
BeyondTrust Security Incident — Command Injection and Escalation Weaknesses (CVE-2024-12356, CVE-2024-12686)
[Update] January 14, 2025: “CVE-2024-12686 Enters the KEV Catalog”
BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) solutions have two vulnerabilities, CVE-2024-12356 and CVE-2024-12686, which have exposed organizations to significant cybersecurity risks. These flaws enable unauthenticated command injection and privilege escalation, allowing attackers to run arbitrary commands and compromise enterprise systems.
BeyondTrust’s PRA and RS products are widely used in various industries to protect remote access and manage privileged accounts. The exploitation of these vulnerabilities, which have now been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog, highlights their severity and the urgent need for remediation. BeyondTrust has actively worked with external forensic experts to investigate the breach while providing customers with timely updates and actionable guidance.
Incident Overview: BeyondTrust Security Breach and Vulnerabilities
CVE-2024-12356: Command Injection Vulnerability
This critical vulnerability (CVSS 9.8) results from improper input sanitization, which allows attackers to execute arbitrary system commands via specially crafted requests. It requires no user permissions or interaction, which makes it extremely dangerous. CVE-2024-12356 was discovered during a forensic investigation into unauthorized access to Remote Support SaaS instances and has since been confirmed to be actively exploited.
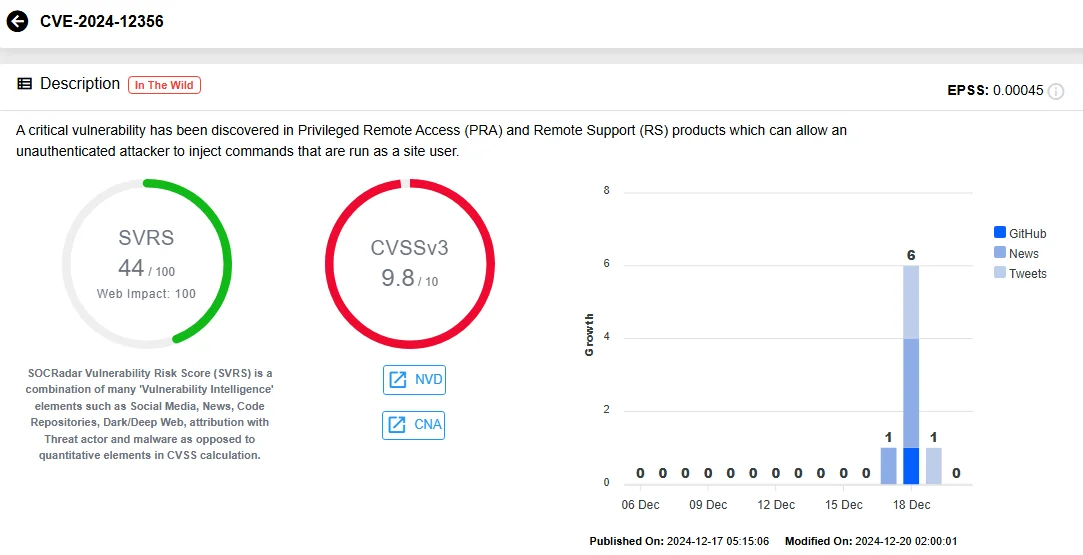
Vulnerability card of CVE-2024-12356 (SOCRadar Vulnerability Intelligence)
CVE-2024-12686: Post-Exploitation Privilege Escalation
CVE-2024-12686 is a medium-severity vulnerability that allows attackers with administrative privileges to upload malicious files and run arbitrary commands. While less severe than CVE-2024-12356, it is an important post-exploitation mechanism that allows attackers to gain a stronger foothold in compromised environments.
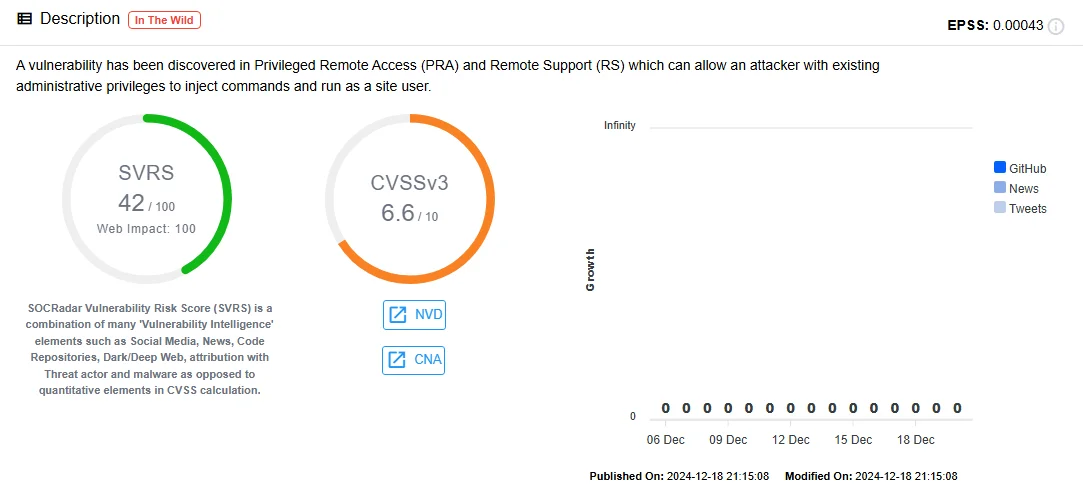
Vulnerability card of CVE-2024-12686 (SOCRadar Vulnerability Intelligence)
Incident Timeline
- December 2, 2024: Anomalous activity detected in Remote Support SaaS instances.
- December 5, 2024: Compromised API key identified and revoked; affected SaaS instances quarantined for forensic analysis.
- December 16 – 18, 2024: BeyondTrust releases patches for CVE-2024-12356 and CVE-2024-12686, addressing both vulnerabilities in cloud and self-hosted instances.
- December 19, 2024: CISA adds CVE-2024-12356 to its KEV Catalog, setting a remediation deadline of December 27, 2024.
Additional Details from BeyondTrust’s Investigation
BeyondTrust’s ongoing forensic analysis, which involved third-party cybersecurity experts, revealed that the attack used a compromised Remote Support SaaS API key to reset application account passwords and allow unauthorized access. The vulnerabilities were quickly patched, and the affected customers were notified. While there is no evidence of exploitation in ransomware campaigns, CISA’s KEV inclusion emphasizes the potential risks.
To assist customers, BeyondTrust provided detailed advisories and non-disruptive patches for all affected instances. They continue to work with impacted customers to ensure that updates are applied and additional mitigations are implemented effectively.
CISA’s KEV Catalog Addition
CISA has added CVE-2024-12356, a critical flaw in BeyondTrust Privileged Remote Access (PRA) and Remote Support (RS) products, to its Known Exploited Vulnerabilities (KEV) Catalog. This vulnerability, which is related to a command injection flaw (CWE-77), enables unauthenticated attackers to execute arbitrary commands as site users by sending maliciously crafted requests. With a CVSS score of 9.8, this issue poses a significant risk to organizations that rely on these solutions.
While there is currently no confirmed evidence of exploitation in ransomware campaigns, the vulnerability’s criticality necessitates immediate action. CISA has set a remediation deadline of December 27, 2024, and encourages organizations to apply BeyondTrust patches or discontinue product use if mitigations are not possible. Addressing this flaw as soon as possible is critical to preventing future exploits.
CVE-2024-12686 Enters the KEV Catalog
CISA has added CVE-2024-12686, the command injection vulnerability in BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS), to its Known Exploited Vulnerabilities (KEV) Catalog. Federal agencies are required to patch this vulnerability by February 3, 2025, as part of the ongoing effort to address actively exploited security flaws.
The inclusion of CVE-2024-12686 follows the earlier addition of CVE-2024-12356 to the KEV on December 19, 2024. Both vulnerabilities have been exploited as zero-days, allowing attackers to compromise BeyondTrust systems and potentially gain access to customer networks.
One high-profile breach linked to these flaws involved the U.S. Treasury Department, where attackers leveraged a stolen Remote Support SaaS API key to exploit a BeyondTrust instance. This attack has been attributed to Silk Typhoon, a Chinese state-sponsored threat actor.
BeyondTrust has already deployed patches for these vulnerabilities across its cloud-hosted systems, but organizations running self-hosted instances must manually apply the updates to mitigate the risks.
Indicators of Compromise (IoCs)
As part of their ongoing investigation, BeyondTrust has released a list of known Indicators of Compromise (IoCs) associated with the exploitation of their Remote Support SaaS instances. These IoCs include both IPv4 and IPv6 addresses observed during malicious activity:
IPv4 Addresses:
- 24.144.114.85
- 142.93.119.175
- 157.230.183.1
- 192.81.209.168
IPv6 Addresses:
- 2604:a880:400:d1::7293:c001
- 2604:a880:400:d1::72ad:3001
- 2604:a880:400:d1::7716:1
- 2604:a880:400:d1::7df0:7001
- 2604:a880:400:d1::8622:f001
Organizations leveraging BeyondTrust’s Remote Support SaaS or Privileged Remote Access solutions are advised to integrate these IoCs into their security monitoring tools immediately. This proactive step can help identify potential compromises and facilitate rapid response.
SOCRadar’s Solutions for Effective Risk Mitigation
Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence module provides organizations with real-time information on critical vulnerabilities such as CVE-2024-12356. This module enables organizations to prioritize remediation efforts based on the impact and risk of exploitation, receive actionable recommendations for rapid threat mitigation, and continuously monitor the status and updates of vulnerabilities affecting their environments.
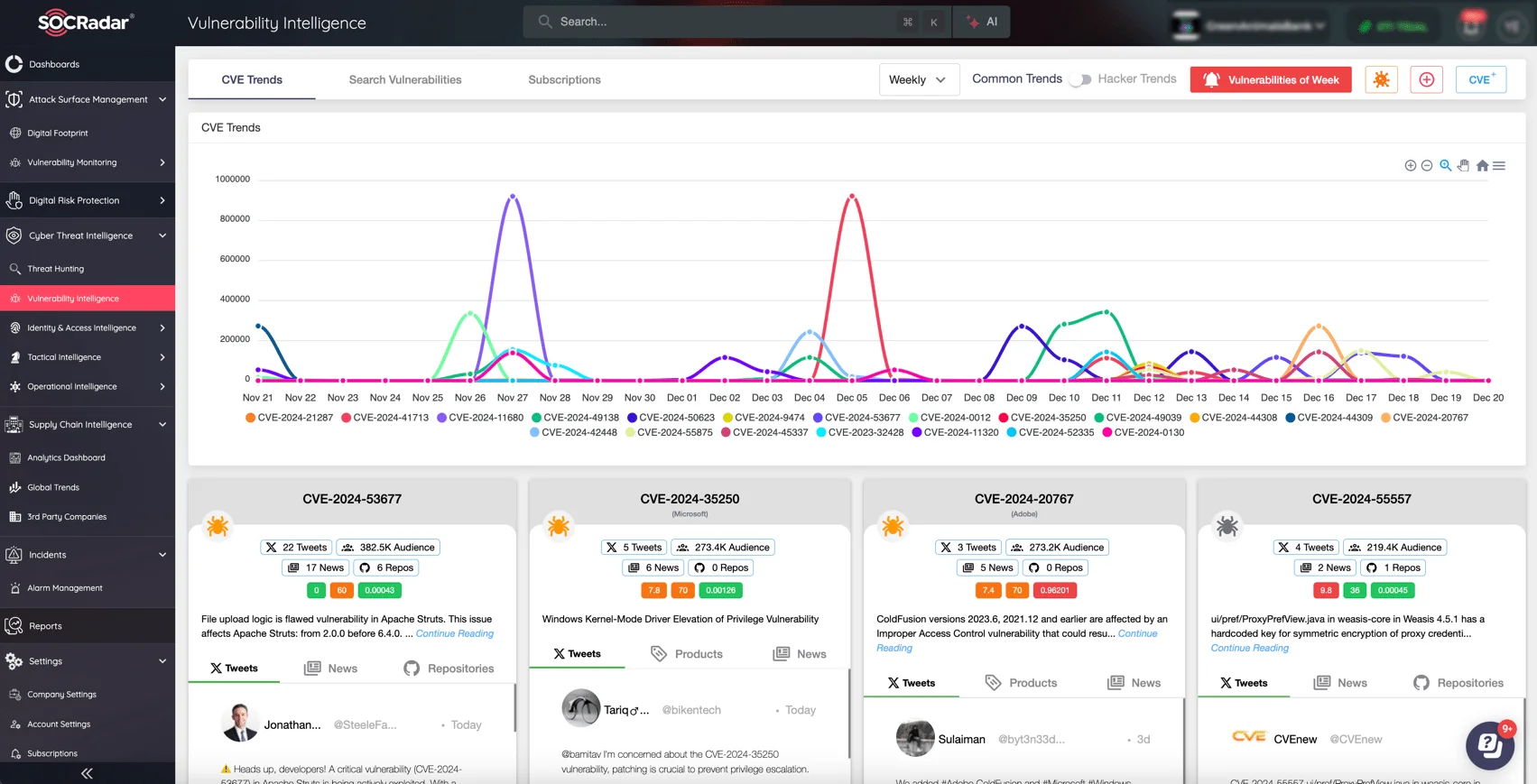
SOCRadar’s Vulnerability Intelligence module
This proactive approach ensures a more effective defense against emerging security threats.
Attack Surface Management
SOCRadar’s Attack Surface Management (ASM) module emphasizes the importance of identifying vulnerable assets and monitoring the cyber attack surface. It enables organizations to detect vulnerable systems and shadow IT, gain real-time visibility into unauthorized access points, and mitigate risk by securing external-facing systems.
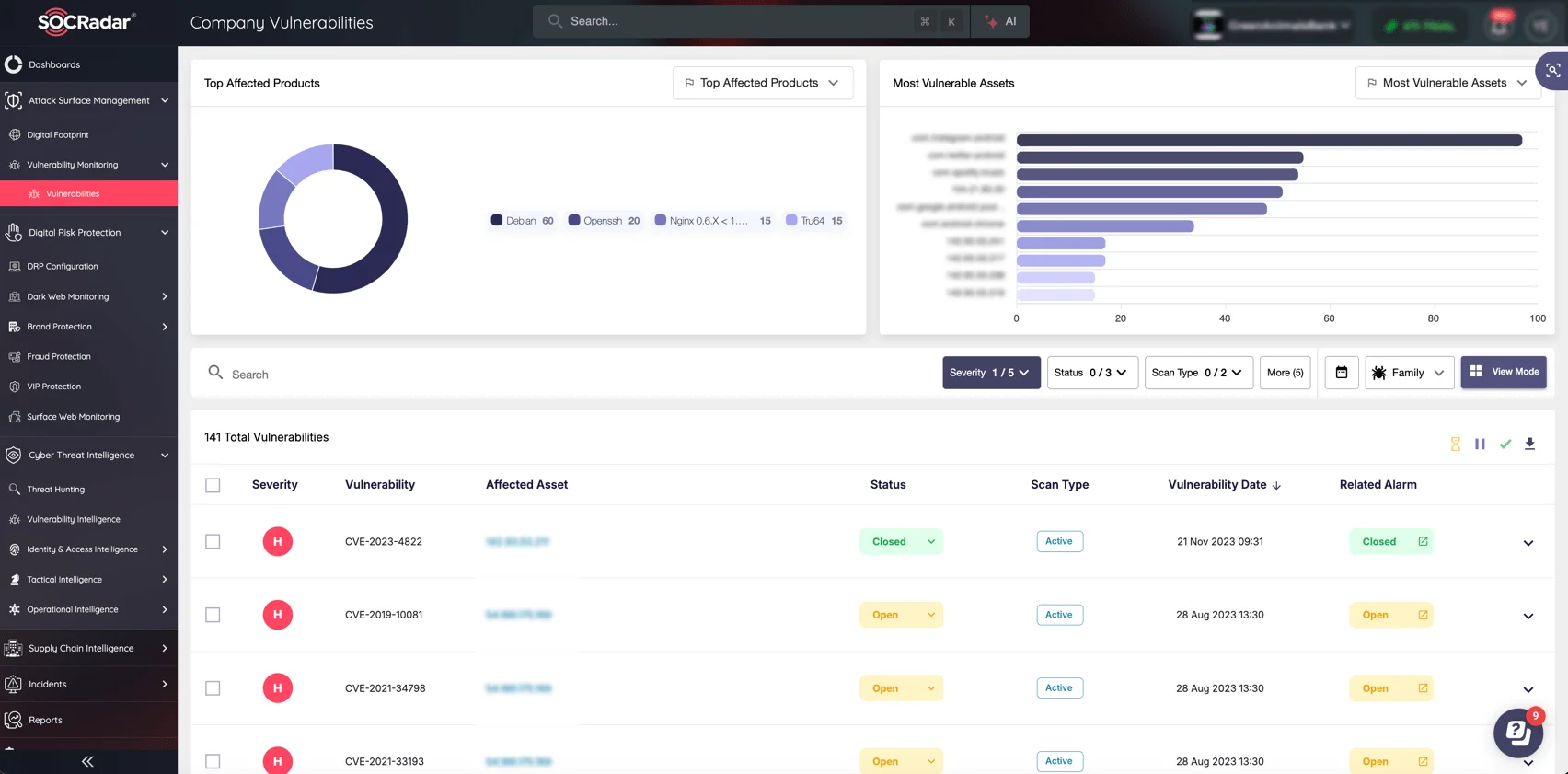
SOCRadar’s Attack Surface Management (ASM) module
This comprehensive view of an organization’s attack surface helps to reduce risks and strengthen defenses against potential exploitation.
Immediate Recommendations
Organizations using BeyondTrust PRA and RS products should:
- Apply Patches: Update to the latest versions to address CVE-2024-12356 and CVE-2024-12686.
- Monitor for IoCs: Review BeyondTrust’s advisories for indicators of compromise, including suspicious IP addresses or anomalous behavior.
- Strengthen Security Posture: Implement enhanced monitoring and leverage SOCRadar’s solutions for ongoing protection and visibility.
By taking these steps, organizations can protect their critical systems, minimize risks, and maintain robust security against evolving threats.




































