
Binance Stealer Logs, Exodus Botnet, Instagram 0-day Exploit, and Database Sales
Explore the most recent dark web threats identified by SOCRadar’s Dark Web Team. From the exposure of Binance user stealer logs to the availability of the Exodus Botnet tool, the digital underworld’s capabilities are expanding.
Concerns arise with the alleged 0-day exploit targeting Instagram and the sale of Dubai property owners’ database. Additionally, the breach of Nissan Australia’s database underscores the pervasive risks of cybercrime.
Receive a Free Dark Web Report for Your Organization:
Stealer Logs of Binance are Leaked
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to have obtained stealer logs from Binance users, a major cryptocurrency exchange. Stealer logs are essentially records obtained from malware-infected devices or breached systems that contain a wealth of sensitive information. This type of data often includes login credentials, financial details, and personal information, making it extremely valuable to cybercriminals.
Exodus Botnet Tool is on Sale
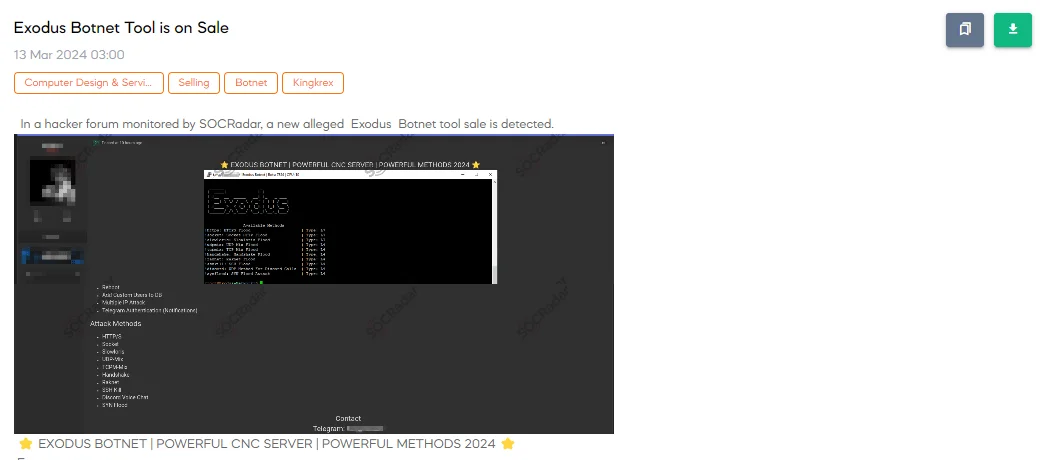
The SOCRadar Dark Web Team discovered a post on a hacker forum where a threat actor is advertising the sale of a new botnet tool, dubbed the Exodus Botnet. This tool is presented as a powerful Command-and-Control (C&C) server solution equipped with a variety of attack methods and features designed to orchestrate and execute cyber attacks. The features listed for the Exodus Botnet include capabilities such as scanning for vulnerable systems, rebooting systems, adding custom users to databases, launching attacks from multiple IP addresses, and even integrating with Telegram for authentication and notifications.
0-day Exploit of Instagram is on Sale
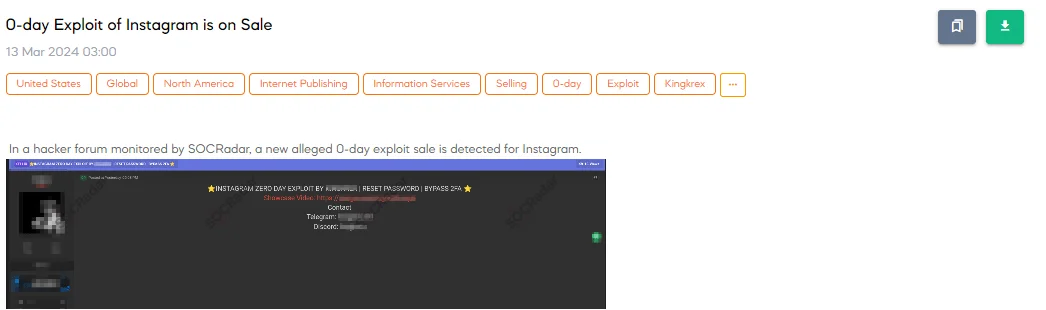
The SOCRadar Dark Web Team uncovered a post on a hacker forum where a threat actor is advertising an alleged new zero-day exploit for Instagram. This exploit allegedly allows for a reset of passwords and the ability to bypass Two-Factor Authentication (2FA), a critical security feature designed to add an extra layer of protection to user accounts.
Database of Dubai Property Owners is on Sale
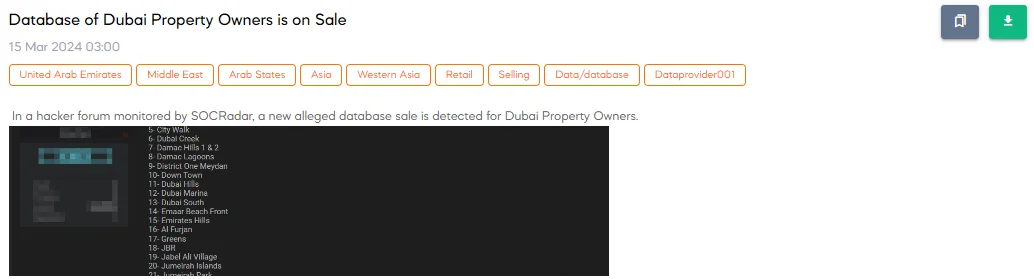
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a database of Dubai property owners. This database is purported to be up-to-date as of 2024, covering various areas within Dubai, and contains information on up to 200,000 contacts.
The level of detail available in this alleged database appears to be extensive, offering a wide range of personal and property-specific information including, but not limited to, procedure values, building names, unit numbers, property types, and owner details such as names, mobile numbers, and even sensitive personal identification information like ID numbers, UAE ID numbers, passport expiry dates, birth dates, and unified numbers.
Database of Nissan Australia is Leaked
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor has claimed to have leaked the database of Nissan Australia. This alleged breach appears to be substantial, with the data encompassing a wide range of sensitive information, including employee details, ongoing projects, confidentiality agreements, and customer information.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































