
Attackers Exploit Adobe Acrobat Sign to Distribute RedLine Stealer Malware
Cybercriminals employ many ways to distribute malware, including taking advantage of legitimate services. Recently, security researchers discovered that cybercriminals have started using Adobe Acrobat Sign service to spread the RedLine information stealer malware.
Adobe Acrobat Sign is an online tool designed to help users with electronic document signing. Additionally, the service allows users to send signature requests via Adobe-generated emails. Hackers are exploiting the capability to add text to these emails by including a link to a document hosted on a legitimate Adobe server (eu1.documents.adobe.com/public/).
With Adobe-generated emails, attackers can trick unsuspecting recipients into believing they can preview the document when, in reality, the link redirects to another site. The site prompts the user to complete a hardcoded Captcha quiz, then directs them to download a ZIP archive which includes RedLine information stealer.
Users need to be cautious when opening unexpected emails that contain links, even if they appear to be from a trusted source.
Adobe Acrobat Sign Might Become a New Technique
In one instance, the attackers targeted the same victim once more a few days later by adding a new link to an email that seemed to be from Adobe.
When the victim clicked on the link, it took them to a webpage on dochub[.]com, which also provides a service for signing electronic documents.
The attackers used a different version of the RedLine Trojan in the archive for this second attack and some harmless files related to the Grand Theft Auto V video game.
To avoid being detected, they are making the trojan file larger than 400MB by adding zeros, which the victim will not notice as the file is compressed. Although not certain, the motive could be to evade antivirus software that behaves differently with larger files.
According to Avast researchers, using Adobe Acrobat Sign to distribute malware is a new method attackers use in targeted attacks. They are concerned that this technique may become more popular among cybercriminals.
Stay Ahead of Malware Threats with SOCRadar
SOCRadar’s Threat Actor/Malware tab provides a comprehensive view of malware-related information, including its associated threat actors, descriptions, related CVEs, IoCs, and the latest news about RedLine and its aliases.
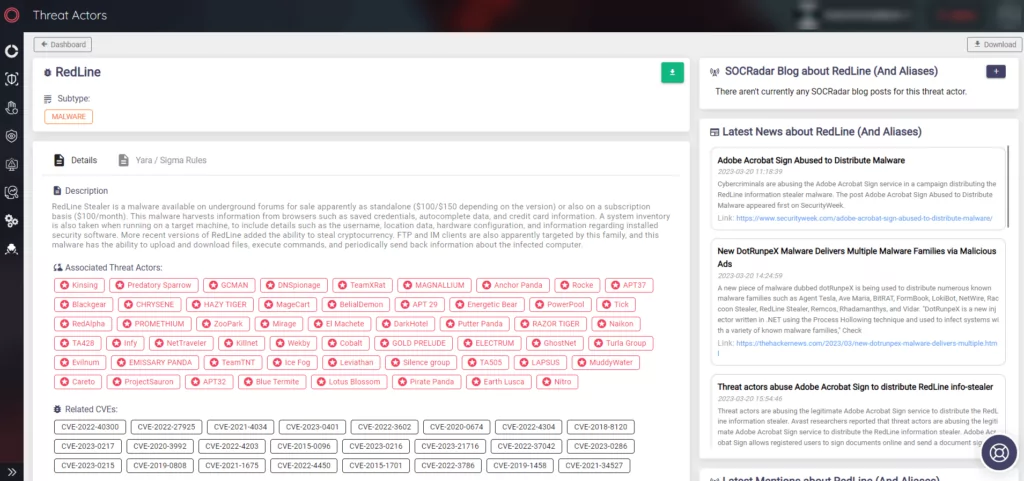
Related CVEs help organizations prioritize which vulnerabilities to patch, and IoCs enable them to identify and block the malware. The latest news about RedLine and its aliases keeps organizations updated on any new developments or attacks related to this threat.
By displaying this information, SOCRadar helps organizations stay informed about the latest threats and proactively protect their systems and data.



































