
ALPHV’s Roller Coaster, $22 Million Ransom
[Update] March 7, 2024: “Money Paid, Data Retained; ALPHV’s Exit Scam”
The ransomware attack on Change Healthcare has become one of the most disruptive incidents in recent memory, causing widespread chaos in pharmacies across the United States, including hospitals, and leading to significant disruptions in nationwide prescription drug distribution for over ten days. Just after this incident, a substantial plot in the ongoing crisis has been revealed: a partner of the hackers, known as ALPHV/BlackCat, has taken a $22 million transaction, strongly suggesting a large ransom payment.
According to researchers, a post on RAMP known within the cybercriminal community has asserted that UnitedHealth Group (UNH.N) paid $22 million to regain access to data and systems encrypted by the ALPHV ransomware gang. Neither UnitedHealth nor the implicated hackers have provided any statements regarding the purported ransom payment, although a cryptocurrency tracing firm offered partial validation of the claim on Monday.
The identity of the owner or owners of the wallets in question remains undisclosed to the public. However, blockchain analysis firm TRM Labs indicated that the funds’ destination was linked to ALPHV, highlighting that the address had been utilized to gather ransom payments from other victims. UnitedHealth, when queried about the ransom payment, responded solely that its attention was directed towards the investigation and recovery efforts.
Therefore, Change Healthcare did possibly pay a $22 million ransom, but the roller coaster is going down now.
ALPHV Scammed its Affiliate
The individual identifying themselves as an ALPHV affiliate, known as “notchy,” lamented on RAMP that ALPHV had allegedly received the $22 million ransom from Change Healthcare and retained the entire amount, breaching their agreement to share profits with their hacking partner.
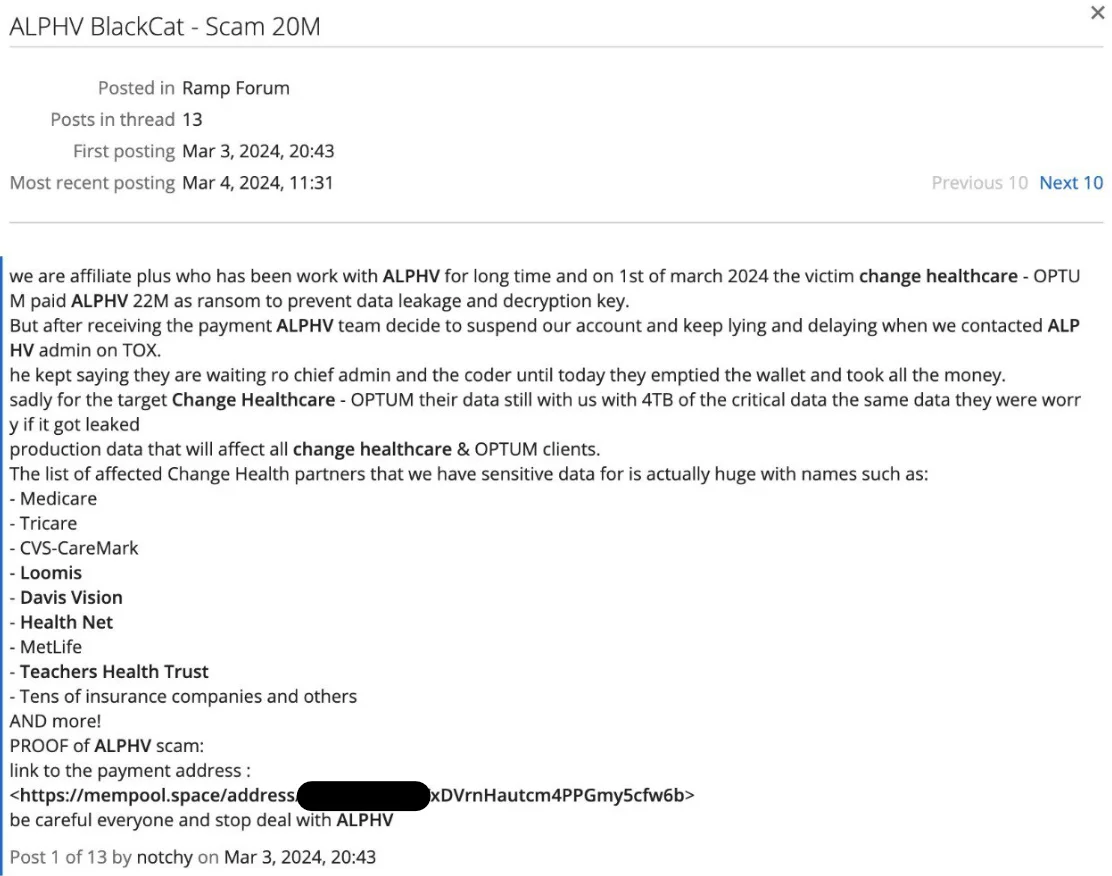
Posted in RAMP Forum, translated into English
The affiliate hacker also claimed to have accessed the data of numerous other healthcare firms partnered with Change Healthcare during their network penetration. If accurate, this claim raises the additional concern that the affiliate hacker may still possess sensitive medical information. Even if Change Healthcare did pay ALPHV, the hacker affiliate could demand further payment or independently leak the data. Similar to LockBit’s recent acts, ALPHV’s aggressive tactics after the initial seizure of their infrastructure also make this possibility very strong. This situation poses a serious danger, especially to US Healthcare. LockBit’s support account was also banned from the largest Russian-speaking forums after a similar incident, and the same fate may be in store for ALPHV.
Regardless of whether Change Healthcare’s ransom payment is confirmed or they are scammers, the recent attacks underscore their unsettling resurgence(?)
Is ALPHV Seized Again?
Immediately after this incident, the FBI announcement appeared again on ALPHV’s new leak site. Security forces continue to clamp down on ALPHV. The attack on the Trans-Northern Pipeline, which also targeted a critical industry, definitely accelerated this seizure. Still, it was not a coincidence that it came immediately upon this news. However, It could be that ALPHV’s blog is linking to their previous mirrored site, which was seized before. Currently, there isn’t definite evidence of a second law enforcement action. Among the allegations, there is also the possibility that they made their last haul and are going to be disappeared.
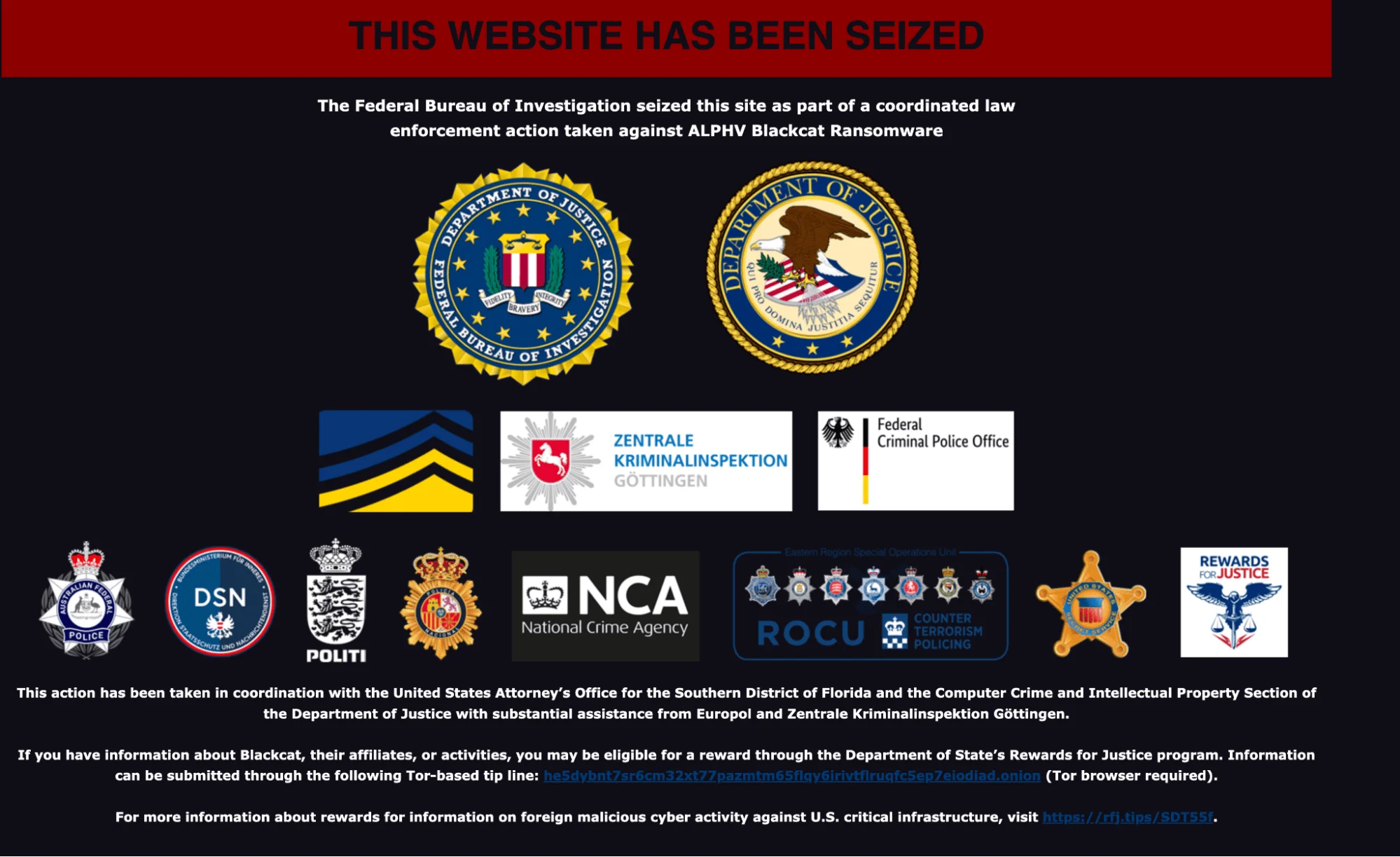
Seizure announcement on ALPHV’s leak site
Dark & Deep Web Monitoring by SOCRadar
Stay one step ahead of cyber adversaries with our comprehensive Dark & Deep Web Monitoring solution. Our cutting-edge technology keeps a vigilant eye on the surface, deep, and dark web, enabling you to identify and neutralize threats before they infiltrate your organization.
SOCRadar Dark Web Monitoring checks every hacker forums and markets
Don’t wait for threats to strike—take control of your cybersecurity with Dark & Deep Web Monitoring by SOCRadar. Stay ahead of the curve and protect what matters most.
Money Paid, Data Retained; ALPHV’s Exit Scam
The alarming update is the ransom could have been paid, but the data wasn’t deleted. The affiliate, Notchy, mentioned that they still retained Change Healthcare’s data. Change Healthcare has neither confirmed nor denied making the payment; instead, they are still focusing on its investigation and service restoration. However, it seems to have backfired if they did pay, as Notchy claimed they still possessed sensitive data from Change Healthcare partners.
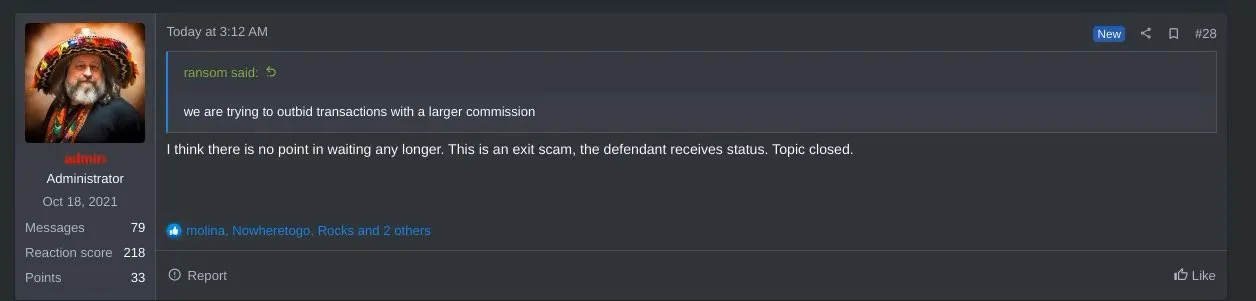
Even the administrator for RAMP, who is responsible for making a judgment in the scam claim for ALPHV has accepted the group is conducting an exit scam. (X)
Therefore, ALPHV scammed its affiliate, and now they are up to a bigger scam. BlackCat announced its shutdown and sale of its ransomware source code, attributing it to pressure from law enforcement. The FBI seizure notice on BlackCat’s website still raises doubts as it appears copied from a previous raid. Affiliates are upset about not receiving promised payments. So, as we stated in the claims, it looks like ALPHV is really exiting the cybercrime landscape with $22 million. The sale of the source code also means that we will see BlackCat variants for a longer time, and BlackCat developers may also come up with a new name and ransom strain.
Stay tuned to our blog for updates on the incident.




































