
Alleged Data Leaks of Truist Bank, Twilio Authy, Genesis Market, and Skull OTP BOT
The SOCRadar Dark Web Team has identified several critical cyber incidents involving major financial institutions and technology companies. Notable breaches include the alleged leak of Truist Bank’s customer database, Twilio Authy’s phone numbers, and the source code for Skull OTP BOT. Additionally, the notorious NoName057 group conducted DDoS attacks on Belgium and Bulgaria’s financial infrastructures, and Genesis Market’s database was leaked.
Receive a Free Dark Web Report for Your Organization:
The Alleged Customer Database of Truist Bank is Leaked
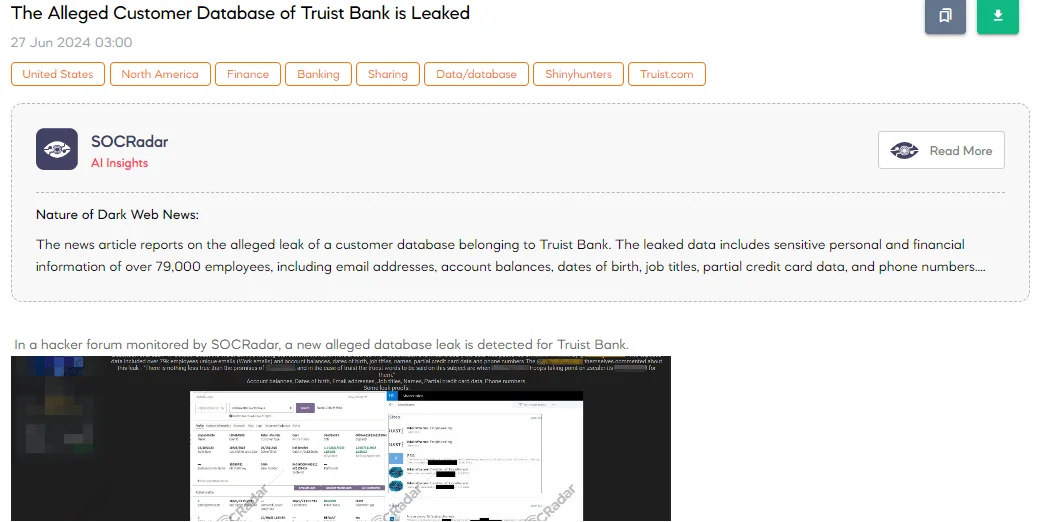
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a database of Truist Bank. According to the threat actor, in October 2023, Truist Bank, a leading U.S. commercial bank, was breached in a cyberattack. The data was then published in June 2024 on a hacker forum.
The exposed data allegedly includes over 79,000 employees’ work emails, account balances, dates of birth, job titles, names, partial credit card data, and phone numbers.
Truist Bank’s database was being sold by a Snowflake-linked threat actor for one million dollars. Although the Truist Bank breach was allegedly linked to Snowflake, Truist Bank has stated that the breach was not connected to Snowflake. For more information on the Snowflake breach, see our blog.
The Alleged Customer Database of Twilio Authy is Leaked
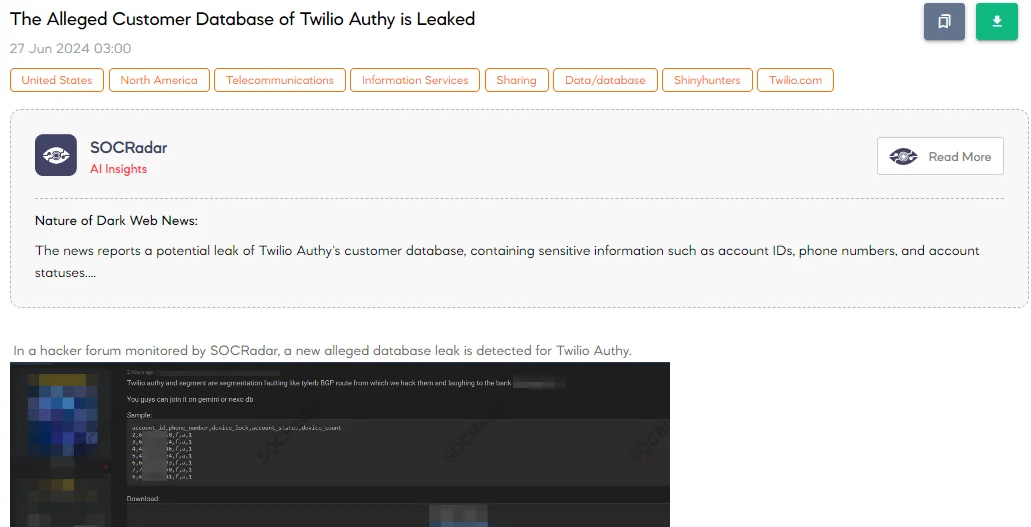
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a database of Twilio Authy, affecting 33 million phone numbers. The threat actor stated that they hacked into Twilio Authy and Segment, revealing account IDs, phone numbers, device locks, account statuses, and device counts.
Twilio confirmed in a security alert that an unsecured API endpoint enabled the threat actors to verify Authy users’ phone numbers. While the company has secured the endpoint, affected users remain at risk of phishing and SIM swapping attacks. Therefore, it is recommended that all Authy users update to the latest Android and iOS apps to enhance security.
NoName057 Conducted DDoS Attacks on Belgium and Bulgaria’s Finance Infrastructures
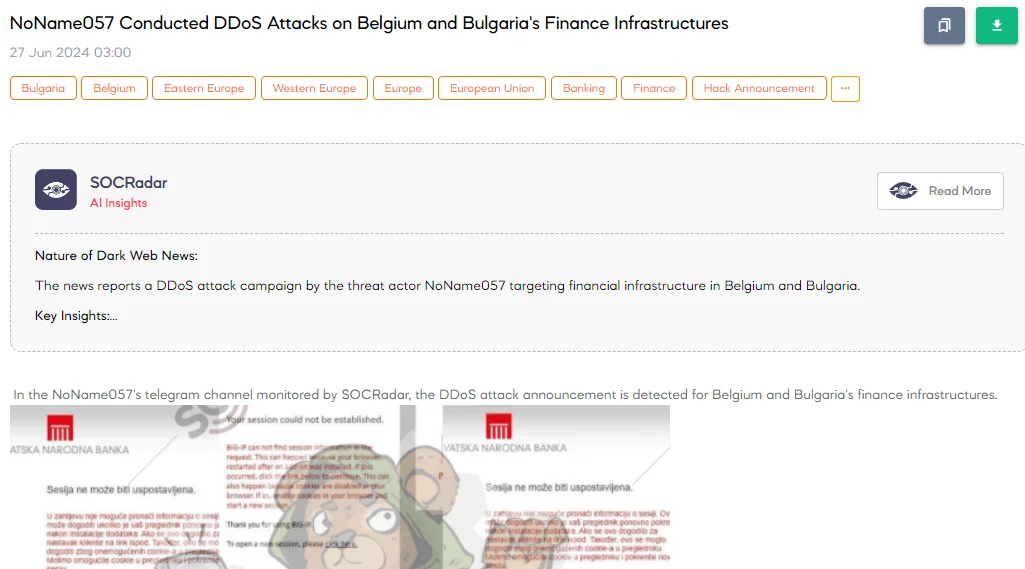
The SOCRadar Dark Web Team detected a post in a Telegram channel that a threat actor, NoName057, announced DDoS attacks targeting Belgium and Bulgaria’s finance infrastructures. The threat actor claims to have attacked several key financial entities, including Febelfin, a non-profit organization providing information about Belgium’s financial sector, the Bulgarian Development Bank (BDB), the API developer portal, the Authorization Bulgarian National Bank, and the Center for Economic Development, a non-governmental organization.
The Alleged Source Code of Skull OTP BOT is on Sale
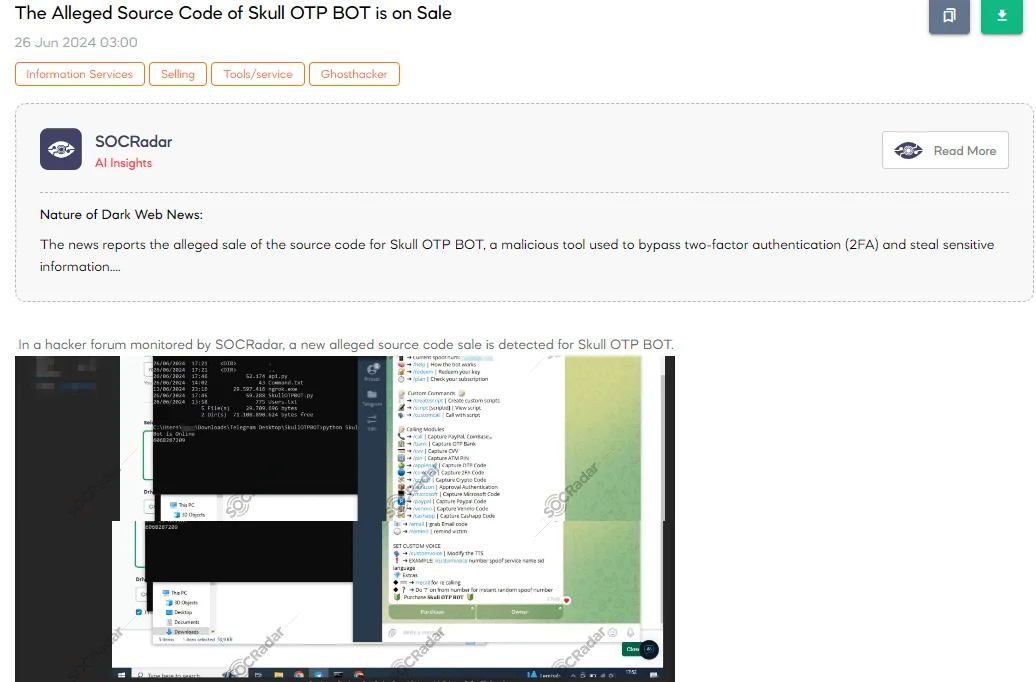
The SOCRadar Dark Web Team detected a post in a hacker forum about a new alleged source code sale for Skull OTP BOT. The threat actor claims that the Skull OTP BOT service can retrieve OTP (One-Time Password) codes from victims using a private caller ID spoofer.
The Skull OTP BOT purportedly offers caller ID spoofing, OTP code bypass, and bypass for any Two-Factor Authentication (2FA) and 3D secure systems. It includes over 70 ready scripts for various banks (e.g., Bank of America, Amex, Vuitton Bank, Discover Bank) and over 40 ready scripts for services (e.g., Chase, PayPal, Apple Pay, Wells Fargo, CashApp). The service also features the receipt of CVV codes, a credit card stealer with PIN option, and PGP & DPGP encryption modes. The alleged price for this service is $250.
This development indicates ongoing efforts to exploit vulnerabilities in multi-factor authentication systems and poses a significant threat to financial and personal security.
The Alleged Database of Genesis Market is Leaked
The SOCRadar Dark Web Team detected a post in a hacker forum that a new alleged database leak for Genesis Market, one of the largest underground marketplaces for stolen credentials, has occurred. The threat actor claims the database, dated September 13th, 2021, contains 1,435,270 lines of SQL data.
In April 2023, the United States Department of Justice announced the successful seizure of Genesis Market’s domain. Dubbed “Operation Cookie Monster,” this effort involved the FBI, Europol, and other international partners, leading to numerous arrests worldwide.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































