
APT Profile: Kimsuky
In cyberspace, the Korean Peninsula has been a hotbed of activity for a while. With conflict unfolding between North and South Korea, North Korean Advanced Persistent Threats (APTs) are emerging as the weapon of choice. Among these, one name stands out: Kimsuky.
North Korean APTs have been responsible for some of the most audacious cyber-attacks in recent history. According to a United Nations report, North Korean hackers have pilfered over $2 billion through cyber-attacks on banks and cryptocurrency exchanges. These funds are believed to be channeled into North Korea’s weapons programs.
Enter Kimsuky, a North Korean APT group that has been operating for a while and recently started to be heard in the media again. But what makes Kimsuky this famous?
This blog post aims to shed light on Kimsuky, providing an in-depth profile of this threat actor. We will explore who they are, how they operate, the tools and vulnerabilities they exploit, their targets, and their operations. We will also provide some security recommendations to help protect against Kimsuky’s attacks. Understanding the threat posed by Kimsuky is the first step towards building a robust defense against cyber-espionage activities.
Who is Kimsuky?
Kimsuky (or APT43), a name that sends tides through the cybersecurity community, is a cyber-espionage group believed to be operating out of North Korea. First observed in 2013, Kimsuky has been determined to pursue sensitive information, primarily focusing on South Korea and extending its reach to the United States and Europe.
How Does Kimsuky Attack?
Kimsuky employs a range of tactics to infiltrate systems and gathers sensitive information. Let’s break down their modus operandi:
Spearphishing Emails
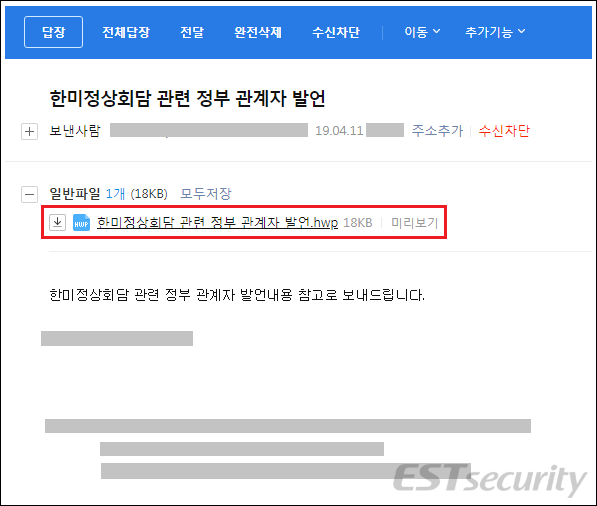
One of the primary methods Kimsuky uses to gain unauthorized access to systems is through spearphishing emails. These are targeted emails sent to specific individuals or organizations. The emails often contain malicious attachments or links. For example, Kimsuky has been known to use Hangul Word Processor (HWP) files, which are popular in South Korea. These files contain exploits for known vulnerabilities or a dropper disguised as a document.
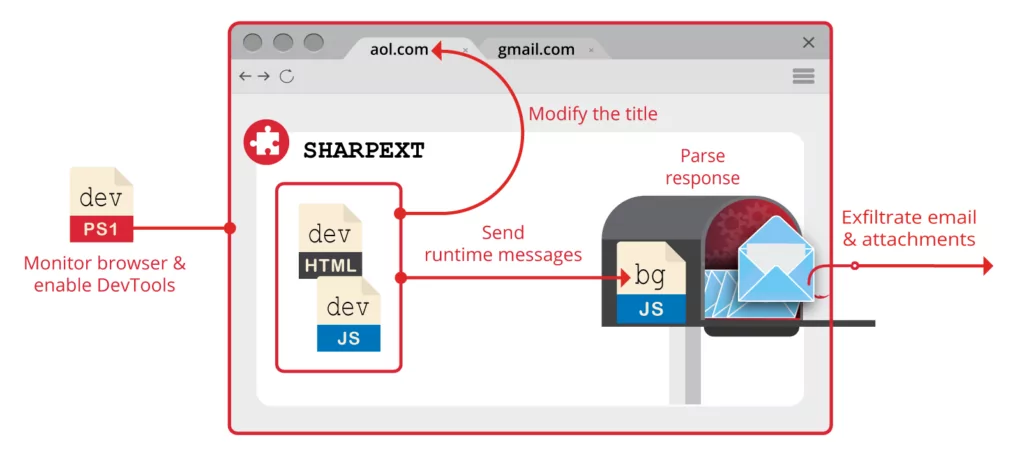
Malicious Chrome Extensions
Kimsuky has also been observed using malicious Google Chrome extensions to infect victims. They lure victims to websites that appear legitimate and prompt them to install a Chrome extension. Once installed, this extension can steal cookies and passwords from the browser.
Exploiting Vulnerabilities
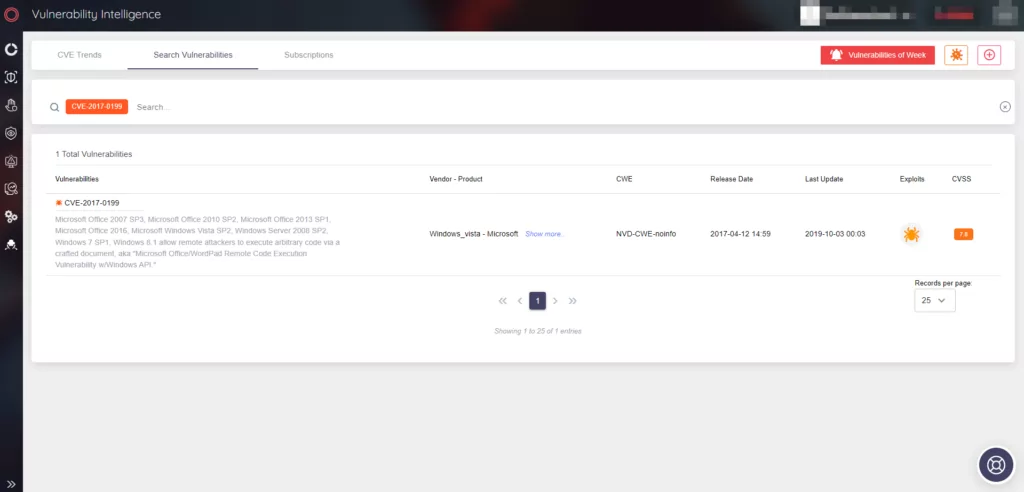
Kimsuky is known for exploiting known vulnerabilities in software. For instance, they have exploited a vulnerability in Microsoft Word (CVE-2017-0199) to execute malicious code. By keeping an eye on newly discovered vulnerabilities and exploiting them before they are patched, Kimsuky can gain access to systems with minimal detection.
Use of Malware
Once Kimsuky has gained access to a system, they deploy malware to maintain control. One such malware is BabyShark, which is used to gather data from the infected system. They also use keyloggers and remote control software to monitor the user’s actions and gather further information.
Kimsuky’s attacks are well-planned and executed with precision. Their ability to use a combination of spearphishing, exploiting vulnerabilities, and deploying malware makes them a formidable threat.
Which Tools and Vulnerabilities Used by Kimsuky?
Kimsuky employs a variety of tools and exploits several vulnerabilities to carry out its cyber espionage campaigns. Here’s a closer look:
Tools Used by Kimsuky:
Kimsuky’s toolkit is extensive and varied, reflecting a high degree of sophistication and adaptability. Their ability to exploit a range of vulnerabilities and deploy a diverse set of tools makes them a formidable and persistent threat.

BabyShark Malware
One of the prominent tools in Kimsuky’s arsenal is the BabyShark malware. This malware is used to collect data from infected systems. It is often delivered through spearphishing emails as a second-stage payload.
Gold Dragon
Gold Dragon, a data-gathering tool that was first seen in December 2017 during a spearphishing campaign in Korea targeting the same Olympic-linked organizations. The tool has observed that it was used in operations aimed at entities connected to the 2018 Pyeongchang Winter Olympics.
As a second-stage backdoor implant, Gold Dragon ensured a lasting presence on the victim’s system after the execution of a file-less, PowerShell-based initial attack that used steganography.
The capabilities of this malware included basic reconnaissance, data extraction, and the ability to download additional components from its command and control server.
SWEETDROP
SWEETDROP is a malware dropper that is actively used by Kimsuky during the Covid-19 pandemic. It is a C/C++ Windows application that collects basic system information and is capable of downloading and executing additional stages such as download and execution of Kimsuky’s backdoor “BITTERSWEET”.
Vulnerabilities Exploited by Kimsuky:
Kimsuky’s use of these tools and exploitation of vulnerabilities demonstrates their adaptability and resourcefulness. They are capable of using both custom and off-the-shelf tools to achieve their objectives.
CVE-2017-0199
Kimsuky exploited this vulnerability to deliver the BabyShark malware. This is a vulnerability in Microsoft Word that allows a specially crafted file to execute code.
HWP Exploits
Hangul Word Processor (HWP) files are widely used in South Korea. Kimsuky has been known to use HWP files that contain exploits for known vulnerabilities to install droppers on systems.
CVE-2015-2545
This is a vulnerability in Microsoft Office that allows for remote code execution through specially crafted EPS image files. Kimsuky has exploited this vulnerability to execute malicious code and install malware on target systems.
CVE-2019-0604
Kimsuky has exploited this vulnerability in Microsoft SharePoint to execute arbitrary code. By sending a specially crafted SharePoint application package, attackers can run arbitrary code in the context of the SharePoint application pool and the SharePoint server farm account.
What are the Targets of Kimsuky?
Kimsuky mainly targets South Korean think tanks, industry, nuclear power operators, and the Ministry of Unification for espionage purposes.
Targeted Sectors
Kimsuky’s cyber-espionage campaigns are highly targeted. They focus on specific sectors and countries that align with the strategic interests of North Korea. The most targeted industries by Kimsuky are:
- Government Institutions,
- Think Tanks and Academic Institutions,
- Media Outlets (Publishing Services),
- Critical Infrastructure (Energy & Utilities, Space & Defence, National Security&International Affairs),
- Cryptocurrency & NFT (Banking, Finance),
- Information Services
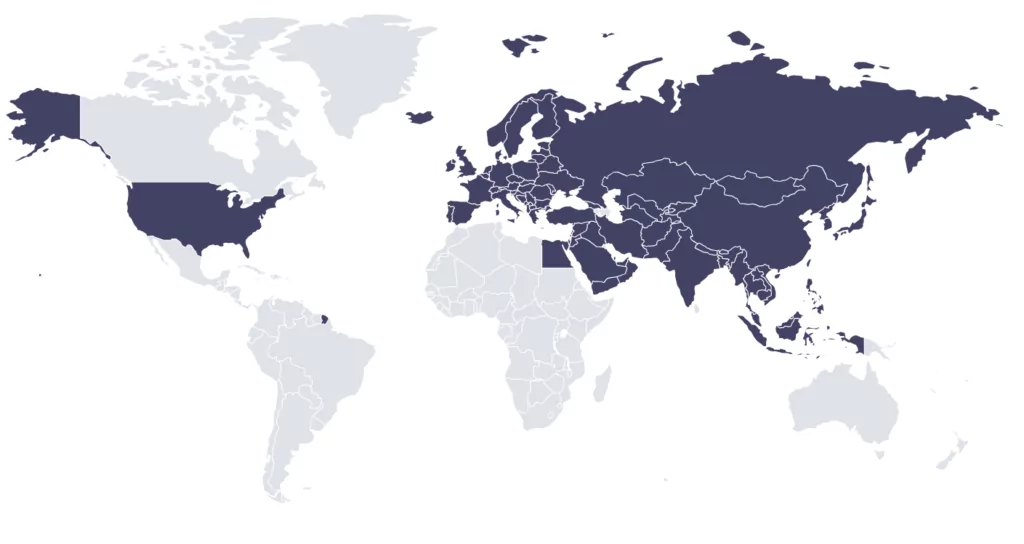
Targeted Countries
Kimsuky’s activities are believed to align with North Korea’s foreign intelligence agency, the Reconnaissance General Bureau (RGB), and the group’s main targets are mostly:
- South Korea
- United States
- European Countries
Operations of Kimsuky
Kimsuky has been involved in several distinct operations, each with specific targets and objectives. Here are some of the notable operations attributed to Kimsuky:
South Korean Nuclear Reactor Cyberattack
Timeframe: December 2014
In this operation, Kimsuky was implicated in cyberattacks against South Korea’s nuclear reactor operator. The attack raised concerns about critical infrastructure security and highlighted the extent of Kimsuky’s capabilities.
Operation Stolen Pencil
Timeframe: Active since at least May 2018
Operation Stolen Pencil was a campaign that targeted academic institutions. Kimsuky used spearphishing emails to lure victims to websites that appeared to be legitimate academic organizations. The victims were then prompted to install a malicious Google Chrome extension. This extension was capable of stealing cookies and passwords from the browser.
Foreign Ministries and Think Tanks Spearphishing Campaign
Timeframe: Late 2018
Kimsuky conducted a spearphishing campaign targeting multiple foreign ministries and think tanks. The spearphishing emails contained malicious Microsoft Word documents that exploited a known vulnerability (CVE-2017-0199) to download and execute the BabyShark malware. The targets included the United Nations Security Council, the U.S. Department of State, and several think tanks based in the U.S. and Europe.
Operation AppleSeed
Timeframe: 2021
In this operation, Kimsuky was observed distributing a backdoor known as AppleSeed. The group used spearphishing emails to target South Korean government agencies. The emails contained malicious attachments that, when opened, would install the AppleSeed backdoor on the victim’s system. This backdoor allowed Kimsuky to exfiltrate data and execute commands remotely.
Operation CloudDragon
Timeframe: 2023
Recently, Kimsuky has been linked to a new campaign dubbed Operation CloudDragon. This operation involves the use of social engineering, spearphishing, and custom malware to target think tanks, news media, and experts on North Korean affairs. Kimsuky impersonated journalists and used spoofed URLs, and weaponized Office documents to steal credentials and gather strategic intelligence.
Emulating Kimsuky’s Espionage Operations
Timeframe: April 2023
AttackIQ released four new attack graphs that emulate the espionage activities of Kimsuky. This politically motivated North Korean adversary has been involved in sophisticated espionage operations, and the attack graphs provide insights into their tactics and techniques.
Social Engineering and Spearphishing Campaigns
Timeframe: June 2023
According to a joint Cybersecurity Advisory by U.S. and Republic of Korea (ROK) agencies, Kimsuky has been involved in social engineering campaigns targeting think tanks, academia, and news media. The advisory provides detailed information on how Kimsuky actors operate and warning signs of spearphishing campaigns. North Korea relies heavily on intelligence gained from these operations. Kimsuky has been involved in impersonation campaigns and has been targeting governments, political organizations, and more for intelligence collection.
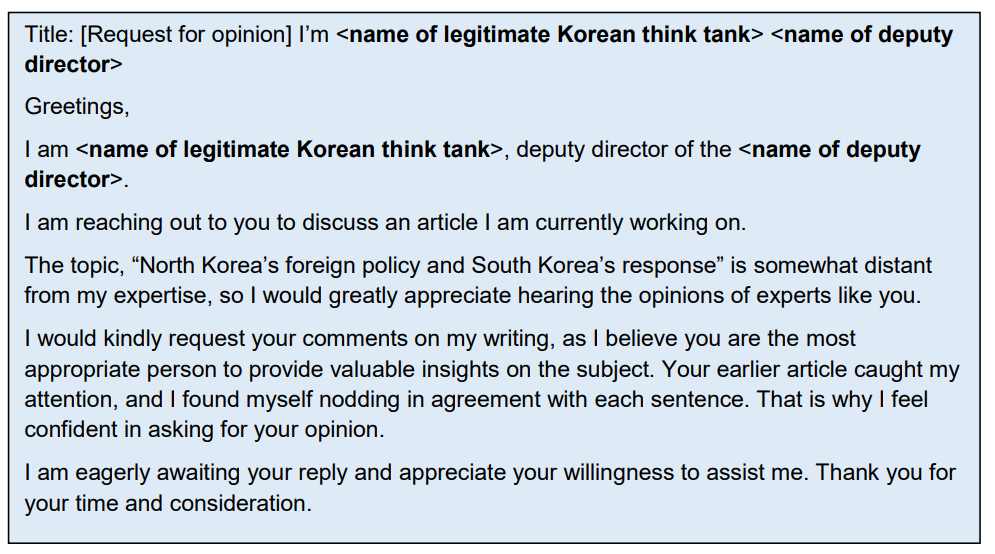
These recent operations highlight Kimsuky’s ongoing efforts to gather intelligence and the evolving nature of their tactics.
Connections with Other APT Groups
Kimsuky is one of several APT groups believed to be operating out of North Korea. While Kimsuky operates independently, there are indications that it may have connections with other North Korean APT groups.
Lazarus
One such group is the Lazarus Group, which is known for its global cyber espionage and cybercrime campaigns. The Lazarus Group has been implicated in high-profile attacks, including the Sony Pictures hack in 2014 and the WannaCry ransomware attack in 2017.
While there is no direct evidence linking Kimsuky to the Lazarus Group, both groups share similarities in their tactics and targets. Additionally, both groups are believed to be sponsored by the North Korean government, which suggests that they may share resources or information.
APT37 (Reaper)
Another North Korean APT group, known as APT37 or Reaper, has been active since at least 2012. Like Kimsuky, APT37 has primarily targeted South Korea but has also conducted operations against Japan, Vietnam, and the Middle East. APT37 is known for using zero-day vulnerabilities and malware in its cyber-espionage campaigns.
Again, while there is no concrete evidence of direct collaboration between Kimsuky and APT37, the similarities in their targets and tactics suggest that they may be part of a coordinated effort by the North Korean government to conduct cyber espionage.
In summary, Kimsuky, while operating independently, is part of a larger ecosystem of North Korean APT groups. The shared tactics, targets, and likely state sponsorship suggest that these groups may be loosely connected or at least aligned in their objectives.
Some of the samples’ strings contain the “Kim” keyword:
- “kimm.r-naver[.]com”,
- “kimsukyang and Kim asdfa” the owner of “iop110112@hotmail[.]com and rsh1213@hotmail[.]com domains extracted in one of the first observations.
- And other IoCs contain “tjkim”, “kimyfrenotsure”, “kimshan”, “Kim_Summit”, etc.
These and similar IoCs can be found on the Kimsuky Threat Actor page on SOCRadar XTI’s Cyber Threat Intelligence Module
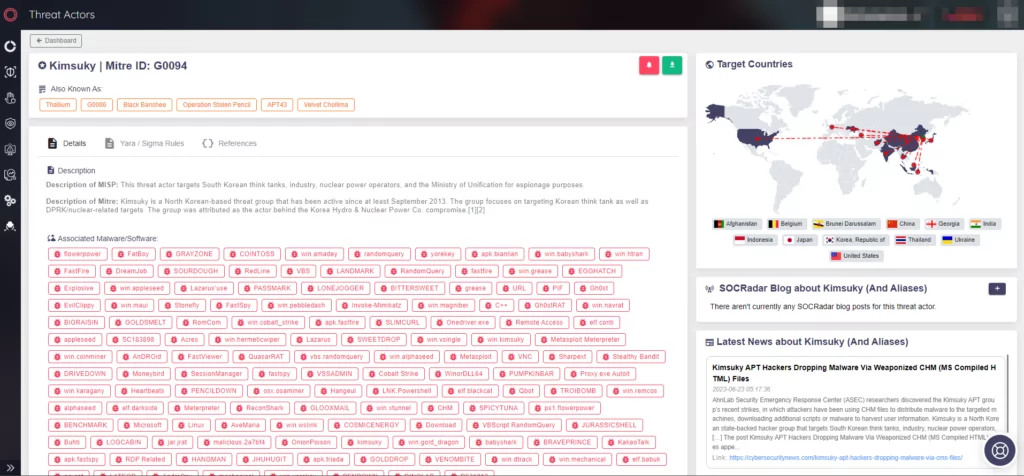
So, it is also possible to conclude from these IoCs that Kimsuky is a separate threat actor and that it stands out from other North Korean threat actors.
Conclusion
Kimsuky, a North Korean cyber-espionage group, has been a persistent and evolving threat since it was first observed in 2013. With a focus on intelligence gathering, Kimsuky has targeted the government institutions, think tanks, academic institutions, and critical infrastructure primarily in South Korea but also in the United States and Europe.
Kimsuky’s tactics are sophisticated and varied, ranging from spearphishing emails and exploiting software vulnerabilities to using malicious Chrome extensions and custom malware. The group’s ability to adapt and evolve its tactics makes it particularly dangerous.
Furthermore, Kimsuky is not operating in isolation. It is part of a larger network of North Korean APT groups, including the Lazarus Group and APT37. These groups, while operating independently, share similarities in tactics and targets, suggesting a coordinated effort by the North Korean government.
The global reach and evolving nature of Kimsuky’s operations highlight the importance of vigilance and robust cybersecurity measures. As Kimsuky continues to adapt and evolve, so too must the defenses against them.
Security Recommendations Against Kimsuky
Educate and Train Staff: Regularly train staff to recognize phishing emails and malicious attachments. Educating users on the risks of spearphishing emails is crucial.
Keep Software Updated: Regularly update all software to ensure that known vulnerabilities are patched. This reduces the avenues through which Kimsuky can gain unauthorized access.
Implement Multi-Factor Authentication (MFA): Use MFA wherever possible, especially for critical systems and data. This adds an additional layer of security, even if passwords are compromised.
Monitor for Suspicious Activity: Regularly monitor networks and systems for unusual activity that could indicate a breach.
Use Security Software: Employ robust security software that can detect and block malware and other malicious activity.
Collaborate and Share Information: Work with other organizations and government agencies to share information on threats and best practices for defense.
Develop an Incident Response Plan: Have a plan in place for responding to security incidents. Knowing how to respond in the event of a breach is critical.
By taking these steps, organizations can reduce their risk of falling victim to Kimsuky and other cyberespionage groups.
In an ever-evolving threat landscape, staying informed and being prepared are key to being out of danger. Cyber Threat Intelligence is among the best threats to take against a specific group conducting espionage activities. For example, obtaining information about the existing weaknesses in the assets owned by the company will enable the company to take early action against possible threats.
MITRE ATT&CK TTPs Used by Kimsuky
|
Technique |
ID |
|
Reconnaissance |
|
|
Gather Victim Identity Information: Email Addresses |
|
|
Gather Victim Identity Information: Employee Names |
|
|
Gather Victim Org Information |
|
|
Phishing for Information: Spearphishing Link |
|
|
Search Open Websites/Domains: Social Media |
|
|
Search Open Websites/Domains: Search Engines |
|
|
Search Victim-Owned Websites |
|
|
Resource Development |
|
|
Acquire Infrastructure: Domains |
|
|
Acquire Infrastructure: Server |
|
|
Acquire Infrastructure: Web Services |
|
|
Compromise Accounts: Email Accounts |
|
|
Compromise Infrastructure: Domains |
|
|
Develop Capabilities: Malware |
|
|
Establish Accounts: Social Media Accounts |
|
|
Establish Accounts: Email Accounts |
|
|
Obtain Capabilities: Tool |
|
|
Obtain Capabilities: Exploits |
|
|
Stage Capabilities: Upload Malware |
|
|
Initial Access |
|
|
Exploit Public-Facing Application |
|
|
Phishing: Spearphishing Attachment |
|
|
Phishing: Spearphishing Link |
|
|
Execution |
|
|
Command and Scripting Interpreter: PowerShell |
|
|
Command and Scripting Interpreter: Windows Command Shell |
|
|
Command and Scripting Interpreter: Visual Basic |
|
|
Command and Scripting Interpreter: Python |
|
|
Command and Scripting Interpreter: JavaScript |
|
|
User Execution: Malicious Link |
|
|
User Execution: Malicious File |
|
|
Persistence |
|
|
Account Manipulation |
|
|
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
|
|
Browser Extensions |
|
|
Create Account: Local Account |
|
|
Create or Modify System Process: Windows Service |
|
|
External Remote Services |
|
|
Scheduled Task/Job: Scheduled Task |
|
|
Server Software Component: Web Shell |
|
|
Software Discovery: Security Software Discovery |
|
|
Privilege Escalation |
|
|
Event Triggered Execution: Change Default File Association |
|
|
Obfuscated Files or Information: Software Packing |
|
|
Defense Evasion |
|
|
Deobfuscate/Decode Files or Information |
|
|
Hide Artifacts: Hidden Users |
|
|
Hide Artifacts: Hidden Window |
|
|
Impair Defenses: Disable or Modify Tools |
|
|
Impair Defenses: Disable or Modify System Firewall |
|
|
Indicator Removal: File Deletion |
|
|
Indicator Removal: Timestomp |
|
|
Masquerading |
|
|
Masquerading: Masquerade Task or Service |
|
|
Masquerading: Match Legitimate Name or Location |
|
|
Modify Registry |
|
|
Obfuscated Files or Information |
|
|
Obfuscated Files or Information: Software Packing |
|
|
Process Injection |
|
|
Process Injection: Process Hollowing |
|
|
Subvert Trust Controls: Code Signing |
|
|
System Binary Proxy Execution: Mshta |
|
|
System Binary Proxy Execution: Regsvr32 |
|
|
System Binary Proxy Execution: Rundll32 |
|
|
Use Alternate Authentication Material: Pass the Hash |
|
|
Valid Accounts: Local Accounts |
|
|
Credential Access |
|
|
Adversary-in-the-Middle |
|
|
Credentials from Password Stores: Credentials from Web Browsers |
|
|
Multi-Factor Authentication Interception |
|
|
OS Credential Dumping: LSASS Memory |
|
|
Unsecured Credentials: Credentials In Files |
|
|
Discovery |
|
|
File and Directory Discovery |
|
|
Network Sniffing |
|
|
Process Discovery |
|
|
Query Registry |
|
|
System Information Discovery |
|
|
System Network Configuration Discovery |
|
|
System Service Discovery |
|
|
Lateral Movement |
|
|
Internal Spearphishing |
|
|
Remote Services: Remote Desktop Protocol |
|
|
Collection |
|
|
Archive Collected Data: Archive via Utility |
|
|
Archive Collected Data: Archive via Custom Method |
|
|
Data from Local System |
|
|
Data Staged: Local Data Staging |
|
|
Email Collection: Remote Email Collection |
|
|
Email Collection: Email Forwarding Rule |
|
|
Input Capture: Keylogging |
|
|
Command and Control |
|
|
Application Layer Protocol: Web Protocols |
|
|
Application Layer Protocol: File Transfer Protocols |
|
|
Application Layer Protocol: Mail Protocols |
|
|
Ingress Tool Transfer |
|
|
Remote Access Software |
|
|
Web Service: Bidirectional Communication |
|
|
Exfiltration |
|
|
Exfiltration Over C2 Channel |
|
|
Exfiltration Over Web Service: Exfiltration to Cloud Storage |
|



































