
Alleged Adobe Database Leak, DJI Access Sale, and DDoS Attacks on Polish Websites
The SOCRadar Dark Web Team discovered several alarming posts on hacker forums and Telegram channels, indicating serious cyber threats and data breaches. Recent incidents include alleged database leaks of Adobe and Piramal Group, unauthorized access sales for DJI, and a significant source code breach at Rapid4Cloud.
Furthermore, the pro-Russian hacktivist group NoName057(16) has claimed responsibility for DDoS attacks on several Polish websites, resulting in widespread disruptions.
Receive a Free Dark Web Report for Your Organization:
The Alleged Database of Adobe is Leaked
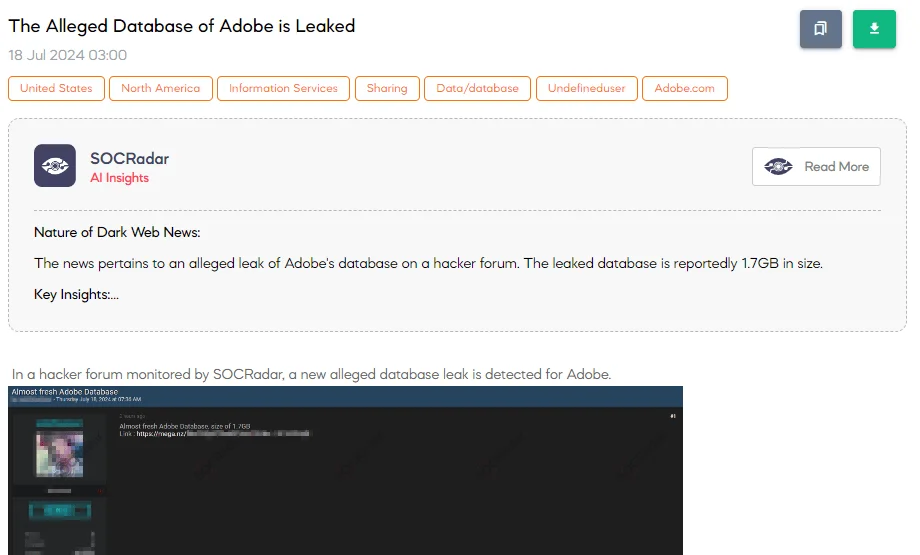
The SOCRadar Dark Web Team detected a post in a hacker forum that a new alleged database leak is detected for Adobe. The threat actor claims that the database is almost fresh, with a size of 1.7GB, and provided a link for download.
Alleged Unauthorized Access Sale Detected for DJI
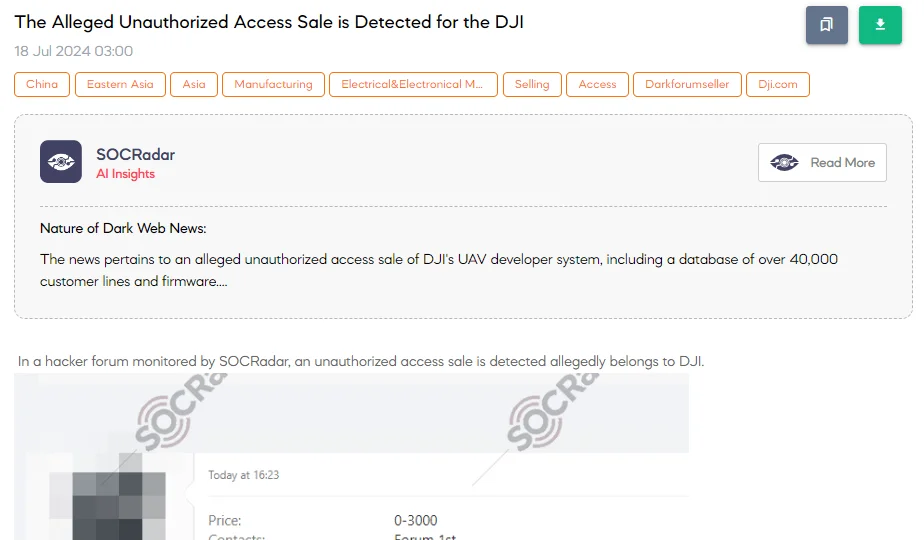
The SOCRadar Dark Web Team detected a post in a hacker forum that an unauthorized access sale allegedly belonging to DJI has been detected. The threat actor claims to offer access to the DJI UAV developer system, including a database of more than 40,000 DJI customer lines and firmware. The offer comes with a negotiable price, proofs of access, and a stipulation that transactions be conducted through a guarantor.
Alleged Data Breach at Rapid4Cloud
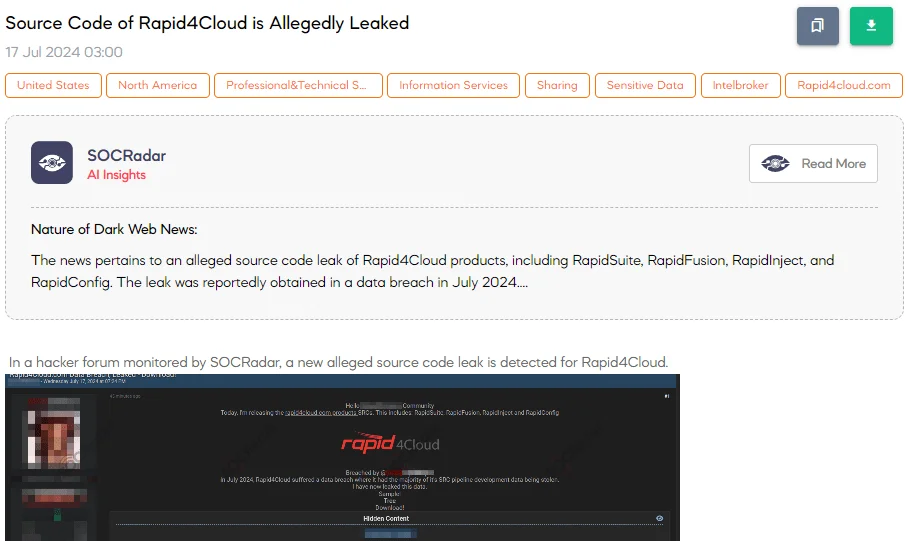
The SOCRadar Dark Web team identified a post on a hacker forum by the notorious threat actor known as IntelBroker, who claims to have leaked a significant source code repository (SRC) allegedly belonging to Rapid4Cloud. The alleged leak includes repositories for several of Rapid4Cloud’s products.
Database of Piramal Group is Allegedly on Sale
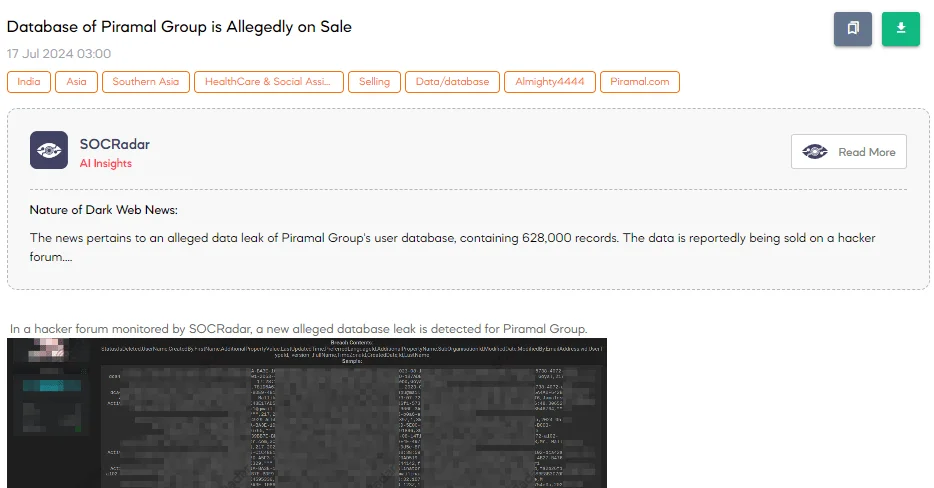
The SOCRadar Dark Web Team detected a post in a hacker forum that a new alleged database leak has been detected for Piramal Group. The threat actor claims the breach affects the Indian multinational conglomerate, Piramal Group, which operates in various sectors including healthcare and real estate. The alleged breach involves 628,000 user records and includes details such as user status, usernames, first and last names, email addresses, organization details, and account creation and modification dates.
NoName057(16) Conducted DDoS Attacks on Polish Websites
The SOCRadar Dark Web Team detected a post on a Telegram channel where a threat actor, pro-Russian hacktivist NoName057(16), claims to have conducted DDoS attacks on several Polish websites. The threat actor stated that they continue to target Poland, causing disruptions to multiple websites, including:
- Trusted Profile (Profil Zaufany)
- A4 Motorway Portal (Autostrada A4)
- Penalty Points Checking (Sprawdzanie Punktów Karnych)
- URBANCARD Tickets for Public Transport in Wroclaw
- NEOBUS POLSKA Czurczak Spółka Komandytowa for Buying Bus Tickets
- Website of the Senate of Poland (Strona Internetowa Senatu RP)
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































