Critical Vulnerability in F5 BIG-IP Configuration Utility Allows Request Smuggling, Leads to RCE: CVE-2023-46747
[Update] November 1, 2023: See the subheading: “F5 Reports Active Exploitation of CVE-2023-46747 in BIG-IP in Combination with CVE-2023-46748.”
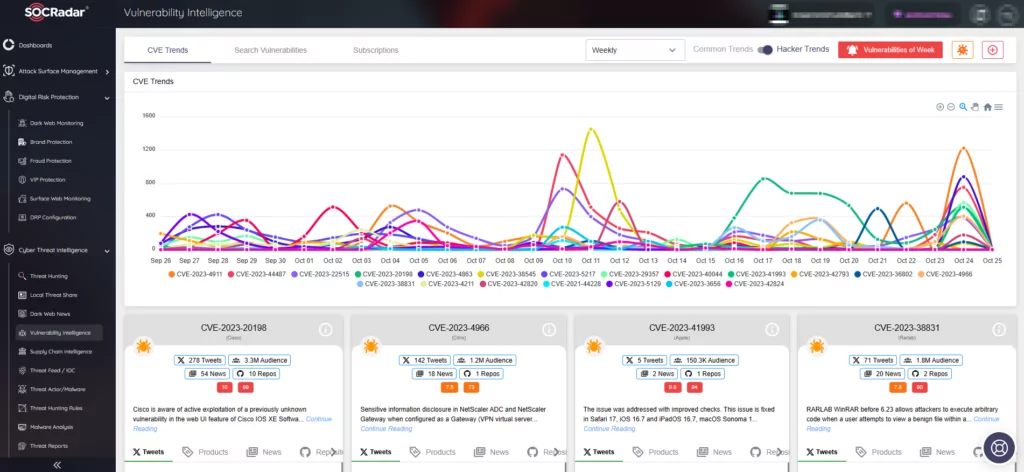
A recent discovery within F5 BIG-IP products reveals a critical vulnerability, identified as CVE-2023-46747, which permits unauthenticated remote code execution. This vulnerability holds a CVSS score of 9.8, raising substantial security concerns.
F5 Networks’ BIG-IP, a comprehensive suite spanning hardware platforms and software solutions, prioritizes security, reliability, and performance. These solutions feature load balancing, web application firewall, access control, and measures to optimize application performance and counteract DDoS attacks, emphasizing application availability and security.
Which Versions of F5 BIG-IP Are Affected by CVE-2023-46747?
The vulnerability impacts all versions of F5 BIG-IP from 17.1.0 to 13.1.5; nevertheless, hotfixes are available to address the issue:
|
Vulnerable versions |
Fixes introduced in |
|
17.1.0 |
17.1.0.3 + Hotfix-BIGIP-17.1.0.3.0.75.4-ENG |
|
16.1.0 – 16.1.4 |
16.1.4.1 + Hotfix-BIGIP-16.1.4.1.0.50.5-ENG |
|
15.1.0 – 15.1.10 |
15.1.10.2 + Hotfix-BIGIP-15.1.10.2.0.44.2-ENG |
|
14.1.0 – 14.1.5 |
14.1.5.6 + Hotfix-BIGIP-14.1.5.6.0.10.6-ENG |
|
13.1.0 – 13.1.5 |
13.1.5.1 + Hotfix-BIGIP-13.1.5.1.0.20.2-ENG |
What is the CVE-2023-46747 Vulnerability in F5 BIG-IP About?
CVE-2023-46747 stems from a flaw in the F5 BIG-IP Configuration Utility, a tool for remotely managing and configuring BIG-IP systems. It represents a request smuggling vulnerability, enabling attackers to dispatch multiple HTTP requests within a single packet.
Successful exploitation of CVE-2023-46747 allows attackers to bypass authentication in the Configuration Utility and execute arbitrary system commands.
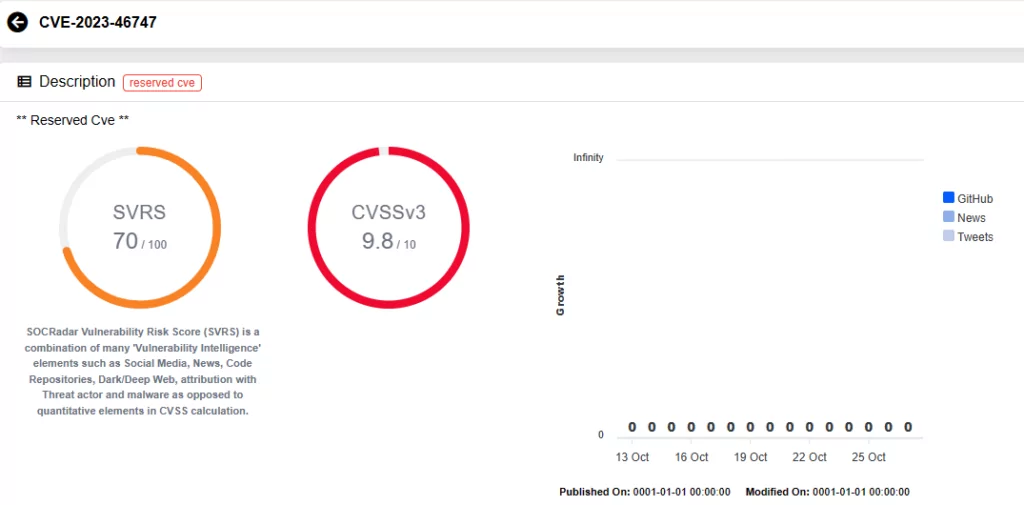
Researchers identified this vulnerability on October 4, 2023. They recently shed light on it in a blog post, emphasizing its close relation to CVE-2022-26377, another request smuggling vulnerability (affecting the Apache HTTP Server). Researchers also assert that the vulnerability impacts the Traffic Management User Interface (TMUI), which had previously experienced CVE-2022-1388 and another critical remote code execution vulnerability, identified as CVE-2020-5902.
How to Apply the Patch? Is There a Mitigation Available?
To address CVE-2023-46747, the primary and most recommended approach is to apply the patches for vulnerable F5 BIG-IP products. F5 has released hotfixes for all affected versions of BIG-IP, which can be obtained from the F5 Support website.
However, if applying the patch is not immediately feasible, you can consider the following interim mitigation methods to limit exposure:
- Block Configuration Utility Access Through the Management Interface: Implement an access control list (ACL) to restrict access to the F5 Traffic Management User Interface from external sources.
- Block Configuration Utility Access Through Self IP Addresses: Restrict all access to the Configuration utility of your BIG-IP system by managing self IP addresses. Adjust the Port Lockdown setting to “Allow None” for each self IP address on the system. If necessary, use the “Allow Custom” option to open specific ports, but ensure you block access to the Configuration utility. By default, the Configuration utility operates on TCP port 443. If you’ve customized the port, make sure to block access to the modified port.
Please note that blocking access via this method restricts all access to the Configuration Utility and iControl REST using the self IP address. F5 warns that this may also impact other services and potentially disrupt high-availability configurations.
Additionally, for BIG-IP versions 14.1.0 and later, an alternative mitigation method is available:
- Use the Script Provided by F5: F5 has provided a script as part of the mitigation process. This script involves modifying the configuration files for proxy_ajp_conf and tomcat_conf by adding or removing a secret.
You can find more details about the vulnerability and its mitigation methods in the F5 advisory.
F5 Reports Active Exploitation of CVE-2023-46747 in BIG-IP in Combination with CVE-2023-46748
F5’s recent advisory update reports active exploitation activity regarding CVE-2023-46748 and notes that threat actors initially use CVE-2023-46747 to exploit the vulnerability.
Shadowserver also reports there have been attempts to exploit CVE-2023-46747 in their honeypot sensors since a Nuclei template to detect the vulnerability was recently made available on GitHub.
The F5 advisory for CVE-2023-45748 notes its combination in exploit chains with CVE-2023-46747, resulting in the observation of certain Indicators of Compromise (IoC). If you review the /var/log/tomcat/catalina.out file, you may encounter entries such as:
{...}
java.sql.SQLException: Column not found: 0.
{...)
sh: no job control in this shell
sh-4.2$
sh-4.2$ exit. F5 points out that you might find different numbers replacing ‘0’ in the “Column not found: 0” line, and the ‘
How Can SOCRadar Help?
By utilizing the Attack Surface Management (ASM) module, you can actively monitor emerging vulnerabilities across your digital assets, receive timely threat alerts, and efficiently manage patching efforts to mitigate their potential impact.
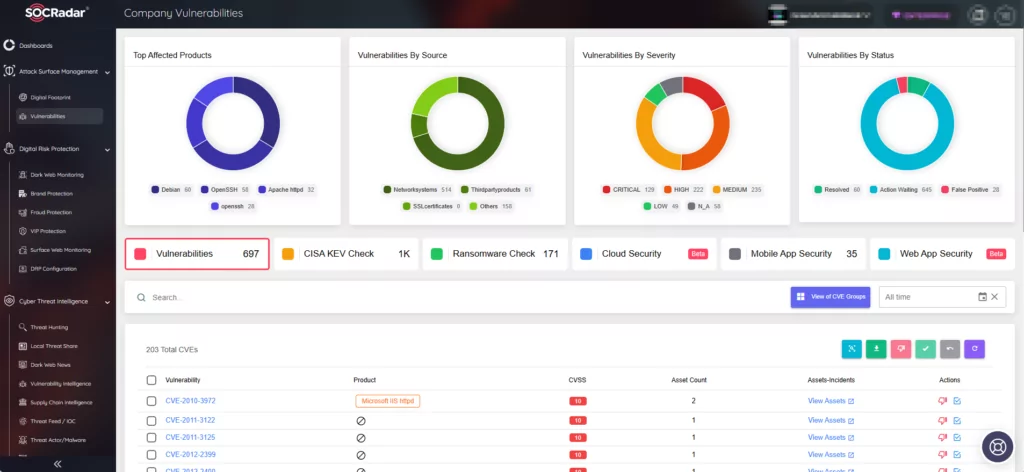
Access more details and updates on identified vulnerabilities with SOCRadar’s Vulnerability Intelligence.