Dark Web Profile: Patchwork APT
The Patchwork APT group, identified in December 2015 but probably active since 2009, is a cyber espionage entity suspected to be based in India. It targets a variety of high-profile entities, including government, defense, and diplomatic organizations, primarily in South and Southeast Asia, but has also expanded its operations to other regions. Known for utilizing spear phishing and watering hole attacks, Patchwork employs a range of custom tools and techniques for espionage, making it a significant threat in the cyber threat landscape.

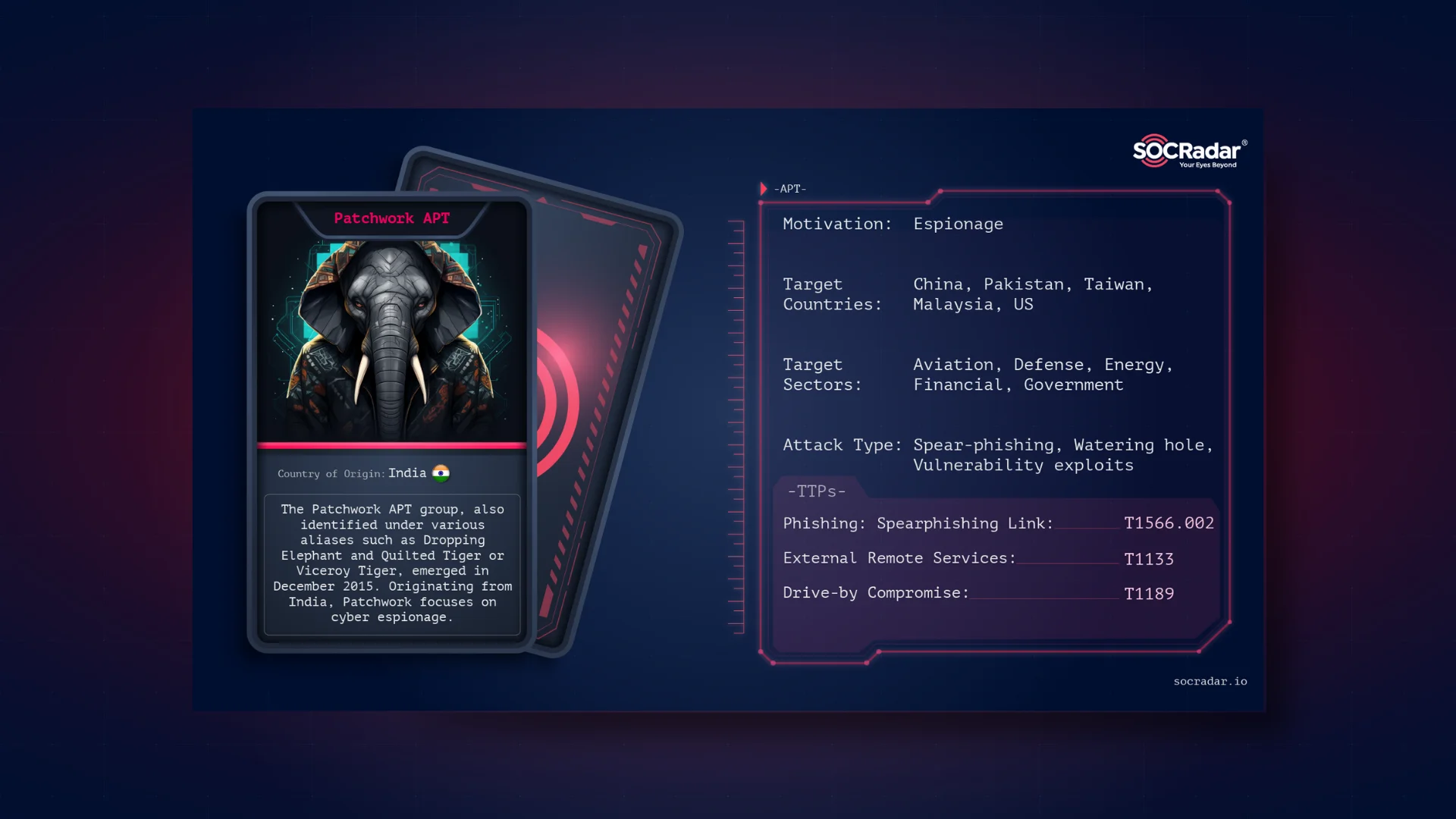
Threat Actor Card, Patchwork APT
Who is Patchwork APT
The Patchwork APT group, also identified under various aliases such as Dropping Elephant and Quilted Tiger or Viceroy Tiger, emerged in December 2015. Originating from India, Patchwork focuses on cyber espionage, targeting diplomatic and economic sectors with ties to China. Utilizing a blend of spear phishing and watering hole attacks, this group demonstrates a keen interest in intelligence gathering from multiple high-profile international targets. Their sophisticated cyber operations underscore the evolving landscape of global cyber threats and the necessity for vigilant cybersecurity defenses.

Image depicting Patchwork APT, created with Dall-E powered Bing AI Image Creation
Since its first detection in 2015, the Patchwork APT group has evolved from using rudimentary tactics to employing sophisticated cyber espionage strategies. Initially focusing on targets in South and Southeast Asia, the group expanded its operations globally, targeting entities in Europe and North America. Patchwork’s modus operandi includes leveraging spear phishing and watering hole attacks and exploiting malware distribution vulnerabilities.
Victimology
Patchwork APT focuses on government, defense, diplomatic entities, and academic institutions across South and Southeast Asia, extending to Europe and North America. Their operations have even notably targeted US think tanks and individuals involved in Chinese foreign relations, showcasing a strategic interest in geopolitical dynamics. The most targeted sectors of Patchwork’s cyber intrusions are Aviation, Defense, Energy, Financial, Government, IT, Media, NGOs, Pharmaceutical, and Think Tanks.
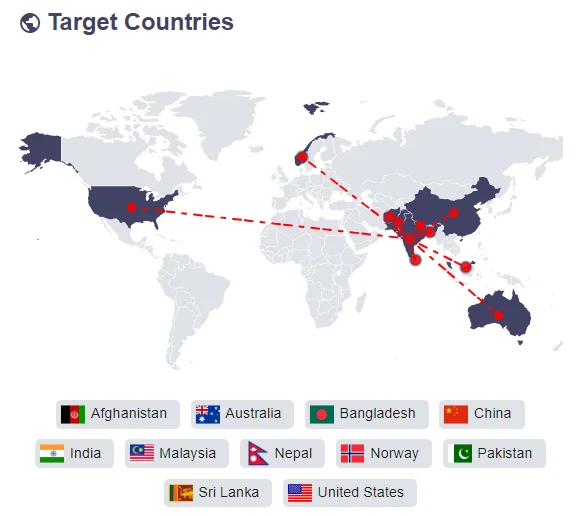
Target Countries of Patchwork APT (SOCRadar)
Therefore, Patchwork APT strategically targets high-profile diplomats and economists engaged in foreign relations with China, utilizing a custom set of cyber tools for espionage. The group’s operations extend to several countries, including Pakistan, Sri-Lanka, Uruguay, Bangladesh, Taiwan, Australia, and the US. 2018 dated campaigns of Patchwork, focusing on think tank groups in the US also drew attention to the group. This pattern of targeting reveals Patchwork’s interest in gathering intelligence on international diplomatic and economic policies and strategies.
Technical Capabilities and Tools
Patchwork APT employs spear phishing and watering hole attacks as primary vectors for infiltration. Spear phishing campaigns are meticulously crafted to target specific individuals within the organizations of interest, often leveraging social engineering techniques to deceive recipients into opening malicious attachments or clicking on compromised links.
Watering hole attacks involve compromising legitimate websites frequented by the group’s targets, aiming to exploit vulnerabilities in their web browsers or other software to deliver malware. These methods showcase Patchwork’s adaptability and focus on using human and system vulnerabilities to achieve their objectives.
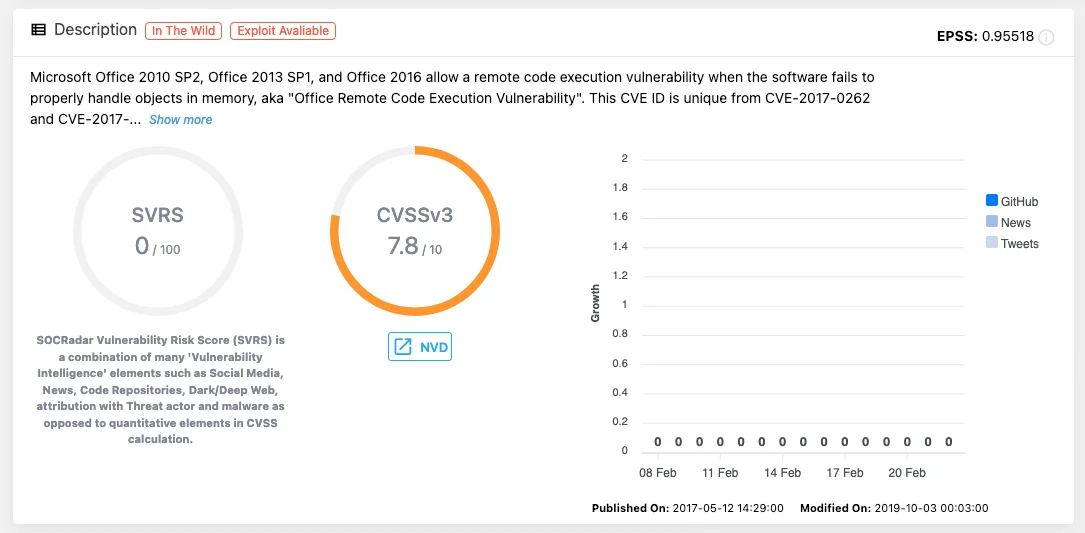
Vulnerability card of CVE-2017-0261 (SOCRadar)
In a cyber attack in 2021, a malicious Microsoft document exploited CVE-2017-0261, a vulnerability enabling remote code execution by improperly handling objects in memory. Analysis of the EPS script within the document revealed sophisticated mechanisms for dropping and executing Patchwork’s payloads, notably a custom keylogger identified by its unique SHA-256 hash.
Recorded CVE Exploits of Patchwork APT
Of course, their arsenal goes way beyond a Microsoft document; Patchwork APT’s arsenal includes malware like the BADNEWS RAT and VajraSpy, an Android-targeted RAT. Their techniques for maintaining access and exfiltrating data demonstrate advanced capabilities in utilizing vulnerabilities, social engineering, and encryption for stealthy operations.
Most recently, ESET researchers uncovered a sophisticated espionage campaign conducted by the Patchwork APT group, involving twelve Android apps bundled with VajraSpy, a remote access trojan (RAT). Six apps were on Google Play, and six were on other platforms. The apps, disguised as messaging tools, targeted users primarily in Pakistan, employing honey-trap romance scams to lure victims into downloading the malware. The campaign, which utilized Firebase Hosting for command and control servers, exfiltrated various data, including contacts and messages. Despite being removed from Google Play, the apps reached over 1,400 installs. Weak operational security exposed 148 compromised devices, mostly in Pakistan and India.
Associated Malware with Patchwork APT in SOCRadar Platform
Mitigations and Defense
The Patchwork APT group’s activities result in significant information theft and unauthorized remote access, posing risks to national security and intellectual property. Their targeted cyber espionage campaigns have broader geopolitical implications, influencing international relations and potentially destabilizing regional security dynamics.
- Implement Email Filtering: Patchwork APT often utilizes spear-phishing campaigns to target specific individuals within government, defense, diplomatic entities, and academic institutions. Email filtering solutions can detect and block malicious emails containing phishing attempts, reducing the risk of employees falling victim to deceptive tactics aimed at delivering malware or stealing credentials.
- Patch Management: They frequently exploit known vulnerabilities to deliver malware and gain unauthorized access to systems. Implementing robust patch management practices ensures that all software vulnerabilities are promptly addressed with the latest security patches, reducing the likelihood of successful exploitation by threat actors.
- Endpoint Security: Their operations involve deploying custom malware like VajraSpy, targeting Android devices to conduct espionage. Comprehensive endpoint security solutions can detect and block malicious activities, including the execution of remote access trojans (RATs), thereby protecting endpoints from compromise.
- Network Segmentation: Patchwork APT targets a wide range of sectors, including Aviation, Defense, Energy, Financial, Government, IT, Media, NGOs, Pharmaceutical, and Think Tanks. Implementing network segmentation isolates critical systems and sensitive data, limiting the lateral movement of attackers within the network and minimizing the potential impact of breaches.
- Access Control: They strategically target high-profile diplomats, economists, and individuals involved in Chinese foreign relations. Enforcing strict access control measures, such as the principle of least privilege, restricts unauthorized access to sensitive information, reducing the risk of compromise by threat actors seeking to gather intelligence on diplomatic and economic policies.
- Multi-Factor Authentication (MFA): They employ sophisticated techniques like spear phishing to compromise user accounts and gain unauthorized access to systems. Implementing MFA adds an extra layer of security, making it more difficult for attackers to compromise accounts, even if passwords are compromised through phishing attacks.
- Behavioral Analysis: They utilize social engineering techniques and custom malware like BADNEWS RAT to maintain access and exfiltrate data stealthily. Behavioral analysis tools can detect anomalous activities indicative of a security breach, allowing organizations to respond promptly and mitigate the impact of intrusions by threat actors.
- Incident Response Plan: In the event of a security breach or compromise, having a well-defined incident response plan ensures a swift and coordinated response to contain the threat, minimize disruption, and restore normal operations. Regularly testing the incident response plan helps identify areas for improvement and ensures readiness to handle cyber incidents effectively.
- User Awareness Training: Provide comprehensive cybersecurity awareness training to employees to educate them about the risks associated with phishing attacks, malicious attachments, and social engineering tactics used by threat actors. Empowering users to recognize and report suspicious activities can help prevent successful infections and campaigns.
In summary, it’s crucial to avoid clicking on unverified links, not to open untrusted email attachments, apply all available patches for vulnerabilities, keep security software updated, and implement rigorous patch management practices. Additionally, enhancing security measures through network and system hardening, alongside code hardening, can significantly reduce the risk of compromise.
To counter the sophisticated cyber espionage tactics employed by the Patchwork APT group further, organizations are also advised to adopt a proactive cybersecurity posture.
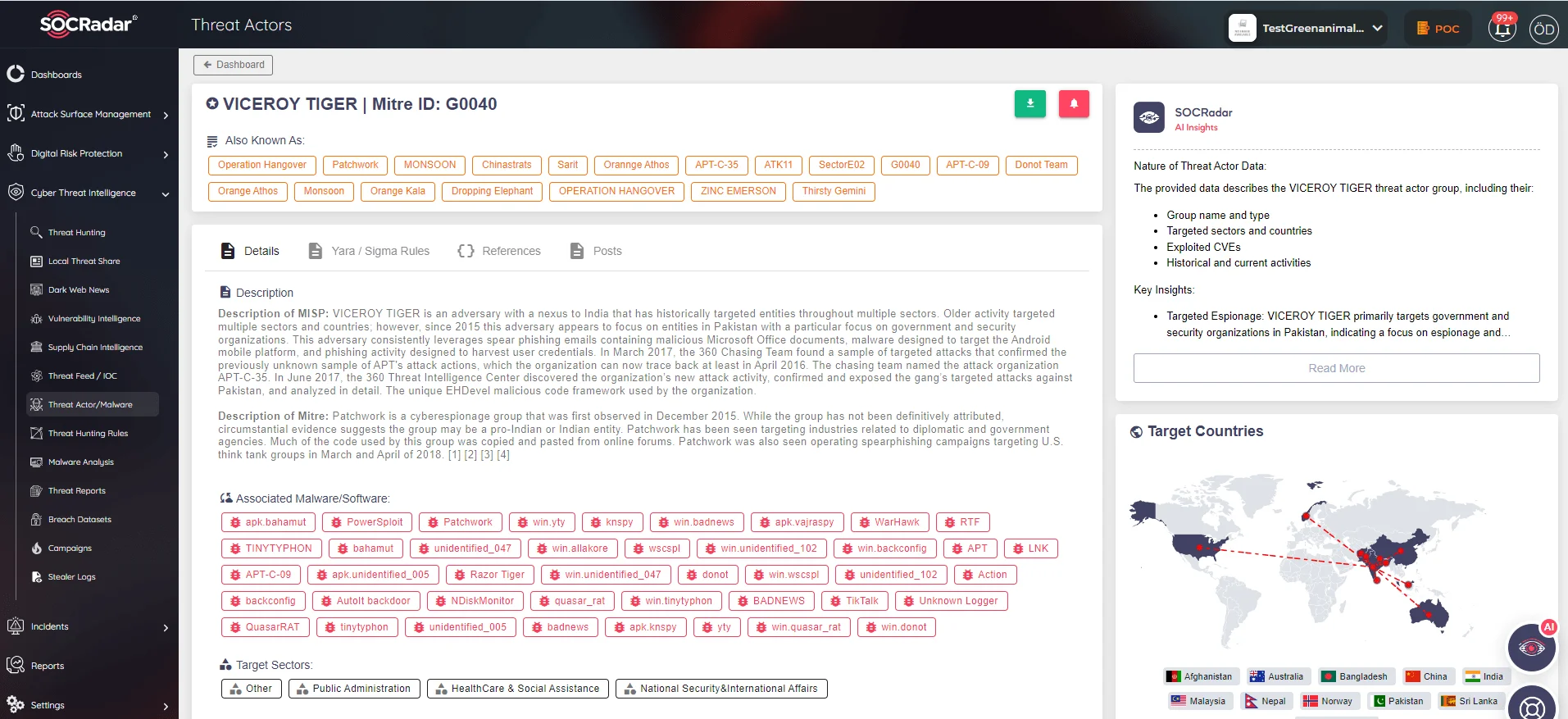
SOCRadar Threat Actor Page
SOCRadar’s Extended Threat Intelligence embodies an innovative advancement from conventional threat intelligence platforms, incorporating sophisticated functionalities that enhance threat detection and visibility significantly. This advanced solution employs robust machine learning technologies to scrutinize extensive volumes of threat data gathered from diverse open sources, social media platforms, and the dark web. Through the utilization of this holistic methodology, SOCRadar’s XTI empowers security teams to promptly discern and rank threats, furnishing them with proactive security measures.
MITRE ATT&CK TTPs of Patchwork APT
| Phase | Technique(s) |
| Reconnaissance | T1430 – Location Tracking, T1420 – File and Directory Discovery, T1517 – Access Notifications, T1426 – System Information Discovery, T1057 – Process Discovery, T1422 – System Network Configuration Discovery, T1033 – System Owner/User Discovery, T1418 – Application Discovery |
| Weaponization | T1204.002 – Malicious File, T1221 – Template Injection, T1132 – Data Encoding, T1218.001 – Compiled HTML File |
| Delivery | T1190 – Exploit Public-Facing Application, T1566 – Phishing, T1434 – App Delivered via Email Attachment, T1534 – Internal Spearphishing, T1566.001 – Spearphishing Attachment, T1193 – Spearphishing Attachment |
| Exploitation | T1055 – Process Injection, T1203 – Exploitation for Client Execution, T1481 – Web Service, TA0011 – Command and Control, T1071 – Application Layer Protocol, T1071.001 – Web Protocols, T1105 – Ingress Tool Transfer |
| Installation | T1053 – Scheduled Task/Job, T1053.005 – Scheduled Task, T1059 – Command and Scripting Interpreter, T1059.005 – Visual Basic, T1059.003 – Windows Command Shell |
| Command & Control | T1559 – Inter-Process Communication |
| Actions on Objectives | T1560 – Archive Collected Data, T1082 – System Information Discovery, T1176 – Browser Extensions, T1437 – Standard Application Layer Protocol, T1005 – Data from Local System, T1533 – Data from Local System, T1025 – Data from Removable Media, T1417 – Input Capture, T1512 – Capture Camera, T1113 – Screen Capture |
| Exfiltration | T1048.003 – Exfiltration Over Unencrypted/Obfuscated Protocol |
| Persistence | T1398 – Modify OS Kernel or Boot Partition, T1574 – Hijack Execution Flow, T1027 – Obfuscated Files or Information |
Latest IoCs related to Patchwork APT
HOSTNAME:
- fich.buzz
- deb-cn.net
- reawk.net
- ms-ethics.net
- aws-check.net
- ap1-acl.net
- preag.info
- dolper.top
- s-db.net
- ongrep.xyz
- mailnavymilbd.govpk.net
- mailnavybd.govpk.net
- dgms.paknavy-gov.com
- dgmp-paknavy.mod-pk.com
- cstc-spares-vip-163.dowmload.net
- Careitservices.paknvay-pk.net
IP:
- 160.20.147.67
- 66.219.22.252
- 5.230.73.106
HASH:
- 155d6932de11b6e1201f46c70160f4ca322642eec2f8c928f3cfcd6c7aa1ee2c
- ca24347d80aed81df2a0e89075c645bfd6081a8e66103ea680f3a8758999b32b
- ec6485f087298ea2f57b1aa64c66dc4b5e8cbc8cb63384770570da9071589074
- 90e7df73e769bf0bde48294c38004341778e6ed2a6cd8db9d20fe57524607607
- b019ed0bb09bda78af75f941ba1bb88f3b3e3604a202309d8661fdaacb04d02e
- f544a74de8264cd5b7bc184c81b78966
- 0daefb3d05e4455b590da122255121079e83d48763509b0688e0079ab5d48886
- 827c5e51d180f621d392885b0bd536b3
- 441d98dff3919ed24af7699be658d06ae8dfd6a12e4129a385754e6218bc24fa
- 135cb239966835fefbb346165b140f584848c00c4b6a724ce122de7d999a3251
- c736033eea8f6e1da5e19703d219842493e4487f
- 618aad16a2f358a977f3c183f2be1b9948cf8e96
- ee679afb897213a3fd09be43806a7e5263563e86ad255fd500562918205226b8
- ec4d6bf06dd3f94f4555d75c6daaf540dee15b18d62cc004e774e996c703cb34
- d3bf492b656ca32223e5eea46a0122a45b967f38bf7af3eea2fa6259e9d5a46f
- a60fc4e5328dc75dad238d46a2867ef7207b8c6fb73e8bd001b323b16f02ba00
- a265c32ed1ad47370d56cbd287066896d6a0c46c80a0d9573d2bb915d198ae42
- 17ccf24c4e09b1bc7ce5c0eb637a4edd
- cf1f4ec1d7db6cf1fe8e15687b348a279889689fa9c387de4a2c310c34336f9f
- cd09bf437f46210521ad5c21891414f236e29aa6869906820c7c9dc2b565d8be
- bc9d4eb09711f92e4e260efcf7e48906dca6bf239841e976972fd74dac412e2f
- 8b718a15f76768ba29849a5f4a6ca0ff1d9c8ba7bcdc9d89efc792fe20e9fdb5
- 8af93bed967925b3e5a70d0ad90eae1f13bc6e362ae3dac705e984f8697aaaad
- 75079e408ca9517825ffac396680a2d2169d691be3f1adbbd797e05e665c6fde
- 59f1d4657244353a156ef8899b817404fd7fedad
- dbdc7073a29e53aa16340d0c3da22680168aea94
- 53a1b84d67b8be077f6d1dd244159262f7d1a0f9
- ef00004a1ebc262ffe0fb89aa5524d42
- 792d20c8cc99ab8e1cf4d4bcba22131b2b76905d
For further IoCs about Patchwork APT, you may check the SOCRadar Platform.