
Better Protect Your Mobile App with SOCRadar MAS Module
Threat actors use all kinds of methods to achieve their malicious goals. Mobile apps are among the most popular targets for attackers lately. Targeting a mobile app with various attack vectors has been an increasing trend amongst cybercriminals lately.
Fake Mobile Apps Lead to Bigger Threats

On SOCRadar blog pages, we often share some research showing that mobile apps are impersonated, and malicious software is installed on users’ devices with this method. In particular, we draw attention to the fact that fake applications that install banking trojans on mobile devices both damage the reputation of brands and cause financial losses for users.
It stands out as an instrument to imitate reliable applications, which is a common feature of banking malware, to deceive users of all levels. These malware droppers support the circulation of malicious tools such as RatMilad spyware and banking malware Octo, which were discovered in the past months.
How Threat Actors Impersonate a Mobile App
The vast majority of impersonated mobile apps are Android-based. So there are quite a lot of malware droppers in the Google Play Store. Although these fake apps are tried to be prevented with strict security measures, threat actors always find a new way. Apps distributed with similar names of mobile applications that are restricted in some countries or apps that claim to offer additional features to real apps are used to deceive users.
Technically, we can talk about two different types of impersonation:
- App fraud: Apps that threat actors design and put into circulation are similar to real mobile apps. This malicious software takes advantage of users’ carelessness and obtains banking, credit card information, or personally identifiable information.
- API manipulation: Using this method, attackers obtain sensitive data of organizations or individuals by exploiting vulnerabilities or bugs in APIs.
How Can Organizations Protect Themselves?
Mobile App Security (MAS), the new SOCRadar Extended Threat Intelligence module, helps organizations proactively combat the reputational damage caused by fake mobile apps.
With the latest release of SOCRadar;
- Find out immediately if there are malicious apps that are similar to the real ones in app stores by using the APK code of the organizations.
- Be instantly notified of an unexpected situation by monitoring the behavior of apps.
- Track which servers the app is communicating with.
- Be aware of potential threats in other apps that the app engages with.
- Always stay one step ahead of threat actors with constant security checks.
How to Use SOCRadar MAS Module
SOCRadar users access the Mobile App Security section after selecting the entity type “Mobile Applications” and searching. All relevant mobile applications are listed on this screen, and those suitable for various security checks can be reviewed. When clicking on an inspectable app, the user sees a screen with information such as size, version, developer ID, APK name, hashes, and server locations.
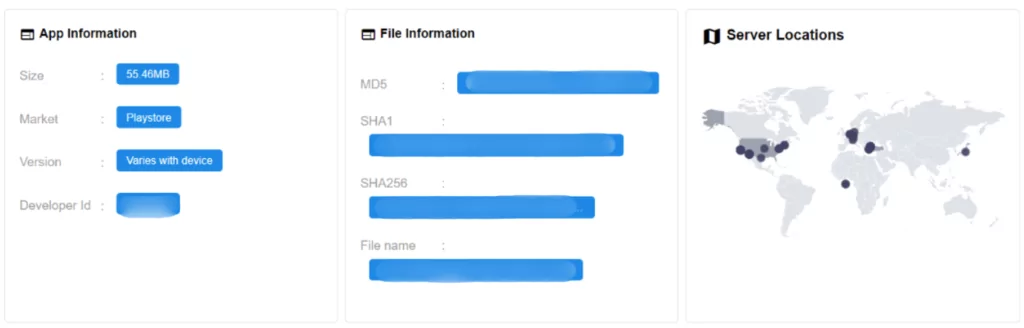
On this screen, in addition to basic information about the application, technical details that will help cyber hygiene are also presented: the application’s services, APK extensions with certificate information, etc.
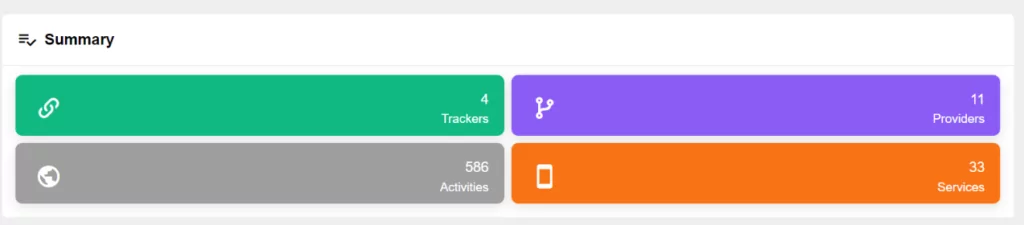
SOCRadar analyzes the application for its permissions, privacy, and risk level and classifies it as “Dangerous” or “Normal.” It also examines the application’s interaction with third-party services and notifies users when suspicious activity is detected.
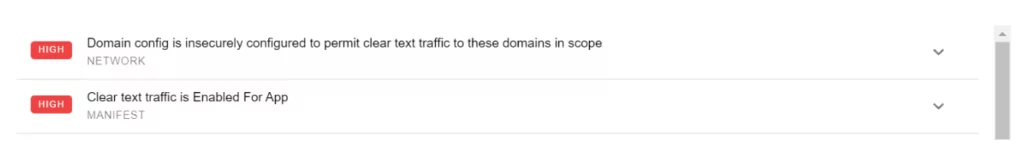
In the “Findings” section, actions that are found to generate security events, details, and severity levels are marked as “High,” “Warning,” and “Good.”



































