
Akira Ransomware Targets SonicWall Vulnerability (CVE-2024-40766) – Immediate Patching Required
[Update] October 4, 2024: “Majority of SonicWall Devices Remain Unpatched for CVE-2024-40766, Patch Now!”
[Update] September 10, 2024: “CISA Adds Critical SonicWall Vulnerability to KEV Catalog”
A recently patched SonicWall vulnerability, CVE-2024-40766, has been found to affect the SSLVPN feature of SonicWall firewalls in addition to management access in SonicOS. Moreover, researchers have reported active exploitation by cybercriminals, particularly the Akira ransomware group.
Attackers exploiting CVE-2024-40766 can compromise vulnerable SonicWall devices, gaining unauthorized access to accounts and potentially executing malicious code.
SonicWall has also issued urgent warnings due to exploitation in the wild, advising administrators to apply patches and implement security measures immediately.
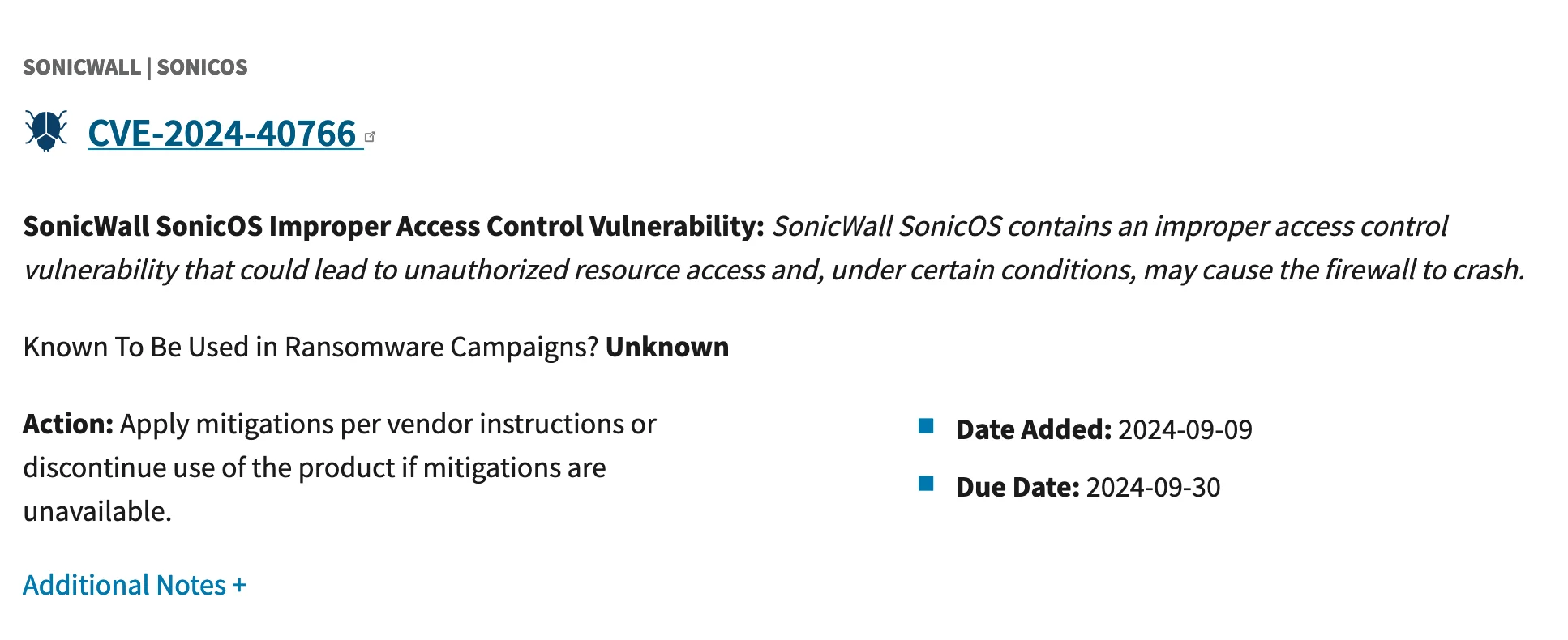
What Is the CVE-2024-40766 Vulnerability?
CVE-2024-40766 (CVSS: 9.3) is classified as a critical access control vulnerability, impacting SonicWall Firewall devices.
Initially, the vulnerability was thought to only impact management access, but further investigations have revealed that it also impacts the firewall’s SSLVPN feature. This has heightened the urgency for affected organizations to implement the necessary updates and security measures.
This flaw can lead to unauthorized resource access and may cause the firewall to crash, effectively disabling network protections.
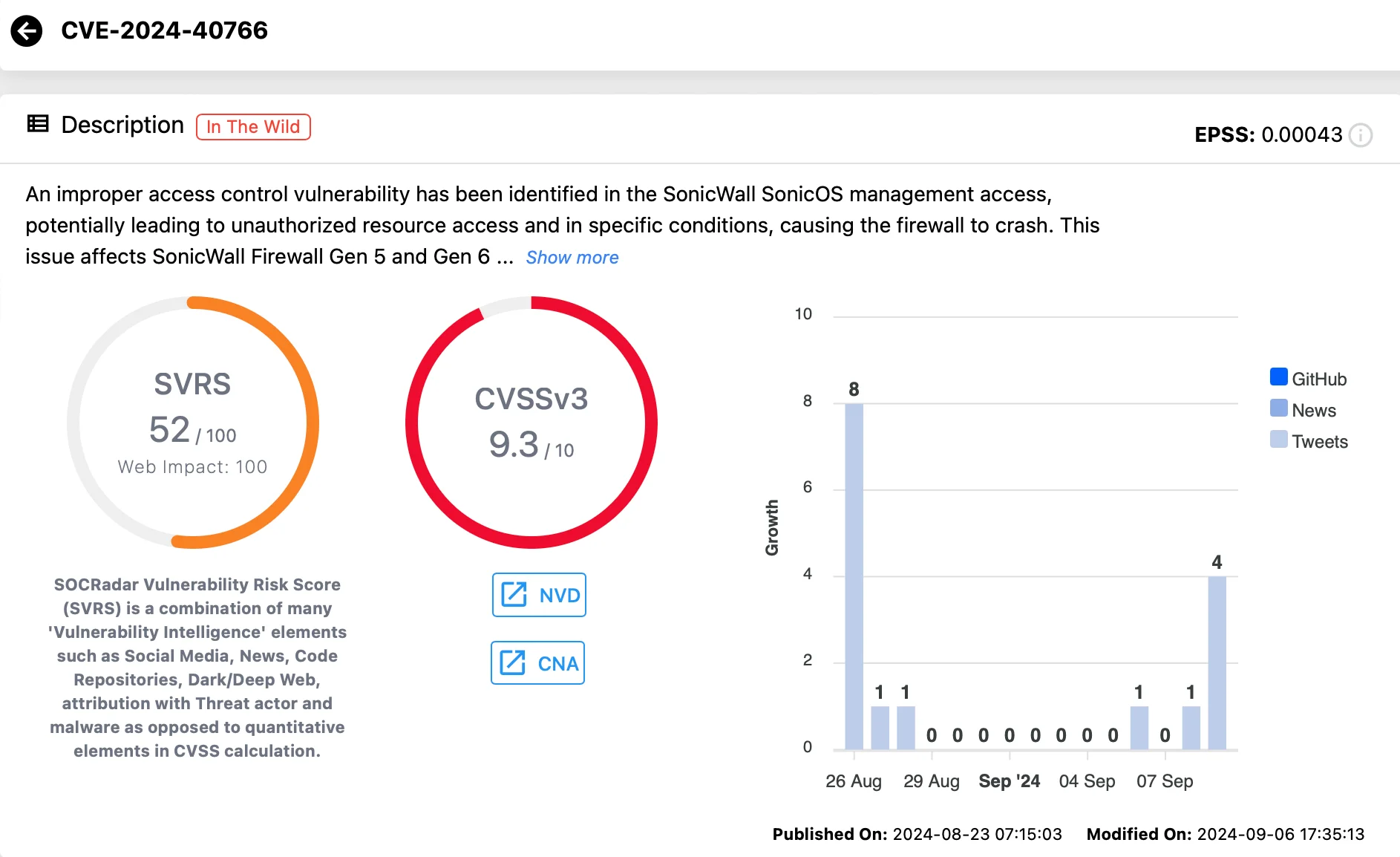
Vulnerability card of CVE-2024-40766 (SOCRadar Vulnerability Intelligence)
The vulnerability’s severity is underscored by its exploitation in the wild, with reports indicating that it is being actively targeted by threat actors.
To combat the escalating threat landscape, SOCRadar’s Vulnerability Intelligence module offers an advanced solution, enabling you to keep pace with the emerging CVEs and exploitation patterns. This essential tool equips you with the insights and actionable information needed for effective vulnerability management and enhanced organizational security.
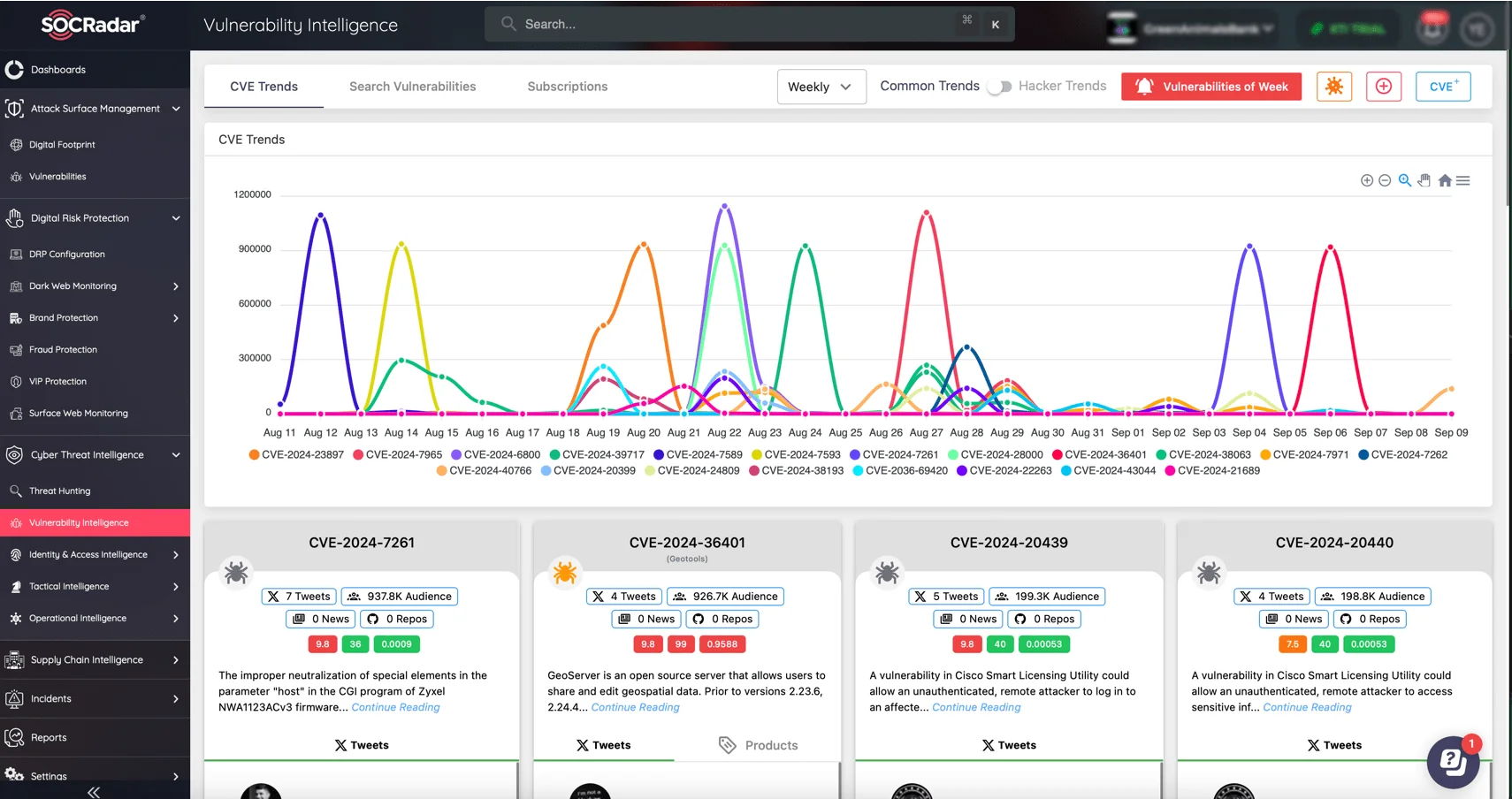
SOCRadar’s Vulnerability Intelligence
By leveraging SOCRadar’s Vulnerability Intelligence module, users can explore the latest vulnerability disclosures, examine real-world exploit trends, and deepen their understanding of the threat environment. Its user-friendly interface and comprehensive insights enable security teams to make informed decisions and prioritize remediation efforts.
Which SonicWall Products and Versions are Affected by CVE-2024-40766?
The following SonicWall products and versions are confirmed to be affected by CVE-2024-40766:
- SonicWall Gen 5 devices with SonicOS version 5.9.2.14-12o and older
- SonicWall Gen 6 devices with SonicOS version 6.5.4.14-109n and older
- SonicWall Gen 7 devices with SonicOS version 7.0.1-5035 and older
A search on ZoomEye reveals over 3.5 million SonicWall Firewall instances exposed to the internet, highlighting a vast potential attack surface.
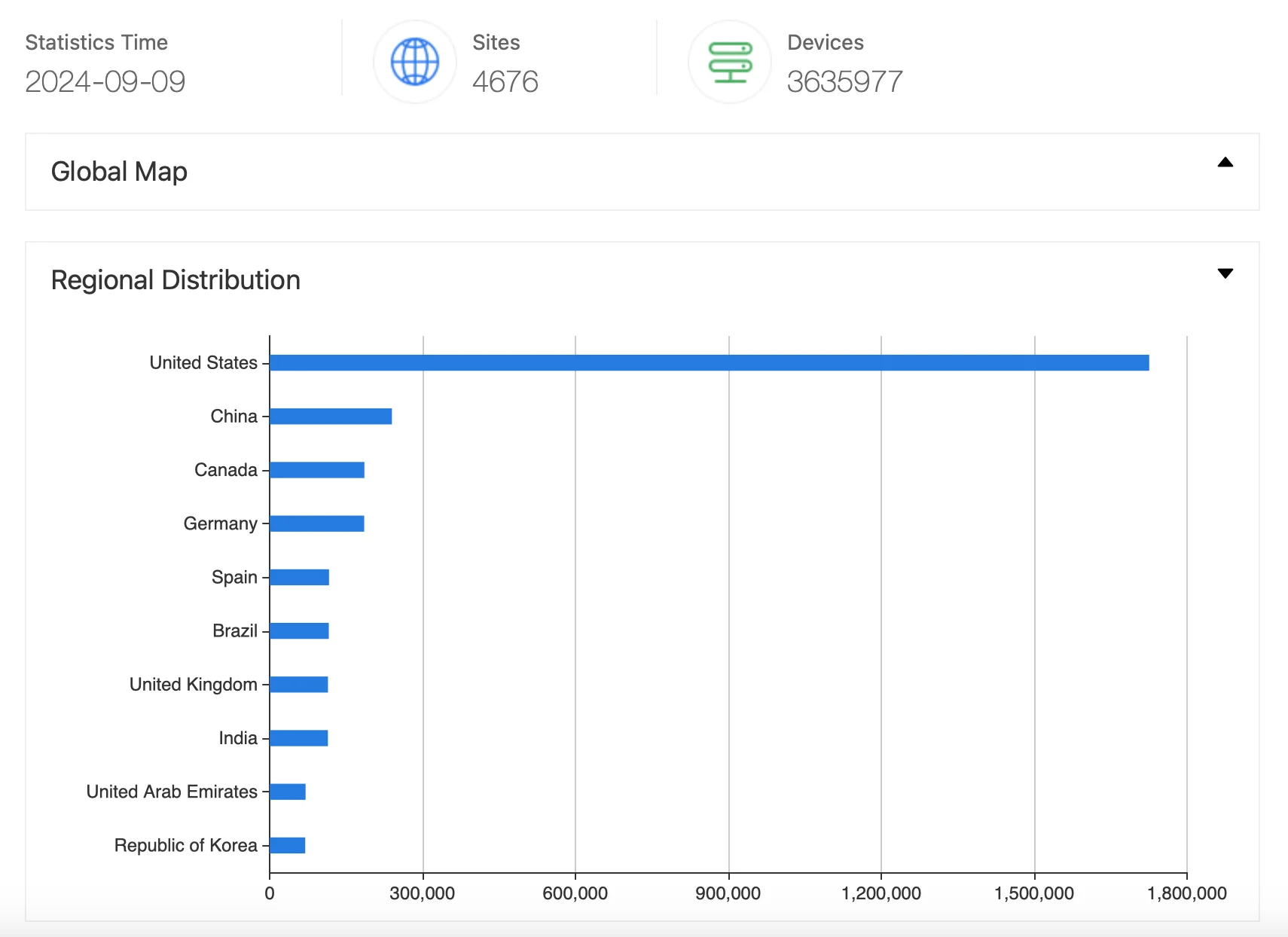
SonicWall Firewall instances exposed over the internet, according to ZoomEye
How Did Akira Ransomware Exploit the SonicWall SSLVPN Vulnerability?
After its announcement in late August 2024, on September 6, SonicWall updated its advisory for CVE-2024-40766 to reveal that the vulnerability now affects both management access and local SSLVPN accounts, and it confirmed that attackers have begun exploiting it.
Researchers reported that the Akira Ransomware group has actively exploited this vulnerability as an initial access vector, compromising SSLVPN user accounts on SonicWall devices. The attackers specifically targeted local accounts, which were not linked to centralized authentication solutions like Microsoft Active Directory. They took advantage of the fact that Multi-Factor Authentication (MFA) was disabled for these accounts.
About Akira Ransomware
Akira ransomware first emerged in March 2023 and has since targeted both Windows and Linux systems. The group operates on a Ransomware-as-a-Service (RaaS) model, providing their software to affiliates in exchange for a share of the ransom payments. Akira employs a double extortion strategy, exfiltrating data before encrypting devices within the targeted network.
The group primarily focuses on large enterprises across North America, Europe, and Australia. For more information, visit our Dark Web Profile article for Akira Ransomware.
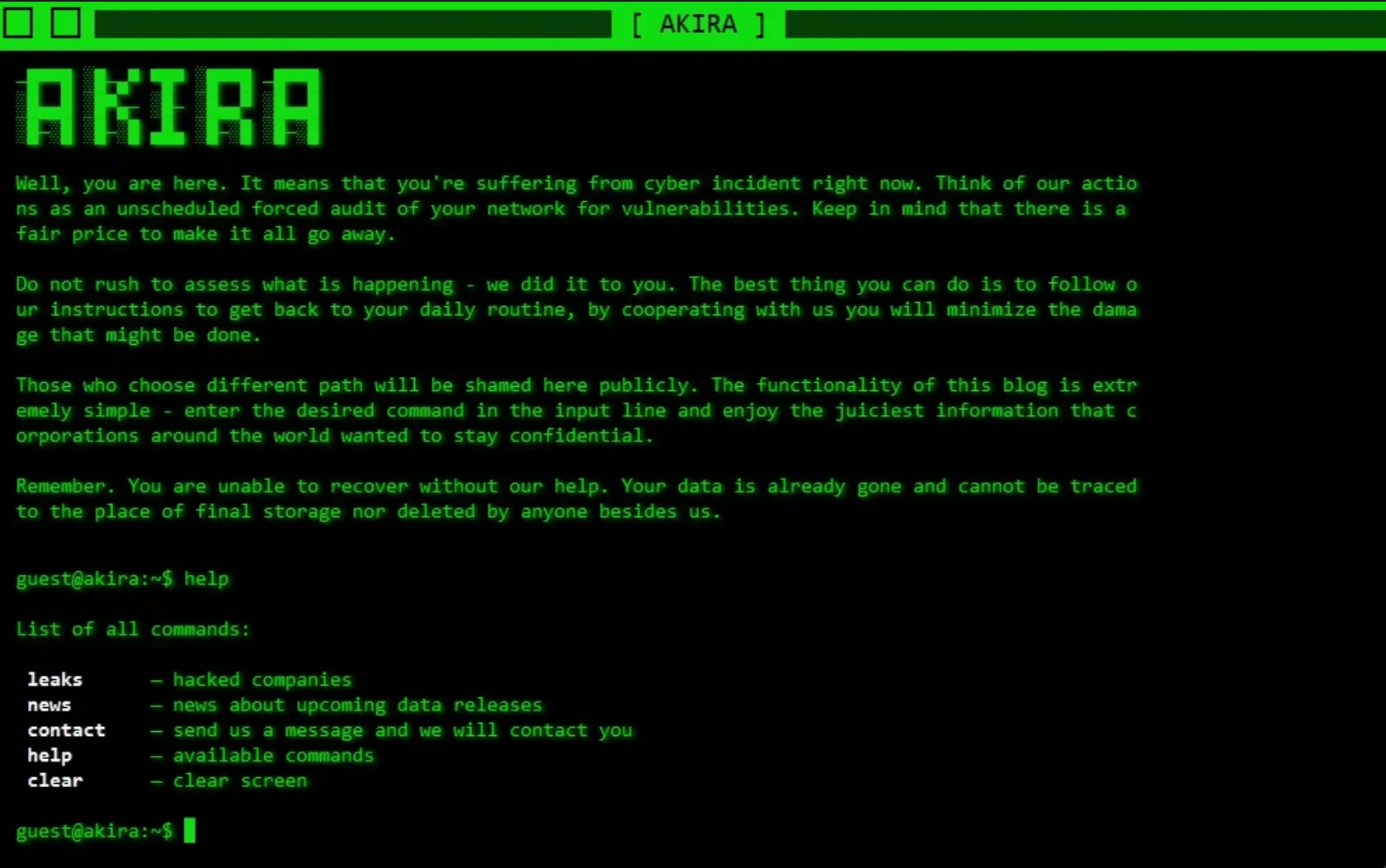
Leak site of Akira ransomware
CISA Adds Critical SonicWall Vulnerability to KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert, adding the critical SonicWall vulnerability, CVE-2024-40766, to its Known Exploited Vulnerabilities (KEV) Catalog.
CISA highlights that vulnerabilities like CVE-2024-40766 are frequently targeted by attackers and pose substantial risks to federal systems. As a result, the agency has mandated that federal organizations apply patches for this vulnerability by September 30, 2024.
Interestingly, in its KEV Catalog listing, CISA has not indicated that this vulnerability has been linked to any ransomware operations.
CISA KEV listing of the CVE-2024-40766 vulnerability
Majority of SonicWall Devices Remain Unpatched for CVE-2024-40766, Patch Now!
SonicWall has reiterated the urgency of patching the critical CVE-2024-40766 vulnerability with an alert, reminding users to apply the patches.
Despite the availability of a patch for over a month, the patch adoption rate remains alarmingly low. Only 10% of affected devices have been updated, leaving 180,000 still vulnerable, according to security researcher Yutaka Sejiyama (@nekono_naha).
Sejiyama’s findings suggest Akira ransomware may have exploited this flaw. In 8 out of 11 recent Akira victims, SonicWall devices were identified, with some patched just weeks before the leaks, indicating a potential pre-patch credential compromise. The focus of concern is the Gen6 series, although Gen5 and Gen7 devices using older firmware are also at risk.
The researcher provided a breakdown of patch status for Gen6 firewalls by country, as follows:
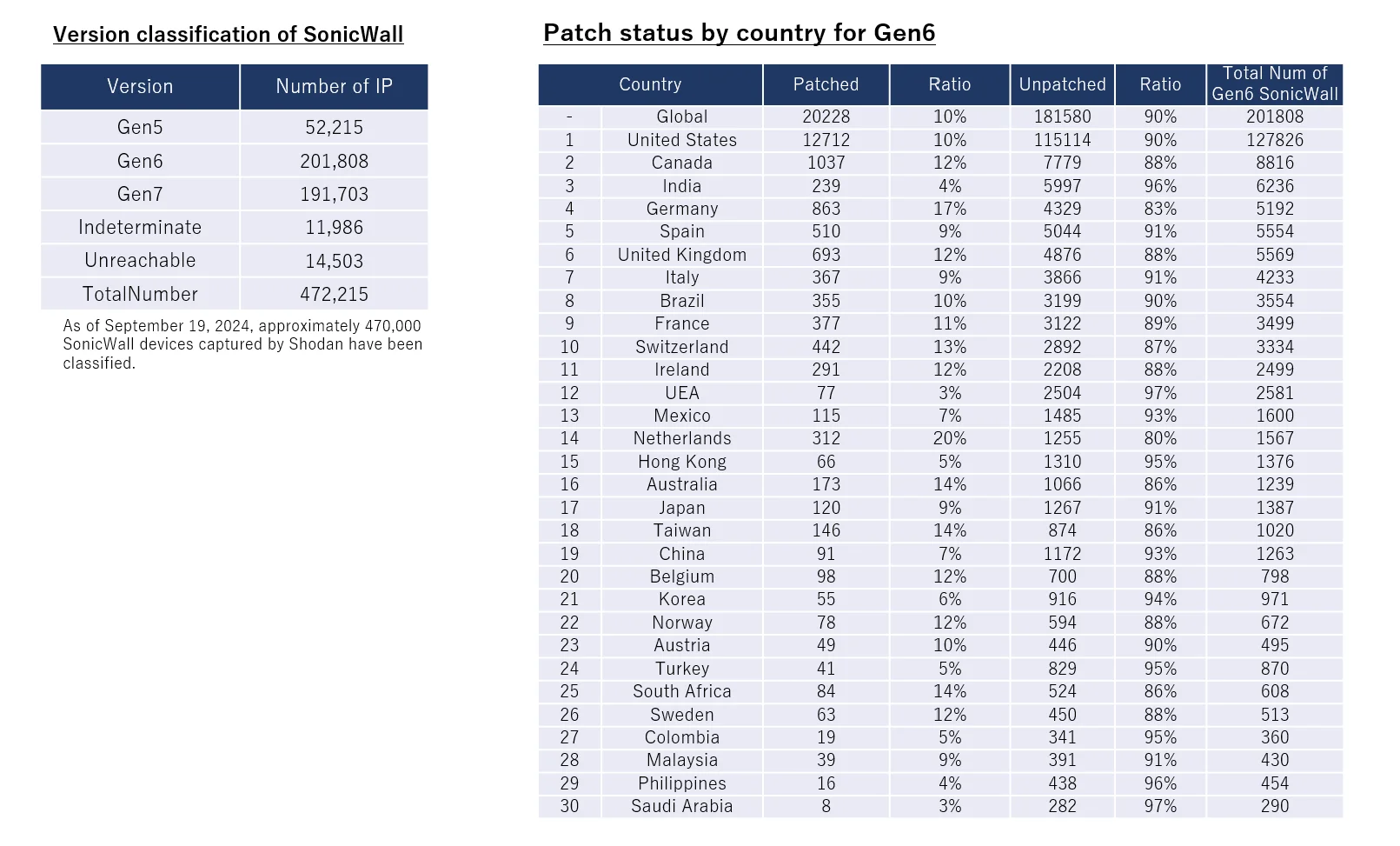
Patch status by country for SonicWall Gen6 firewalls (X)
If you’re using SonicWall, especially Gen6, update your firmware immediately to mitigate CVE-2024-40766 and other vulnerabilities. Take action now to secure your devices from exploitation.
Update SonicOS & Apply These Recommendations
To mitigate the risks associated with CVE-2024-40766, SonicWall strongly urges administrators to take the following actions:
Update SonicOS Firmware: Upgrade to the latest supported SonicOS firmware versions as soon as possible to fix the issue.
Fixes for CVE-2024-40766 are available in the following SonicOS versions:
- For Gen 5 devices, the vulnerability has been fixed in SonicOS version 5.9.2.14-13o.
- For Gen 6 devices, the fix is available in SonicOS version 6.5.2.8-2n, specifically for the SM9800, NSsp 12400, and NSsp 12800 models. For other Gen 6 Firewalls, the vulnerability has been resolved in version 6.5.4.15-116n.
- For Gen 7 devices, the vulnerability is not reproducible in SonicOS version 7.0.1-5035 and later, meaning that these later versions are safe. Users should upgrade to the latest version to ensure complete protection.
The latest patch builds are available for download on mysonicwall.com.
For those unable to apply patches immediately, it is advised to take below steps to mitigate the impact:
- Limit Firewall Management: Restrict management access to trusted sources and disable internet access to the WAN management portal if possible.
- Restrict SSLVPN Access:Limit SSLVPN access to trusted sources only and disable it entirely if not needed.
Further recommendations include:
Password Management: For Gen 5 and Gen 6 devices, SSLVPN users with local accounts should update their passwords immediately. Administrators should enable the “User must change password” option for local users.
Enable Multi-Factor Authentication (MFA):Implement MFA for all SSLVPN users using TOTP or email-based OTPs to enhance security.
Monitor and Respond: Continuously monitor for any suspicious activity and be prepared to respond to potential threats.
To ensure continuous monitoring of your digital assets in the face of ever-evolving vulnerabilities, utilize the power of SOCRadar’s Attack Surface Management (ASM) module.
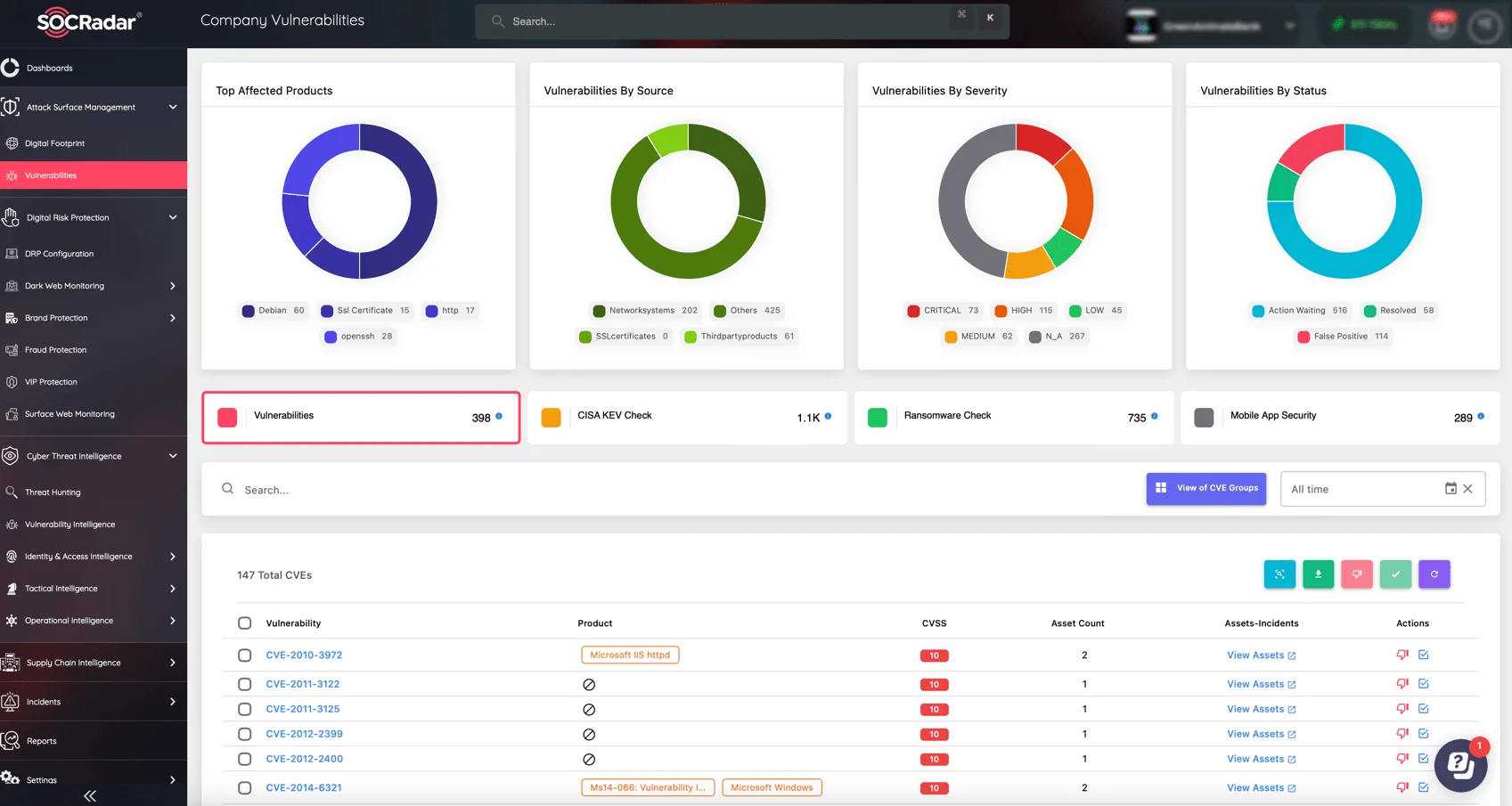
Monitor digital assets, identify and assess vulnerabilities, and take quick actions (SOCRadar’s ASM)
This advanced tool provides comprehensive monitoring and proactive defense, empowering you to stay one step ahead of potential threats.
For more detailed information and guidance on addressing CVE-2024-40766, visit the official SonicWall advisory here.



































