
Cybersecurity Risks During 2024 Indian General Elections
General elections in India will be held from April 19 to June 1, 2024. In the context of election security in cyberspace, a couple of points carry particular significance over others.
The intersection of cyber security with state interests attracts many threat actors from a vast threat surface. In situations like these, simple hacking incidents driven by financial motives are considerably less significant compared to other cases, such as organized disinformation campaigns by rival states, spear-phishing attacks aimed at officials, attempts to manipulate the election results, and, of course, the new plague of our period, malicious use of deepfakes.
These cases are more significant than simple hacking incidents because of the political ramifications that both India and the world will face. Therefore, as a global actor, the safety and stability of India’s political environment are crucial points for both the region and the world.
Overview of the 2024 Indian General Elections
The election process in India differs significantly from that in other countries. The number of eligible voters, approximately 960 million individuals, surpasses the population of certain continents. Therefore, the elections in India take longer than other national elections. This time, it will take 44 days, from April 19, 2024, to June 1, 2024, to elect 543 members of the 18th Lok Sabha, the lower house of India’s bicameral Parliament.
As a nuclear power and the fifth-largest economy in the world as of 2024, securing cyberspace, protecting the electoral infrastructure, and maintaining digital hygiene during the elections is vital for the security and the future of India, the region, and the world.
Overview of the risks
The cybersecurity risks in Indian elections are multifaceted, and to correctly identify them, it is essential to categorize them into two distinct groups. We can divide the threats into problems stemming from domestic issues and threats arising from international factors.
When considering domestic issues, we identified vulnerabilities related to the electoral system, such as database leaks, political campaigns filled with fake content, and questions about the security of voting machines. Even though these machines are presented as standalone products without connection to the web, the discourse can be used for disinformation campaigns.
These vulnerabilities create lucrative opportunities for threat actors who seek to disrupt the democratic process of Indian elections.
Internationally, India’s geopolitical alignments expose the country to serious cyber threats, particularly from threat actors seeking to exploit the country’s vulnerabilities because of India’s international alliances or political tensions with its rivals. For example, the Israel-Hamas conflict and India’s friendly stance with Israel puts a target on its back. This support invites retaliatory cyber operations from hostile actors targeting private companies, critical infrastructure, government institutions, or political figures.
When analyzed, local and international sources point out the risks that may originate from deepfakes. And the amount of attention brought to this point shows that deepfakes are a more significant threat than cyberattacks or malicious attempts.
Political Risks for the Indian General Elections
Politically motivated cyber attacks and malicious attempts towards India’s elections can be analyzed under two categories.
One is related to India’s geopolitical position and strategic competition with regional powers. At the same time, the other revolves around the ideological and religious rivalry that arose from India’s support of Israel after October 7, 2023. The significance of the current events increases the severity of risks from the second category.
Geopolitical Problems of India and Their Reflections on Cyberspace
As a significant player on the global stage, India constantly competes with numerous other states. Adversaries utilize a variety of strategies to undermine India’s digital infrastructure. Whether using threat actors as proxies or deploying their teams, these rivals present tough challenges for India’s cybersecurity. Such tactics can be used to disrupt infrastructure or sow chaos through disinformation campaigns to gain strategic advantages as a result.
Besides state actors, India is also fighting against hacktivist groups that take action with different social motivations. India faces ongoing attacks by threat actors from South Asia, primarily motivated by religious ideologies, notably Islam.
India also has a history of geopolitical conflicts and competition with regional powers like Pakistan. This historical rivalry affects governments and individuals, fueling hatred towards India and leading to malicious activities. When this hate spills into cyberspace, it motivates threat actors to act on their nations’ behalf. You can see a Telegram message of a cyber attack from a Pakistan-based threat actor below.
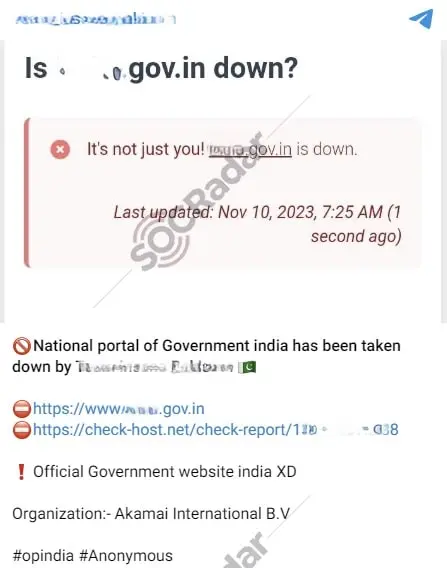
A threat actor monitored by SOCRadar announces their cyber attack on the National Portal of India
For over a month, this threat actor has orchestrated a series of DDoS attacks as part of the #OpIsrael and #OpIndia campaigns. On November 10, 2023, the india.gov.in governmental URL address fell victim to one such attack. The motivation behind these attacks appears to stem from political and religious tensions, particularly India’s support of Israel after October 7, and that leads us to the second category of cyber-attacks aimed at India.
Israel-Hamas Conflict
India and its support for Israel during the Israel-Hamas conflict have provoked many threat actors. Following the Israel-Hamas conflict, there has been a significant increase in the number of incidents, and the reasoning behind them is generally the same: India’s pro-Israel stance. Threat actors against Israel are showing a unified stance and trying to help each other attack other countries supporting Israel, with India being one of them.
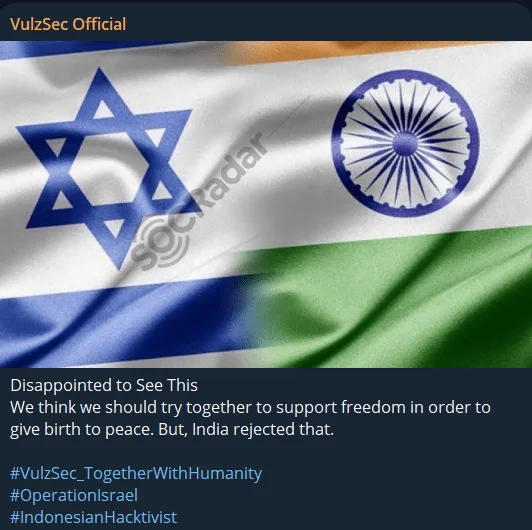
Announcement from a threat actor’s Telegram channel monitored by SOCRadar
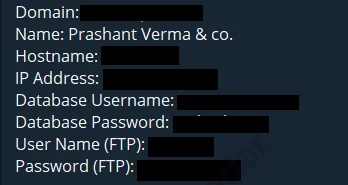
The threat actor released access data and credentials for multiple Indian websites, including some prominent ones. They leaked domain names, IP addresses, usernames, passwords, and FTP credentials
For more detailed information about the cyber front of the Israel-Hamas conflict, you can check SOCRadar’s report here.
Data breaches and voter information security
Another issue to be aware of is related to data leaks. Threat actors utilize every bit of their arsenal to obtain data from weak sources to profit from them. While the threat actors themselves may not be interested in the data they steal, political parties or rival states can utilize these sources, which can be bought on the dark web easily.
Data leaks and the complications they can create differ. From compromising voter privacy to enabling election manipulation and foreign interference, the effects are extensive. In terms of India’s elections, leaked personal information can help fraudulent voters or groups with malicious intent (like political parties or nation-states) muddy the waters by using the leaked data and deepfake-generated voices to create targeted disinformation campaigns.
The following leak, shared by a threat actor monitored by SOCRadar, reportedly originates from the Election Commission of India and allegedly comprises 7.6 million records, including names, addresses, phone numbers, gender, and birth dates.
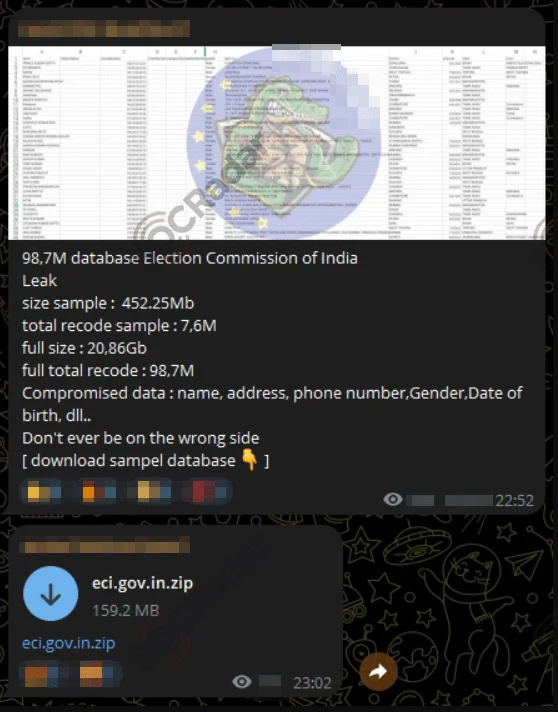
A Telegram channel monitored by SOCRadar. Claiming to have the database of Election Commission of India
Check SOCRadar’s Dark Web News module to hear the footsteps of threat actors from miles ahead.
Disinformation and social media manipulation
Disinformation and social media manipulation are significant concerns in India. According to the World Economic Forum’s 2024 Global Risk Report, India was ranked highest for the risk of misinformation and disinformation. In an era where disinformation causes detrimental effects to its citizens, India should be at the forefront of efforts to combat this threat.
In the context of India’s elections, the dissemination of disinformation poses a significant threat. Previously, it has led to social unrest in many locations around India. Besides the short-term risks, it can cause erosion of trust in institutions in the long term, which is another detrimental effect. Social media, in particular, acts as fertile ground for false information, enabling those behind disinformation campaigns to manipulate public opinion. During sensitive times like elections, social media platforms witness a surge in fake articles, images, and videos due to companies that provide this service.
Organizations find it hard to find out about fraudulent use of their names or domains. Threat actors can create very similar domains and accounts to imitate real brands. You can use SOCRadar’s Brand Protection module to get notified when hackers use your organization’s name.
SOCRadar’s Brand Protection module
The following message is obtained from a threat actor’s Telegram channel monitored by SOCRadar. The message is sent to the Telegram channel, claiming to have citizen data from India. While the leak itself is crucial and needs to be handled carefully, the message’s content is what we will pay attention to.
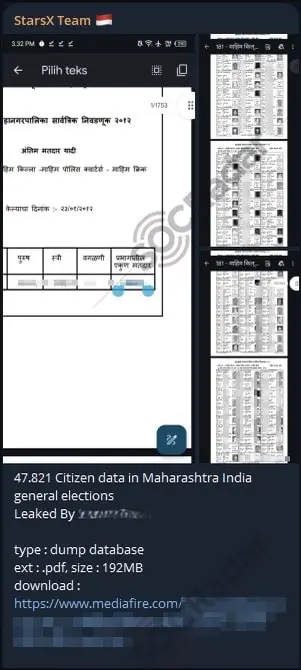
A Telegram channel monitored by SOCRadar. Shows an alleged data leak for Indian citizens
Since it contains images of paper materials with personal information and pictures on them, any actor aiming to disrupt the peaceful electoral process of India can use these materials to create a disinformation campaign. They could trick individuals into believing that the elections are rigged and that sensitive documents (which can be presented as ballots) have been shared with some parties before the elections, giving them an advantage.
It is important to take proactive steps to prevent such a disinformation campaign. While this is just one example, the dark web is full of threat actors trading personal information. You can use SOCRadar’s Threat Actors/Malware module to learn about threat actors’ activities and their plans.
Deepfakes
The use of deepfakes is probably the most problematic part of the Indian elections this year. Even though it can be analyzed under the disinformation title, the use of deepfakes and their impacts requires an additional analysis.
The technology allows even an average citizen to manipulate media like videos, voices, and images to make individuals, such as government officials, say things they haven’t. This will sow seeds of doubt and create uncertainty for the people who will vote. In an environment where every party aims to utilize this technology, the whole news landscape will be filled with fake content, making it impossible for authorities to fact-check and deliver correct information to voters.
According to this article from Aljazeera, an AI startup got an interesting offer for a political candidate. It turns out that a problematic video of the candidate was released, and the candidate’s political party wanted to generate deepfake content, spread it quicker than the initial problematic video, and blame the initial video as deepfake content.
Several sources point out that an industry is shaped in India solely for fake content production, and these companies also started using deepfakes. While there are ethical ways to use deepfakes for election campaigns, such as altering a candidate’s voice to send legitimate personalized messages, malicious use of this technology is more common, and the possibilities are vast. Altered videos or audio files to target political opponents, framing them as if they are committing fraud, sharing AI-generated adult content, and using candidates’ voices to send personalized and harassing messages to voters are some examples.
Another considerable development occurred on the OpenAI side with their new voice cloning tool, Voice Engine. Only a 15-second clip is enough for Voice Engine to clone someone’s voice. Even though OpenAI is not releasing it widely, the point this technology achieved shows how easy it is to create fake content with a potentially significant impact.
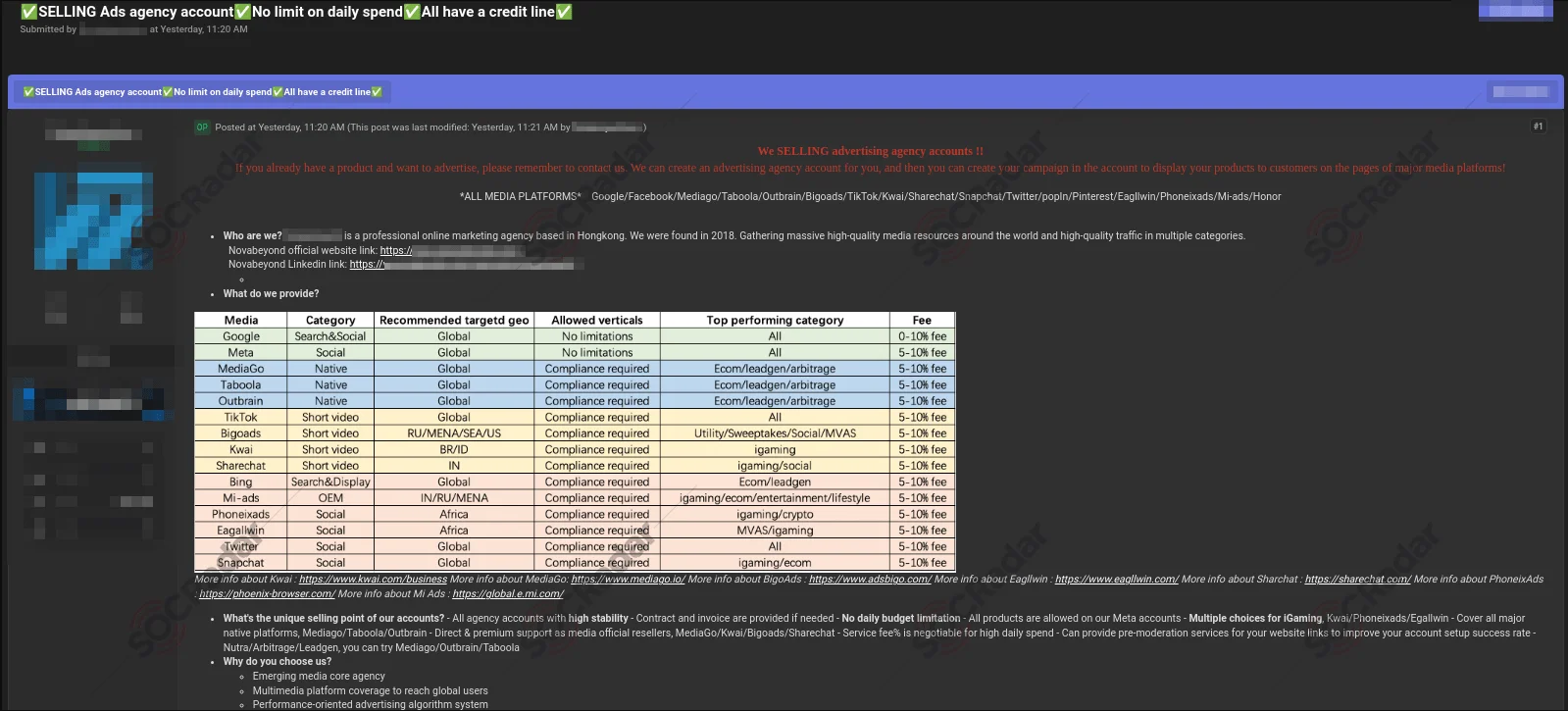
A threat actor selling advertising agency accounts for various social media platforms
This threat actor is trying to sell advertising agency accounts for various platforms on a hacker forum monitored by SOCRadar. Even though this threat actor is not targeting advertising agency accounts from India specifically, the existence of such a service should be kept in mind. These compromised accounts can be bought and used for many illicit activities. During the election period, fake news can be shared via compromised accounts and appear genuine.
To understand the threat landscape better and learn about the latest developments about your organization, you can benefit from SOCRadar’s Dark Web Monitoring module.
Ransomware Risks
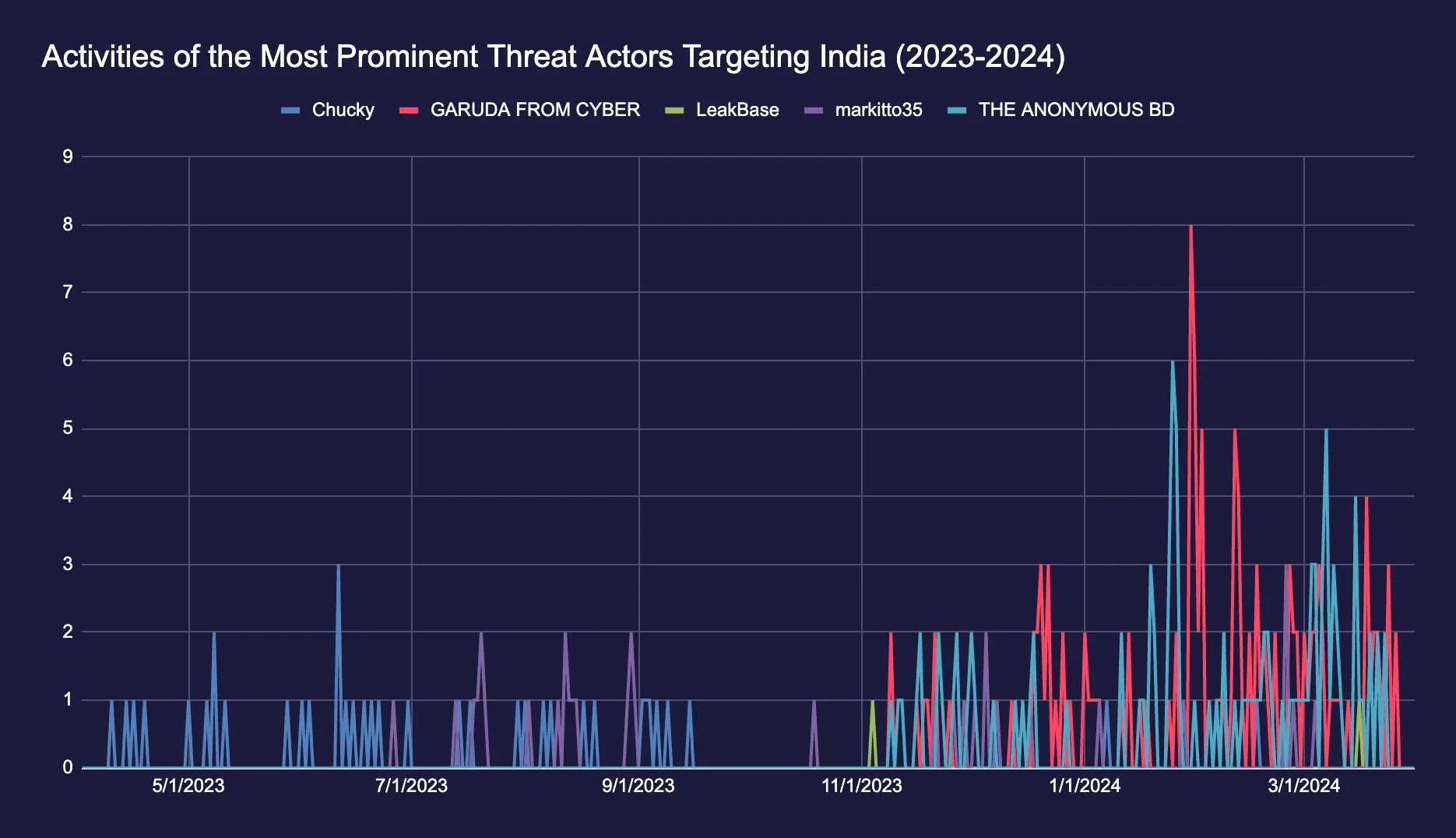
Threat actor activity in India grows as election dates are approaching
According to data from SOCRadar Extended Threat Intelligence platform, the threat actors in the graph are the most prominent hacker groups operating against India. From the graph, we can see the activities of “Chucky” decreased over time, and then they re-emerged as LeakBase recently. We can also see that the most prominent threat actors became more active after October 7, 2023, the starting date of the conflict between Israel and Hamas. As we got closer to the elections, their activity increased even more.
The following data was acquired from SOCRadar’s Extended Threat Intelligence platform. According to intelligence collected from the dark web, in recent years, threat actors aiming to obtain ransom from Indian institutions were mostly successful. This situation generates two threats:
- Threat actors can target Indian institutions more; therefore, we will see frequent data leaks.
- This frequent flow of data can make organizing disinformation campaigns easier.
- General trust in Indian institutions and authorities will decrease.
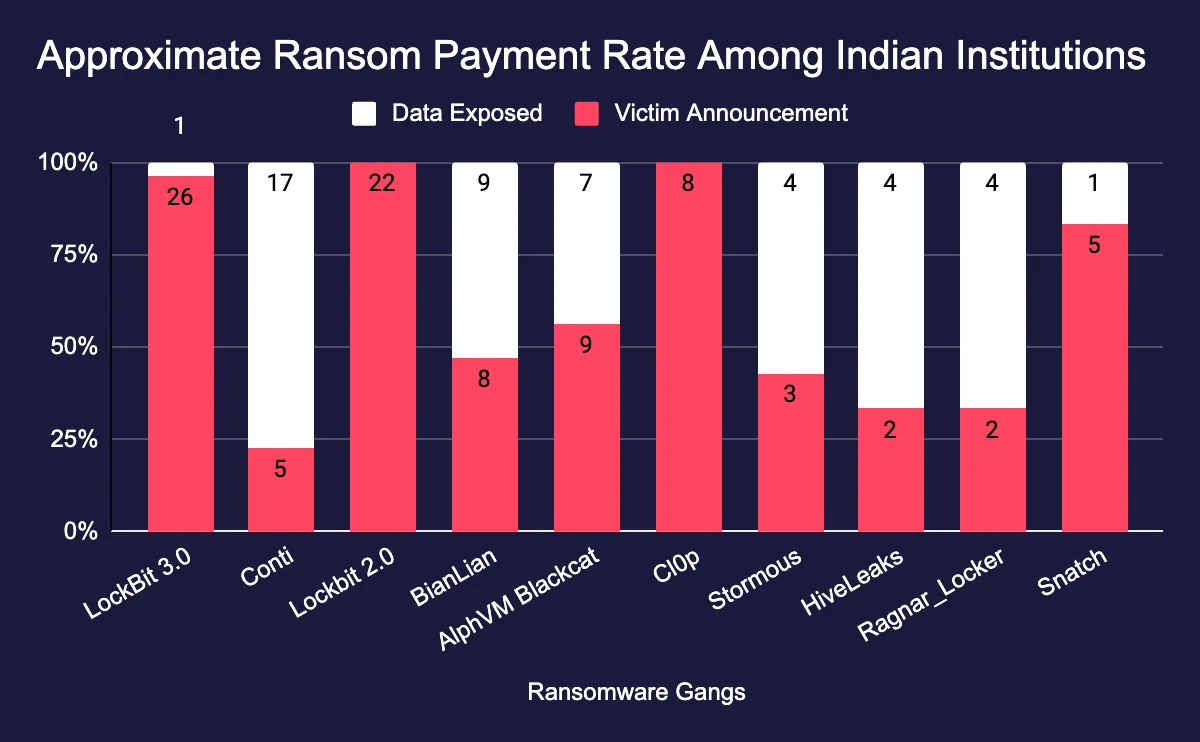
Victim announcements without data leaks are a strong indicator of paid ransom
After these ransomware gangs announced their attacks, they went silent and didn’t expose any victim data. This generally occurs when the victims can not fight against the gangs, accept their terms, and make the payment. This is not a definite indicator but a good approximation of actual cases.
For more information about your industry and the most prominent threat actors aiming to steal data from you, try SOCRadar’s Breach Datasets module.
Discover the compromised data swiftly with SOCRadar’s Breach Dataset module
Conclusion
To wrap up, the spread of fake news, disinformation, and the increasing use of deepfakes are pressing concerns for India’s upcoming 2024 general elections. Furthermore, the threat of cyber attacks, whether from rival states or politically driven actors, adds another layer of complexity to the electoral landscape.
This complex landscape will only create noise for you and make things complicated. To address these challenges correctly and protect your organization, you can get accurate intelligence from SOCRadar’s Extended Threat Intelligence Platform.




































