
Critical Vulnerabilities Affecting GitHub Enterprise Server, Kubernetes Image Builder, and GiveWP Plugin
Recently, several critical vulnerabilities have been disclosed, affecting widely used platforms like GitHub Enterprise Server (GHES), Kubernetes Image Builder, and the GiveWP plugin for WordPress. These vulnerabilities pose significant risks, including unauthorized access, privilege escalation, and remote code execution, impacting businesses and organizations that rely on these tools.
This blog will provide a detailed overview of these vulnerabilities, explore their potential impacts, and show guidance on how to mitigate these threats effectively.
GitHub Enterprise Server (GHES) Security Update – Three Vulnerabilities Addressed, One Critical (CVE-2024-9487)
The latest security update for GitHub Enterprise Server (GHES) addresses three newly discovered vulnerabilities, including a critical issue that could allow unauthorized access to the platform. These vulnerabilities, reported through GitHub’s Bug Bounty program, have raised concerns due to the potential risks they pose for organizations using self-hosted versions of GHES.
While GitHub has already provided patches for these vulnerabilities, it is important for organizations to understand the implications of the flaws and ensure timely updates to protect their systems.
CVE-2024-9487 – Critical SAML SSO Authentication Bypass
CVE-2024-9487 (CVSS 9.5) is a critical flaw in GitHub Enterprise Server (GHES) that enables attackers to bypass SAML Single Sign-On (SSO) authentication if the optional encrypted assertions feature is active. This vulnerability allows unauthorized user provisioning and access to the system due to improper cryptographic signature verification within the SAML authentication process.
It’s important to highlight that encrypted assertions are not enabled by default; moreover, attackers would need direct network access and a signed SAML response or metadata document to exploit this issue.
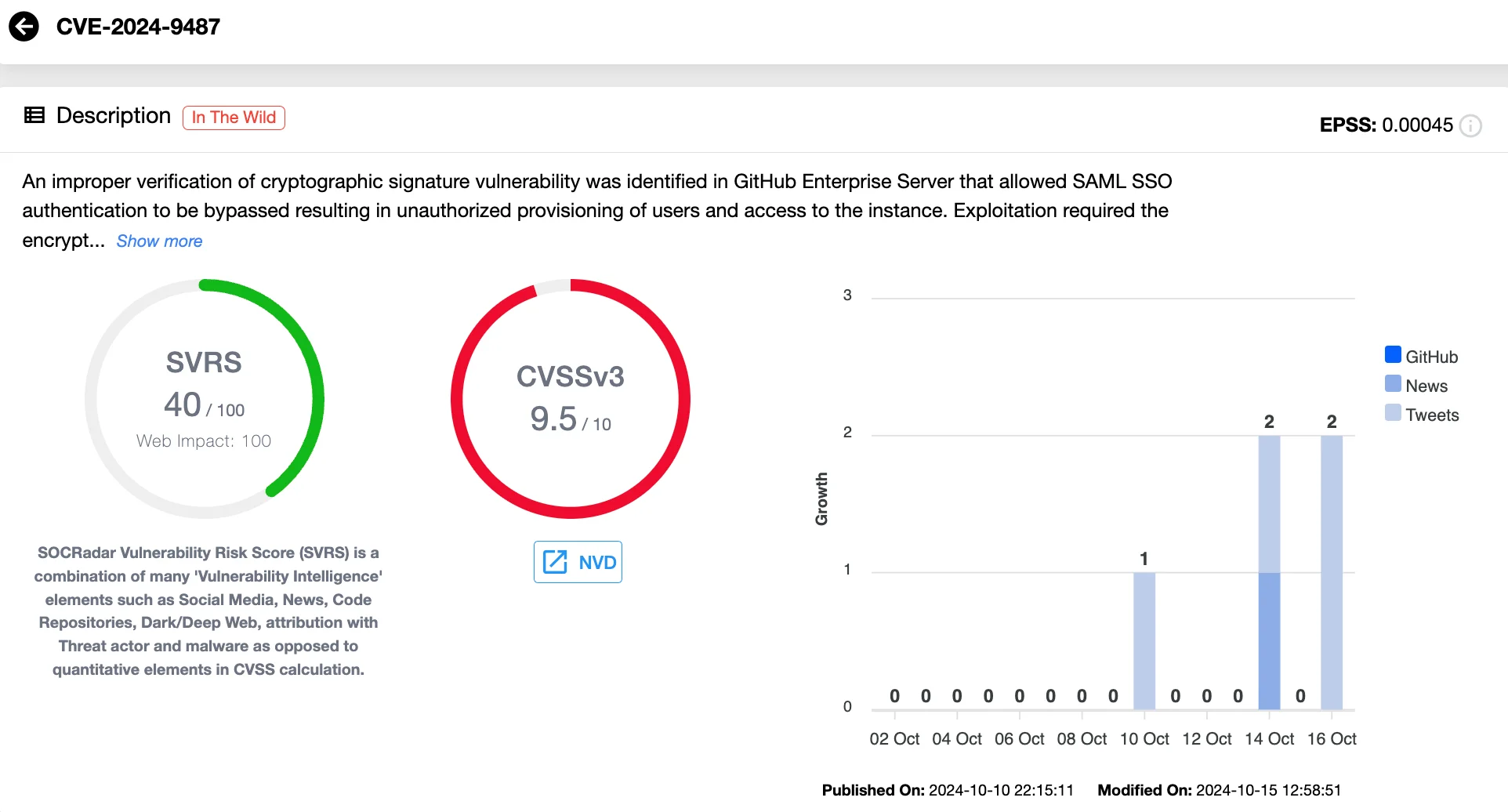
Details of CVE-2024-9487 (SOCRadar Vulnerability Intelligence)
This vulnerability emerged as a result of regression from the remediation efforts for CVE-2024-4985, a previous authentication bypass vulnerability with a CVSS score of 9.8. Learn more about CVE-2024-4985.
In addition to CVE-2024-9487, another CVE – CVE-2024-9539 (CVSS 5.7) – was also addressed. This lower-severity vulnerability could allow an attacker to retrieve metadata by tricking victims into clicking malicious URLs linked to SVG assets. Furthermore, GitHub resolved a sensitive data exposure issue within HTML forms in the management console by removing the “Copy Storage Setting from Actions” feature.
Update GHES to Prevent Exploitation
All of the latest security vulnerabilities in GitHub Enterprise Server (GHES), including CVE-2024-9487 and CVE-2024-9539, have been addressed in versions 3.14.2, 3.13.5, 3.12.10, and 3.11.16. Organizations using vulnerable self-hosted versions should update immediately to protect their systems.
ZoomEye results reveal over 81,000 instances of GitHub Enterprise Server exposed on the internet, with the majority located in the United States. This number highlights the potential assets that may be vulnerable to the recently disclosed vulnerabilities.
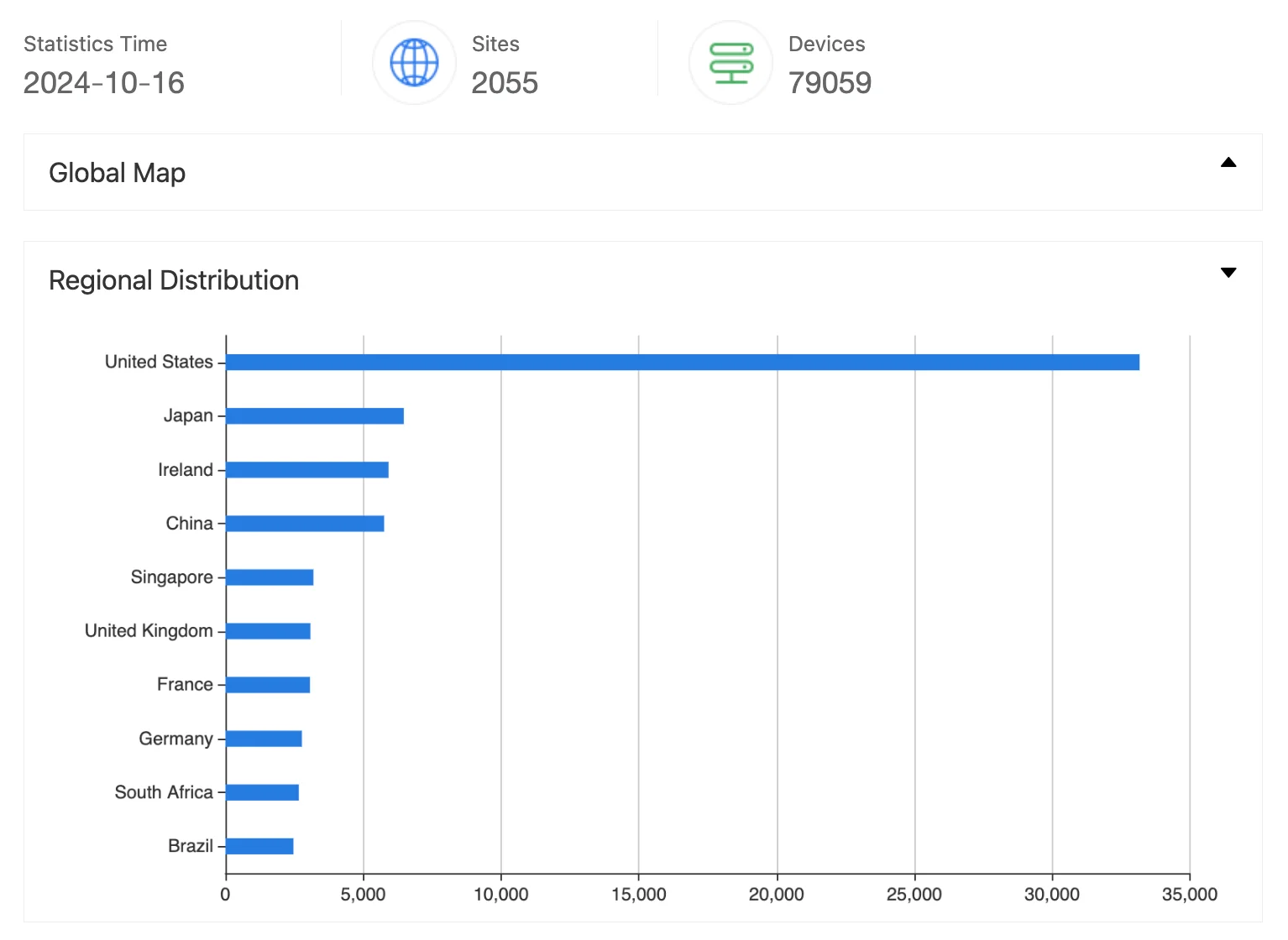
Results for GitHub Enterprise on ZoomEye
Exploitation of these vulnerabilities can result in unauthorized access, data exposure, and user account compromise. In the case of CVE-2024-9487, a successful attack could result in full access to the system, enabling further malicious actions. Therefore, timely updates are essential to minimize risk, safeguard sensitive data, and reduce your organization’s attack surface.
SOCRadar’s Attack Surface Management (ASM) module enhances your security posture by offering continuous monitoring of your digital assets. It provides real-time alerts on potential vulnerabilities, helping your organization identify and prioritize risks before they are exploited.
ASM integrates with your patch management strategy, providing detailed insights for identifying and resolving vulnerabilities within your systems.
Critical Kubernetes Vulnerabilities in Image Builder Expose VMs to Root Access Attacks
Close in timing with the GitHub security updates, the Kubernetes Security Response Committee disclosed vulnerabilities specifically affecting Kubernetes Image Builder, a tool used to create virtual machine images across various infrastructure platforms.
Two important vulnerabilities, CVE-2024-9486 and CVE-2024-9594, were identified, which could allow attackers to gain root access to virtual machines by exploiting default credentials used during the image build process.
CVE-2024-9486 (CVSS 9.8) This vulnerability affects images built with the Proxmox provider. The issue occurs because these virtual machines retain default credentials, making them accessible to attackers who can exploit this weakness to gain complete control over the virtual machines.
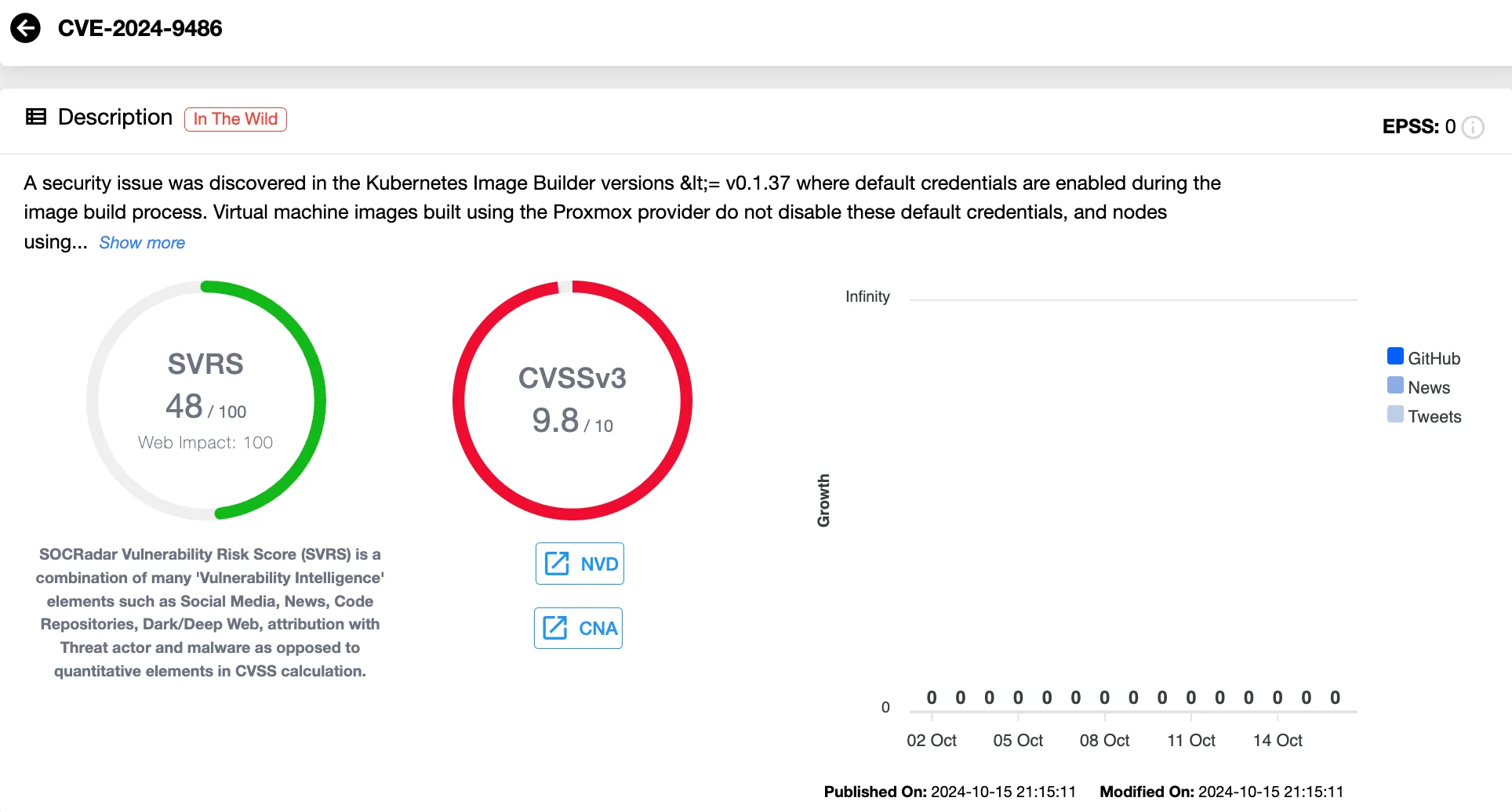
Details of CVE-2024-9486 (SOCRadar Vulnerability Intelligence)
On the other hand, CVE-2024-9594 (CVSS 6.3) impacts images built with Nutanix, OVA, QEMU, and raw providers, and involves default credentials that are used during the build process but disabled upon completion. This less severe vulnerability is exploitable only if an attacker gains access to the virtual machine during the build process.
Which Versions Are Affected?
Clusters running virtual machine images built with Kubernetes Image Builder v0.1.37 or earlier, alongside any of the impacted providers, are at significant risk. The vulnerabilities could leave these virtual machines susceptible to exploitation by attackers, particularly if default credentials are not disabled during the build process.
Ensure Your Kubernetes Image Builder is Updated
The Kubernetes Security Response Committee strongly recommends rebuilding any vulnerable images using Image Builder v0.1.38 or later to prevent exploitation.Download the latest version here.
For the critical vulnerability CVE-2024-9486, an additional mitigation step involves disabling the “builder” account on affected virtual machines by running the ‘usermod -L builder’ command.
To verify your current Image Builder version, use the following commands, as provided in the advisory:
- For git clones: make version
- For tarball downloads: grep -o v0.[0-9.]* RELEASE.md | head -1
- For container image releases: docker run –rm <image pull spec> version or podman run –rm version
Ensure you’re using the latest version to protect your virtual machines from exploitation.
Critical Vulnerability in GiveWP Donation Plugin (CVE-2024-9634)
The final critical vulnerability we will highlight in this blog concerns the GiveWP Donation Plugin, a popular WordPress tool used by over 100,000 fundraiser websites.
This plugin, essential for fundraising platforms, is vulnerable to CVE-2024-9634 (CVSS 9.8), a PHP Object Injection flaw affecting all versions up to and including 3.16.3.
The vulnerability allows unauthenticated attackers to inject a PHP object through the deserialization of untrusted input from the give_company_name parameter. When combined with a POP chain, this flaw could lead to Remote Code Execution (RCE).
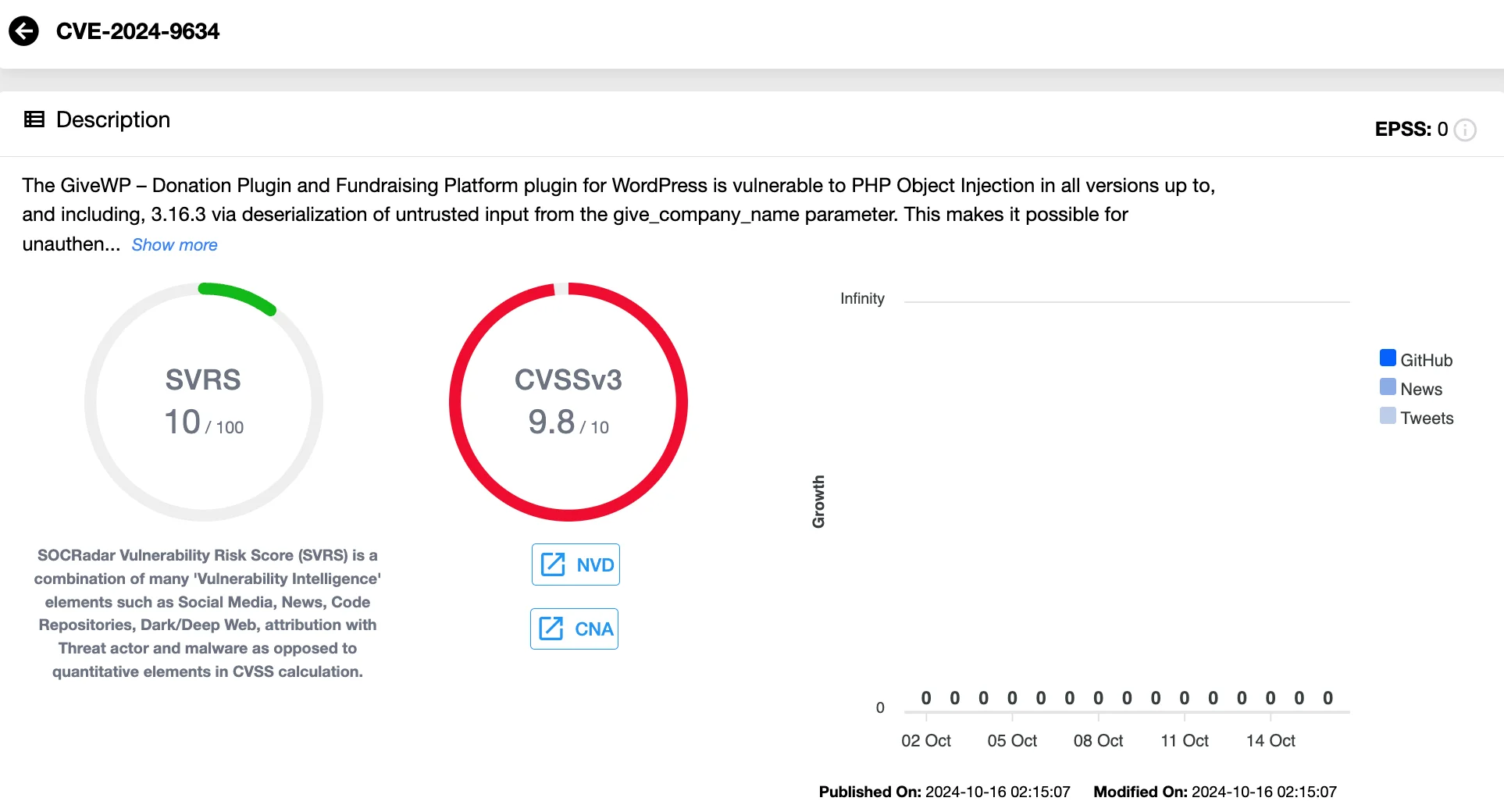
Details of CVE-2024-9634 (SOCRadar Vulnerability Intelligence)
To remediate the CVE-2024-9634 vulnerability, it is strongly recommended that all websites using the affected plugin update to version 3.16.4 or later
Tracking the state of multiple vulnerabilities, third-party software disclosures, and asset exposures can be complex, but is critical to protecting your organization. With SOCRadar’s Vulnerability Intelligence, you can efficiently track and manage vulnerabilities, gaining real-time insights into emerging CVEs, exploitation trends, and hacker activities.
SOCRadar’s Vulnerability Intelligence, available under the Cyber Threat Intelligence (CTI) module
Leveraging Vulnerability Intelligence allows your security team to respond proactively, enhancing your overall vulnerability management strategy.



































