
Massive Swiss Medical Leak, Binance Phishing Panel, and WhatsApp Ban S...
Massive Swiss Medical Leak, Binance Phishing Panel, and WhatsApp Ban Service Found SOCRadar’s Dark Web Team has uncovered several alarming cyber threats circulating on hacker forums this week. Key dis...

Top 10 Advanced Persistent Threat (APT) Groups That Dominated 2024
Top 10 Advanced Persistent Threat (APT) Groups That Dominated 2024 Advanced Persistent Threats (APTs) are among the most sophisticated and persistent cyber adversaries in the world. Unlike ordinary cy...
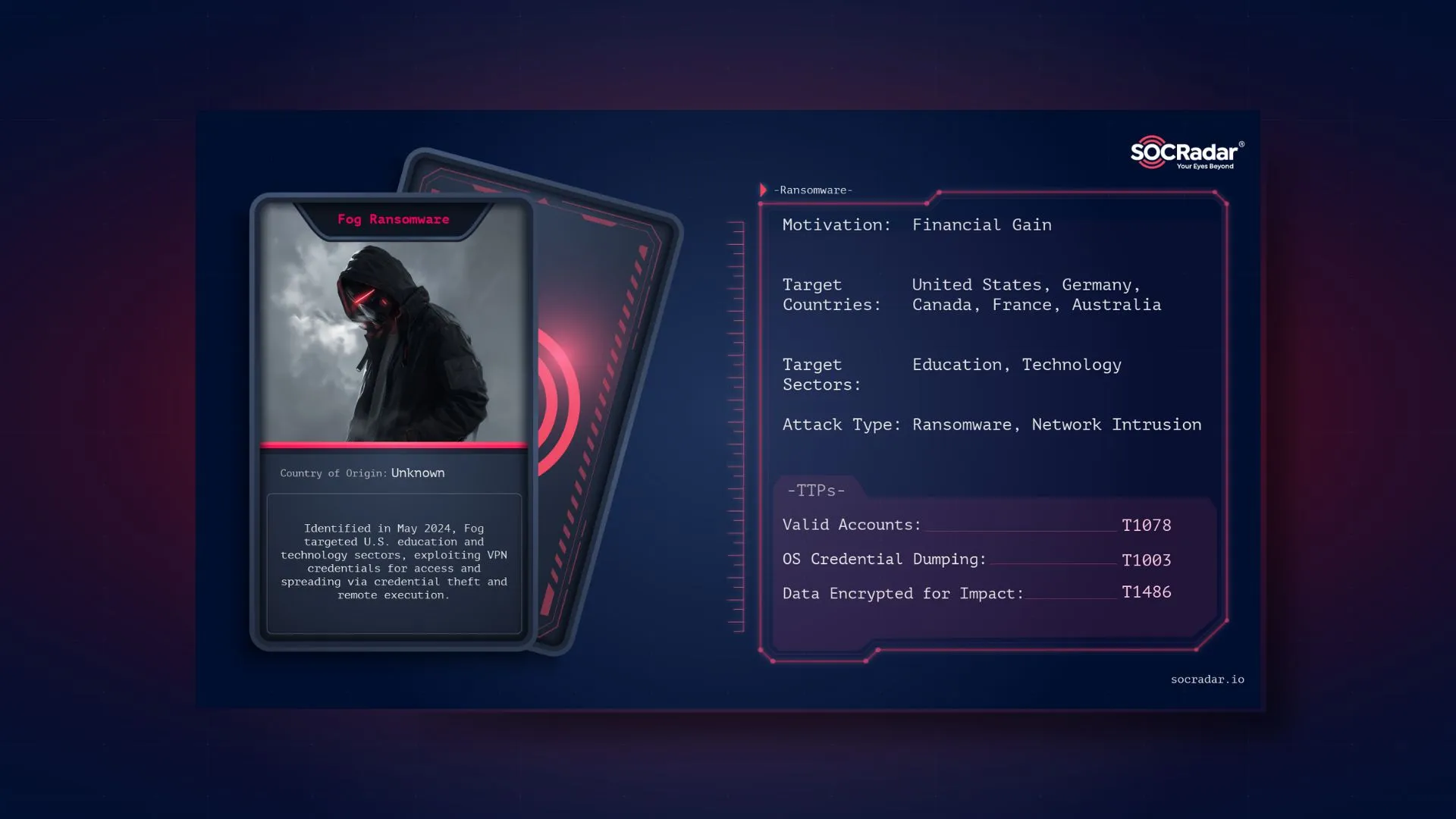
Dark Web Profile: Fog Ransomware
Dark Web Profile: Fog Ransomware Fog Ransomware emerged in April 2024, was first detected in the wild in early May, primarily targeting US based educational institutions targeting both Windows and Lin...

International Operation Targets 8Base and Phobos Ransomware Gangs
International Operation Targets 8Base and Phobos Ransomware Gangs In a coordinated global effort, law enforcement agencies have successfully dismantled the dark web infrastructure of the 8Base ransomw...

Dread: The Dark Web’s Reddit-Like Forum
Dread: The Dark Web’s Reddit-Like Forum Dark web forums are crucial gathering points for cybercriminals, facilitating illegal trade, data breaches, and financial fraud. According to SOCRadar’s Annual ...

Massive OpenAI Leak, WordPress Admin Exploit, Inkafarma Data Breach
Massive OpenAI Leak, WordPress Admin Exploit, Inkafarma Data Breach SOCRadar’s Dark Web Team has detected a wave of cyber threats on hacker forums this week, including an alleged leak of millions of O...

The Escalating Threat of the Dark Web to Small and Medium Enterprises ...
The Escalating Threat of the Dark Web to Small and Medium Enterprises (SMBs) The Dark Web poses significant threats to Small and Medium-sized Businesses (SMBs) because it serves as a marketplace for c...
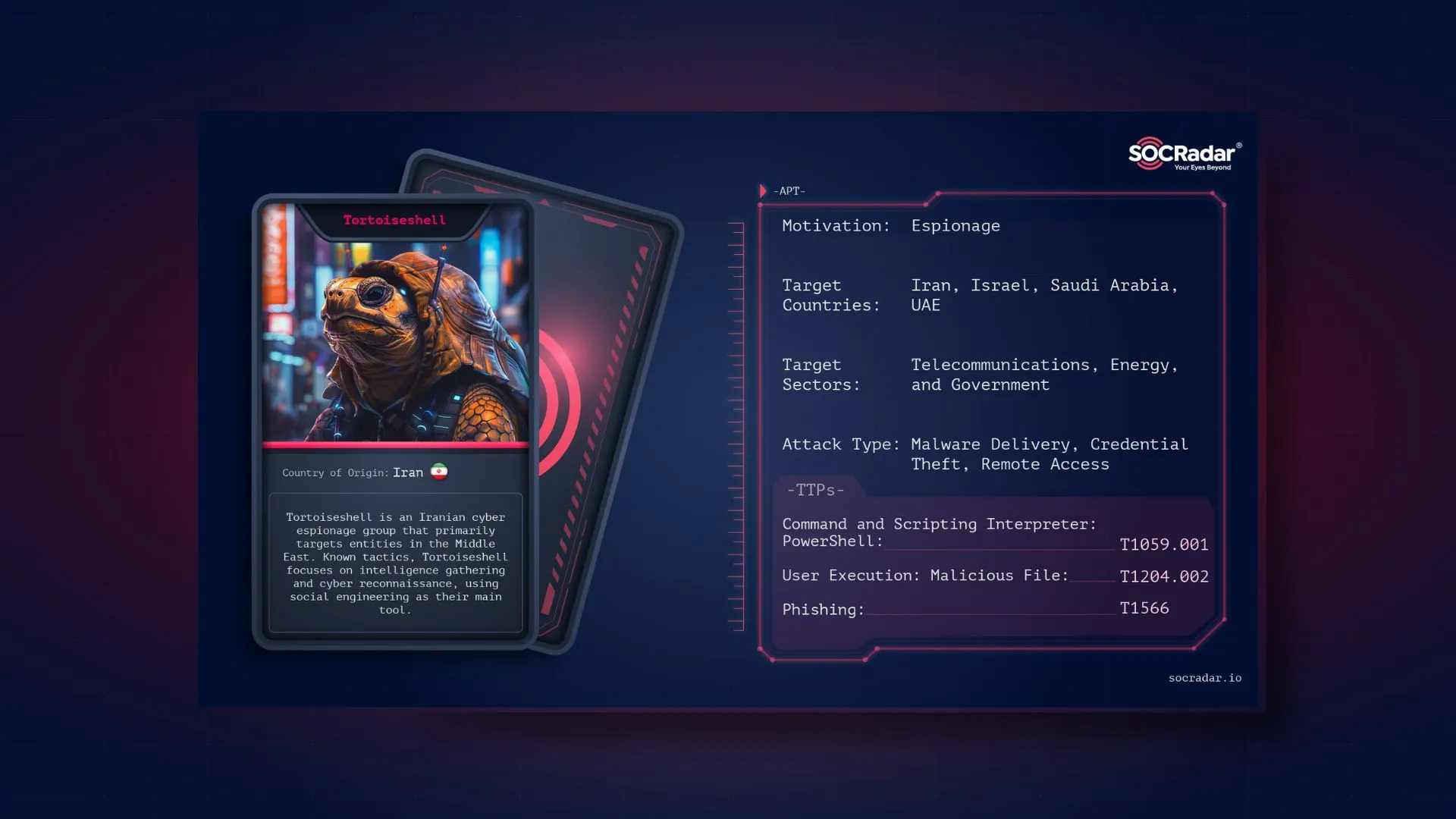
Dark Web Profile: Tortoiseshell APT
Dark Web Profile: Tortoiseshell APT In recent years, Iran has ramped up cyber campaigns to safeguard national interests, deter adversaries, and conduct espionage. These operations are carried out by u...

IntelBroker Strikes HPE Again, Cardinal Health Breach, and U.S. ISP Ro...
IntelBroker Strikes HPE Again, Cardinal Health Breach, and U.S. ISP Root Access Sale SOCRadar’s Dark Web Team has identified alarming cyber threats this week, including a second alleged data leak from...
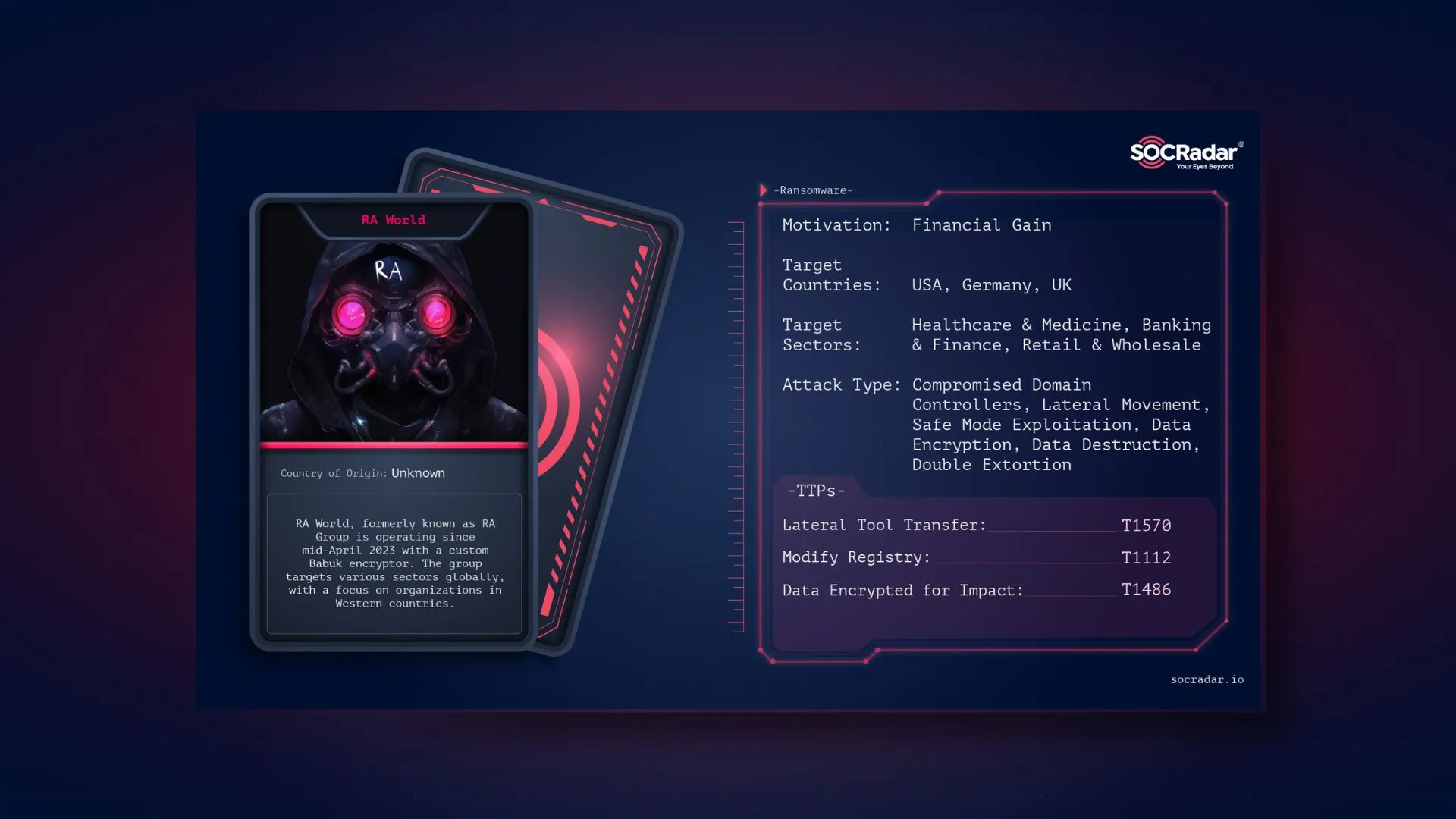
Dark Web Profile: RA World
Dark Web Profile: RA World RA World is believed to be a rebranded iteration of the ransomware operation previously known as RA Group. This is because it employed the same extortion and encryption tech...

Dark Web Profile: Termite Ransomware
Dark Web Profile: Termite Ransomware The dark web, a hidden part of the internet, remains a source of growing cyber threats, with ransomware being one of the most prominent. Among these threats, Termi...

Dark Web Profile: FunkSec
Dark Web Profile: FunkSec [Update] January 4, 2024: “Update: FunkSec Expands Their Operation and Teams Up With Other Cyber Criminals” A new ransomware group, FunkSec, has gained attention after taking...

Lyca Mobile Breach, U.S. Government VPN Access, TalkTalk Data Leak Amo...
Lyca Mobile Breach, U.S. Government VPN Access, TalkTalk Data Leak Among Latest Cyber Threats This week, hacker forums revealed several alarming cyber incidents, including an alleged database leak fro...

Dark Web Profile: OilRig (APT34)
Dark Web Profile: OilRig (APT34) OilRig, also known as APT34, is a state-sponsored Advanced Persistent Threat (APT) group with strong ties to Iranian intelligence. Known for its sophisticated cyber-es...

IntelBroker Targets HPE, Carrefour France Leak, Nillious Android RAT
IntelBroker Targets HPE, Carrefour France Leak, Nillious Android RAT SOCRadar’s Dark Web Team has reported significant findings on hacker forums over the past week, including a range of high-profile d...

The Dark Web Economy: A Hidden Marketplace Reshaping Cybersecurity
The Dark Web Economy: A Hidden Marketplace Reshaping Cybersecurity In today’s digital landscape, cybersecurity isn’t just about sophisticated technical exploits anymore. The game has funda...

Dux Human Health Breach, U.S. Credit Card Sale, Boulanger Database Lea...
Dux Human Health Breach, U.S. Credit Card Sale, Boulanger Database Leak, and More SOCRadar’s Dark Web Team has monitored concerning activity on hacker forums over the past week, revealing significant ...
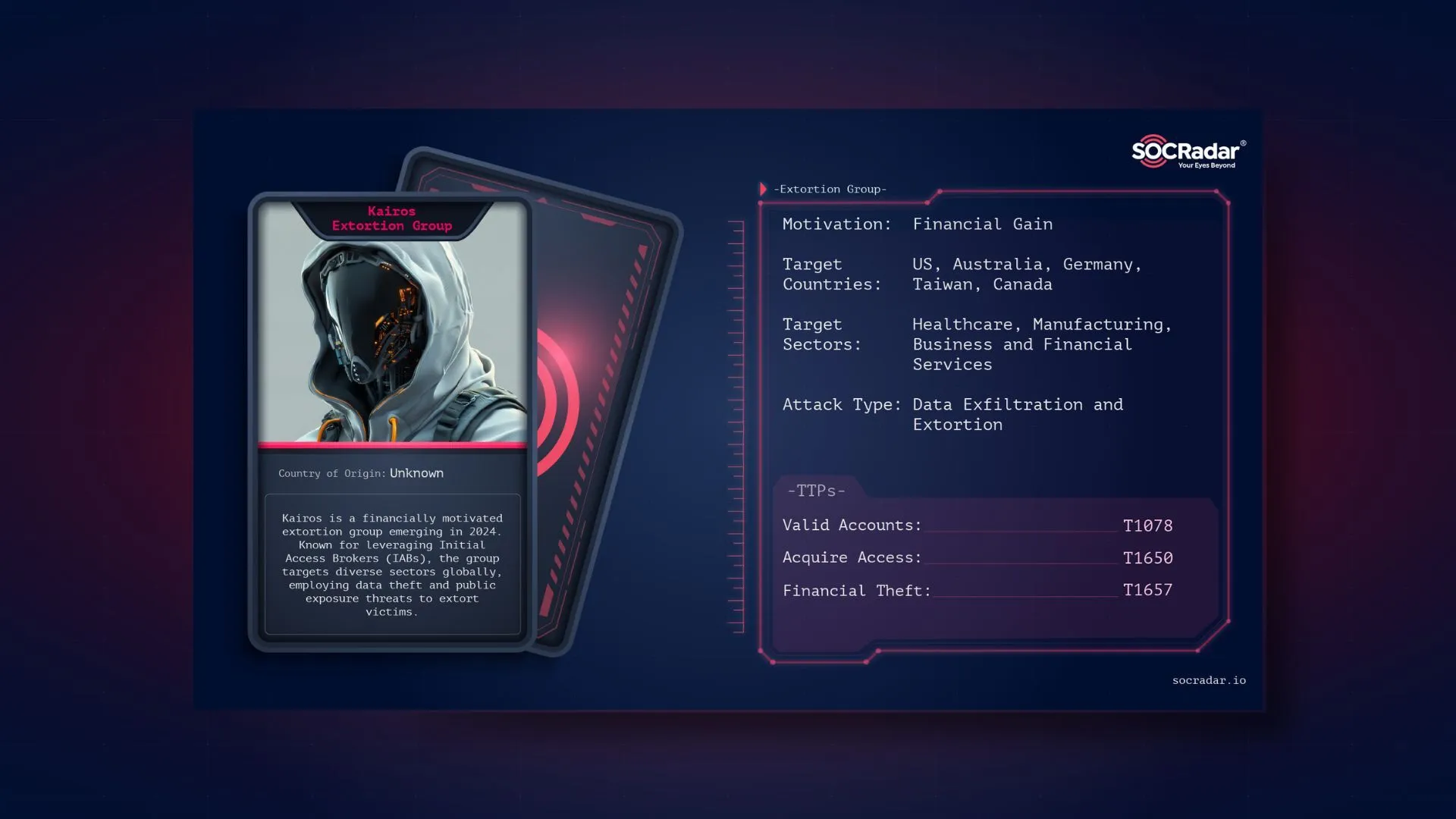
Dark Web Profile: Kairos Extortion Group
Dark Web Profile: Kairos Extortion Group Kairos is a low-profile but rising cyber extortion group that has been active since late 2024. Unlike many of its counterparts, Kairos does not rely on ransomw...

Hacker Forums Reveal ICAO Leak, SonicWall Vulnerability, and Other New...
Hacker Forums Reveal ICAO Leak, SonicWall Vulnerability, and Other New Exploit Sales Recent findings from SOCRadar’s Dark Web Team spotlight a series of alarming cyber threats surfacing on hacke...

Dark Web Monitoring Tools and How They Benefit Businesses
Dark Web Monitoring Tools and How They Benefit Businesses Now as we all know, in depths of the internet lies the Dark Web, a hidden network where cybercriminals thrive. Here, stolen credentials, finan...

































