficiently prioritize security fixes based on actual threat potential, helping your organization prevent breaches proactively.
Hacker Leaked 12 Million Zacks User Records and Claimed Access to Source Code
In February 2025, Zacks, a financial services company known for its stock-ranking platform, experienced a significant data breach. A cybercriminal operating under the alias Jurak leaked sensitive information belonging to approximately 12 million users, including usernames, emails, addresses, full names, and phone numbers. The attacker claimed to have infiltrated Zacks’ Active Directory as a domain administrator, allowing them to steal source code from the primary Zacks.com website and 16 additional internal sites.
Jurak shared data samples as proof, highlighting their extensive access, and mentioned potentially leaking source code as well, though currently opting against public disclosure.
HSHS Cyberattack Compromised Personal and Medical Data of Over 882,000 Patients
Hospital Sisters Health System (HSHS), a non-profit healthcare organization operating hospitals and clinics in Illinois and Wisconsin, suffered a significant cyber attack between August 16 and August 27, 2023.

HSHS Cyberattack Compromised Personal and Medical Data (Wikipedia)
It was recently revealed that the incident disrupted critical systems and communications, including operational infrastructure and phone lines. Attackers gained access to sensitive patient data, exposing names, birthdates, Social Security numbers, driver’s license numbers, medical records, and addresses of more than 882,000 individuals. Although there is no evidence yet of data misuse, HSHS has provided affected patients with complimentary credit monitoring services for one year as a precaution against identity theft and fraud.
SOCRadar’s Dark Web Monitoring module
Detect leaks of sensitive data and credentials on dark web forums and marketplaces with SOCRadar’s Advanced Dark Web Monitoring. By continuously scanning hidden channels, SOCRadar ensures your team is quickly alerted to potential breaches, enabling swift action to prevent damage, fraud, or identity theft.




































