
Dark Web Profile: OilRig (APT34)
OilRig, also known as APT34, is a state-sponsored Advanced Persistent Threat (APT) group with strong ties to Iranian intelligence. Known for its sophisticated cyber-espionage campaigns, OilRig primarily targets government, energy, financial, and telecommunications sectors across the Middle East and beyond. Leveraging advanced spear-phishing techniques and custom malware, the group has cemented its reputation as a persistent and highly adaptive threat actor in the global cyber landscape.
Who is OilRig?
OilRig Initially recognized for targeting organizations in Saudi Arabia, the group has since broadened its operations, with a primary focus on the Middle East. OilRig is widely considered to be linked to Iranian state interests, primarily conducting intelligence operations to further Iran’s geopolitical objectives. The group is also known by several aliases, including APT34, Helix Kitten, and Earth Simnavaz.
OilRig, also known as APT34, is a sophisticated cyber-espionage group widely attributed to Iranian state-sponsored activities. Active since at least 2016, the group has consistently targeted organizations primarily in the Middle East, focusing on sectors such as government, telecommunications, energy, and finance. Their operations, however, are not geographically restricted, with confirmed attacks extending to Europe, North America, and parts of Asia.

Threat Actor card for OilRig
Renowned for their stealth and persistence, OilRig employs a combination of custom-built malware, open-source tools, and advanced spear-phishing campaigns to compromise networks. The group is also adept at leveraging stolen credentials to infiltrate systems and gain prolonged access. Reports indicate OilRig uses a variety of sophisticated techniques, including DNS tunneling and web shell deployment, to exfiltrate sensitive information without detection.
This group’s modus operandi often involves strategic targeting to align with Iran’s geopolitical interests, such as gathering intelligence or undermining adversaries. Over the years, OilRig has demonstrated adaptability, frequently updating its arsenal with new tools and tactics, making it one of the most prominent APTs associated with Iranian cyber operations.
Whom Do They Target?
OilRig primarily focuses its cyber-espionage efforts on organizations that align with Iran’s geopolitical and economic interests. Their primary targets are in the Middle East, with a particular emphasis on sectors critical to national security and infrastructure, such as:
- Government Agencies: Including defense ministries, foreign affairs departments, and intelligence entities, to gather strategic and sensitive data.
- Energy and Oil & Gas Companies: Reflecting Iran’s interest in gaining competitive insights and monitoring global energy developments.
- Telecommunications Providers: To intercept communications, compromise infrastructure, and gain access to broader networks.
- Financial Institutions: For intelligence on economic strategies, sanctions circumvention, and sometimes monetary theft.
While the Middle East remains their core area of operation, OilRig has extended its activities to regions like Europe, North America, and Asia. Their secondary targets often include universities, research institutions, and think tanks that work on technology, cybersecurity, or political issues relevant to Iran’s interests.
OilRig’s strategic targeting approach often involves high-profile and well-resourced entities, with a preference for organizations that can provide long-term intelligence value or advance their sponsor’s political goals. This targeting methodology underscores the group’s state-sponsored nature and highlights its alignment with Iran’s global ambitions.
How Do They Operate?
OilRig follows a typical cyber kill chain model to execute its operations, leveraging a blend of tools, techniques, and strategies to gain access, maintain persistence, and carry out espionage activities. Their tactics are highly methodical, progressing from initial access to exfiltration and, in some cases, destruction. Here’s a breakdown based on software and TTPs by MITRE of how OilRig typically operates using the kill chain framework:
Reconnaissance:
OilRig begins its campaigns with extensive reconnaissance to identify vulnerable systems, network configurations, and potential entry points. During this phase, they gather information using tools like Netstat for system network discovery and Systeminfo for identifying system configurations. DNS and web protocols are also commonly used for passive network mapping.
Weaponization:
After gaining a detailed understanding of the target environment, OilRig creates and deploys weaponized payloads tailored to the specific environment. This includes the use of custom tools like BondUpdater to initiate Command and Scripting Interpreter execution, often through PowerShell or Windows Command Shell. They rely on domain generation algorithms to obscure command-and-control communications.
Delivery:
To deliver their payloads, OilRig commonly uses social engineering tactics, spear-phishing emails, and tool transfers using FTP for lateral movement and ingress tool transfers. These tools help deliver initial access while also facilitating the subsequent phases of the attack.
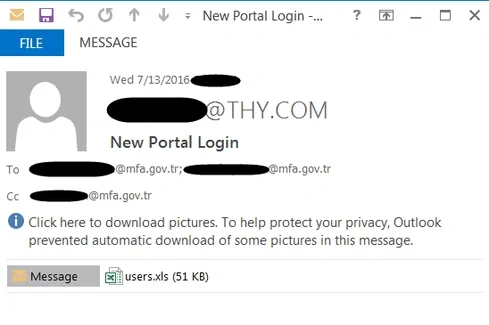
Phishing is both a common delivery and initial access point, a phishing e-mail to Turkish Airlines by OilRig in 2017 (DarkReading)
Exploitation:
Exploitation typically involves leveraging known vulnerabilities in software, systems, or configurations. Tools like Mimikatz are used for credential dumping and privilege escalation, allowing attackers to gain administrative access and execute further malicious activities. They use PowerShell or Windows Command Shell for exploitation through scripted commands, including credential harvesting.
Installation:
Once initial access is achieved, OilRig installs additional tools for persistence. This includes PowerShell scripts to establish scheduled tasks and registry modifications for autostart execution. Tools like Helminth facilitate this persistence, along with keylogging and remote access mechanisms through tools like PSExec to spread throughout the network.
Command and Control (C2):
OilRig uses DNS tunneling, encrypted channels, and fallback methods to communicate with compromised systems while evading detection. They rely on Command and Scripting Interpreters, such as PowerShell and Windows Command Shell, to execute remote commands and maintain control over infected hosts.
Actions on Objectives:
The final stage of the operation typically involves stealing sensitive data, escalating privileges, and maintaining long-term access. OilRig exfiltrates valuable information using tools like LaZagne and ISMInjector for credential harvesting. In some instances, they execute destructive operations, as evidenced by their involvement in the ZeroCleare attack, where they performed disk wiping and other forms of data destruction. To ensure the attack’s success, they use encrypted channels and fallback mechanisms for data exfiltration, often through web protocols or C2 channels.
By following this structured attack methodology, OilRig is able to carry out sophisticated cyber espionage campaigns, maintaining stealth while achieving long-term access and targeting critical data for theft or destruction. The group’s wide arsenal of tools and techniques ensures they can adapt to changing environments and security measures, making them a persistent and dangerous threat to their targets.
How to Defend Against OilRig and Iranian APT Threats?
Mitigating the threats posed by OilRig requires a multi-faceted approach that incorporates proactive defense strategies, robust security measures, and continuous monitoring. Below are recommended steps to protect against OilRig’s advanced tactics:
1. Strengthen Email and Communication Security
- Use advanced email filtering to detect and block phishing attempts.
- Train employees to recognize phishing emails and social engineering tactics.
- Implement DMARC, SPF, and DKIM protocols to prevent email spoofing.
2. Regularly Patch and Update Systems
- Ensure timely updates of software and operating systems to close vulnerabilities.
- Pay special attention to public-facing applications, such as VPNs and email servers.
3. Enforce Strong Access Controls
- Use Multi-Factor Authentication (MFA) for all critical accounts.
- Limit administrative privileges by following the Principle of Least Privilege (PoLP).
- Monitor and secure remote access through encrypted VPNs and strong authentication.
4. Monitor Network and Endpoint Activity
- Deploy Endpoint Detection and Response (EDR) tools to catch malware and unusual behavior.
- Analyze network traffic for signs of data exfiltration, lateral movement, or Command-and-Control (C2) activity.
- Set up Intrusion Detection and Prevention Systems (IDPS) with updated threat intelligence feeds.
5. Secure Supply Chain Operations
- Conduct thorough security audits of third-party vendors and partners.
- Require vendors to adhere to strict cybersecurity policies and industry standards.
6. Segment and Harden Networks
- Divide networks into secure segments to minimize lateral movement opportunities.
- Disable unnecessary ports and services to reduce attack surfaces.
- Implement network access controls to detect and block unauthorized devices.
7. Conduct Proactive Threat Hunting
- Regularly search for Indicators of Compromise (IoCs) and TTPs associated with OilRig.
- Leverage threat intelligence platforms to stay informed about evolving threats.
8. Prepare and Test Incident Response Plans
- Develop and regularly update an incident response plan tailored to APT scenarios.
- Maintain offline, encrypted backups of critical data and systems.
- Establish protocols for rapid detection, containment, and recovery during an incident.
By adopting these measures, organizations can reduce their exposure to OilRig and other Iranian APT threats, ensuring robust defense against espionage and sabotage campaigns.
How Can SOCRadar Help?
How Can SOCRadar Help?
SOCRadar offers a comprehensive platform to enhance your organization’s threat intelligence and security posture. Here’s how SOCRadar can assist in countering threat actors like OilRig:
- Extended Threat Intelligence
SOCRadar provides real-time threat intelligence, leveraging vast data sources to monitor emerging threats, TTPs, and indicators of compromise (IOCs) associated with OilRig and other adversaries. - Advanced Dark Web Monitoring
Stay ahead of OilRig’s activities by detecting potential data leaks, breached credentials, or threat actor communications on dark web forums and marketplaces. - Vulnerability Intelligence
Identify and remediate vulnerabilities that OilRig might exploit, including CVEs and security gaps in your systems. SOCRadar’s vulnerability intelligence integrates seamlessly with your existing security tools for streamlined action. - Threat Actor Intelligence
Access detailed profiles of OilRig and other advanced threat actors, including their motivation, TTPs, target sectors, and countries, enabling proactive defense strategies.
SOCRadar’s CTI Module, Operational Intelligence > Threat Actor Intelligence Tab
- Attack Surface Management (ASM)
Monitor your organization’s digital footprint to detect exposed assets or misconfigurations that could be exploited by threat actors like OilRig.
By integrating SOCRadar into your security strategy, organizations can gain the visibility, context, and tools necessary to thwart sophisticated adversaries like OilRig.
What are OilRig’s TTPs?
Techniques table provided by MITRE;
| ID | Name | Use |
| T1087.001 | Account Discovery: Local Account | The APT group has run net user, net user /domain, net group “domain admins” /domain, and net group “Exchange Trusted Subsystem” /domain to get account listings on a victim. |
| T1087.002 | Account Discovery: Domain Account | The APT group has run net user, net user /domain, net group “domain admins” /domain, and net group “Exchange Trusted Subsystem” /domain to get account listings on a victim. |
| T1071.001 | Application Layer Protocol: Web Protocols | Has used HTTP for C2. |
| T1071.004 | Application Layer Protocol: DNS | Has used DNS for C2, including the publicly available requestbin.net tunneling service. |
| T1119 | Automated Collection | Has used automated collection. |
| T1110 | Brute Force | Has used brute force techniques to obtain credentials. |
| T1059 | Command and Scripting Interpreter | Has used various types of scripting for execution. |
| T1059.001 | PowerShell | Has used PowerShell scripts for execution, including using a macro to run a PowerShell command to decode file contents. |
| T1059.003 | Windows Command Shell | Has used macros to deliver malware such as QUADAGENT and OopsIE and has used batch scripts. |
| T1059.005 | Visual Basic | Has used VBScript macros for execution on compromised hosts. |
| T1555 | Credentials from Password Stores | Has used credential dumping tools such as LaZagne to steal credentials to accounts logged into the compromised system and to Outlook Web Access. |
| T1555.003 | Credentials from Web Browsers | Has used LaZagne and PICKPOCKET to dump passwords from web browsers. |
| T1555.004 | Windows Credential Manager | Has used VALUEVAULT to steal credentials from the Windows Credential Manager. |
| T1140 | Deobfuscate/Decode Files or Information | Has used PowerShell commands and certutil to decode base64-encoded files. |
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | Has used the Plink utility and other tools to create tunnels to C2 servers. |
| T1048.003 | Exfiltration Over Alternative Protocol | Has exfiltrated data over FTP separately from its primary C2 channel over DNS. |
| T1133 | External Remote Services | Has used remote services such as VPN, Citrix, or OWA to persist in an environment. |
| T1008 | Fallback Channels | OilRig malware ISMAgent falls back to its DNS tunneling mechanism if unable to reach the C2 server over HTTP. |
| T1070.004 | Indicator Removal: File Deletion | Has deleted files associated with their payload after execution. |
| T1105 | Ingress Tool Transfer | OilRig can download remote files onto victims. |
| T1056.001 | Input Capture: Keylogging | Has used keylogging tools called KEYPUNCH and LONGWATCH. |
| T1036 | Masquerading | Has used .doc file extensions to mask malicious executables. |
| T1046 | Network Service Discovery | Has used SoftPerfect Network Scanner and a custom tool called GOLDIRONY for network scanning. |
| T1027.005 | Obfuscated Files or Information | Has tested malware to evade AV detection and used base64 encoding in malware. |
| T1137.004 | Office Application Startup: Outlook Home Page | Has abused the Outlook Home Page feature for persistence and used CVE-2017-11774 to bypass patches. |
| T1003.001 | OS Credential Dumping: LSASS Memory | Has used Mimikatz to steal credentials from LSASS memory. |
| T1003.004 | OS Credential Dumping: LSA Secrets | Has used LaZagne to steal credentials stored in LSA Secrets. |
| T1003.005 | OS Credential Dumping: Cached Domain Credentials | Has used LaZagne to steal cached domain credentials. |
| T1201 | Password Policy Discovery | Has used net accounts /domain to find the domain’s password policy. |
| T1120 | Peripheral Device Discovery | Has used tools to identify if a mouse is connected to a targeted system. |
| T1069.001 | Permission Groups Discovery: Local Groups | Has used net localgroup administrators to identify local administrators. |
| T1069.002 | Permission Groups Discovery: Domain Groups | Has used net group /domain and similar commands to find domain group permissions. |
| T1566.001 | Phishing: Spearphishing Attachment | Has sent spearphishing emails with malicious attachments using spoofed email accounts. |
| T1566.002 | Phishing: Spearphishing Link | Has sent spearphishing emails with malicious links. |
| T1566.003 | Phishing: Spearphishing via Service | Has used LinkedIn to send spearphishing links. |
| T1057 | Process Discovery | Has run tasklist on victim machines. |
| T1572 | Protocol Tunneling | Has used the Plink utility and other tools to create tunnels to C2 servers. |
In Summary
OilRig, also known as APT34, is a sophisticated and highly targeted threat actor primarily focused on cyber espionage campaigns, often linked to Iranian interests. Operating across various stages of the cyber kill chain, from initial reconnaissance to the exfiltration of sensitive data, their operations are marked by careful planning and the use of advanced tactics and tools.
Their attacks often target critical infrastructure, government agencies, and corporations, with a particular focus on industries such as energy and finance. OilRig’s ability to adapt to evolving environments and employ sophisticated evasion methods, including DNS tunneling, encrypted communications, and fallback channels, allows them to carry out long-term campaigns with minimal detection.
To sum up, OilRig’s operations reflect a highly methodical and adaptable approach, underpinned by their extensive toolset and expertise in exploiting system vulnerabilities. These factors, combined with their persistence and ability to execute attacks across multiple stages, make OilRig a formidable threat in the cyber landscape.





































