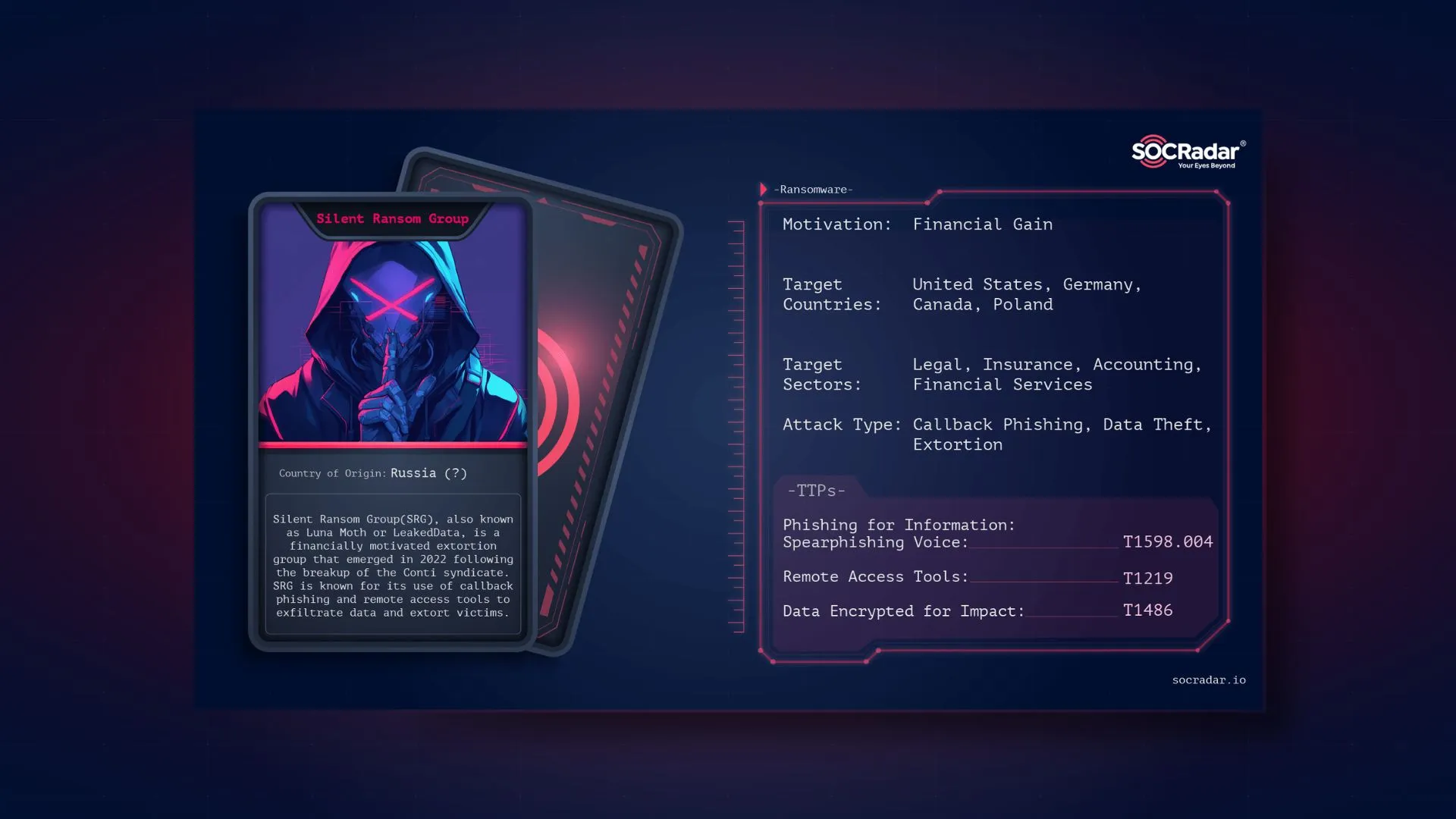
Dark Web Profile: APT40
APT40, also known as TEMP.Periscope, Leviathan, and many other aliases, is a Chinese cyber-espionage group attributed to the Chinese Ministry of State Security (MSS). Active since at least 2009, APT40 has been implicated in numerous high-profile cyber-espionage campaigns targeting a variety of sectors, particularly focusing on maritime, defense, aviation, and technology. The group’s activities are aligned with China’s strategic objectives, including the modernization of its military and expansion of its maritime influence.
Who is APT40?
APT40’s operations have been linked to the Hainan State Security Department (HSSD) of the MSS, a provincial arm of China’s primary civilian intelligence agency. This attribution is supported by multiple cybersecurity agencies and organizations, including the Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC). These organizations have collectively identified the group’s Tactics, Techniques, and Procedures (TTPs) as consistent with those used by state-sponsored Chinese actors.

Threat Actor Card for APT40
Indictment Against APT40 Cyber Actors
As stated in the CISA advisory: On July 19, 2021, the U.S. Department of Justice (DOJ) unsealed an indictment against four APT40 cyber actors, revealing their illicit Computer Network Exploitation (CNE) activities conducted through the front company Hainan Xiandun Technology Development Company (Hainan Xiandun). Wu Shurong, an employee of Hainan Xiandun, collaborated with and executed orders from intelligence officers Ding Xiaoyang, Zhu Yunmin, and Cheng Qingmin of the Hainan State Security Department (HSSD) of the PRC Ministry of State Security (MSS).

Wanted poster by the FBI (U.S. Department of Justice)
Wu’s CNE operations led to the theft of trade secrets, intellectual property, and other high-value information from companies and organizations in the United States and other countries, as well as from multiple foreign governments. These MSS-affiliated actors targeted victims across various industries, including academia, aerospace and aviation, biomedical, the defense industrial base, education, government, healthcare, manufacturing, maritime, research institutes, and transportation sectors such as rail and shipping.
How APT40 Attacks?
APT40 employs a diverse array of TTPs to infiltrate, maintain persistence, and exfiltrate data from targeted networks.
Initial Access
- Spear Phishing: APT40 frequently uses spear-phishing emails with malicious attachments or links to gain initial access to target systems. These emails are often tailored to the victim, using information gathered through reconnaissance to increase their credibility.
- Exploitation of Vulnerabilities: The group is known for quickly exploiting newly disclosed vulnerabilities in widely used software, such as web servers, content management systems, and network appliances. This rapid exploitation allows them to gain access before organizations can apply patches.
Modus Operandi
According to ACSC, APT40 has the ability to swiftly adapt and utilize Proof-of-Concept (PoC) exploits for new vulnerabilities, deploying them immediately against target networks with the relevant infrastructure. The group consistently conducts reconnaissance on networks of interest, including those within the countries of the authoring agencies, to identify opportunities for compromise. This continuous reconnaissance allows APT40 to pinpoint vulnerable, end-of-life, or unmaintained devices on these networks and quickly deploy exploits. APT40 has successfully exploited vulnerabilities dating back to 2017.
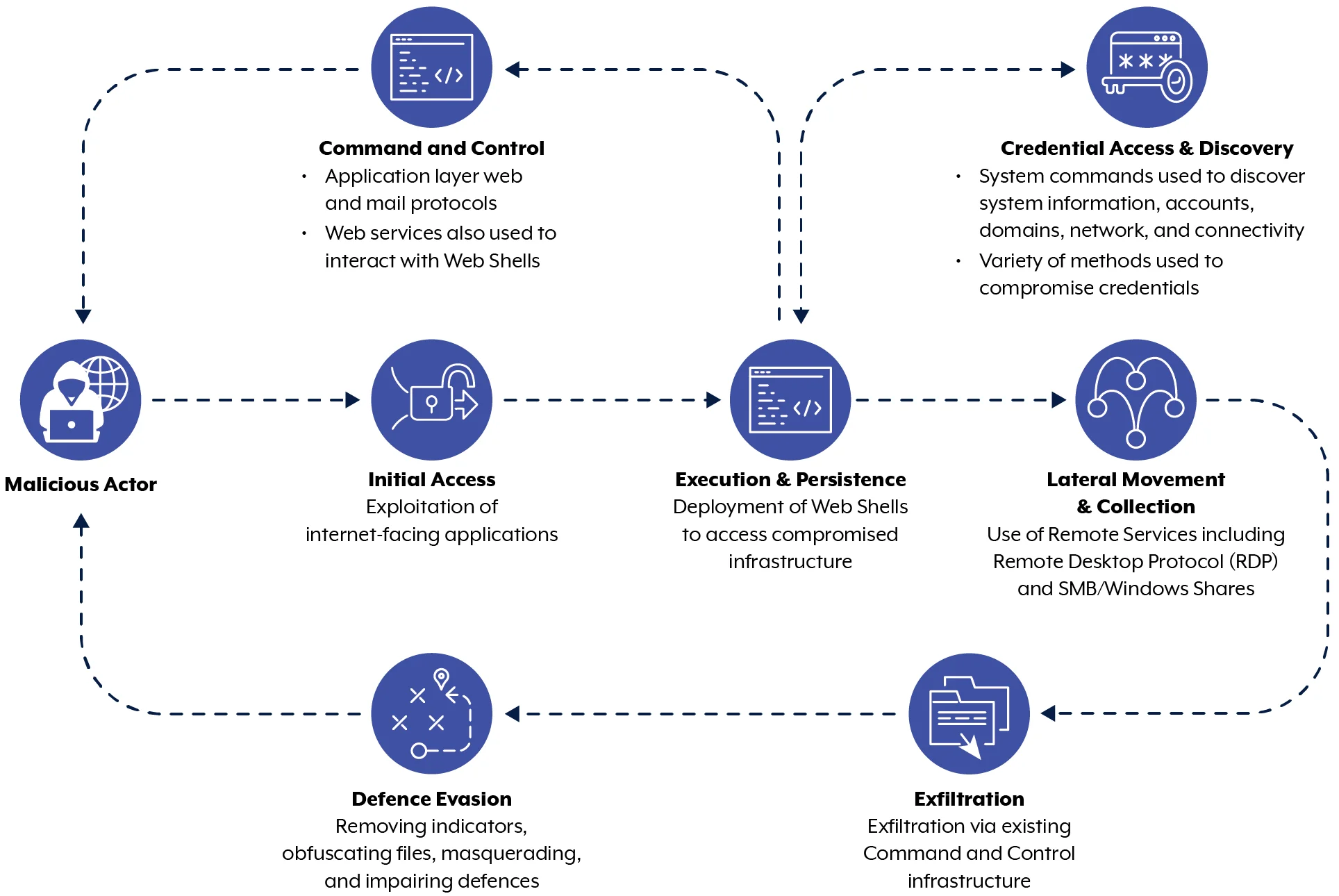
A flowchart of APT40’s modus operandi (ACSC)
Technical Details
Rapid Exploitation of New Vulnerabilities:
- Adaptation of PoCs: APT40 is adept at quickly transforming and utilizing Oroof-of-Concept (PoC) exploits for newly discovered vulnerabilities. As soon as a new vulnerability is publicly disclosed, the group can exploit it against target networks with the relevant infrastructure.
- Targeting Public-Facing Infrastructure: The group prioritizes exploiting public-facing infrastructure over techniques that require user interaction, such as phishing campaigns. This includes vulnerabilities in widely used software like Log4J (CVE 2021-44228), Atlassian Confluence (CVE-2021-26084), and Microsoft Exchange (CVE-2021-31207; CVE-2021-34523; CVE-2021-34473).
- Persistent Exploitation: APT40 continues to find success in exploiting vulnerabilities from as early as 2017, demonstrating a broad and sustained capability to exploit both new and older vulnerabilities.
Continuous Reconnaissance:
- Network Scanning: The group regularly conducts reconnaissance on networks of interest, including those within the countries of the authoring agencies. This continuous scanning enables APT40 to identify vulnerable, end-of-life, or unmaintained devices that can be targeted for exploitation.
- Credential Harvesting: APT40 places a high priority on obtaining valid credentials to enable a range of follow-on activities and to maintain access within compromised environments.
Persistence Mechanisms:
- Web Shells: The group frequently uses web shells (T1505.003) for persistence, especially early in the intrusion lifecycle. These tools allow APT40 to maintain access to compromised systems even if initial exploitation vectors are closed.
- Establishing Long-Term Access: After gaining initial access, APT40 focuses on establishing and maintaining persistence to ensure continued access to the victim’s environment. This early-stage persistence is a hallmark of their operations and can be observed in all intrusions regardless of the extent of further compromise.
Use of Compromised Infrastructure:
- SOHO Devices: APT40 has evolved its tradecraft to include the use of compromised small-office/home-office (SOHO) devices as operational infrastructure and last-hop redirectors (T1584.008). Many of these devices are end-of-life or unpatched, making them easy targets for exploitation. Once compromised, these devices allow APT40 to launch attacks that blend in with legitimate traffic, complicating detection and mitigation efforts.
- Global Trend: This technique of using SOHO devices is not unique to APT40 and is regularly employed by other PRC state-sponsored actors worldwide. It is considered a shared threat among various state-sponsored groups.
Command and Control (C2) Infrastructure:
- Dynamic C2 Tactics: APT40 has previously used compromised websites as Command and Control (C2) hosts for its operations, recently they have shifted towards using compromised devices as C2 infrastructure.
- Leased Infrastructure: While the group occasionally uses procured or leased infrastructure for victim-facing C2 operations, this method appears to be in relative decline.
Notable Campaigns
As we mentioned above, APT40 has a well-documented history. As FireEye highlighted back in 2019, APT40 was targeting the maritime industry, reflecting China’s strategic interest in naval dominance and maritime trade routes. The group has targeted a variety of organizations, including research institutions, universities, and private companies involved in naval technology and maritime research. These attacks often aim to exfiltrate sensitive information that can be used to enhance China’s naval capabilities and inform its strategic decisions in disputed maritime regions, such as the South China Sea.
Key Incidents
- Naval Research and Development: In multiple instances, APT40 has targeted universities and research institutions involved in naval research and development, stealing sensitive research data and proprietary technologies.
- Shipping Companies: The group has also targeted global shipping companies, seeking to gather intelligence on logistics, shipping routes, and cargo manifests.
APT40 has been involved in extensive cyber-espionage campaigns against the defense and aerospace sectors. The group’s operations are designed to gather intelligence on military technology, aviation systems, and satellite communications, providing the Chinese military with critical insights and technological advantages.
Key Incidents
- Military Technology Theft: APT40 has targeted defense contractors and technology firms involved in the development of military hardware and software, stealing blueprints, technical specifications, and other sensitive information.
- Aviation Industry Espionage: The group has infiltrated aerospace companies to gather data on aircraft designs, satellite systems, and communication technologies, aiming to advance China’s own aerospace capabilities.
The activities of APT40 pose significant threats to national security, economic stability, and technological advancement in the countries they target. The exfiltration of sensitive data can undermine competitive advantages, erode trust in public and private institutions, and lead to substantial financial losses. Additionally, the group’s focus on critical infrastructure and strategic sectors means that their activities have far-reaching implications for global security and geopolitical stability.
How to Detect and Mitigate?
Organizations can take several steps to detect and mitigate the threat posed by APT40:
- Regularly Updating Software: Ensure that all software and systems are kept up-to-date with the latest security patches to prevent exploitation of known vulnerabilities. Install vendor-provided and verified patches for critical vulnerabilities promptly, especially for internet-connected servers and software handling internet data (e.g., web browsers, browser plugins, and document readers). Implement proper migrating steps or compensating controls for vulnerabilities that cannot be patched immediately. Maintain up-to-date antivirus signatures and engines and audit configuration and patch management programs routinely.
- Advanced Email Filtering: Implement advanced email filtering solutions to detect and block spear-phishing attempts before they reach end-users. This reduces the likelihood of successful phishing attacks, which are common entry points for APT40 and similar threat actors.
- Network Segmentation: Segment networks to limit lateral movement in the event of a breach, isolating critical systems and sensitive data from general access. This practice, along with robust network defense-in-depth strategies, helps in mitigating threats and reducing the risk of widespread compromise.
- Employee Training: Conduct regular cybersecurity training for employees to raise awareness about phishing, social engineering, and other common attack vectors. Emphasize the importance of safeguarding credentials and recognizing suspicious activities.
- Behavioral Analytics: Utilize behavioral analytics to monitor for anomalies that may indicate malicious activity, such as unusual login patterns or data access behaviors. Develop and monitor network and system baselines to allow for the identification of anomalous activity and audit logs for suspicious behavior.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to suspicious activities on endpoints, providing visibility into potential intrusions and enabling rapid response. Monitor server disk use and audit for significant changes to detect potential compromises.
- Patch and Vulnerability Management: Implement a rigorous patch and vulnerability management program. Ensure timely installation of patches, prioritize critical vulnerabilities, and use compensating controls for those that cannot be patched immediately. Routinely audit and update your configuration and patch management programs to effectively track and mitigate emerging threats.
- Protect Credentials: Strengthen credential requirements by regularly changing passwords, implementing multi-factor authentication, and avoiding password reuse across multiple accounts. Audit remote authentications and correlate credentials used internally with those on external-facing systems. Enforce the principle of least privilege and log system administrator commands.
- Network Hygiene and Monitoring: Actively scan and monitor internet-accessible applications for unauthorized access and anomalous activities. Log Domain Name Service (DNS) queries and consider blocking all outbound DNS requests not originating from approved DNS servers. Monitor DNS queries for Command and Control (C2) traffic. Use allowlist or baseline comparison to monitor Windows event logs and network traffic for unusual activities, such as mapping privileged administrative shares.
- Use Threat-Reputation Services: Leverage multi-sourced threat-reputation services for files, DNS, URLs, IP addresses, and email addresses to identify potential threats. Ensure network device management interfaces are secured with strong passwords and encryption, and turn off unused interfaces when possible.
- Segment and Protect Critical Information: When feasible, segment critical information on air-gapped systems and apply strict access control measures for sensitive data to further safeguard against unauthorized access.
By implementing these measures, organizations can enhance their defenses against APT40 and other sophisticated cyber threats, reducing the risk of a successful attack and mitigating potential damage.
How Can SOCRadar Help?
To counter the sophisticated cyber espionage tactics employed by the APT40 group, organizations are advised to adopt a proactive cybersecurity posture.
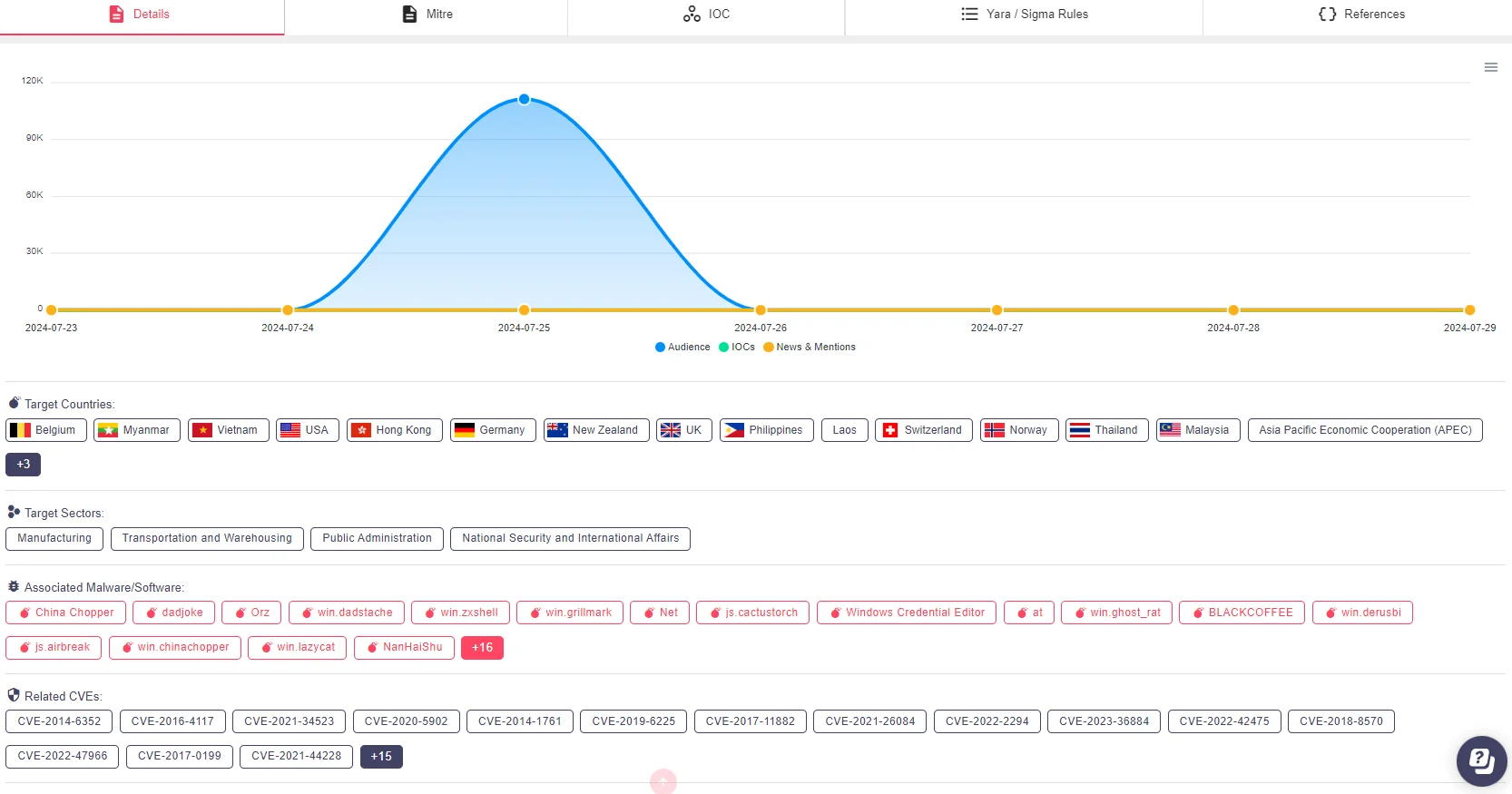
Threat actor page for APT40 in SOCRadar’s Platform, Threat Actor Intelligence
SOCRadar’s Extended Threat Intelligence represents a significant advancement over traditional threat intelligence platforms, incorporating advanced features that greatly enhance threat detection and visibility. This solution leverages powerful machine learning technologies to analyze vast amounts of threat data collected from a variety of open sources, social media platforms, and the dark web. By employing this comprehensive approach, SOCRadar’s XTI enables security teams to quickly identify and assess threats, providing them with proactive security measures.
Conclusion
APT40 remains a sophisticated and persistent threat actor, leveraging a wide range of techniques to achieve its espionage goals. Organizations, particularly those in targeted sectors such as maritime, defense, and aerospace, must stay vigilant and proactive in their cybersecurity efforts. By implementing robust security measures and staying informed about the latest threat intelligence, organizations can better protect themselves against the persistent and evolving threat posed by APT40.
What are the TTPs of APT40?
Below are the TTPs provided by the CISA for APT40:
| Tactic | Activities and Techniques |
| Reconnaissance [TA0043] | Gathered victim identity information [T1589] |
| Resource Development [TA0042] | Collected compromised credentials [T1589.001] |
| Acquired infrastructure [T1583] to establish domains that impersonate legitimate entities | |
| Established new [T1585.002] and compromised existing email and social media accounts | |
| Initial Access [TA0001] | External remote services (e.g., VPN services) [T1133] |
| Spearphishing emails with malicious attachments [T1566.001] and links [T1566.002] | |
| Drive-by compromises [T1189] and exploitation of public-facing applications [T1190] | |
| Access to valid [T1078] and compromised administrative [T1078.001] accounts | |
| Execution [TA0002] | Command and scripting interpreters [T1059] such as PowerShell [T1059.001] |
| Exploitation of software vulnerabilities in client applications to execute code [T1203] | |
| User execution [T1204] of malicious files [T1204.002] and links attached to spearphishing emails | |
| Persistence [TA0003] | Utilized tool frameworks and malware for persistence |
| Privilege Escalation [TA0004] | Escalated privileges on victim networks |
| Credential Access [TA0006] | Accessed and harvested credentials |
| Discovery [TA0007] | Mapped networks and conducted internal spear phishing attacks [T1534] |
| Lateral Movement [TA0008] | Moved laterally on victim networks using various tools and malware |
| – BADFLICK/Greencrash | |
| – China Chopper [S0020] | |
| – Cobalt Strike [S0154] | |
| – Derusbi/PHOTO [S0021] | |
| – gh0st RAT [S0032] | |
| – GreenRAT | |
| – jjdoor/Transporter | |
| – jumpkick | |
| – Murkytop (mt.exe) [S0233] | |
| – NanHaiShu [S0228] | |
| – Orz/AirBreak [S0229] | |
| – PowerShell Empire [S0363] | |
| – PowerSploit [S0194] | |
| – Web Shell [TA1505.003] | |
| Defense Evasion [TA0005] | Used steganography [T1027.003] to hide stolen data |
| Employed protocol impersonation [T1001.003] using API keys for Dropbox accounts | |
| Utilized protocol tunneling [T1572] and multi-hop proxies [T1090.003], including Tor [S0183] | |
| Used domain typosquatting for C2 infrastructure [T1583.001] | |
| Command and Control [TA0011] | Established C2 channels and used typosquatting domains |
| Collection [TA0009] | Archived [T1560], encrypted [T1532], and staged collected data locally [T1074.001] and remotely [T1074.002] |
| Exfiltration [TA0010] | Exfiltrated data over C2 channel [T1041] |
For more information, analysis, and Indicators of Compromise (IoCs) related to APT40, refer to resources from CISA and ACSC. Additionally, you can review our China & Russia Cybercrime report and access the SOCRadar Platform, which contains thousands of IoCs for APT40 and other related APT groups.