
Analysis of Stealer Logs within the Entertainment Industry
Stealer logs – databases of stolen information that vividly depict compromised security – are one of the many pieces that hold together the digital underworld. Cybercriminals find a wealth of useful information in these logs, which usually contain sensitive information such as payment card numbers and user credentials, typically used for fraud and initial access.
The wealth of information found in stealer logs is collected by infostealer malware, in an autonomous way, casting shadow over industries far and wide. These dangerous software quietly infiltrate computers, siphoning sensitive data with superb precision. From personal credentials to financial information, the material gathered then makes its way into the eerie corners of dark web forums, where it becomes currency for illegal trades and fuel for a variety of cyber attacks.
To counter such threats, check out SOCRadar’s Threat Hunting module, a ray of hope in the fight against cyber intrusion. It allows defenders to sift through massive amounts of data within gathered stealer logs, giving them the tools they need to identify and neutralize threats before they cause havoc.
SOCRadar’s Threat Hunting page
Focusing on the subject of our blog post: it is undeniable that the entertainment industry stands as a prime target of stealer malware. Leveraging our Threat Hunting module, we ventured into the labyrinth of stolen data, analyzing trends and dissecting cases of popular names, such as Netflix and Spotify.
In this blog post, we will take a journey through the corridors of cybercrime, shedding light on the complex web of data theft that plagues the entertainment industry.
Scope of the Entertainment Industry Stealer Logs
The entertainment industry is a vast and diverse sector that encompasses various forms of media, including movies, music, television shows, and online streaming platforms. As with any industry, the entertainment sector is not immune to cybersecurity threats, and one such threat is the presence of stealer logs.
Concerningly, the presence of stealer logs indicates a security breach and potential harm to individuals or organizations within the entertainment industry. The logs may contain sensitive information that can be exploited for financial gain or other malicious purposes.
Following is a list of the leading global entertainment websites currently, potentially facing an elevated risk of encountering stealer logs:
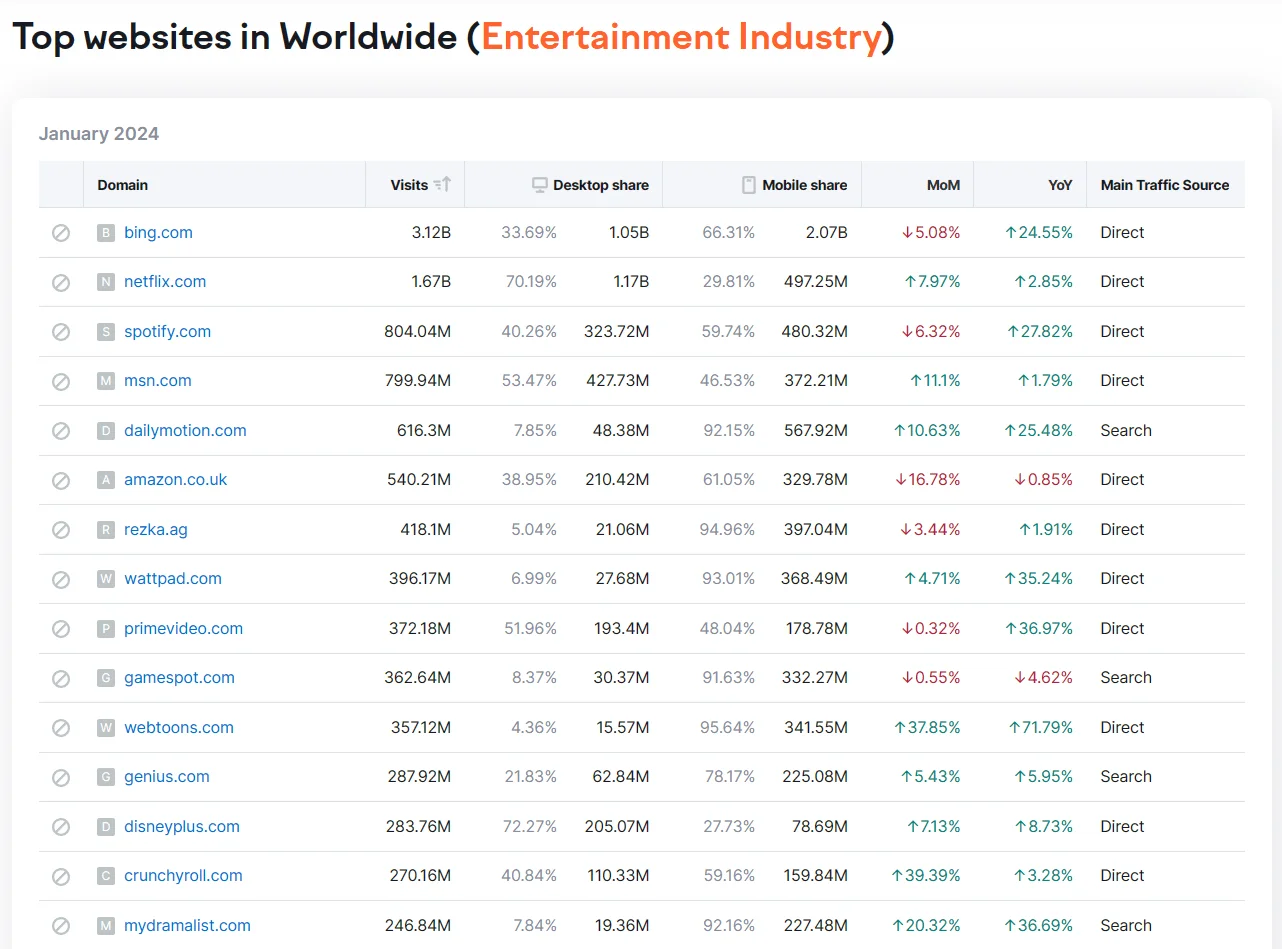
A list of top entertainment industry-related websites worldwide (Semrush)
Among these, we chose the genius.com domain as our 10th selection instead of wattpad.com, which was originally in the top 10 at the time of writing. Our top 10 to examine will be as follows:
- Bing.com
- Netflix.com
- Spotify.com
- Msn.com
- Dailymotion.com
- Amazon.co.uk
- Rezka.ag
- Genius.com
- Primevideo.com
- Gamespot.com
In this article, we will analyze the data gathered from stealer logs within the entertainment industry, focusing on the following aspects:
- Domain Count: This refers to the number of unique domain names found within the stealer logs. Domains are the addresses used to access websites, and a high domain count may indicate a wide range of targeted websites within the entertainment industry.
- Email Count: The email count represents the number of email addresses that have been compromised and are present in the stealer logs. Email addresses are often used for communication and account verification purposes, making them valuable targets for cybercriminals.
- URL Count: The URL count in the stealer logs indicates the number of unique web page addresses that have been compromised.
- CC/BIN Count: CC stands for credit card, while BIN refers to Bank Identification Number. The CC/BIN count in the stealer logs represents the number of compromised credit card details or bank identification numbers associated with the accounts. This information can be used for fraudulent activities or unauthorized transactions.
- Hash Count: Hashes are unique alphanumeric strings generated from data using cryptographic algorithms. In the context of stealer logs, the hash count refers to the number of hashed passwords or other sensitive information that has been compromised.
First Look at the Stealer Logs
In our investigation of stealer logs within the entertainment industry, we examined logs from a total of 143 domains, associated with various stealer malware and threat actors, including Redline Stealer, Meta Stealer, Crypton, You Logs, Lulzsec, and Expert Logs.
Let’s examine the number of domains the stealer logs targeted, per platform:
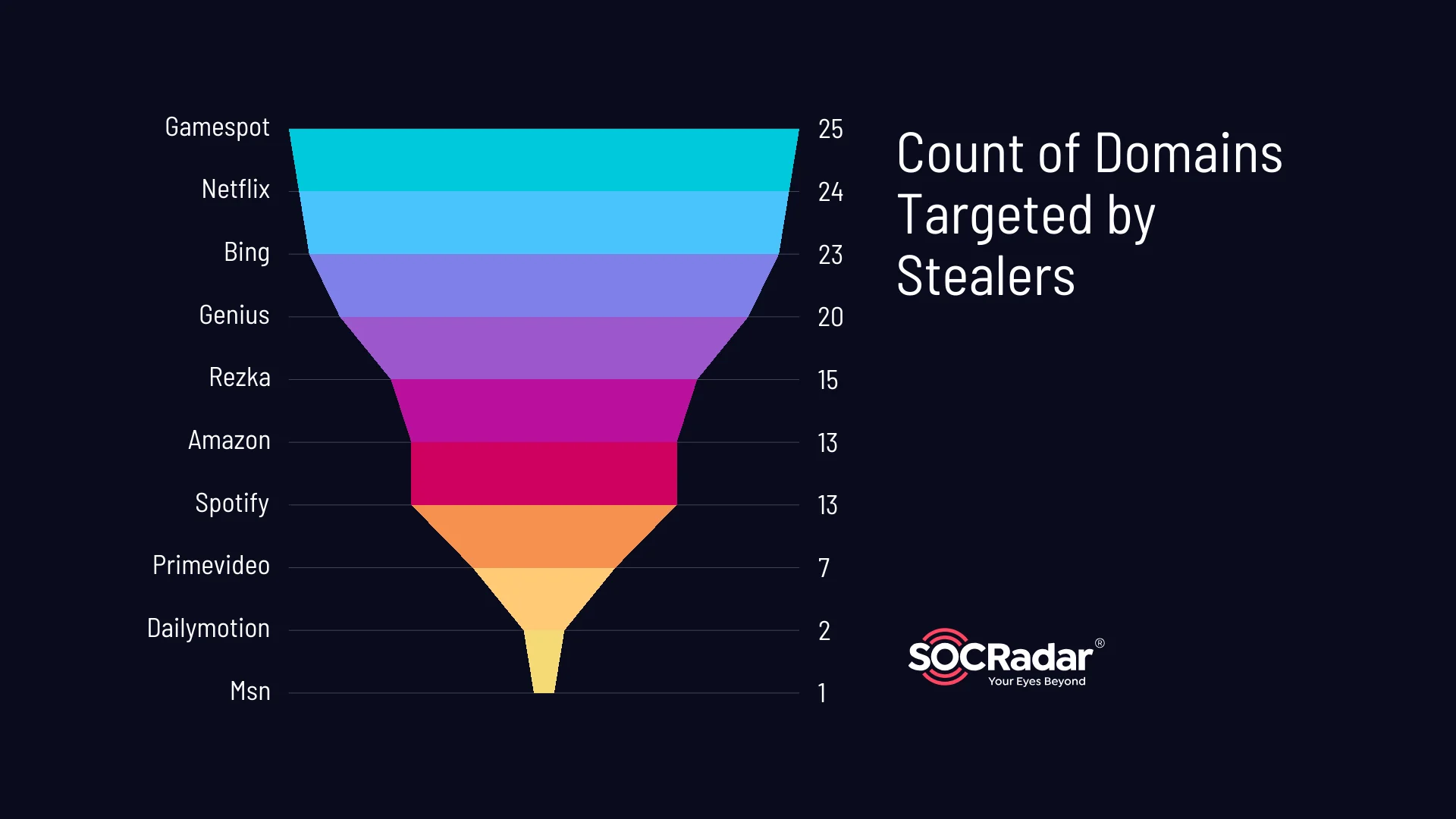
Count of related domains targeted by stealers
Among these, Gamespot and Netflix had the highest number of domains targeted by stealer logs, with 25 and 24 domains respectively. This suggests that these platforms may be more frequently targeted by cybercriminals aiming to pilfer user information.
To further analyze the impact of these stealer logs, we examined the count of records associated with each domain. Here are the top domains in terms of the count of records:
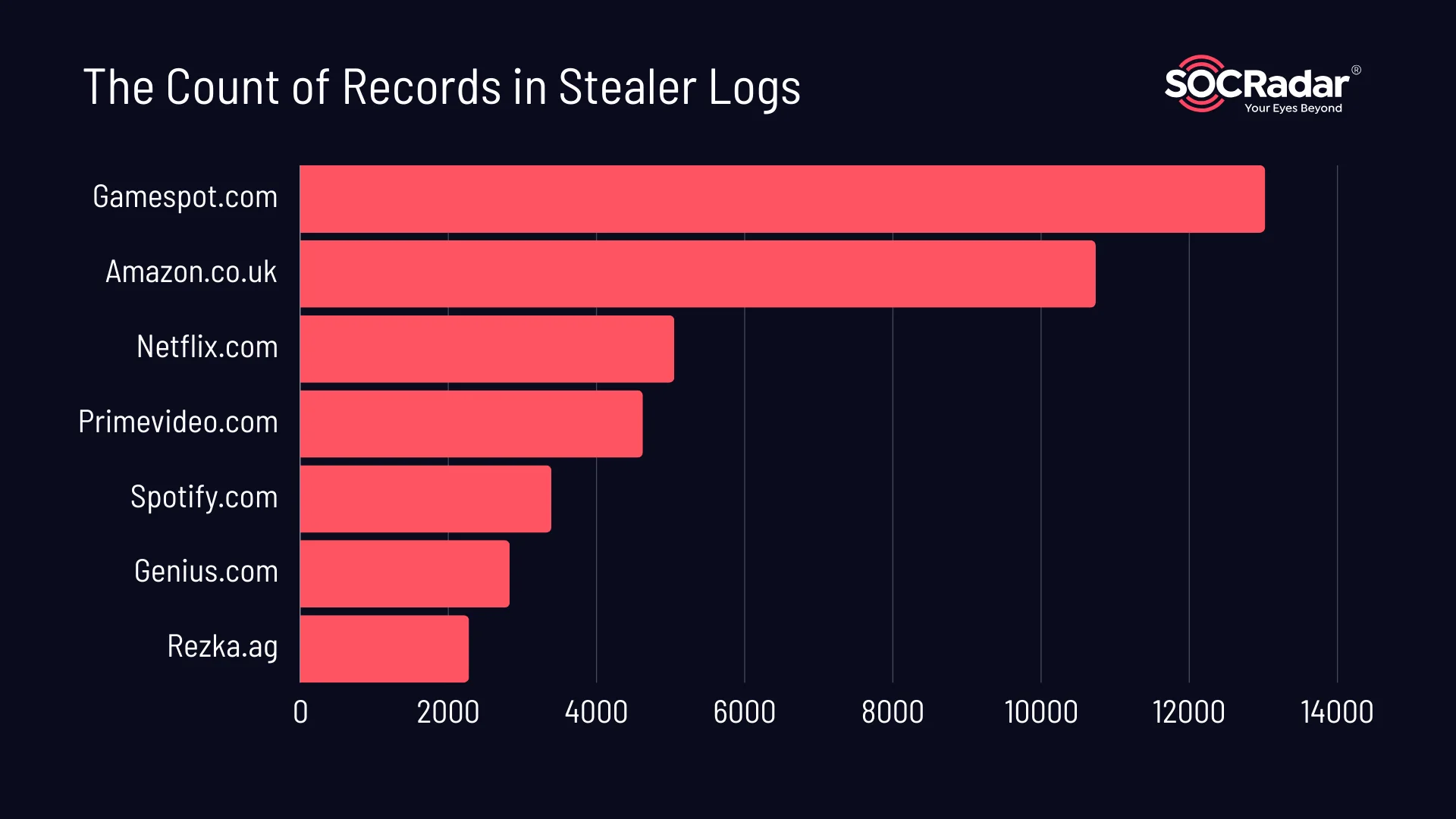
Bar chart depicting the count of records in stealer logs.
The chart illustrates the volume of compromised data associated with each domain. Gamespot.com stands out with a significantly higher line count of 13,025, implying a substantial amount of compromised user information. Amazon follows in second place. In contrast, the stealer logs related to Dailymotion, Bing, and MSN collectively contain less than 500 lines of data, as we have not included them in the chart. When considering all 10 domains, the total number of records amounts to 42,284.
By leveraging SOCRadar’s proactive threat intelligence approach and insightful alarms, organizations can enhance their security measures and mitigate potential threats at an earlier stage, ensuring heightened awareness and protection against emerging risks.
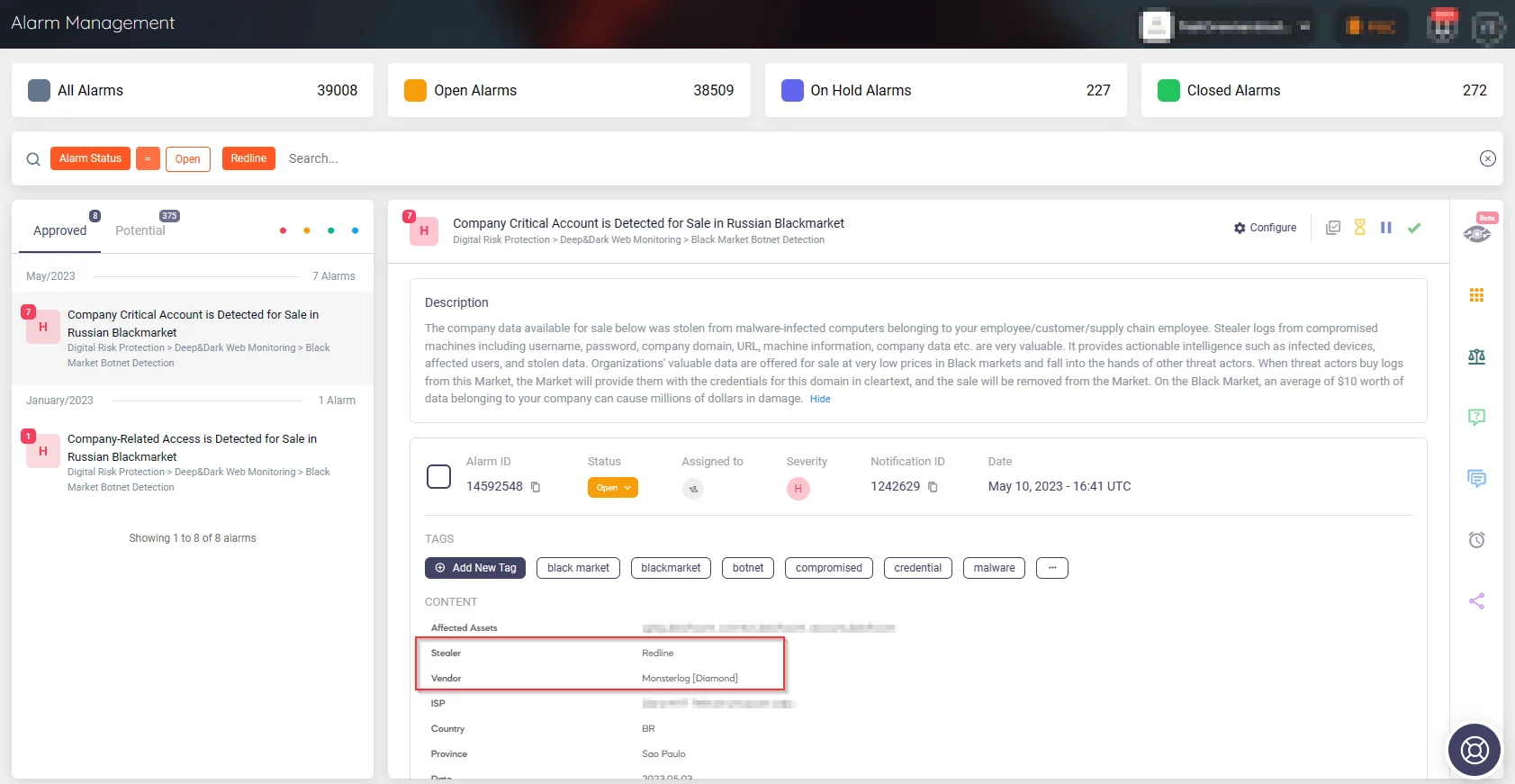
Alarm: Company Critical Account is Detected for Sale in Russian Blackmarket (SOCRadar)
Geographic Trends in the Entertainment Industry Stealer Logs
Understanding the geographic distribution of stealer logs within the entertainment industry can provide valuable insights into the regions most prone to subsequent cyber threats.
Based on the log counts, it is evident that certain countries have been targeted more frequently. The top victim countries in terms of log counts are as follows:
- Mayotte (YT): 27 logs
- Brazil (BR): 14 logs
- Ukraine (UA): 9 logs
These three countries account for a significant portion of the stealer logs analyzed. Mayotte, a small overseas department of France, surprisingly takes the lead with the highest number of logs, followed closely by Brazil and Ukraine.
To further understand the distribution, let’s consider the victim country distribution by percentage. This metric allows us to gauge the relative impact of the stealer logs in each country. The percentages of victim country distribution are as follows:
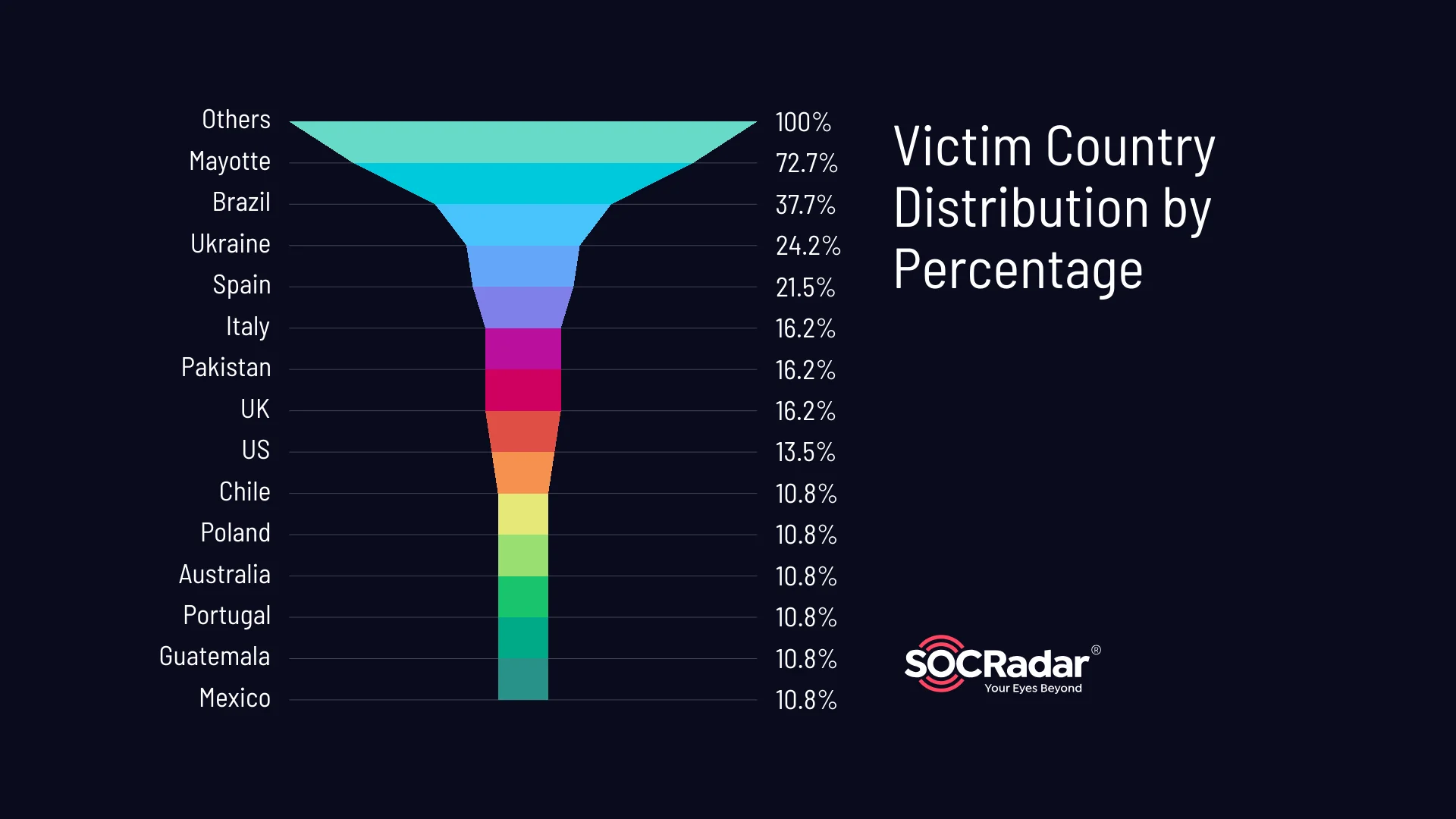
Victim countries’ distribution
The “Others” category includes several countries that individually represent smaller percentages, such as Morocco, Argentina, and Colombia, as well as some mixed logs. However, when combined, these account for a significant proportion of the victim country distribution.
Analysis of E-mail, Credit Card (CC), and Hash Information
In this section, we will analyze the e-mail, credit card (CC), and hash information extracted from the logs, along with the top countries associated with each type of data.
The average counts across all logs provide a general overview of the prevalence of different data types within the stealer logs:
- Email Count: 20
- URL Count: 166
- CC/BIN Count: 4
- Hash Count: 26
These average counts give us an idea of the scale and magnitude of compromised data present in the logs. However, it is important to note that these numbers significantly depend on the specific log.
E-mail inclusion is observed in all logs, indicating that cybercriminals prioritize the acquisition of e-mail addresses due to their value in various cyber activities. E-mail accounts are often linked to personal or professional information, making them valuable targets for phishing attempts, identity theft, or unauthorized access to online services.
Out of the total logs examined, a staggering 22,591 records contained email addresses. When examining the email service domains used in these records, several prominent platforms emerged. The top email service domains found within the entertainment industry stealer logs were:
- Gmail: Gmail is the most prevalent email service domain targeted by cybercriminals, as proven again with a substantial count of 16,665 records.
- Mchsi: Mchsi, with 588 records, is another legitimate email domain that appeared in the stealer logs. It is not as widely recognized as Gmail or Hotmail.
- Hotmail: While not as prevalent as Gmail, Hotmail still appeared in 566 records within the stealer logs. Hotmail, now known as Outlook.com, remains a popular email service provider, and its inclusion in the logs suggests that cybercriminals continue to target users of this platform.
- Yahoo: Yahoo, a well-known email service provider, appeared in 258 records within the stealer logs. Having faced security breaches in the past, Yahoo’s large user base and extensive range of services continue to make it an attractive target.
Credit card (CC) and Bank Identification Number (BIN) information is present in approximately 38.46% of the logs. This indicates a substantial risk considering the potential for financial fraud or unauthorized transactions. The top three countries associated with CC inclusion are Mayotte (49.09%), Brazil (10.91%), and Italy (7.27%).
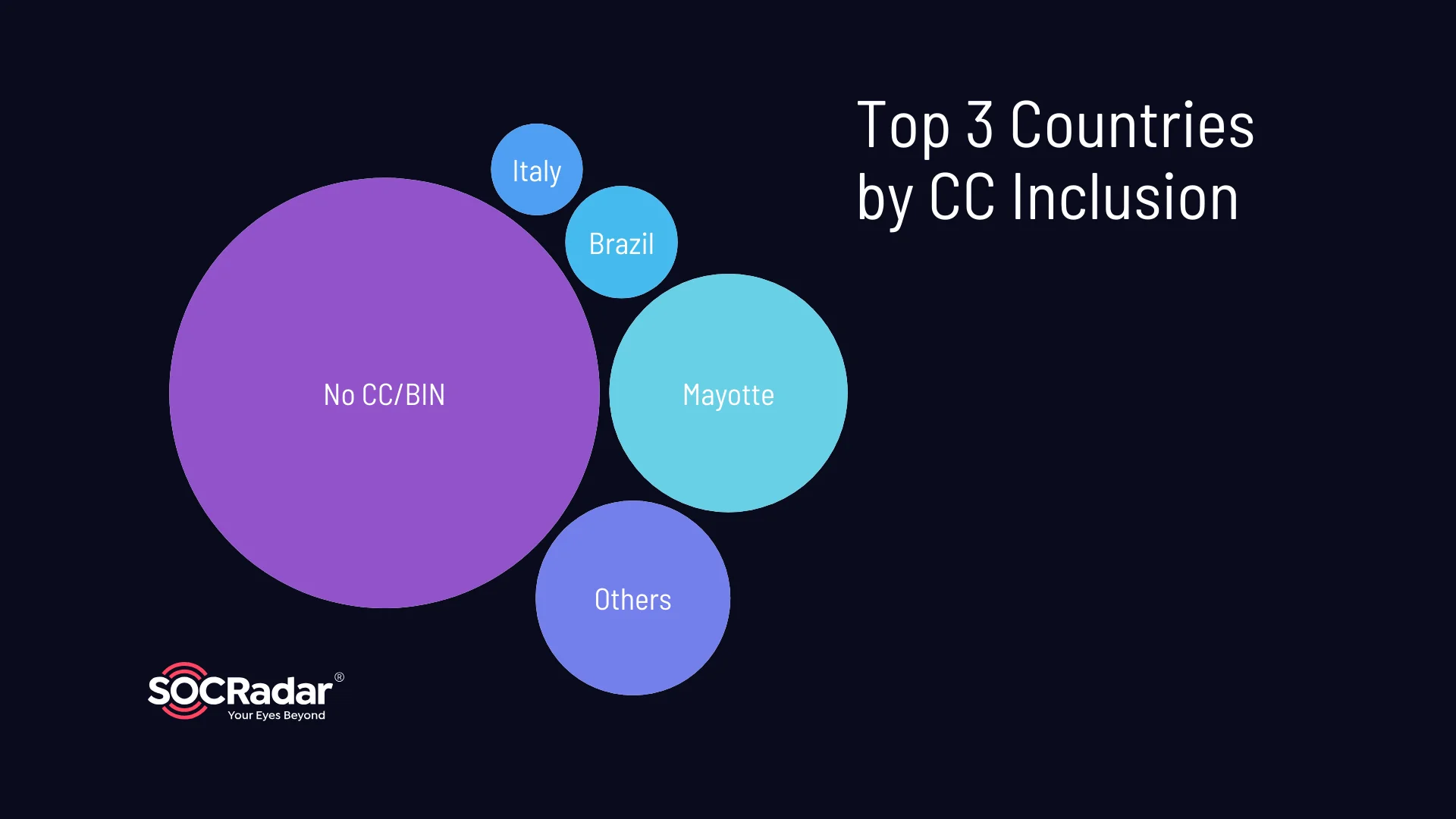
Top 3 countries by CC/BIN inclusion
These countries have a higher concentration of compromised credit card information within the stealer logs, suggesting a higher risk for financial fraud or misuse of credit card details.
Hash information, which represents hashed passwords or other sensitive data, is found in around 68.53% of the logs. The presence of hashed information poses a significant risk as cybercriminals can attempt to crack these hashes to gain access to user accounts or decrypt sensitive data. The top three countries associated with hash inclusion are Mayotte (27.55%), Ukraine (9.18%), and Brazil (8.16%).
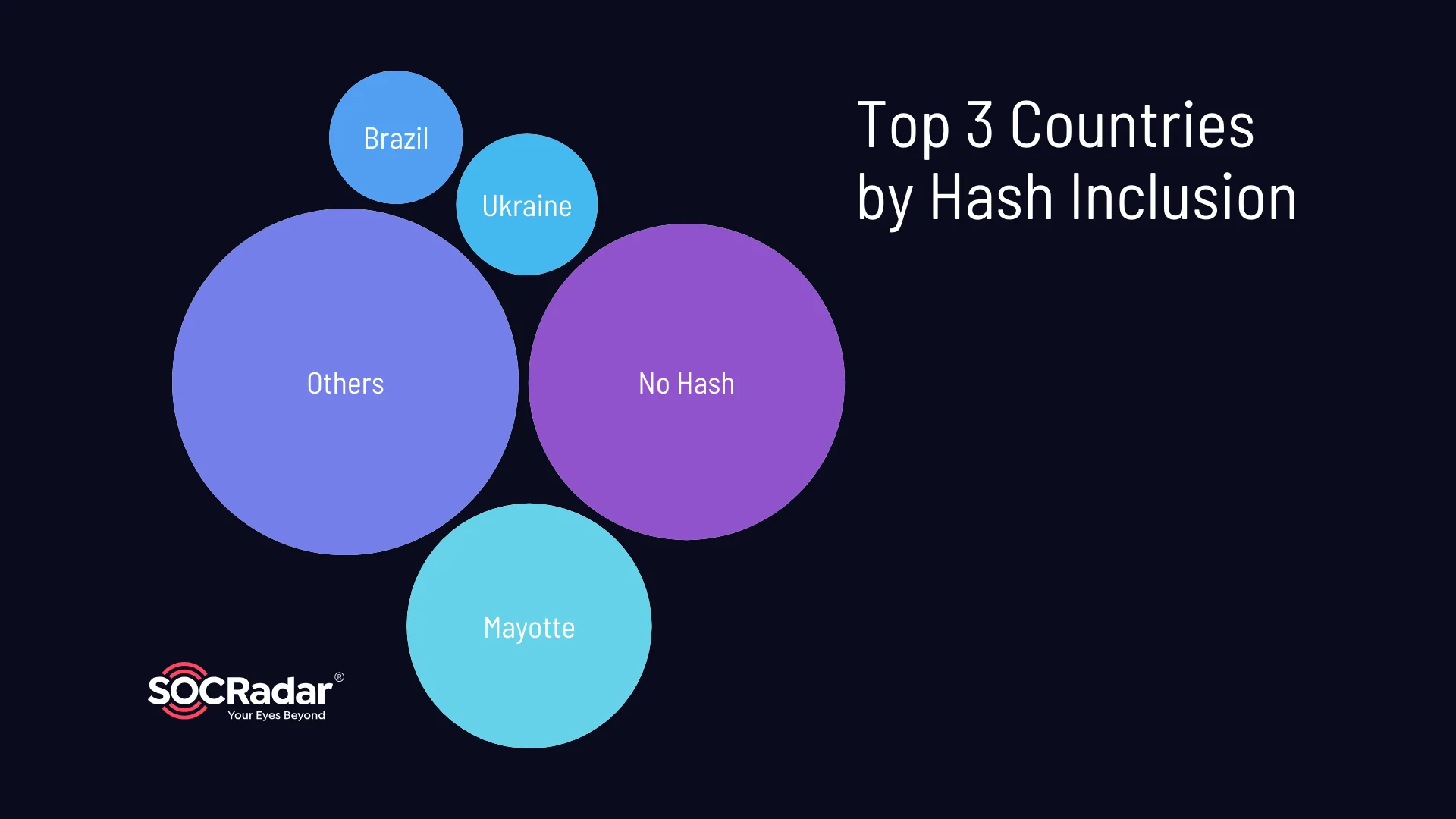
Top 3 countries by hash inclusion
These countries demonstrate a higher prevalence of compromised hash information within the stealer logs, indicating a potential risk to user accounts and sensitive data.
Strategies for Enhanced Security Against Stealer Logs in Entertainment Platforms
To mitigate the threat of stealer malware, organizations, including the ones in the entertainment industry, should adopt a comprehensive approach to data security and implement a series of key measures:
- Organizations need to strictly control employee access to their accounts. This involves implementing multiple authentication methods, such as Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA), which adds an additional layer of security to user accounts.
- Employees should also be encouraged to use password managers to manage their passwords effectively. Strong and unique passwords for each service or application should be emphasized, and regular password changes should be encouraged to minimize the risk of compromised credentials.
- Regular software updates are crucial for maintaining the security of organizational systems. Organizations should ensure that all software is up to date with the latest security patches and fixes to prevent vulnerabilities that could be exploited by stealer malware.
- When stealer malware is detected on employees’ systems, it is essential to isolate the infected systems from the network promptly. Necessary actions should be taken against affected users and systems to prevent further data compromise.
- Employee awareness and education play a vital role in mitigating the threats posed by stealer logs. Employees should be trained to recognize and avoid suspicious emails and attachments. They should also be encouraged to seek help from security teams or the Security Operations Center (SOC) when in doubt. Regular security awareness programs can also help employees understand the importance of data security and their role in maintaining it.
- Organizations should emphasize downloading and running applications only from official sources recommended by the organization. This reduces the risk of inadvertently installing malicious software or compromised versions of legitimate applications.
- Regularly checking accounts for credential leaks in services open to the internet is crucial. Popular chat applications and storage services can be targets for cybercriminals seeking to compromise employee and organizational data.
SOCRadar’s Dark Web Monitoring provides continuous surveillance of the entire web, including the deep and dark web, to detect compromised Personally Identifiable Information (PII). With real-time alerts on the most recently compromised account credentials and credit card numbers relevant to your organization, you can protect your company and customers from the risks of identity theft and fraud brought on by stealer logs.
SOCRadar’s Dark Web Monitoring
In addition to implementing these strategies, it is important to stay informed about the latest trends and insights regarding stealer logs and malware. For a deeper understanding of the widespread nature of stealer malware and its impact, check out the “Snapshot of 70 Million Stealer Logs” whitepaper by SOCRadar.
Conclusion
Stealer logs represent compromised digital security within the entertainment industry, harboring stolen data collected by infostealer malware for illicit purposes. Our examination revealed their pervasive presence across entertainment platforms such as Netflix, Spotify, Amazon, and Gamespot, among others, highlighting the industry’s vulnerability to cyber intrusion.
SOCRadar’s Threat Hunting module offers a solution, enabling defenders to sift through vast amounts of data within stealer logs, identifying and neutralizing threats before they cause harm. Leveraging this module, our examination revealed the widespread presence of stealer logs across entertainment platforms, emphasizing the sector’s susceptibility to cyber intrusion.
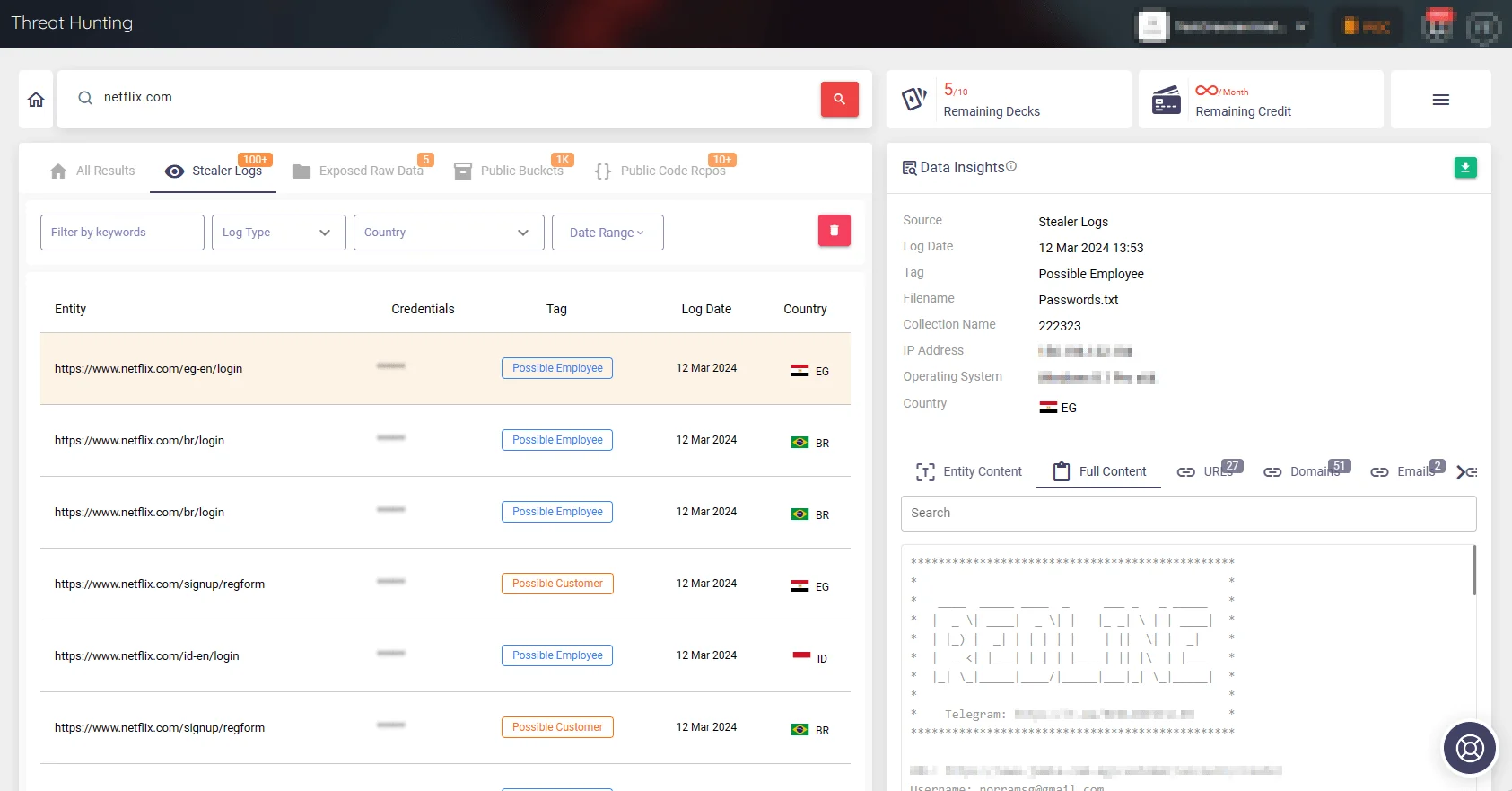
Search on stealer logs for Netflix (SOCRadar Threat Hunting)
The scrutiny of stealer logs exposes the complex cybersecurity landscape confronting the entertainment sector. By leveraging insights from analyzing stealer logs in a similar way, organizations can identify patterns, anticipate threats, and fortify their cybersecurity posture. Aligning with this objective, SOCRadar’s vigilant monitoring of threats ensures that organizations are equipped with timely and actionable intelligence to defend against cyber attacks.




































