
Anonymous Threatened Western Companies Operating in Russia Raises Concerns of Cyber Attack
Global hacktivist group Anonymous has threatened a list of companies that continue to operate in Russia, unlike many Western companies that suspended doing business due to Moscow’s decision to invade Ukraine.
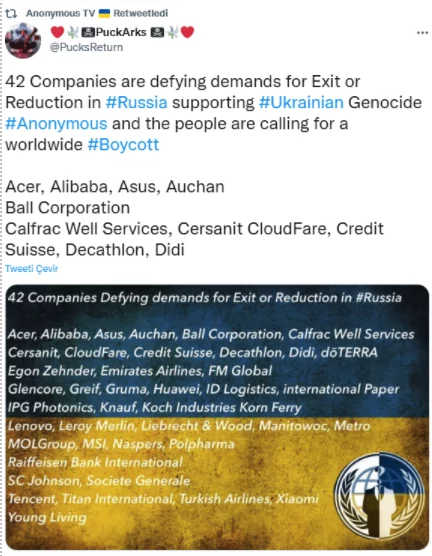
In a tweet post from an account considered close to Anonymous leadership, the group published a list of 42 companies and warned that they would face cyber-attacks if they did not pull out of Russia.
After the military action launched by the Russian forces, Anonymous mobilized its volunteers to target Russian public institutions and state-controlled media outlets.
In its recent attempts against the Russian invasion, the decentralized international hacktivist collective targeted the Russian Central Bank and the Russian construction company Rostproekt.
In a post on Twitter, an account representing the group said that it would release 35,000 files that contain “secret agreements.” The group also claimed to hack Rostproekt’s email and is expected to leak the dump. Anonymous plans to launch a new site to host it is upcoming dumbs.
Russia’s media regulator Roskomnadzor and Russian intelligence and security service FSB were on Anonymous’s target lists, among many other targets. The group leaked thousands of classified documents to expose the details of Russia’s plans to conquer Ukraine.
Apart from leaking data and swapping TV programs, Anonymous hackers have defaced Russian websites. So far, the attacks have caused disruption and embarrassment, but it also indicates the group’s potential to sustain cyber raids targeting Russia and its allies.
What Can Western Companies Expect from a Potential Anonymous Attack?
Anonymous has not been this active in years. The launch of a military campaign in Ukraine has served the collective as a critical event that returns it to life. SOCRadar analysts emphasize the evolution of the group’s strategy from the start of the war.
The decisions taken by many western companies to terminate operations in Russia is a critical turning point for Anonymous making them expand their attack portfolio. The boycott against Russia has created polarization among western business conglomerates. While some of them harshly reacted to Russia by closing their offices in Moscow, others have decided to go on business.
As highlighted in the latest tweet, Anonymous has planned to conduct cyber-attacks on western companies that defied exit or reduction activities in the Russian market.
Unlike previous incidents targeting Russian websites where Anonymous focused on stealing data and web defacement, it is considered that Anonymous’s initial plan was to conduct DDoS attacks on the western companies it threatened.
It may start a more extensive campaign that aims to intimidate the companies. In further steps, the collective is likely to continue with other types of cyber-attacks like the ones it exercised in Russia.
According to the list compiled by Jeffrey Sonnenfeld and Yale Research Team, there are currently 43 companies that defy demands for exit or reduction of activities. In addition, 58 companies decided to hold off on new investment and business expansion. Click here to see the complete list.
What is the Lesson Learned from Nestle “Hack”?
The Nestle incident may help get some insights into the group’s current modus operandi. Anonymous claimed that it got 10 GB of data from Nestle doe to its continuing business in Russia during the invasion.
However, Nestle company denied the claims and stated that they had already leaked the data. The data shared “relates to a case from February when some randomized and predominantly publicly available test data of a B2B nature was made accessible unintentionally online for a short period on a single business test website”.
A lesson learned from this incident is that hacktivist groups may claim to leak the data they did not steal. For the aim of propaganda and motivating its members, this is a traditional way this kind of actors, both in the physical and cyber domain, usually apply.
Secondly, it is strategically vital for companies to monitor their data. From publicly accessible repositories to test data, as in the case of Nestle, attack surface management has become even more significant for the companies protecting their data and maintaining their market reputation.
Search cybercrime black markets, combolists, and known breaches with SOCRadar’s free AccountBreach tool. There are more than 10 billion records in the SOCRadar Breach Database. Check it out right now if there is anything to do with you.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































