
CISA Updates: Microsoft 365 Guidance, SCuBAGear Tool, Mozilla Alert, QNAP & FXC Vulnerabilities Enter KEV
CISA has officially released the Microsoft 365 Secure Configuration Baselines, aiming to assist organizations in enhancing the security and resilience of their Microsoft 365 cloud services. This release also includes an updated tool called SCuBAGear (Secure Cloud Business Applications Gear).
Developed by CISA, SCuBAGear is an automated assessment tool crafted to evaluate the status of organizations’ M365 cloud services in alignment with CISA’s recommended baselines.

The SCuBA project offers guidance and capabilities to secure cloud business application environments, safeguarding federal information throughout its lifecycle. For more details on the SCuBA project, visit CISA’s page.
In essence, CISA’s recent updates to the Microsoft 365 Secure Configuration Baselines include stakeholder input from last year’s public comment period and a pilot effort with federal agencies. These updates have been seamlessly integrated with the SCuBAGear tool, now enhanced for better automation, reducing organizational workload, as reported by CISA.
Additionally, CISA has issued an alert concerning updates on significant vulnerabilities affecting Mozilla’s Firefox browser and Thunderbird email client software. Also, two high-severity vulnerabilities have been added to the Known Exploited Vulnerabilities (KEV) Catalog.
CISA Issued an Alert for Mozilla Firefox and Thunderbird Updates Addressing High Impact Vulnerabilities
CISA has issued an alert highlighting Mozilla’s recent updates for Firefox and Thunderbird, addressing vulnerabilities deemed ‘High’ in impact. CISA cautions that malicious actors could exploit the vulnerabilities, potentially gaining control over affected systems. Administrators and users are strongly advised to promptly implement the necessary measures to mitigate these risks.
Details of the vulnerabilities are as follows:
CVE-2023-6856 (Heap-buffer-overflow in WebGL DrawElementsInstanced method with Mesa VM driver) and CVE-2023-6864 (Memory safety bugs) have been fixed in Firefox ESR 115.6, Firefox 121, and Thunderbird 115.6. Exploitation of CVE-2023-6856 could lead to Remote Code Execution (RCE) and sandbox escape, while CVE-2023-6864 could result in memory corruption and running arbitrary code.
CVE-2023-6865 (Potential exposure of uninitialized data in EncryptingOutputStream) has been addressed in Firefox ESR 115.6 and Firefox 121.
CVE-2023-6135 and CVE-2023-6873, fixed in Firefox 121, involve multiple NSS NIST curves susceptible to the “Minerva” attack and Memory safety bugs present in Firefox 120, respectively. CVE-2023-6135 could allow attackers to recover the private key, while CVE-2023-6873 could result in memory corruption and the execution of arbitrary code.
CVE-2023-50762 and CVE-2023-50761, addressed in Thunderbird 115.6, involve a truncated signed text showing with a valid OpenPGP signature and an S/MIME signature being accepted despite a mismatching message date, respectively. CVE-2023-50762 could be exploited to spoof email messages, and using the CVE-2023-50761 vulnerability, an attacker could manipulate the perceived date and time of a message.
SOCRadar XTI provides real-time alerts and comprehensive Vulnerability Intelligence to proactively address critical vulnerabilities, so organizations can stay informed about vulnerabilities targeted by threat actors, receiving actionable insights and context that streamline the response process.
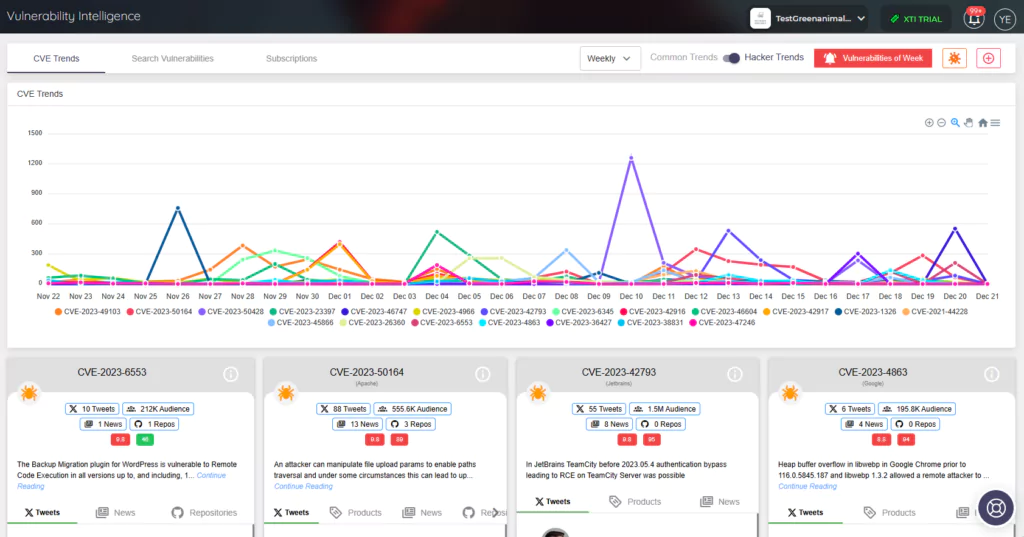
You can delve deeper into SOCRadar’s Vulnerability Intelligence capabilities with CVE Radar, a complimentary feature from SOCRadar Labs. CVE Radar allows you to track vulnerability trends, providing clarity on the most frequently mentioned vulnerabilities, associated exploits, repositories, and the latest updates conveyed through tweets and news blogs.
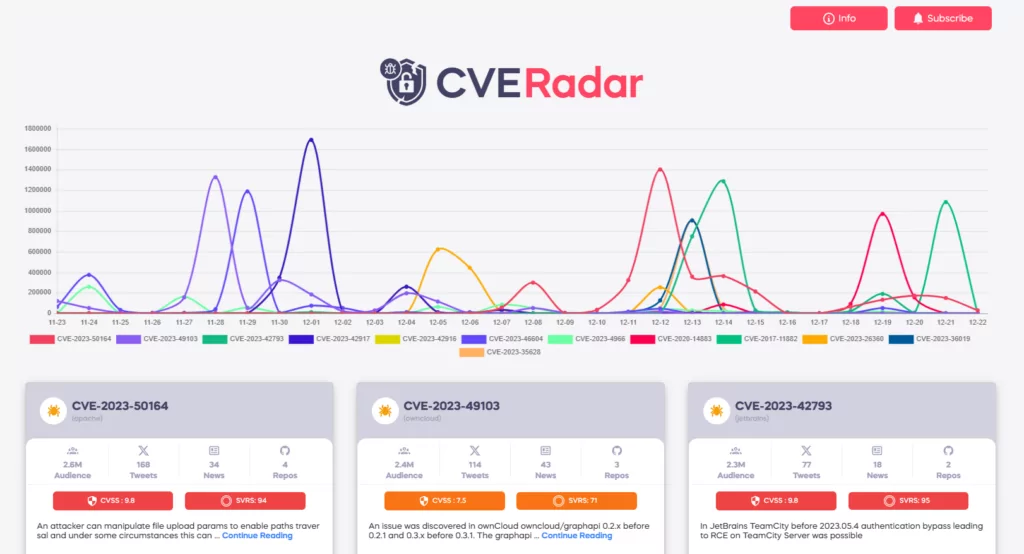
Additions to KEV: High Severity OS Command Injection Vulnerabilities in QNAP’s Legacy VioStor NVR and FXC Routers Are Exploited
On December 21, CISA made updates to the Known Exploited Vulnerabilities (KEV) Catalog, adding two vulnerabilities involving OS command injection. The agency ordered organizations to patch them until January 11, 2024. Here are the details of the vulnerabilities:
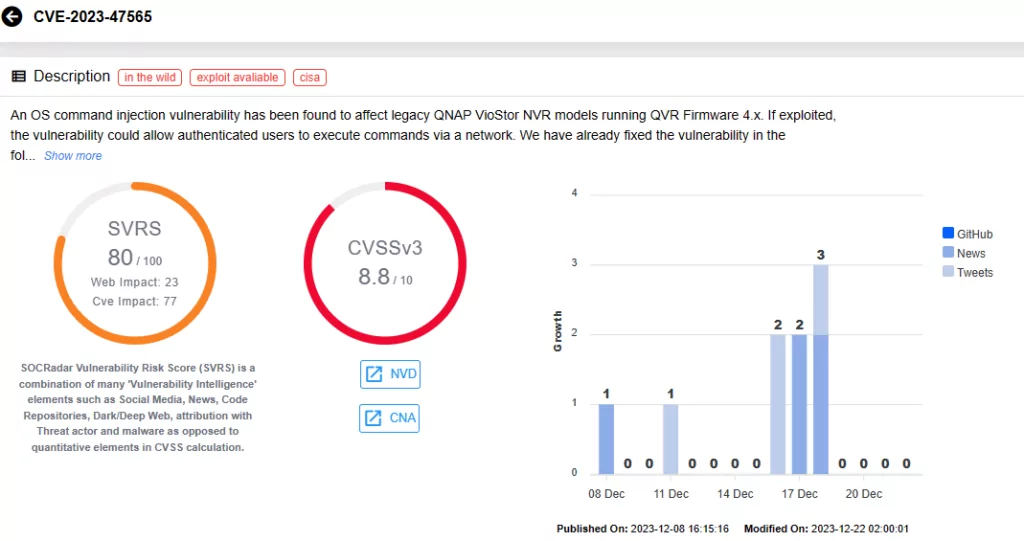
One of the vulnerabilities, CVE-2023-47565 (CVSS score: 8.8, High severity), impacts QNAP VioStor NVR models running QVR Firmware 4.x. Successful exploitation of the vulnerability can enable authenticated attackers to execute commands via a network. QNAP has previously fixed the vulnerability, and users are advised to use QVR Firmware version 5.0.0 and later to avoid its exploitation.
Another vulnerability, CVE-2023-49897 (CVSS score: 8.8, High severity), affects Future X Communications’ (FXC) outlet wall routers, specifically AE1021PE firmware version 2.0.9 and earlier, and AE1021 firmware version 2.0.9 and earlier.
An authenticated attacker can exploit the vulnerability to perform OS command injection with a payload delivered via a POST request to the management interface. It uses device default credentials in the captured payloads in its current configuration.
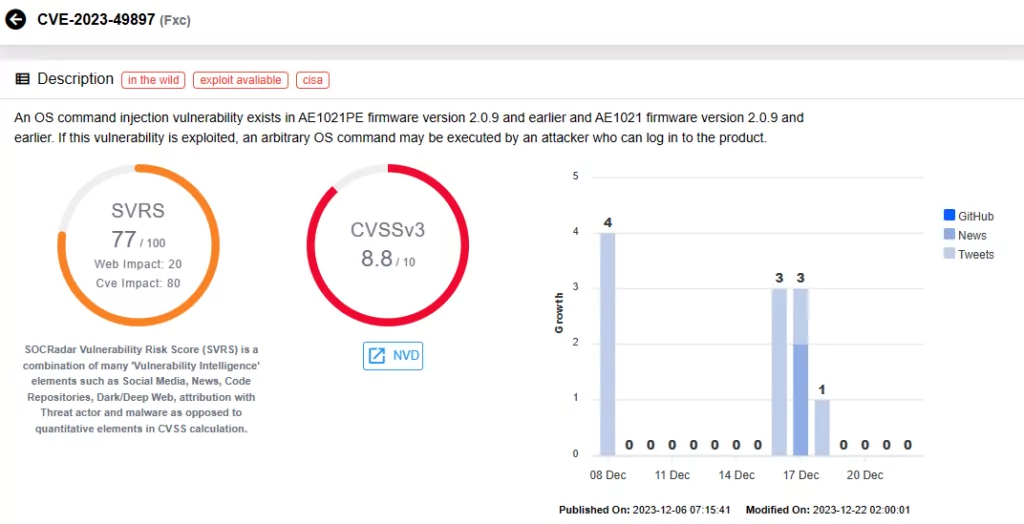
Researchers discovered the CVE-2023-49897 vulnerability as part of a campaign that is building the InfectedSlursbotnet, and the payloads discovered in the wild involve the installation of Mirai-based malware. More information is available here.
FXC has released a patched version of the device’s firmware and advises users to upgrade to version 2.0.10. Performing a factory reset to change the default management screen login password on the first boot is also recommended.
How Can SOCRadar Help?
The Attack Surface Management (ASM) module of SOCRadar keeps an eye out for new threats to your digital assets. You can get alerts about security vulnerabilities that might affect your digital assets through this module, along with information about your asset inventory.
Moreover, the CISA KEV Check feature in the ASM module helps determine whether any vulnerabilities that impact your assets have been added to CISA’s Known Exploited Vulnerabilities catalog.
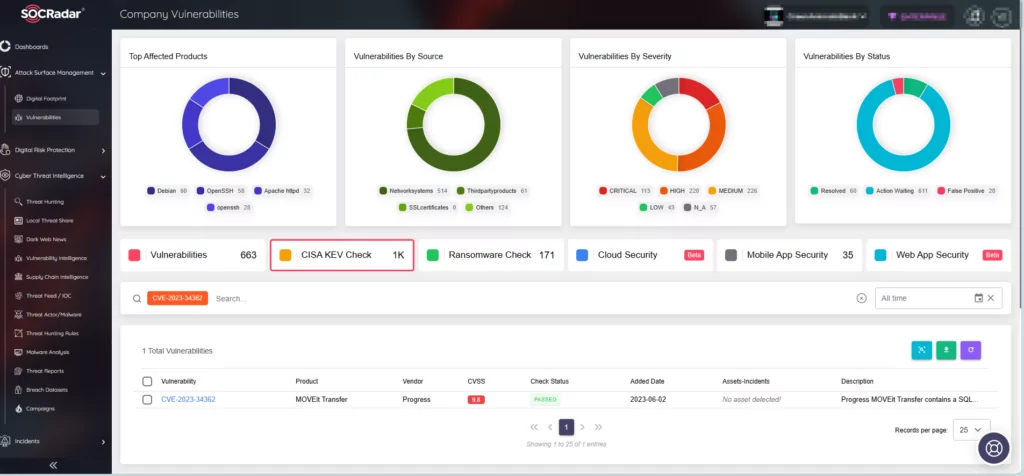
Missing the deadlines for fixing vulnerabilities on CISA KEV can lead to fines and possibly contract termination for compliant organizations. This is why the CISA KEV Check feature on SOCRadar is valuable, notifying organizations about potential issues that threaten their compliance.


































