Dark Web Profile: Salt Typhoon
[Update] February 15, 2025: “Salt Typhoon Exploited Cisco Router Flaws and Breached Telecoms”
Salt Typhoon, a Chinese state-sponsored Advanced Persistent Threat (APT), has been a formidable force in cyber espionage since its emergence in 2020. Known by various names such as GhostEmperor, FamousSparrow, and UNC2286, the group is linked to China’s Ministry of State Security and is believed to be a critical component of the country’s long-term cyber strategy. Salt Typhoon focuses on infiltrating critical communication networks and exfiltrating sensitive data, targeting entities across North America and Southeast Asia.
Employing sophisticated techniques, including the use of a Windows kernel-mode rootkit named Demodex, Salt Typhoon is adept at evading detection while conducting widespread data theft. Its campaigns have disrupted multiple sectors, exposing vulnerabilities in telecom infrastructure, broadband networks, and government systems. The group’s high-value targets include U.S. Internet Service Providers (ISPs), cloud service providers, and even political campaigns, reflecting its strategic emphasis on intelligence gathering and cyber warfare.
This profile delves into Salt Typhoon’s methods, notable campaigns, and the broader implications of its operations on global cybersecurity and national security frameworks.
Who is Salt Typhoon?
Salt Typhoon, first identified as a state-sponsored actor linked to Chinese intelligence, targets critical communication infrastructure, including broadband networks and telecom providers. First revealed to the public in September 2024 by the Wall Street Journal (WSJ), Salt Typhoon has rapidly become one of the most concerning cyber threats globally. Unlike many threat actors disclosed by private cybersecurity firms, Salt Typhoon’s activities were brought to light through investigative journalism, highlighting their significant geopolitical implications.

Threat actor card for Salt Typhoon
The group’s focus lies in intercepting call records, metadata, and sensitive communications. It has exploited vulnerabilities in systems associated with sensitive operations like court-authorized wiretaps, raising alarms about potential compromises in judicial and law enforcement networks. Experts speculate that Salt Typhoon is linked to high-profile Chinese APT groups, such as GhostEmperor and FamousSparrow, indicating shared methodologies and possibly a coordinated state-backed effort.
How Does Salt Typhoon Operate?
Salt Typhoon employs sophisticated tactics to infiltrate and maintain persistence within target environments. Key strategies include:
- Exploiting Zero-Day Vulnerabilities: Leveraging unpatched flaws in telecom infrastructure to gain access.
- Advanced Malware Frameworks: Using tools like GhostEmperor for kernel-mode privilege escalation.
- Broadband Network Manipulation: Intercepting call metadata and wiretap communications to extract critical data.
Salt Typhoon’s overlapping tactics with other Chinese APTs, such as UNC4841, suggest a shared operational pool of resources. Their methods focus on espionage, exfiltrating data for political, economic, and strategic advantage.
SOCRadar’s Threat Actor Intelligence provides detailed profiles and real-time insights into threat actors and APT groups such as Salt Typhoon, allowing organizations to identify adversaries’ TTPs and anticipate risks. This intelligence allows security teams to stay ahead of emerging threats to their sector.
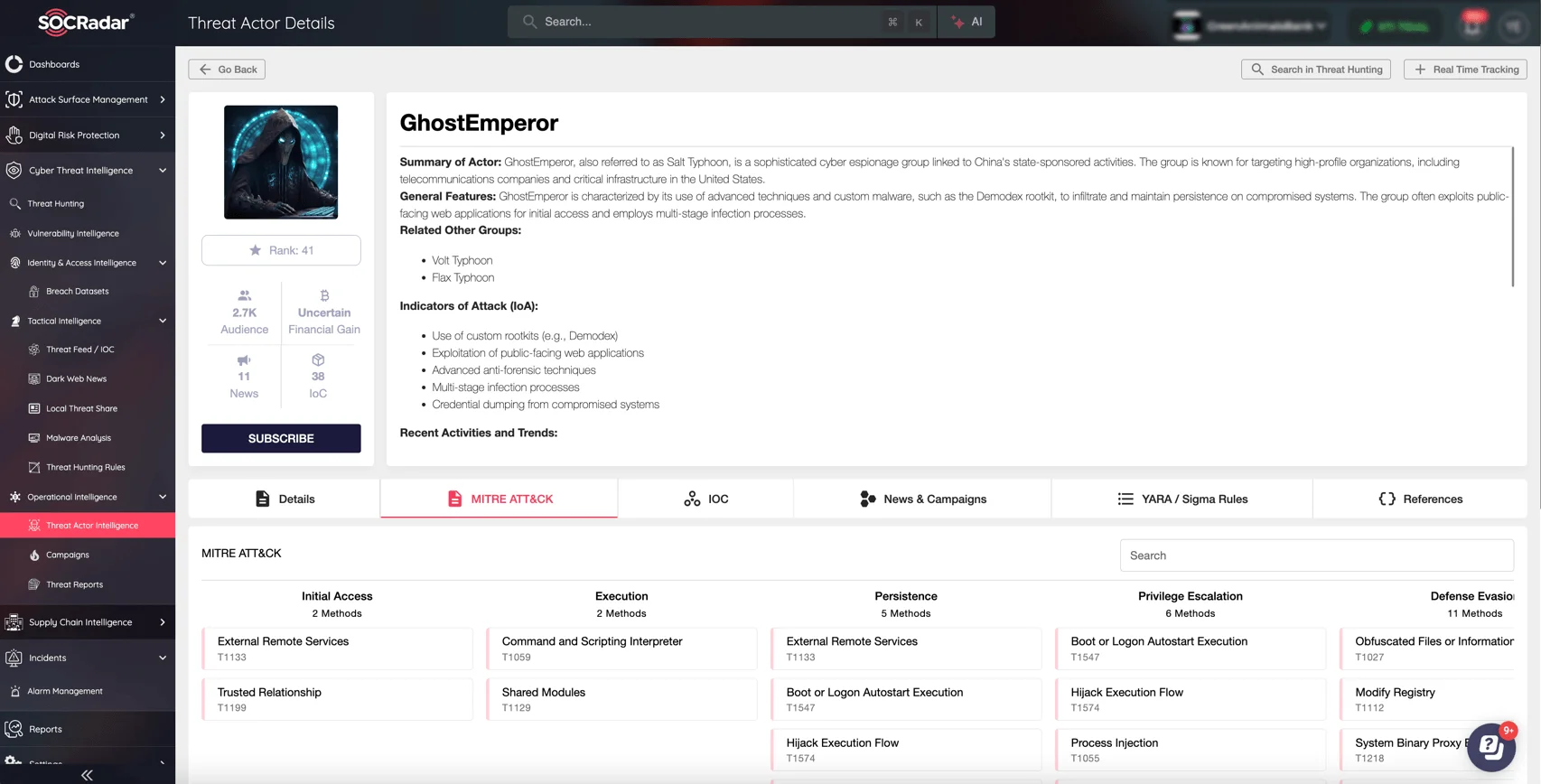
GhostEmperor (Salt Typhoon) details in SOCRadar’s Threat Actor Intelligence
Organizations can improve their defenses by monitoring campaigns and tracking the strategies of state-sponsored and criminal groups. Threat Actor Intelligence ensures a proactive response to evolving cyber threats, safeguarding critical infrastructure and sensitive information.
Campaigns
GhostEmperor Campaign: Leveraging Advanced Malware
Salt Typhoon was linked to sophisticated operations using an advanced multi-stage malware toolkit. Salt Typhoon leveraged the Demodex rootkit, which operates at the Windows kernel level to bypass detection and maintain long-term persistence. This framework was first observed during attacks exploiting the ProxyLogon vulnerability in 2021 and has since been linked to activities targeting Southeast Asia, the Middle East, and North America.
The infection chain begins with exploiting public-facing servers, including Exchange and web servers, followed by deploying in-memory implants and malicious drivers. The group uses custom encryption and obfuscation techniques to evade forensic analysis, ensuring their operations remain undetected for extended periods. By employing these techniques, Salt Typhoon demonstrated a high level of technical expertise and a calculated approach to cyberespionage.
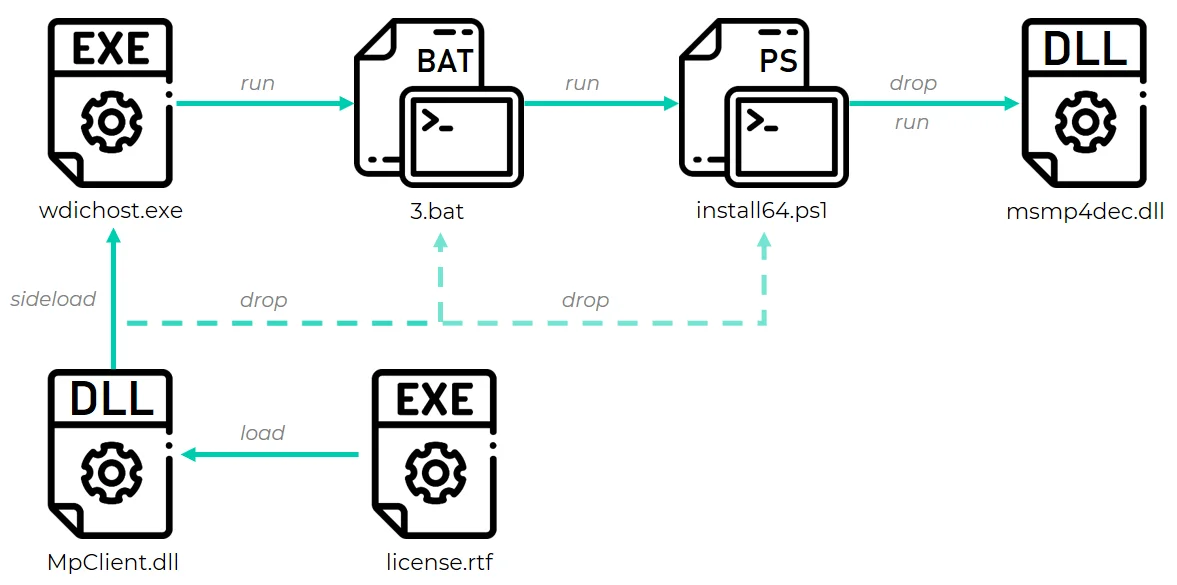
Illustration of a GhostEmperor infection chain initiated via a side-loaded DLL (Source: securelist)
Media-Driven Revelation of ISP Breaches
Salt Typhoon’s campaign began with infiltrating major U.S. Internet Service Providers (ISPs), including AT&T, Verizon, and Lumen Technologies. Initially disclosed by the Wall Street Journal in September 2024, the breaches targeted systems managing court-authorized wiretaps, allowing unauthorized access to sensitive communications. This intrusion raised alarms about the misuse of surveillance backdoors, which are inherently vulnerable to exploitation.
The attack persisted for months, compromising core infrastructure and enabling the interception of call metadata and generic internet traffic. Researchers linked these breaches to advanced malware capable of harvesting passwords and spreading malicious code through ISP networks. The scale and sensitivity of the operation highlighted the vulnerabilities of critical U.S. infrastructure.
T-Mobile and Metadata Attacks

In November 2024, Salt Typhoon expanded its operations to target T-Mobile, exfiltrating customer call records and metadata. Metadata attacks further underscored the group’s focus on high-value data, revealing insights into the personal and professional networks of individuals of interest to Chinese intelligence. This campaign affected at least eight U.S. telecommunications companies and involved exploiting both broadband networks and backend telecom systems. Metadata, while lacking content details, provides critical context about call durations, recipient numbers, and locations, making it invaluable for espionage.
Salt Typhoon Exploited Cisco Router Flaws and Breached Telecoms
Chinese threat actors have successfully breached several U.S. telecommunications providers by exploiting vulnerabilities in Cisco IOS XE network devices, according to recent findings from Recorded Future.
The attackers targeted two specific Cisco vulnerabilities (CVE-2023-20198 and CVE-2023-20273) in devices with enabled Web User Interface features and active HTTP/HTTPS servers. The zero-day vulnerability CVE-2023-20198, which Cisco disclosed to customers in October 2023, allows attackers to gain administrator access and take control of affected routers.
To maintain their presence and secretly extract data, the group employed generic routing encapsulation tunnels on the compromised devices, concealing the stolen information within GRE packets.
Broader Implications
Salt Typhoon’s intrusion into telecom networks was labeled “historically significant” due to its potential to disrupt critical infrastructure and harvest sensitive government and political communications. By October 2024, reports emerged of their attempts to compromise the phones of U.S. political figures, including President-elect Donald Trump and Vice President Kamala Harris’s campaign staff. These brazen attacks, coinciding with the U.S. election period, suggest a deliberate psychological and strategic operation designed to undermine confidence in American cybersecurity and governance.
Tactics, Techniques, and Procedures (TTPs)
Salt Typhoon’s operational methods align with advanced threat actor profiles. Key TTPs include:
| Tactic | MITRE ID – Technique | Description |
| Initial Access | T1190 – Exploit Public-Facing Application | Exploiting vulnerabilities in public-facing systems like web servers, Exchange servers, and Oracle servers to gain access. |
| Initial Access | T1566.001 – Phishing: Spearphishing Attachment | Delivering malicious attachments or links through phishing campaigns to compromise targeted accounts. |
| Execution | T1059.001 – Command and Scripting Interpreter: PowerShell | Using PowerShell scripts to deploy and execute malware payloads, often in obfuscated or encrypted form. |
| Execution | T1204.002 – User Execution: Malicious File | Deploying malicious files such as side-loaded DLLs and scripts to initiate infection chains. |
| Persistence | T1069 – Persistence Through Kernel-Mode Malware | Using Demodex rootkit for long-term persistence by bypassing Windows Driver Signature Enforcement. |
| Defense Evasion | T1027 – Obfuscated Files or Information | Leveraging encryption, custom loaders, and unique obfuscation techniques to avoid detection by security solutions. |
| Defense Evasion | T1036.005 – Masquerading: Match Legitimate Name or Location | Using fake headers (e.g., RIFF, JPEG, PNG) to disguise malicious traffic as legitimate media files. |
| Credential Access | T1555.003 – Credentials from Password Stores: Web Browsers | Harvesting credentials stored in web browsers to expand access within the target environment. |
| Credential Access | T1552.001 – Unsecured Credentials: Credentials in Files | Extracting plaintext credentials from configuration files and logs on compromised systems. |
| Lateral Movement | T1210 – Exploitation of Remote Services | Using tools like PsExec and WMI to pivot across networks after gaining initial foothold. |
| Collection | T1005 – Data from Local System | Harvesting sensitive data, including call metadata and government communications, for intelligence purposes. |
| Collection | T1115 – Clipboard Data | Monitoring clipboard activity to capture credentials and sensitive information copied by users. |
| Command and Control | T1219 – Remote Access Software | Maintaining communication with infected systems through custom Command-and-Control (C2) channels. |
| Impact | T1486 – Data Encrypted for Impact | Encrypting critical data to render it inaccessible, primarily for long-term espionage rather than extortion. |
Media Spotlight and Strategic Concerns
Public knowledge of Salt Typhoon’s activities has largely been driven by media reports rather than traditional cybersecurity firm disclosures. The Wall Street Journal first revealed the group’s existence in September 2024, followed by further details of compromised ISPs, telecom providers, and political entities. These revelations highlight not only the group’s technical sophistication but also its strategic intent to leverage stolen data for geopolitical gain.
The U.S. government responded by forming a unified coordination group, including the FBI, NSA, and CISA, to investigate and mitigate the breaches. Despite ongoing efforts, Salt Typhoon’s ability to re-enter patched systems and target prominent political figures underscores the need for enhanced vigilance.
How Can Organizations Defend Against Salt Typhoon?
Defending against Salt Typhoon requires a comprehensive, multi-layered strategy:
Network Segmentation and Monitoring
Isolating critical systems and continuously monitoring network activity is crucial to detect and mitigate threats early. Employing tools to analyze unusual behavior, such as changes in router configurations or unauthorized access attempts, can help in identifying potential compromises.
Regular Patch Management
Timely updates are essential to protect against zero-day vulnerabilities exploited by advanced actors like Salt Typhoon. Critical infrastructure, particularly telecom and broadband systems, should prioritize securing known vulnerabilities.
Zero Trust Architecture
Implementing strict access controls and regularly verifying the integrity of accounts and devices can minimize risks. Encrypting communications and enforcing least privilege policies are key components of a Zero Trust framework.
Threat Intelligence
Using platforms like SOCRadar to gain actionable insights into Salt Typhoon’s TTPs can help organizations stay ahead of potential threats. Real-time threat intelligence enhances the ability to implement targeted defensive measures.
Salt Typhoon campaigns show how sophisticated threat actors use compromised infrastructure to target sensitive communications and data. While their activities are primarily focused on exploiting compromised systems, the fallout frequently appears on the dark web. Credentials, metadata, and even insider knowledge can make their way into underground forums, posing additional risks to organizations.
SOCRadar’s Dark Web Monitoring provides unparalleled visibility into the internet’s hidden corners. By constantly scanning dark web forums, marketplaces, and stealer logs, the platform assists organizations:
- Detect stolen credentials and sensitive data leaks in real time.
- Monitor for discussions or transactions related to their digital assets or industry.
- Identify early warning signs of targeted campaigns or breaches.
SOCRadar’s Dark Web Monitoring module
SOCRadar’s Dark Web Monitoring provides actionable insights, allowing your organization to stay ahead of cybercriminals’ activities and mitigate threats before they escalate. By implementing this proactive defense solution, you can protect your assets and ensure operational security.
Example of Updated Guidance: CISA’s Recommendations Post-Salt Typhoon
In response to Salt Typhoon’s widespread attacks on U.S. telecom operators, the Cybersecurity and Infrastructure Security Agency (CISA), alongside the NSA, FBI, and international partners, issued updated security guidelines for Communications Service Providers (CSPs). These guidelines highlight the need for:
- Identifying Anomalies: Monitoring unusual configurations or alterations in devices such as routers, switches, and firewalls.
- Reducing Exposure: Limiting public internet access to management traffic and ensuring devices are inventoried and secured.
- Strengthening Network Infrastructure: Implementing advanced segmentation techniques like router ACLs and stateful packet inspection, along with deploying hardened VPN gateways and end-to-end encryption.
- Out-of-Band Management Networks: Physically separating management networks from operational traffic to prevent unauthorized access.
These recommendations also include specific measures for Cisco systems exploited by Salt Typhoon, emphasizing the application of hardening best practices to mitigate risks. Organizations, especially operators of critical national infrastructure, are urged to adopt these strategies to safeguard against future incursions.
By combining these tailored CISA recommendations with a proactive defense framework, organizations can better prepare for and mitigate the risks posed by advanced persistent threats like Salt Typhoon.
Conclusion
Salt Typhoon exemplifies the evolving threat landscape, where state-sponsored actors exploit critical infrastructure for espionage and strategic gain. Its campaigns, ranging from telecom breaches to metadata attacks, highlight the vulnerabilities in national infrastructure and the pressing need for robust defense measures.
To combat Salt Typhoon and similar APTs, organizations must invest in threat intelligence, adopt proactive defense strategies, and foster collaboration between private and public sectors. As this cyberstorm continues to churn, preparation and vigilance remain the best defense.




































