Dark Web Profile: Silent Ransom Group (LeakedData)
A threat group identifying itself as LeakedData emerged in mid-December 2024, claiming responsibility for attacks on at least 41 victims.

Header of LeakedData’s Data Leak Site (DLS)
Early speculation from some researchers suggested LeakedData might have been a lure for a watering hole attack, a tactic where attackers compromise websites likely to be visited by specific targets in order to deliver malware. However, this theory appears unlikely, as there is little to indicate that researchers were the intended targets. However, emerging evidence points to LeakedData being a rebranded incarnation of a familiar adversary: a remnant of the Conti ransomware, Silent Ransom Group.
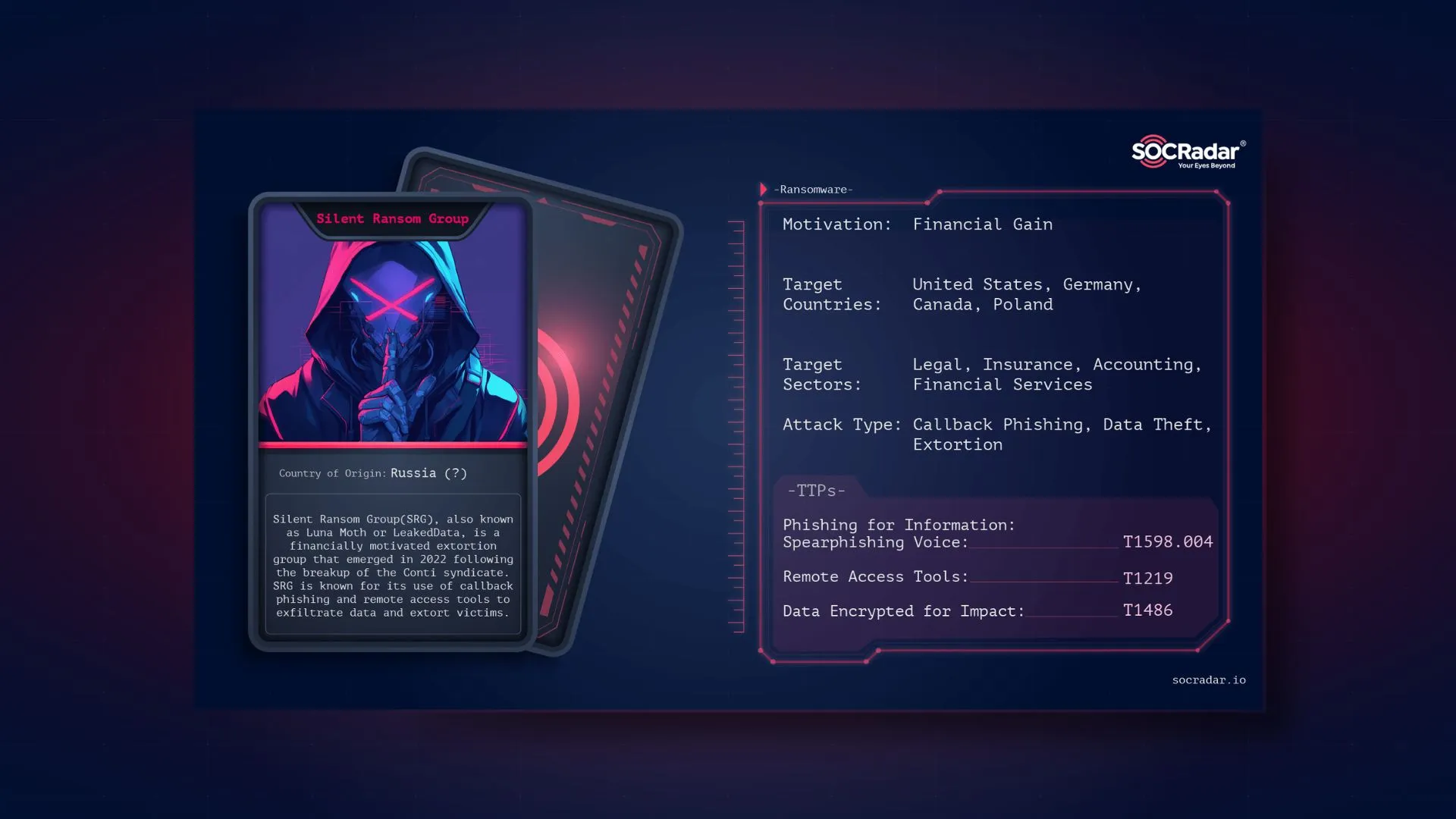
Who is Silent Ransom Group
Silent Ransom Group (SRG), also known as Luna Moth or apparently LeakedData, is a cybercriminal organization that emerged in early 2022 following the collapse of the Conti ransomware syndicate. SRG gained notoriety for deploying a callback phishing technique, often referred to as BazarCall-style attacks, to gain initial access to victim environments.

Threat actor card for Silent Ransom Group
According to the FBI, as of June 2023, SRG conducted phishing campaigns that involved sending victims a notification about fictitious charges, prompting them to call a phone number. Once on the call, victims were instructed to install legitimate remote management tools via a link sent by email. These tools were then exploited to gain deeper access to systems, allowing the attackers to move laterally, exfiltrate sensitive data, and ultimately extort the victim organization without encrypting files.
Historically, the group behind SRG had previously supported Ryuk and Conti ransomware operations by using BazarCall tactics to penetrate networks. In March 2022, around the time Conti disbanded amid the fallout from Russia’s invasion of Ukraine, this cluster of operators split off to form their own independent extortion group, Silent Ransom Group.
For months, LeakedData’s data leak site (DLS) remained a mystery to many observers in the ransomware tracking community. Some initially dismissed it as a recycling platform for previously leaked data. However, with a growing number of victims, at least eight of whom have filed public breach disclosures, it has become clear that this site is indeed the operational front of SRG. The oldest confirmed incident dates back to June 7, 2022, just three months after Conti’s implosion, while most publicly known breaches occurred throughout 2024.
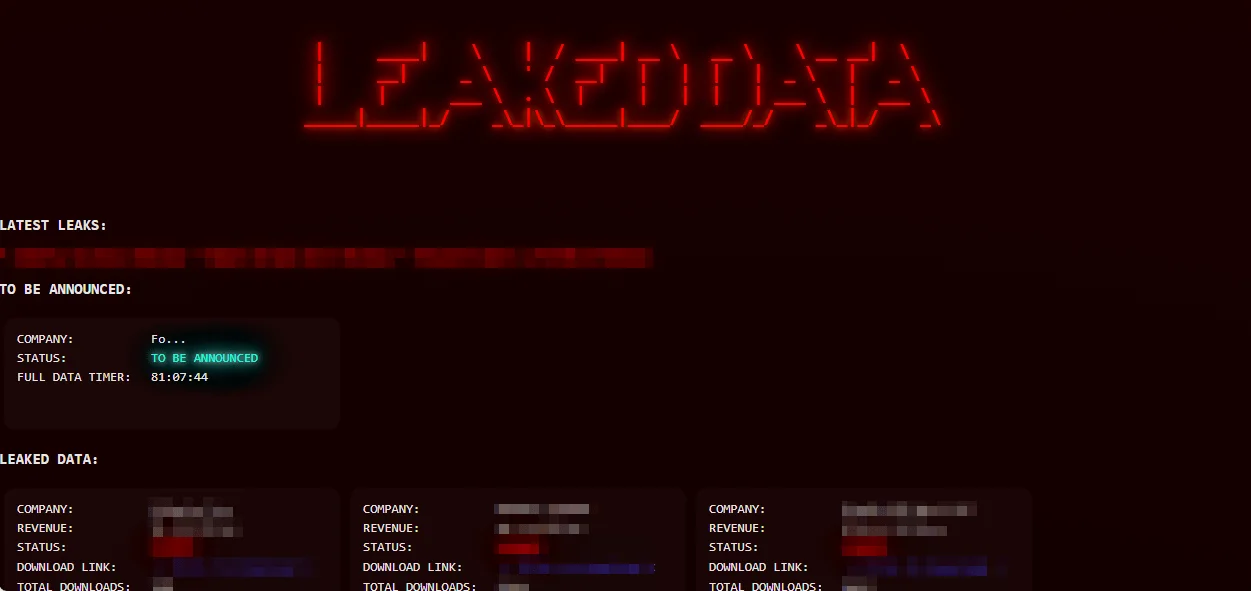
Silent Ransom Group’s DLS
In essence, SRG represents a Conti offshoot that evolved from ransomware deployment to targeted data extortion, leveraging social engineering, legitimate tools, and advanced lateral movement techniques to maximize their reach and pressure on victim organizations.
What are Silent Ransom Group’s Targets?
Silent Ransom Group (SRG) primarily targets organizations in the United States, which account for the overwhelming majority of known victims. Their focus is heavily weighted toward data-sensitive industries, especially law firms, insurance providers, accounting firms, and financial services companies. These sectors are often chosen for the critical, confidential information they manage and their urgency to avoid public exposure.
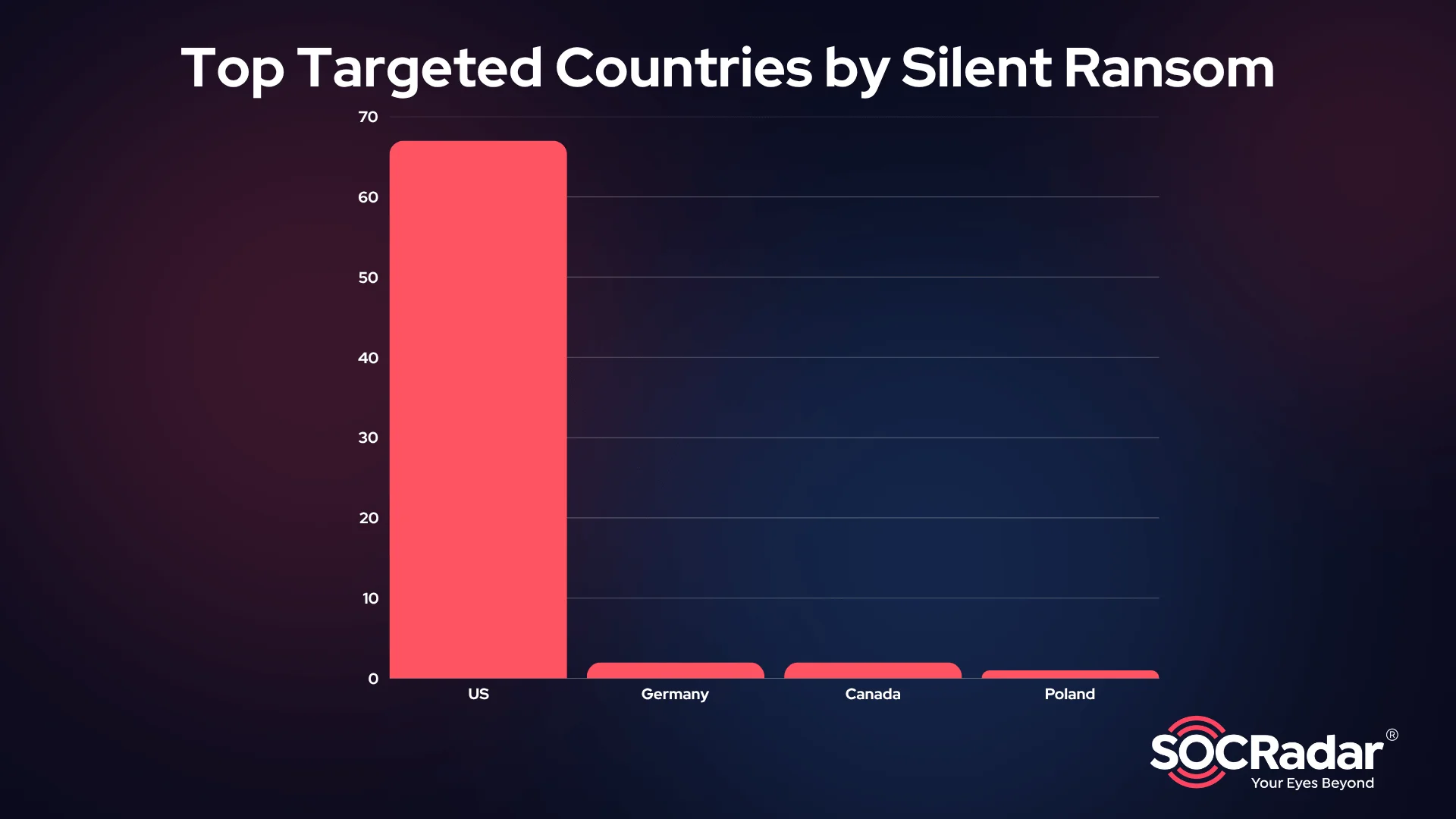
Top targeted countries by SRG according to their leaked data list
SRG’s victims range from small and mid-sized businesses to large firms. While most targets are American, a small number of victims have been identified in Germany, Canada, and Poland.
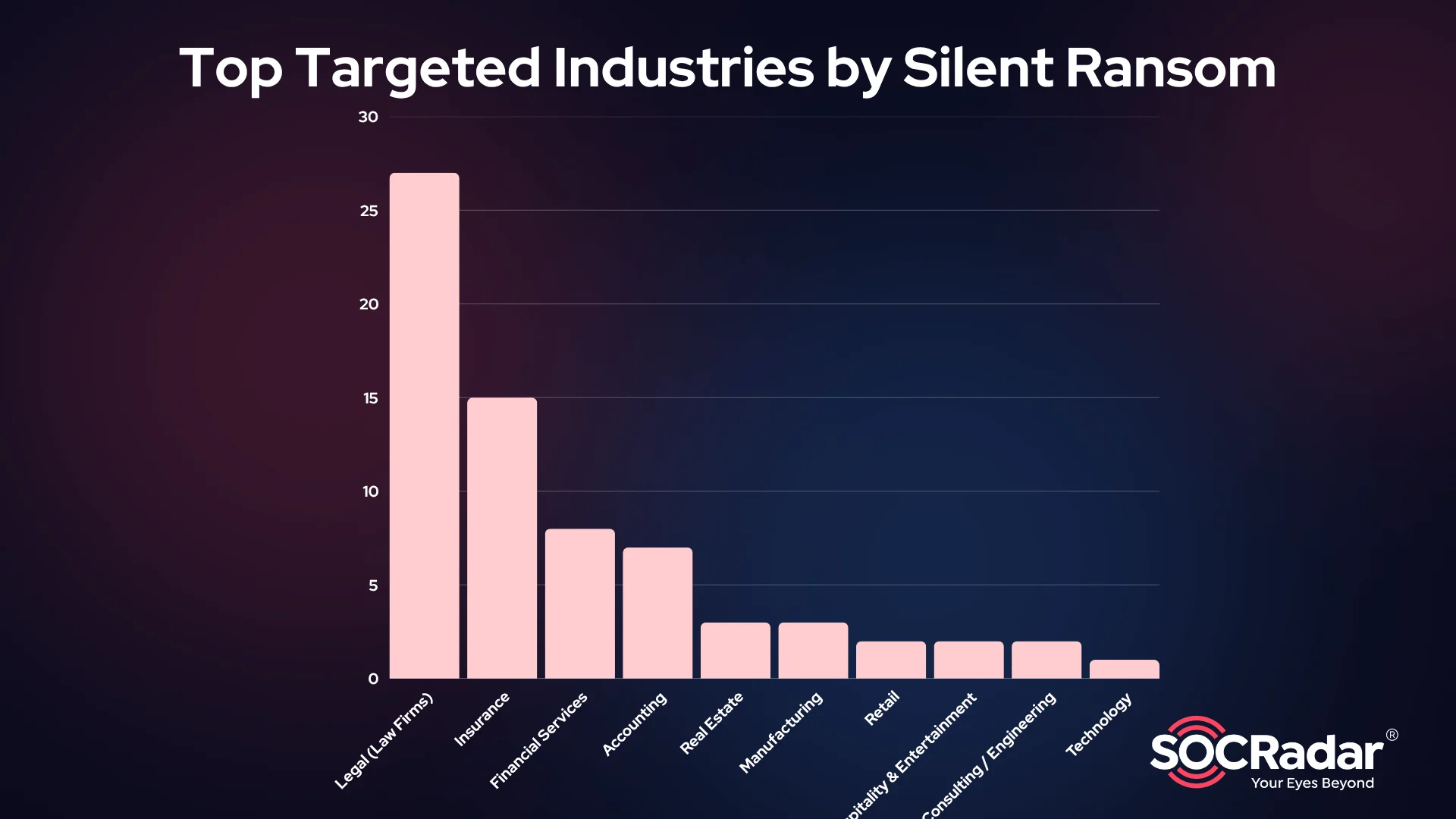
Top targeted industries by SRG according to their leaked data list
The group favors sectors where regulatory pressure, reputational risk, and client confidentiality can be exploited to maximize extortion leverage. Their approach reflects a deliberate strategy: quietly infiltrate, steal data, and demand payment, not through mass disruption, but by applying targeted pressure on organizations that can least afford a breach.
What are Silent Ransom Group’s Techniques?
LeakedData’s DLS is minimal, consisting of a single clear web page but most extortion groups rely on TOR. The site has no rules, contact info, or any other pages. It features two sections: one listing named victims whose data has been leaked, and another showing countdowns for upcoming disclosures. Initially, victim names are partially redacted and revealed once a timer expires, at which point a link to the stolen data is provided, nearly identical to any ransomware-extortion group other than its simplicity.

Silent Ransom Group’s DLS, Leaked Data section
Recent research shows the group now creates fake helpdesk-themed domains to impersonate corporate IT support portals. These lookalike domains, e.g., “company.name”-helpdesk[.]com, are crafted to lure employees into submitting credentials or sensitive data. Registered mainly through GoDaddy and often using nameservers from domaincontrol[.]com, these domains follow recognizable naming conventions such as combining a target’s name with “help” or “helpdesk”.
Fake IT support site (EclecticIQ)
Their phishing campaigns are highly tailored, using spoofed domains and convincing emails to trick users into interacting with fake support portals. Once credentials are harvested, attackers may proceed to steal data, access internal systems, and set the stage for extortion.
Silent Ransom Group (SRG) also continues to employ “call-back” phishing attacks. According to a blog post by Arctic Wolf, the group sends emails impersonating brands like Duolingo or Masterclass, claiming a suspicious charge and urging the recipient to call a support number. Once contact is made, the attackers socially engineer the victim into installing legitimate remote desktop software, such as Zoho Assist or AnyDesk, which gives them full control of the system. From there, they exfiltrate sensitive files, often to private servers hosted on providers like Hostwinds, and demand a ransom under the threat of public data exposure or sale.
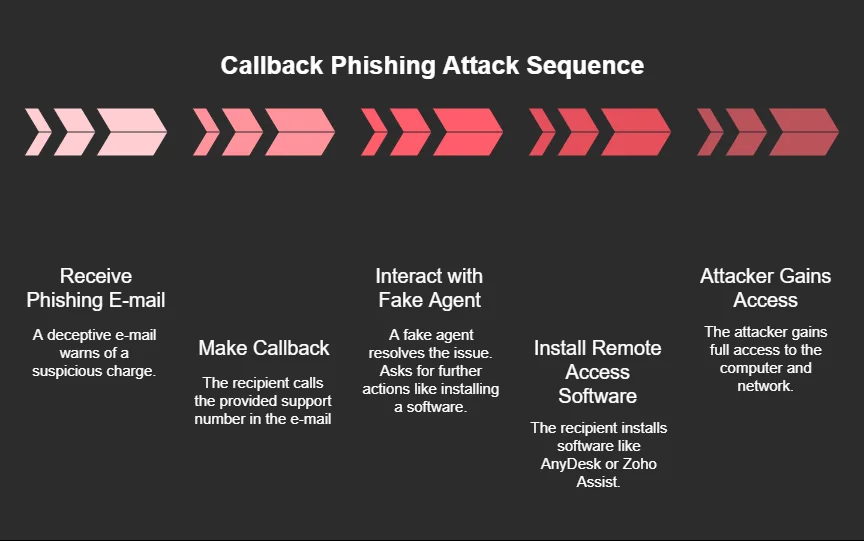
Callback phishing steps
This approach, as outlined in Arctic Wolf’s investigation, enables SRG to carry out highly targeted campaigns with a low malware footprint. Their use of trusted software and convincing social engineering techniques has been particularly effective against law firms, though similar tactics have also been observed in attacks on other industries.
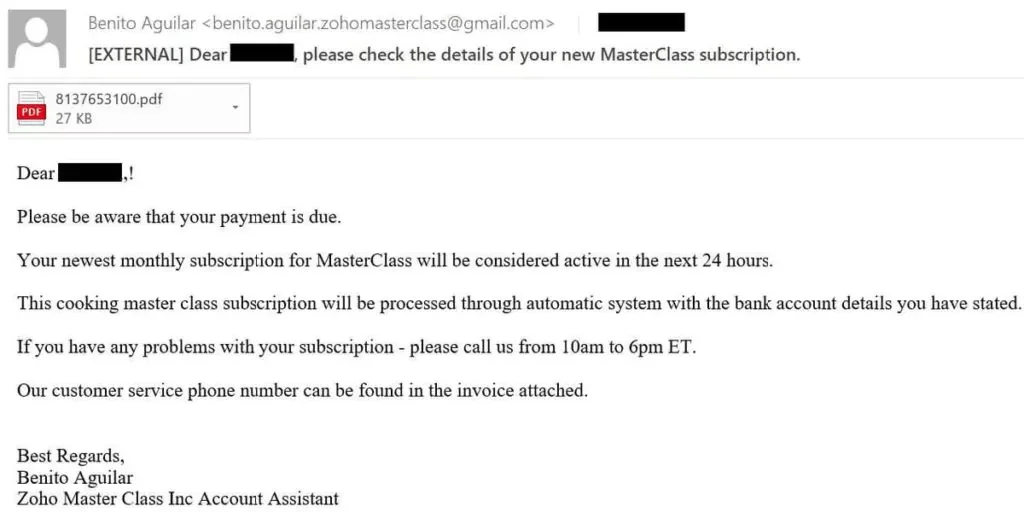
Example Silent Ransom callback phishing mail from 2022 (Sygnia)
What Are the Mitigation Tactics Against Silent Ransom Group?
Mitigating threats from the Silent Ransom Group (SRG) requires a multi-layered strategy combining domain intelligence, network controls, access management, and end-user awareness.
- Detect and Monitor Suspicious Domains
EclecticIQ researchers have outlined a clear method to proactively identify domains used by SRG:
- Pattern Recognition: Look for domains following the format ^[a-z]{1,}-help(desk){0,1}.com$, which mimic internal IT support (e.g., company-helpdesk.com).
- Registrar Filtering: Monitor newly registered domains through registrars like GoDaddy, commonly used in SRG campaigns.
- Nameserver Check: Flag domains using domaincontrol[.]com, a frequent component of SRG infrastructure.
- Registration Date Range: Focus especially on domains registered after March 1, 2025, when recent waves of attacks were first observed.
Applying these filters across DNS and WHOIS databases has already exposed dozens of malicious domains impersonating law firms and other high-risk organizations.
- Strengthen Email and Domain Protection
- Threat Intelligence Integration: Use automated tools and threat feeds to continuously scan for domains that match SRG patterns.
- Block Suspicious Domains: Preemptively block domains that follow known SRG naming conventions at the DNS level or via secure web gateways.
- Registrar Collaboration: Report suspicious domains to registrars like GoDaddy or Namecheap for potential takedown.
- Restrict Unnecessary Network Access
- Limit SFTP Traffic: Block outbound SFTP (port 22), as SRG uses tools like WinSCP to exfiltrate stolen data over secure file transfer.
- Harden Network Segmentation: Restrict access to internal shares and sensitive data directories unless strictly necessary.
- Lock Down Remote Access Tools
- Remove Unused RMM Software: Uninstall remote management tools such as AnyDesk, Zoho Assist, or TeamViewer if they are not actively used for business operations.
- Enforce Application Control Policies: Only allow pre-approved remote access software via endpoint protection or group policy rules.
- Monitor for RMM Installations: Set alerts for the appearance of unauthorized RMM tools within your environment.
- Enforce Strong Identity and Access Controls
- Enable Multi-Factor Authentication (MFA): Ensure MFA is required across all privileged accounts and access points to mitigate stolen credential use.
- Implement Least Privilege: Audit and reduce user access rights, particularly for roles exposed to phishing and fraud attempts.
- Conduct Targeted Security Awareness Training
- Vishing & Phishing Simulations: Train employees to spot callback phishing scams, including fake support emails and phone-based social engineering.
- Verification Protocols: Encourage users to verify IT support requests by contacting internal helpdesks directly, not via email prompts or external numbers.
- Regular Refreshers: Reinforce awareness through routine simulations and targeted alerts when phishing trends evolve.
- Incident Response and Threat Hunting
- Establish Playbooks: Maintain up-to-date response plans tailored to data extortion scenarios.
- Deploy Threat Hunting: Use EDR/XDR platforms to detect lateral movement, RMM activity, or unauthorized file transfers.
- Monitor Exfiltration Channels: Flag abnormal outbound connections, especially to file-sharing or remote hosting platforms like Hostwinds, often used by SRG.
How Can SOCRadar Help?
SOCRadar offers comprehensive solutions to defend against Silent Ransom Group and similar ransomware threats. Here’s how:
Extended Threat Intelligence: SOCRadar’s real-time platform delivers deep insights into ransomware group’s tactics, techniques, and procedures (TTPs), helping organizations anticipate and counter evolving attack strategies.
SOCRadar, Ransomware Intelligence
Dark Web Monitoring: The platform continuously scans the dark web and underground forums for mentions of compromised data, leaked credentials, or infrastructure linked to Silent Ransom Group, enabling early threat detection and faster response.
SOCRadar, Advanced Dark Web Monitoring
Vulnerability Intelligence & Management: SOCRadar identifies and prioritizes vulnerabilities that may be exploited by ransomware groups, allowing organizations to close potential entry points before they’re used in a campaign.





































