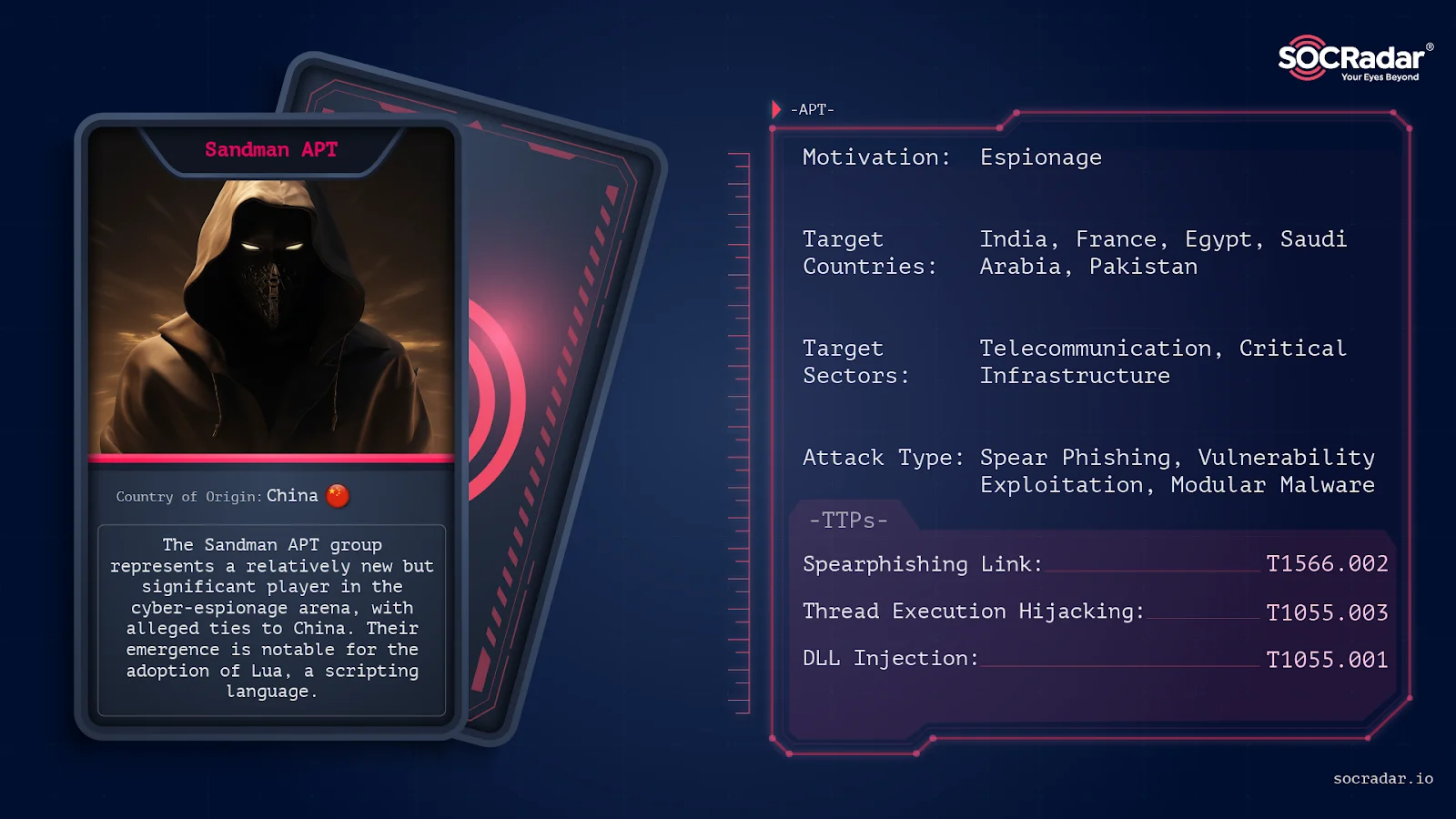
Dark Web Profile: Sandman APT
The Sandman APT group has garnered massive attention in 2023 for its targeted attacks against telecommunications providers in regions including Europe and Asia. As revealed by By Aleksandar Milenkoski, Bendik Hagen (PwC), and Microsoft Threat Intelligence, utilizing a unique and sophisticated LuaJIT-based modular backdoor, LuaDream; Sandman distinguishes itself through a strategic and stealthy approach, minimizing detection risks and leaving a minimal digital footprint.
Who is Sandman
Who is SandmanThe Sandman APT group represents a relatively new but significant threat in the cyber-espionage arena, with alleged ties to China. Their emergence is notable for the adoption of Lua, a scripting language historically associated with Western-aligned actors, indicating a shift in cyber-espionage tactics.
Sandman’s activities have been primarily observed targeting telecommunications sectors in the Middle East, Western Europe, and South Asia, aligning with China’s broader strategic interests in these regions.

Threat Actor Card
Modus Operandi
Sandman’s tactics involve spear phishing and exploiting vulnerabilities, with a particular focus on telecommunications companies for espionage purposes. Their operations are characterized by advanced evasion techniques and the ability to communicate over multiple protocols, demonstrating a high level of technical sophistication and strategic planning in their cyber-espionage activities.
According to research conducted by SentinelOne and QGroup, the Sandman APT group employs highly sophisticated and stealthy attack methods, with a particular focus on a novel modular backdoor known as LuaDream, which is built on the LuaJIT platform. LuaDream is strategically designed to minimize detection risks and showcases a continuous development approach.
The LuaDream staging process is a carefully designed operation focused on evading detection and thwarting analysis. It comprises seven stages conducted entirely in memory, utilizing a combination of fully-formed DLL PE images, code, and LuaJIT bytecode. Key DLL images involved in LuaDream staging include “ualapi.dll,” “MemoryLoadPex64.dll,” and “common.dll.”
While there is a possibility that threat actors manipulated DLL timestamps, their proximity to the intrusion date suggests their authenticity. Noteworthy anti-analysis measures include concealing LuaDream’s threads from debuggers using techniques like the NtSetInformationThread function, employing in-memory mapping of malicious PE images to evade EDR API hooks, and employing various other evasion techniques.
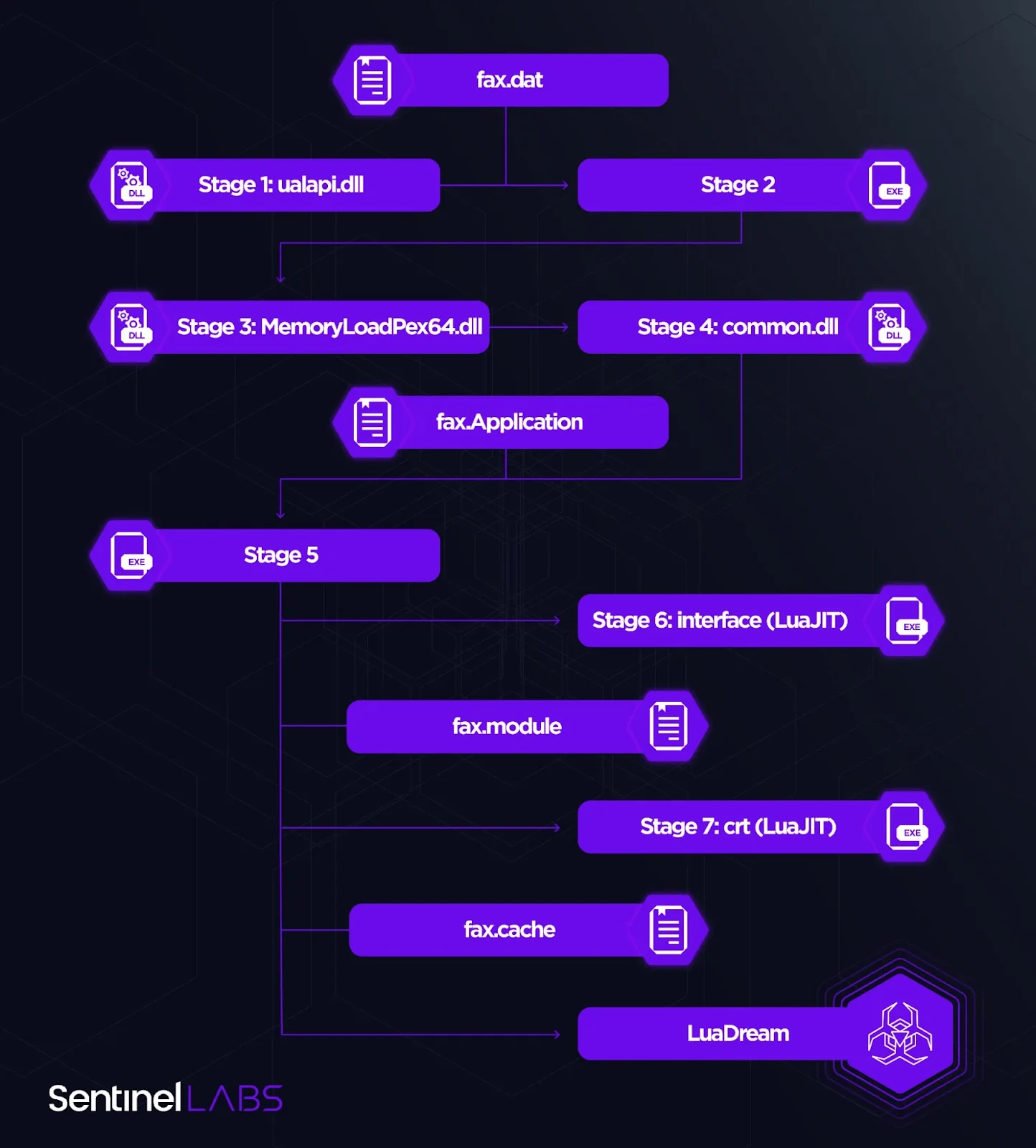
LuaDream’s staging process (SentinelOne)
LuaDream is a multifaceted, continually developed modular backdoor with a sophisticated architecture. Its primary functions encompass gathering system and user data for highly targeted attacks and managing attacker-provided plugins that enhance its capabilities. Although intrusion attempts were halted before plugins were deployed, analysis of LuaDream samples on VirusTotal provided insights into potential plugin functionalities, including command execution. Researchers have identified 36 distinct LuaDream components, and its support for multiple communication protocols hints at a large-scale project. LuaJIT is leveraged to obfuscate malicious Lua script code, making it challenging to detect.
LuaDream samples communicate with C2 servers “ssl.explorecell[.]com” and “mode.encagil[.]com.” Notably, there have been changes in infrastructure management practices, such as transitioning from directly exposed IP addresses to a load-balancing infrastructure. This shift likely aims to conceal the true hosting location. An interesting observation is that multiple LuaDream deployments communicate with the same C2 server, indicating a lack of comprehensive C2 infrastructure segmentation.
While Sandman’s specific targeted vulnerabilities in telecommunications networks remain undisclosed, this reflects the group’s secretive nature and ongoing efforts to uncover their full technological capabilities.
Targets
As mentioned above, The Sandman APT group predominantly targets telecommunications providers in regions such as Europe, the Middle East, and South Asia. These operations reflect a strategic focus on gathering intelligence from these key sectors, likely for espionage purposes. The group’s activities involve sophisticated cyber-espionage tactics, aiming to infiltrate and extract valuable information from these targets. While specific details of their operations are undisclosed, their known focus on telecommunications sectors indicates a keen interest in intercepting and monitoring communications, possibly for gathering geopolitical and economic intelligence.
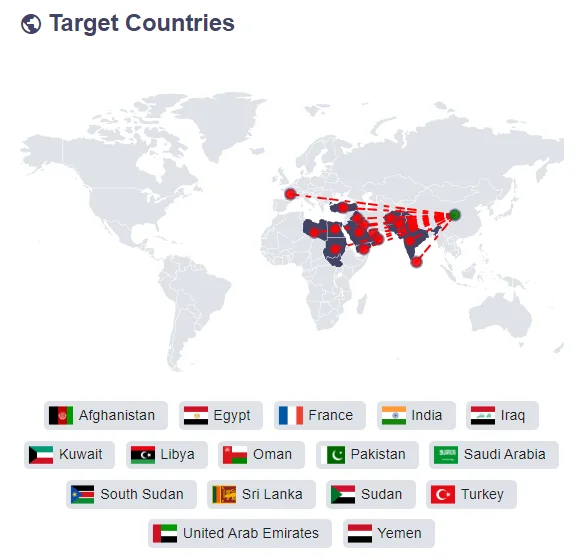
Target Countries in SOCRadar Threat Actors tab
Relations
In a later research again by SentinelOne and Microsoft Threat Intelligence some similarities with other actors and joined operations are observed. The Sandman APT group exhibits significant connections with other China-based threat actors, particularly STORM-0866/Red Dev 40. These groups share similarities in infrastructure control and management practices, including hosting provider choices and domain naming conventions. The use of KEYPLUG, a backdoor commonly employed by these groups, further suggests a close association. This interconnection highlights the collaborative nature of the Chinese cyber-espionage landscape, where multiple threat groups often cooperate or share tools and tactics.
Actions in late 2023 against the Sandman APT group have been predominantly in the realm of research and exposure. Cybersecurity firms and intelligence agencies have been working to uncover and document the group’s Tactics, Techniques, and Procedures (TTPs). This includes a detailed analysis of their malware, infrastructure, and operational patterns. However, specific details about direct countermeasures or offensive actions against Sandman are not publicly disclosed. The ongoing research and monitoring efforts are crucial in understanding and mitigating the threat posed by this group.
Conclusion
To safeguard against threats like the Sandman APT group, organizations, especially telecommunications providers, should enhance their cybersecurity defenses. This includes regularly updating and patching systems, implementing strong endpoint security measures, and educating staff on the dangers of spear phishing and social engineering attacks. Regular network monitoring and analysis can help in early detection of suspicious activities. Additionally, organizations should develop and maintain robust incident response plans to quickly address any breaches or suspicious activities. These measures, coupled with staying informed about the latest threat intelligence, can significantly reduce the risk of compromise by sophisticated threat actors like Sandman.
In conclusion, the exploration of the Sandman APT group unveils the intricate and evolving landscape of cyber-espionage. With their sophisticated tactics and tools, particularly LuaDream, Sandman represents a significant threat, especially to the telecommunications sectors. Their connections with other APT groups, notably within the China-based cyber threat landscape, highlight the complex and collaborative nature of state-sponsored cyber activities. This analysis underlines the importance of vigilant cybersecurity practices and continued research to understand and counter such advanced adversaries.
Mitigation Strategies against Sandman APT
- Patch and Update Systems: Regularly apply security patches and updates to all software and systems, especially public-facing applications. This can help protect against initial access through exploiting known vulnerabilities.
- Network Segmentation: Implement network segmentation to restrict lateral movement within your network. This can limit the attacker’s ability to move freely once inside the network.
- Endpoint Protection: Deploy advanced endpoint protection solutions that can detect and prevent process injection, code execution, and other malicious activities.
- Threat Intelligence: Stay informed about the latest threat intelligence related to Sandman APT and similar threat actors. This can help organizations proactively identify and respond to potential threats.
- SOCRadar provides real-time threat intelligence feeds, including indicators of compromise (IoCs), malware signatures, and Tactics, Techniques, and Procedures (TTPs) associated with Sandman APT. This enables organizations to stay ahead of emerging threats.
SOCRadar Platform, Threat Actors/Malware
- User Training: Train employees to recognize phishing attempts and suspicious activity. A well-informed workforce can be a valuable defense against initial access attempts.
- Intrusion Detection and Response: Implement robust intrusion detection and response systems to detect and respond to suspicious activities and lateral movement.
- Privilege Management: Implement the Principle of Least Privilege (PoLP) to restrict users and systems to the minimum level of access necessary. This can limit the impact of a successful intrusion.
- Threat Hunting: Proactively search for signs of compromise within your network. Conduct regular threat hunting exercises to detect any malicious activity that may have gone unnoticed.
- Incident Response Plan: Develop and regularly update an incident response plan to guide your organization’s response to a security incident. Ensure that all relevant personnel are familiar with the plan.
- Security Awareness: Maintain a high level of security awareness within the organization. Encourage reporting of suspicious activities and promote a culture of cybersecurity.
- Network Monitoring: Implement robust network monitoring to detect unusual or unauthorized traffic patterns that may indicate a security breach.
- Zero Trust Architecture: Consider adopting a Zero Trust security model, which assumes that threats exist both inside and outside the network. This approach enforces strict access controls and continuous verification of trust.
Indicators Of Compromises
Here is a IoC list provided by the SentinelOne about the Sandman APT and LuaDream:
Domains:
dan.det-ploshadka[.]com (KEYPLUG C2 server)
mode.encagil[.]com (LuaDream C2 server)
ssl.articella[.]com (Suspected KEYPLUG or LuaDream C2 server)
ssl.e-novauto[.]com (KEYPLUG C2 server)
ssl.explorecell[.]com (LuaDream C2 server)
yum.luxyries[.]com (KEYPLUG C2 server)
IP Addresses:
146.70.157[.]20 (KEYPLUG C2 server, based on known C2 certificates)
172.67.216[.]63 (KEYPLUG C2 server)
185.38.142[.]129 (KEYPLUG C2 server, based on a known C2 certificate)
185.51.134[.]27 (LuaDream and KEYPLUG C2, based on known C2 certificates)
185.82.218[.]230 (LuaDream C2 server)
37.120.140[.]205 (KEYPLUG C2 server, according to a known C2 certificate)
45.129.199[.]122 (KEYPLUG C2 server, based on a known C2 certificate)
45.80.148[.]151 (LuaDream C2, based on a known C2 certificate)
45.90.59[.]17 (KEYPLUG C2 server, according to a known C2 certificate)
5.2.67[.]176 (KEYPLUG C2 server, based on a known C2 certificate)
5.2.72[.]130 (KEYPLUG C2 server, based on a known C2 certificate)
5.255.88[.]188 (KEYPLUG C2 server, based on a known C2 certificate)
79.110.52[.]160 (KEYPLUG C2 server)
Certificate Thumbprints:
a7932112b7880c95d77bc36c6fcced977f4a5889 (KEYPLUG C2)
b6d759c9ea5d2136bacb1b2289a31c33500c8de8 (KEYPLUG C2)
fc8fdf58cd945619cbfede40ba06aada10de9459 (LuaDream C2)
SHA1 File Names:
1cd0a3dd6354a3d4a29226f5580f8a51ec3837d4 (fax.dat)
27894955aaf082a606337ebe29d263263be52154 (fax.Application)
5302c39764922f17e4bc14f589fa45408f8a5089 (ualapi.dll)
77e00e3067f23df10196412f231e80cec41c5253 (fax.cache)
b9ea189e2420a29978e4dc73d8d2fd801f6a0db2 (UpdateCheck.dll)
fb1c6a23e8e0693194a365619b388b09155c2183 (updater.ver)
ff2802cdbc40d2ef3585357b7e6947d42b875884 (fax.module)
LuaDream Folder File Paths:
%ProgramData%FaxConfig
%ProgramData%FaxLib
C2 Server Domains:
mode.encagil[.]com
Ssl.explorecell[.]com
Potential MITRE ATT&CK TTPs:
| Tactic | Technique | Procedure |
| Initial Access | Phishing (T1566) | Sandman employs spear phishing to gain initial access, targeting telecommunications companies for espionage. |
| Spear Phishing Link (T1566.002) | Utilizes malicious links in spear phishing emails as a method for initial compromise. | |
| Execution | Command and Scripting Interpreter (T1059) | Uses LuaJIT-based modular backdoor, LuaDream, for executing commands. |
| Privilege Escalation | DLL Injection (T1055.001) | The use of LuaDream suggests the potential for DLL Injection for executing malicious payloads within the context of legitimate processes. |
| Thread Execution Hijacking (T1055.003) | Although not explicitly mentioned, techniques akin to Thread Execution Hijacking may be utilized by Sandman for stealthy execution of malicious code. | |
| Defense Evasion | Obfuscated Files or Information (T1027) | LuaDream employs obfuscation to hide its malicious code, making detection challenging. |
| Deobfuscate/Decode Files or Information (T1140) | Utilizes LuaJIT for deobfuscation of malicious code executed in memory. | |
| Discovery | System Network Configuration Discovery (T1016) | Capable of gathering system and user data, indicating use of discovery techniques for network configurations and sensitive information. |
| Command and Control | Multi-protocol Command and Control (T1071) | Supports multiple communication protocols for sophisticated C2 operations. |
| Exfiltration | Exfiltration Over C2 Channel (T1041) | Capability to exfiltrate data over the established C2 channels. |



































