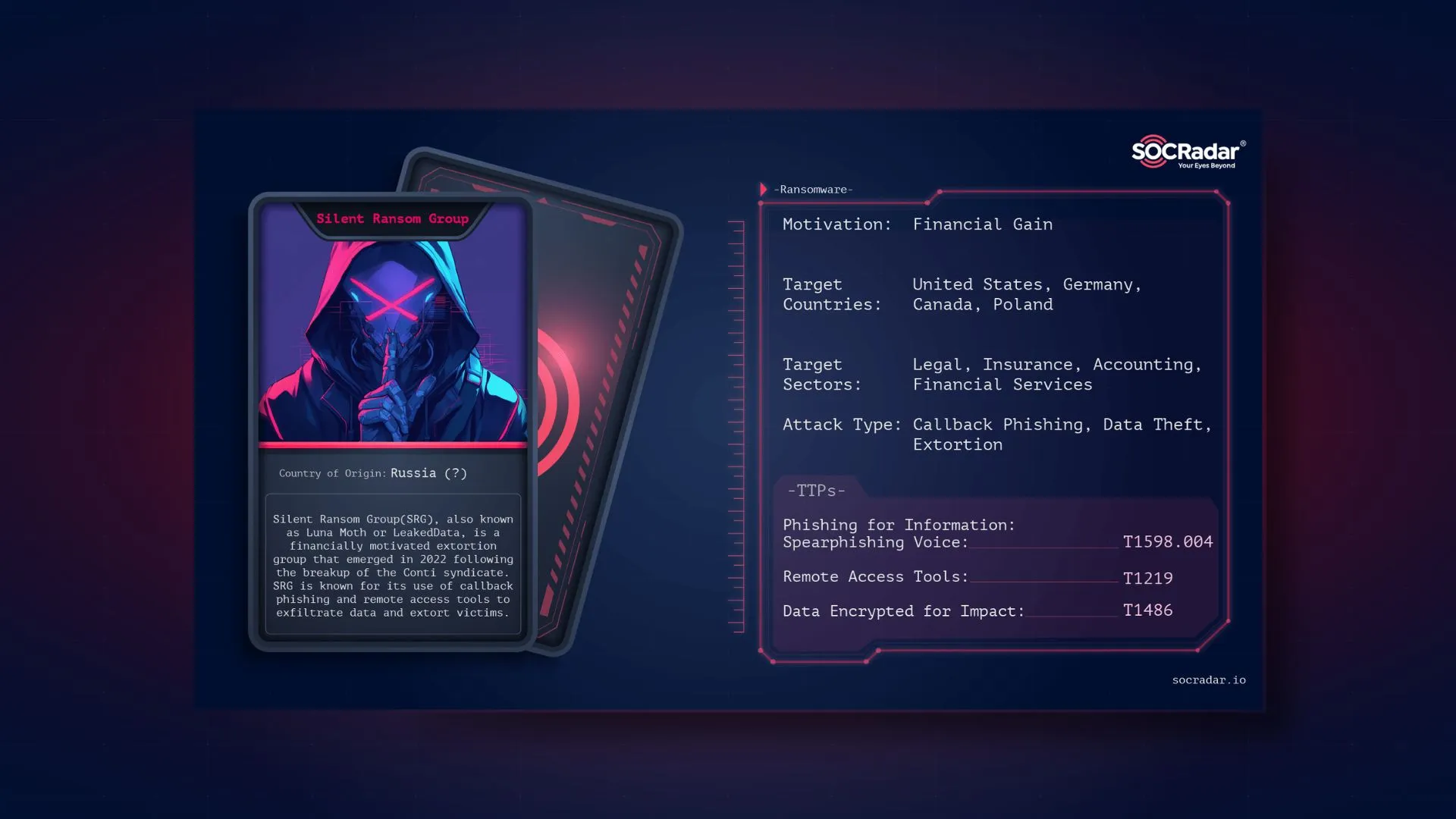
Data Tracking on the Dark Web: Leveraging Threat Intelligence for Insights
Today, when the world is increasingly moving towards digital operation, stolen data circulating on the Dark Web has been a nightmare for any organization. Data injected into the internet after a breach doesn’t just disappear; it often shows up on underground markets, where hackers are most actively trading it, selling it, or reusing it for malicious purposes. This increased exposure creates growing danger for individuals and companies for longer times since the very first event took place.

Illustration of the silent watchers of the unseen realm. Generated by DALL-E
It’s all about monitoring these buried networks to enable cybersecurity teams to identify the re-emergence of sensitive data and to take rapid, preventive measures. That is exactly where threat intelligence plays a very important role: giving views on where and how data is spread across the Dark Web, threat intelligence arms the security professional with an edge over potential risks, so it reduces the damage and strengthens the defense strategy for the organization.
Key Takeaways
- Cross-Platform Activity of Threat Actors: Cybercriminals maximize visibility for their stolen data by listing it across multiple hacker forums. This approach increases the likelihood of reaching a broader audience and finding a buyer. Continuous monitoring across various platforms is crucial for detecting threats early and responding effectively.
- Extended Risk Window for Affected Organizations: By selling the same data on multiple platforms, threat actors extend the risk window for affected organizations. High-value data may remain available for purchase over a prolonged period, necessitating ongoing vigilance from cybersecurity teams to mitigate recurring threats.
- High-Value Data Breaches and Economic Impact: Stolen data often carries high value, incentivizing threat actors to seek economic gain. Understanding what types of data fetch premium prices on the Dark Web allows organizations to prioritize and invest in the protection of their most critical information.
- Misattribution Risks and Evolving Threat Actor Identities: Changing aliases and shifting identities among threat actors can lead to misattributions, complicating response strategies. Effective threat intelligence requires consistent monitoring and validation across multiple platforms to accurately link incidents to the correct actors.
- Legacy Data Breaches and Persistent Threats: Old breaches continue to resurface on hacker forums, creating a persistent threat even years after the original incident. Monitoring legacy data breaches is essential to prevent cybercriminals from exploiting previously exposed information in new attack scenarios.
- The Need for Proactive Threat Intelligence Tools: Threat intelligence tools provide more than just data breach detection; they also monitor the movement and resale of compromised data. This proactive approach helps cybersecurity teams catch repeated data sales and movements, allowing for a timely response to emerging threats.
Reselling Strategy of Repeated Data for Maximum Profit on the Dark Web
Various threat actors in the underground markets strive to obtain maximum exposure and profits from data they sell by publishing the same offer on multiple hacker forums. This time, a threat actor using the alias CyberPhant0m announced on October 12, on the Russian-speaking hacker forum XSS forum, a breach in Verizon’s PTT service.
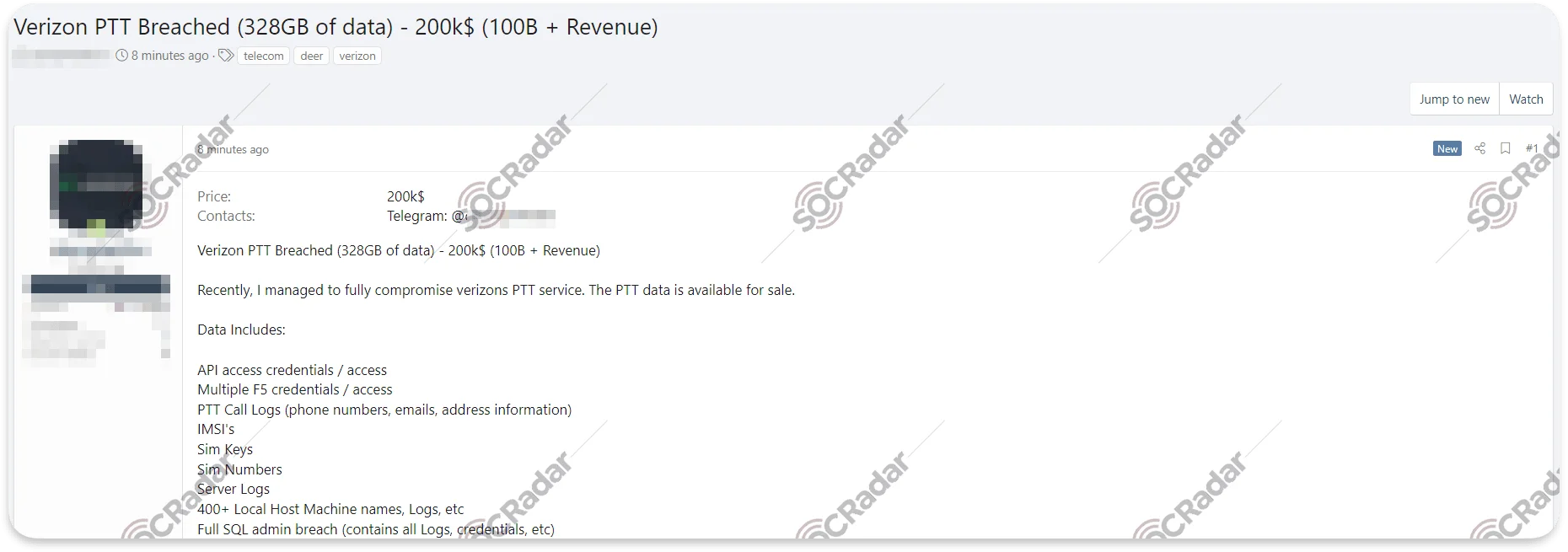
CyberPhant0m claims of having breached Verizon on XSS
Just two days later, a similar post appeared on BreachForums under the name kiberphant0m, offering the same data for sale. This is one possible way that threat actors expand their reach to a wider audience in hopes of finding a buyer.
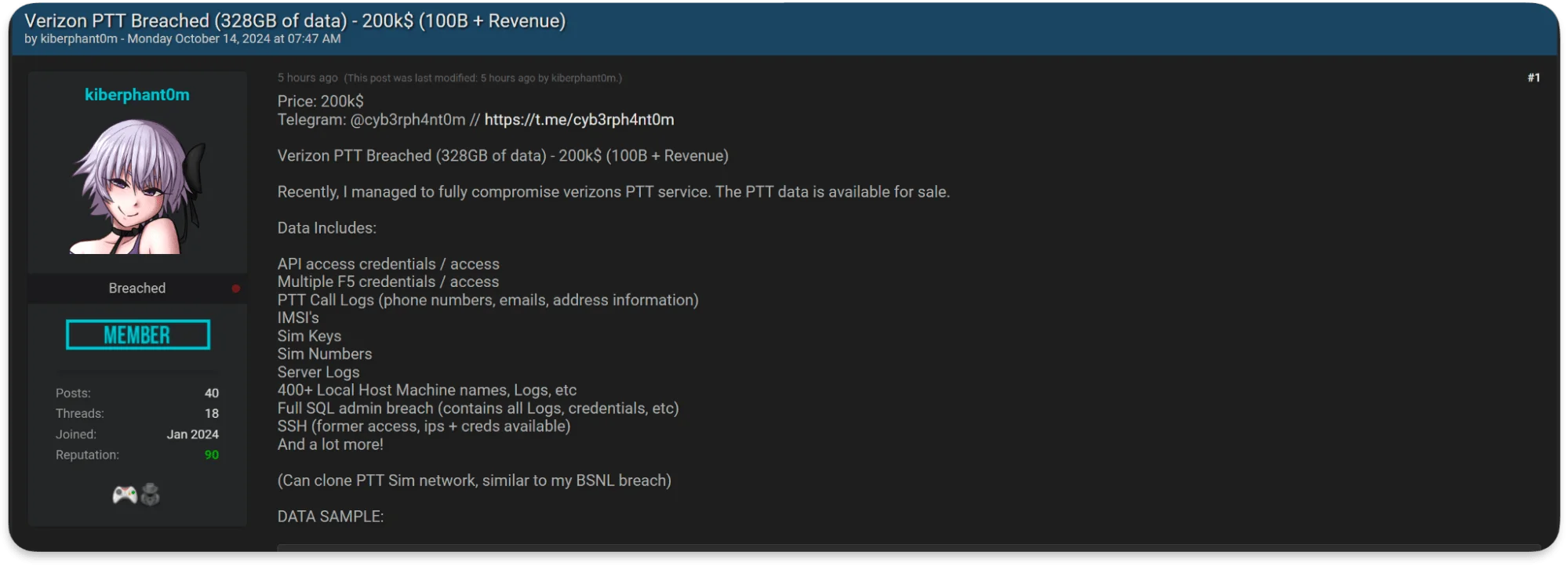
kiberphant0m’s claims to have breached Verizon on BreachForums
In the meantime, what that shows is the persistence of actors to use different platforms to market the same stolen data, extending the possible risk window for targeted organizations such as Verizon. This tactic indicates to cybersecurity teams the importance of continuous monitoring across a number of forums if timely detection and response to the threats are to be ensured.
This example gives several important points that can be related to cybersecurity and Dark Web monitoring:
Cross-Platform Activity: Many threat actors use different hacker forums to increase visibility for the sales of their data, making it important for cybersecurity teams to track a variety of underground platforms. A single listing may be overlooked, but tracking cross-platform activity may highlight consistent, possibly greater threats.
Longer Exposure Window: The cyber threat actor has reposted his sales offer of the same data in various forums. This means that the period of exposure of the compromised data is longer, thereby increasing the window of vulnerability for the impacted organization. This implies that even after the initial detection of the threat, it may continue to resurface several times thereafter, which may require vigilance.
High-Value Targets and Data: API access credentials, server logs, and full SQL admin access BDS that are on sale depict just how high-value the breach is and the damage that could result. Threat actors realize very well the value of such data, as reflected in the price tag of $200,000. Organizations will, therefore, know the data pattern that calls for attention across the Dark Web and apply their security measures accordingly.
The need for proactive threat intelligence: This case fuels how threat intelligence could be used to monitor and predict such activities, enabling security teams to take action much before the data is being distributed or in use. It infuses the fact that only identifying the initial breach is not enough but staying tuned to what transpires afterwards with the data.
Effective Dark Web Monitoring: Key to Accurate Attribution in Data Breaches
Accurately identifying the threat actors behind data breaches requires consistent and comprehensive Dark Web Monitoring. Without a thorough understanding of the underground activity across multiple forums, cybersecurity researchers risk misattributing incidents and overlooking critical details. This is particularly evident when multiple threat actors make similar claims, or when a high-profile group appears to take credit for an incident that originated elsewhere. A recent series of events surrounding breaches at Santander and Ticketmaster highlights the challenges of accurate attribution and the role that in-depth monitoring plays in understanding the true origins of a breach.
The investigations into the Snowflake-related breaches involving Santander and Ticketmaster proved that regular Dark Web monitoring is extremely important to correctly attribute the actors involved. On May 28, 2024, ShinyHunters, a known hacking group, posted on BreachForums, claiming to sell what they purported to be the Ticketmaster breach. Due to a lack of continuous monitoring, many researchers assumed the breach came from the ShinyHunters group and that said group directly targeted Ticketmaster.
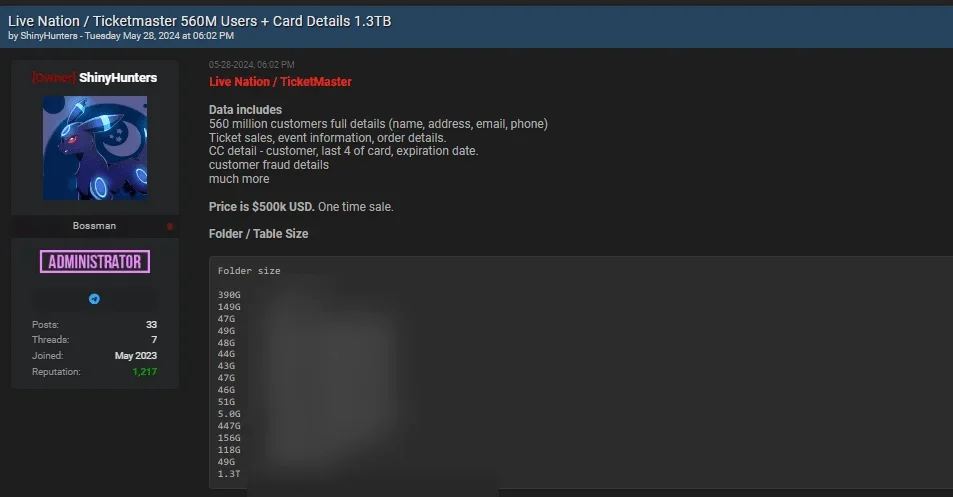
On May 28, 2024, threat actor ShinyHunters claimed a data breach of Ticketmaster in a post
However, all of this started earlier, on 24th May 2024, when a newly registered user by the name “whitewarlock” showed up on the Russian-language forum Exploit. On the same day, Whitewarlock claimed responsibility for a Santander Group breach. Since this user had zero reputation, his claim did not appeal to researchers or the community.
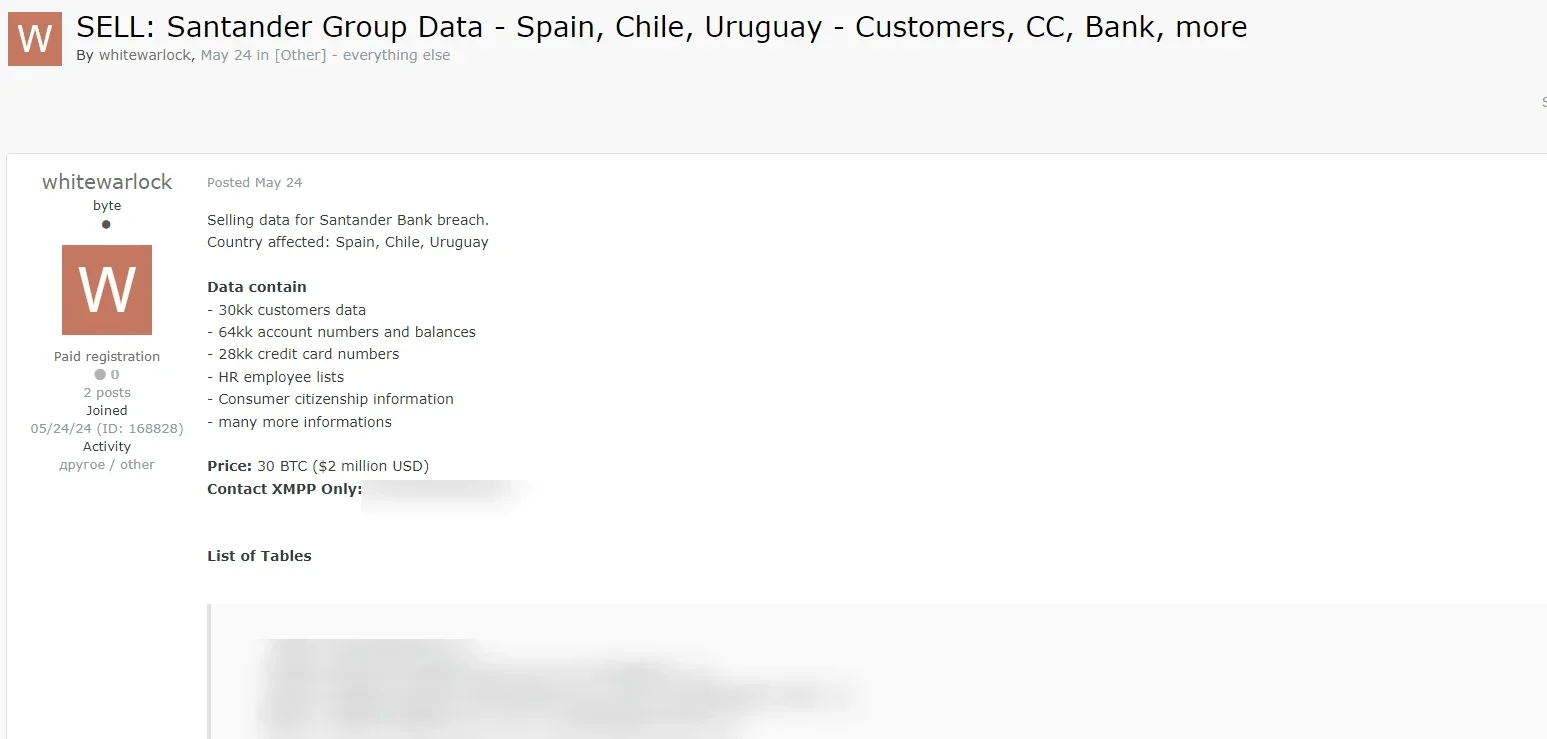
Threat Actor Whitewarlock Claims Santander Group Data Breach in a Post Dated May 24, 2024
Later, on May 27, another actor-this one operating under the handle “SpidermanData-“ created an account on Exploit. On that same day, SpidermanData posted that he had compromised Ticketmaster’s systems and was offering up data from 560 million user records for $500,000. That post, while major, saw little fanfare until ShinyHunters shortly posted a mirrored version of the Ticketmaster post to BreachForums.
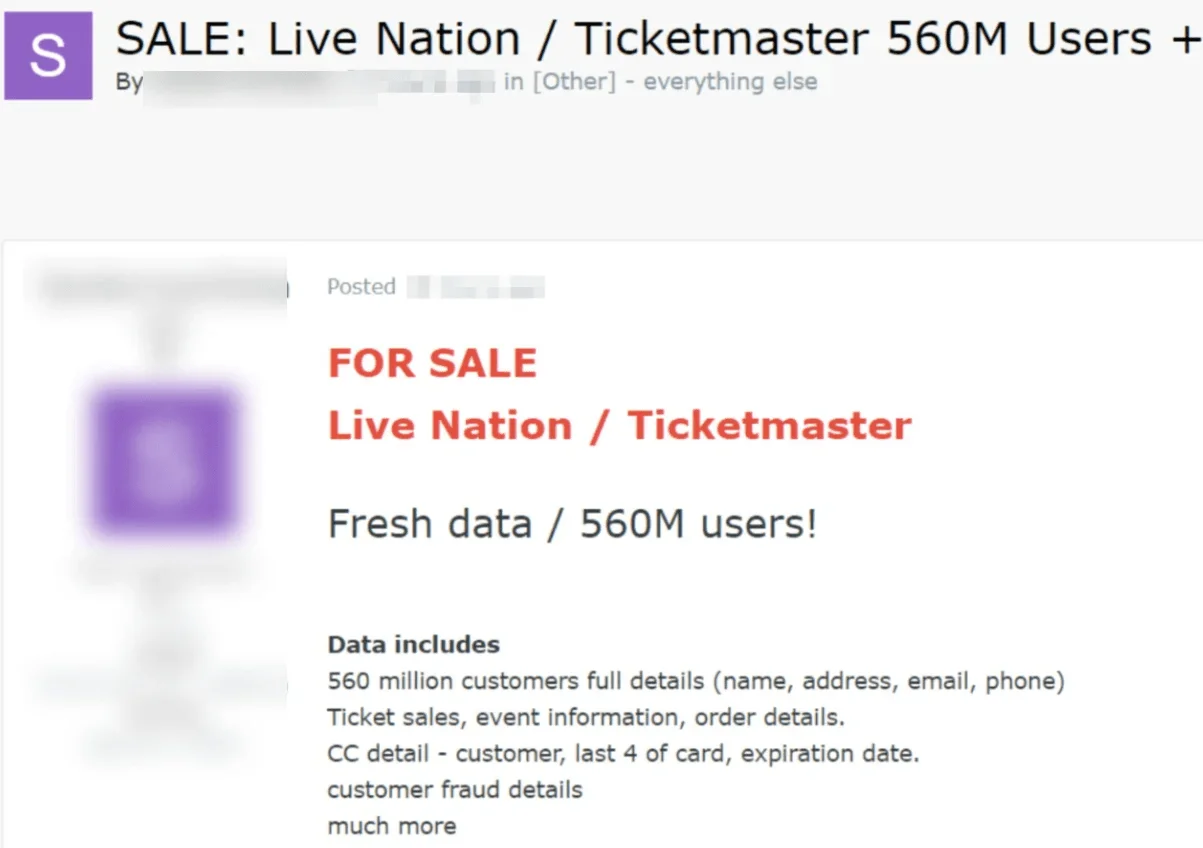
The threat actor known as SpidermanData claimed a data breach involving Ticketmaster in a post dated May 24, 2024.
Making matters even worse was June 1, 2024, in which SOCRadar researchers came upon a new post from BreachForums. The post, written by an actor known as “Sp1d3r,” whose alias apparently sounded like SpidermanData from Exploit, claimed the rogue actor got data in considerable amounts coming from QuoteWizard and LendingTree, hinting to a larger involvement of Snowflake into the breaches.
The plot thickened when Sp1d3r launched a rebranding into “Spid3rHunters,” continuing to make Snowflake-related claims. Then, an administrator of the ShinyHunters forum claimed this was controlled by ShinyHunters-an assertion that seems to imply a relationship between the actors and their activities connected with the Snowflake breach. This chain of events has shown that Dark Web monitoring can expose complex connections among threat actors and give a fuller view of the dynamics of a breach that otherwise might result in misattribution.
Skeptical Approach of the Aegis Threat Actor
This example highlights several critical insights for cybersecurity and Dark Web monitoring:
- Importance of Monitoring Multiple Forums: The initial attribution of the Ticketmaster breach to ShinyHunters shows the risks of relying on a single source of information, such as BreachForums. Monitoring a range of forums, including regional and less popular ones like Exploit, can provide a fuller picture of threat activity and prevent premature conclusions.
- Evolving Threat Actor Identities: The use of different aliases by the same threat actor—such as WhiteWarlock changing to SpidermanData and then changing to Sp1d3r and then Spid3rHunters—demonstrates how easily threat actors can obscure their identities. This makes accurate attribution challenging, emphasizing the need for constant tracking of changes in usernames and behavior patterns across platforms.
- Reputation’s Role in Threat Actor Visibility: The limited attention given to whitewarlock’s initial claim about the Santander breach illustrates how a threat actor’s reputation impacts the perceived credibility of their claims. Less-established actors can be overlooked, potentially delaying the recognition of serious breaches. This highlights the need for analysts to evaluate the content of claims alongside reputation.
- Misattribution Risks: The case shows how a lack of comprehensive monitoring led to the misattribution of the Ticketmaster breach to ShinyHunters, when other actors, like SpidermanData and whitewarlock, had made similar claims earlier. Misattributions can mislead response efforts, making it crucial to validate data through cross-referencing information from different sources.
- Collaboration and Rivalries Among Threat Actors: The connections between Spid3rHunters and ShinyHunters, as well as claims of collaboration or leadership changes, indicate that threat actors may work together or compete for credit. Understanding these dynamics can help predict potential alliances or rifts that might influence future activities and threats.
These insights emphasize the necessity of comprehensive Dark Web Monitoring, precise threat attribution, and the ability to adapt to evolving threat landscapes. Without these measures, organizations risk overlooking critical intelligence and misdirecting their response strategies.
From Exclusive Sale to Free Leak: Trello Data Breach Released Months After Initial Offer
On January 16, 2024, a threat actor named “emo” posted on a popular hacking forum, offering a database containing sensitive information from over 15 million Trello accounts for sale. The dataset included unique email addresses, usernames, full names, and other account details, all gathered through Trello’s unsecured API. This initial sale was presented as a unique opportunity for interested buyers to access Trello account information.
Six months later, on July 16, 2024, emo followed up by releasing the entire Trello dataset for free, with a detailed explanation of how the information was collected. Emo’s post described how the open API allowed anyone to link email addresses to Trello accounts without authentication. The database, he noted, could be particularly useful for doxxing activities, as it contained email addresses matched to users’ full names and aliases.
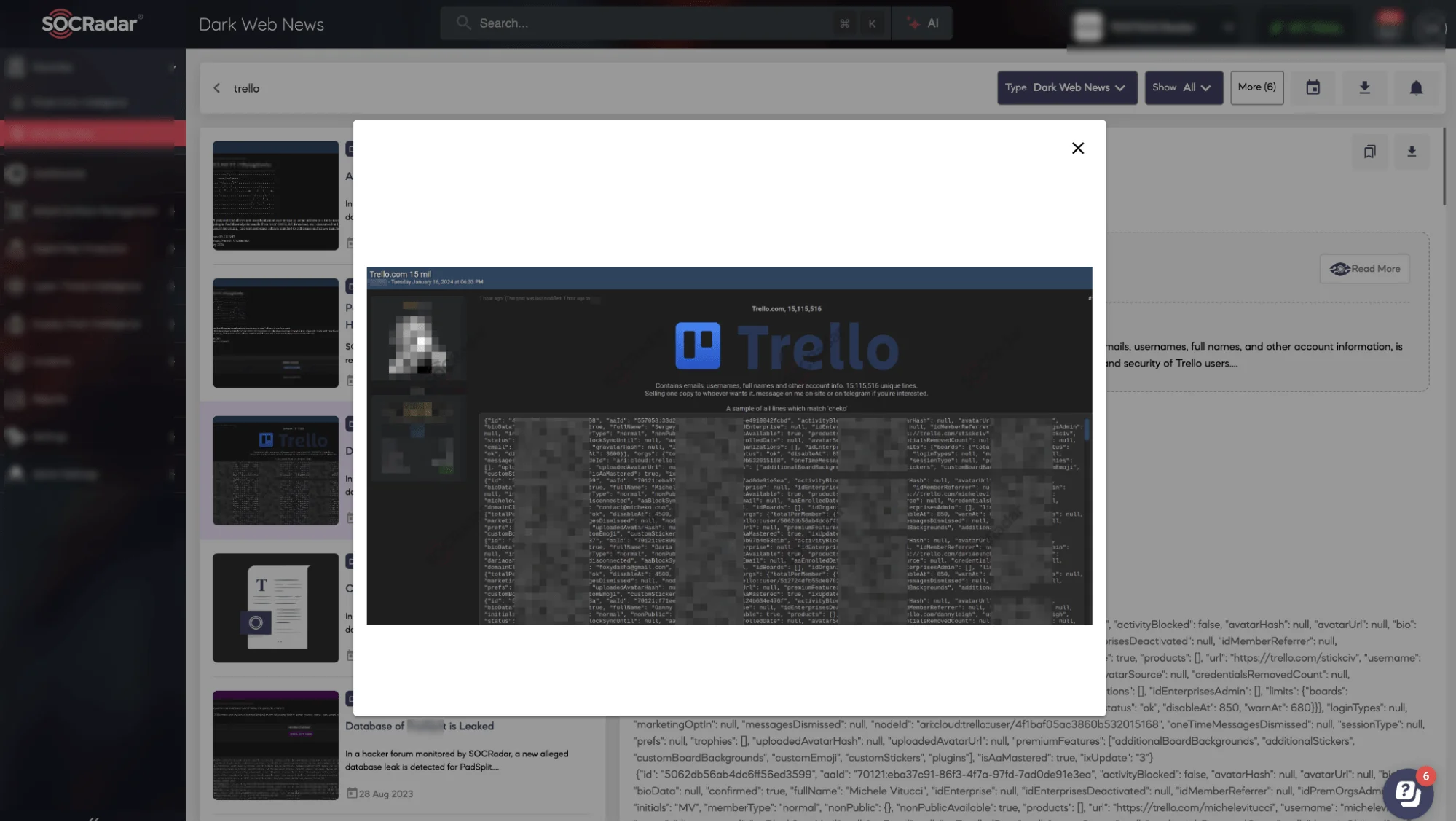
Emo’s January 16 post offering the Trello dataset for sale. (SOCRadar Dark Web News)
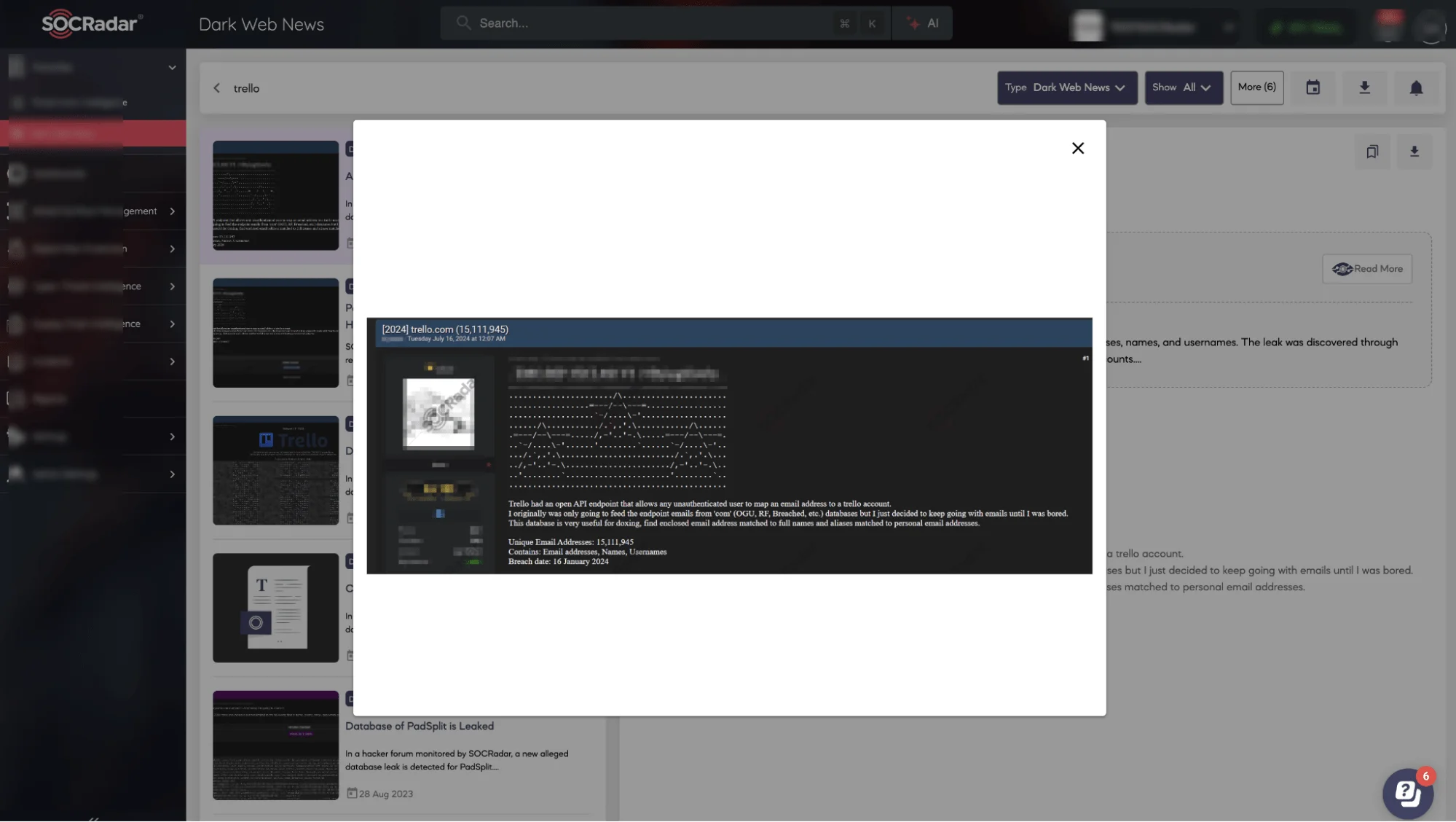
Emo’s July 16 post releasing the Trello dataset for free (SOCRadar Dark Web News)
How the Leak Happened: Exploiting Trello’s Open API
Emo accessed Trello’s API to input a large list of 500 million email addresses, querying the endpoint to check which emails were linked to Trello accounts. The API returned profiles for over 15 million users, which emo then combined into a comprehensive database of usernames, emails, and full names. Initially offered as an exclusive sale in January, the dataset was later made available for free in July, exposing Trello users to even broader risks.
Unsecured APIs have become a notable vulnerability for organizations, especially when they allow unauthenticated access to user information. As seen in this case and similar incidents involving Twitter and Twilio, unsecured APIs can lead to mass data leaks, compromising personal privacy and increasing risks like identity theft and doxxing.
Enhancing API Security with SOCRadar
Organizations can prevent such incidents by implementing stronger API security measures. SOCRadar provides essential solutions within External Attack Surface Management (EASM), Digital Risk Protection (DRPS), and Cyber Threat Intelligence (CTI), helping organizations to:
- Monitor for Sensitive Data Exposure: Detect leaked credentials or sensitive data on both public and underground platforms.
- Ensure Comprehensive Threat Monitoring: Monitor the clear, deep, and dark web for potential cyber threats, enabling early detection.
- Automate Incident Response: Respond quickly to incidents with automated processes, ensuring a robust approach to threat management.
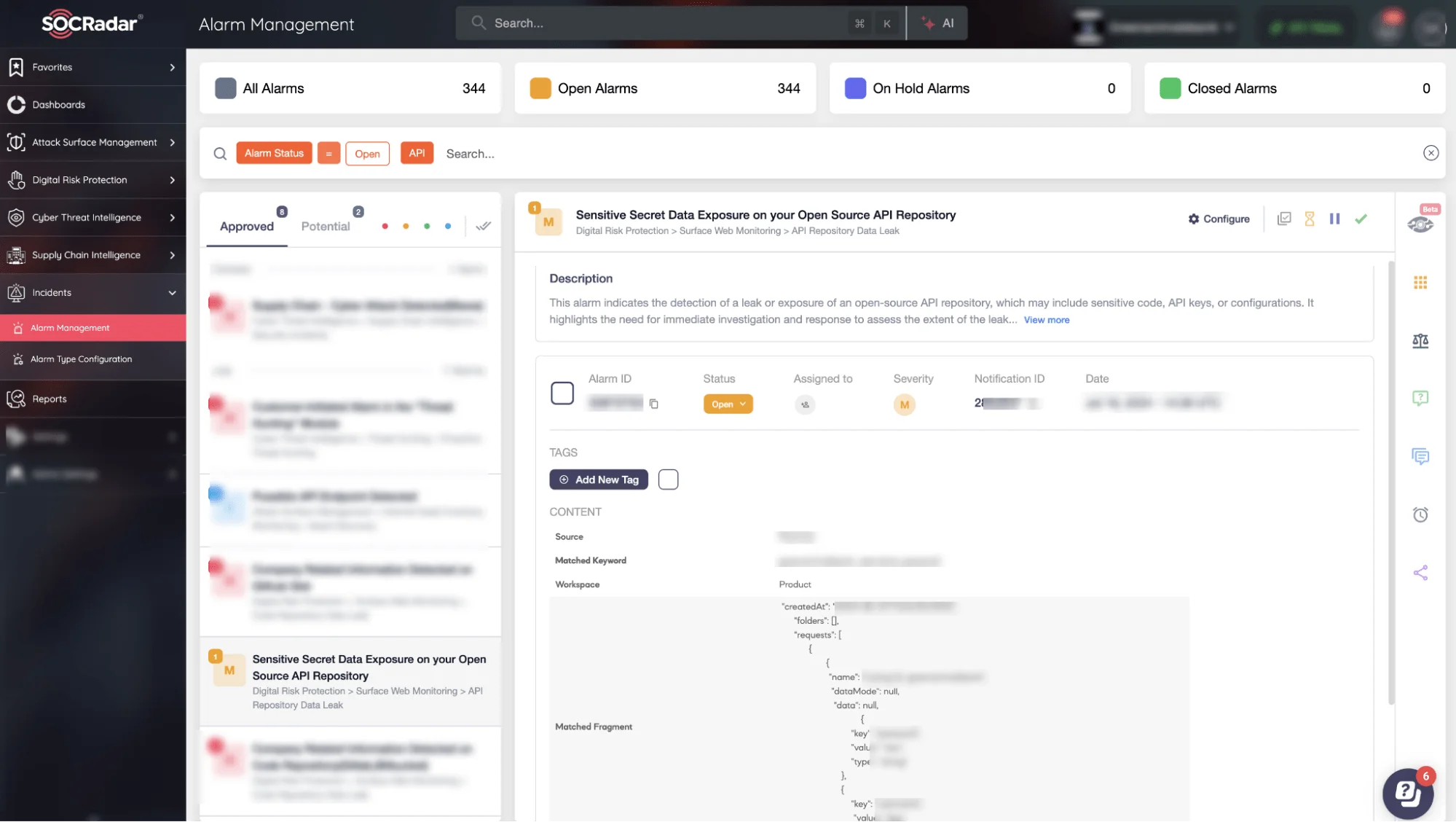
Exposure of Sensitive Secret Data on Public API Repository (SOCRadar Alarm)
Legacy Leaks Resurfacing: The Ongoing Risks of Past Data Breaches
Data breaches from past years, even from now-closed forums, continue to pose threats as they resurface across various underground platforms. One such example is a 2021 leak from a once-popular hacker forum, reintroduced by a threat actor in a recent post titled “FREE LEAK – 2021.” The data, reportedly sourced from a California insurance risk database acquired in September 2021, includes sensitive information like names, phone numbers, email addresses, and residential addresses. Although old, this data can still be valuable for cybercriminals, making it critical for cybersecurity teams to remain vigilant about historical breaches that may reappear unexpectedly.
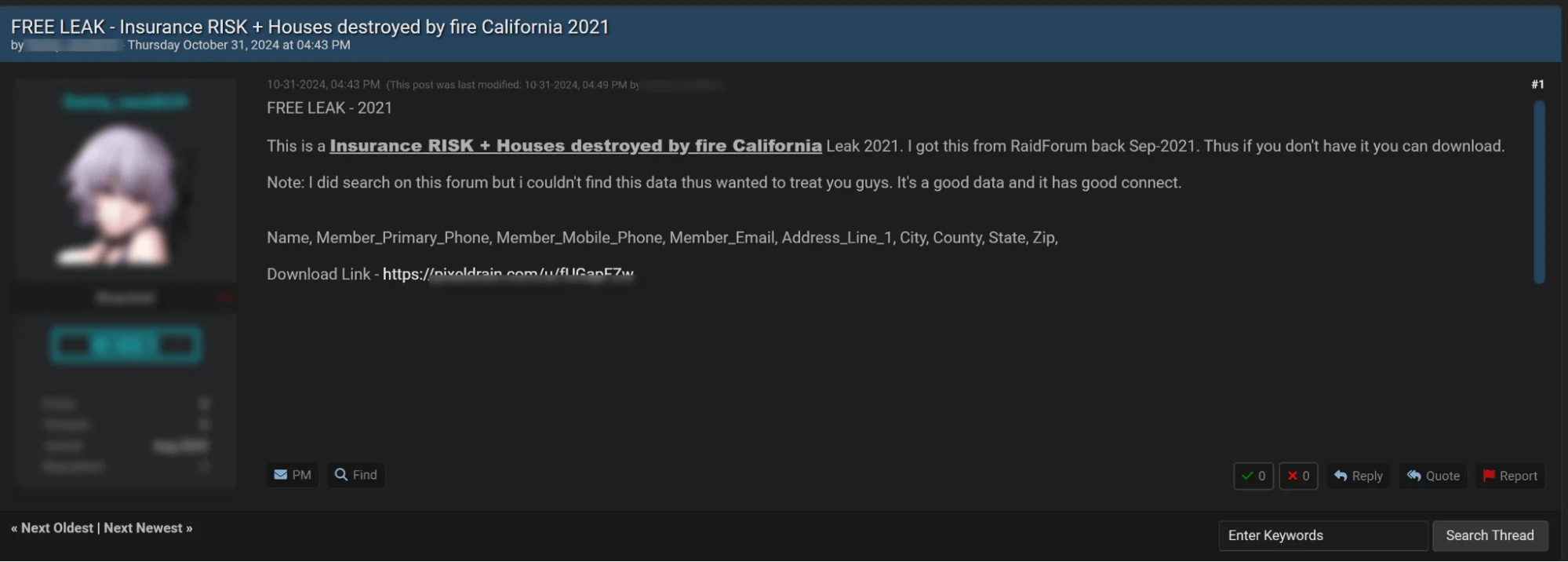
Threat actor’s post offering a free download of the 2021 California insurance leak data.
The ongoing availability and structured organization of breach data on hacker forums like BreachForums and LeakBase significantly heighten the risks posed by both recent and historical data leaks. These forums aggregate records from data breaches dating back to 2007, forming a massive, centralized repository accessible to cybercriminals. By archiving billions of records across numerous datasets, these hacker forums offer an invaluable resource for those seeking to exploit compromised information.
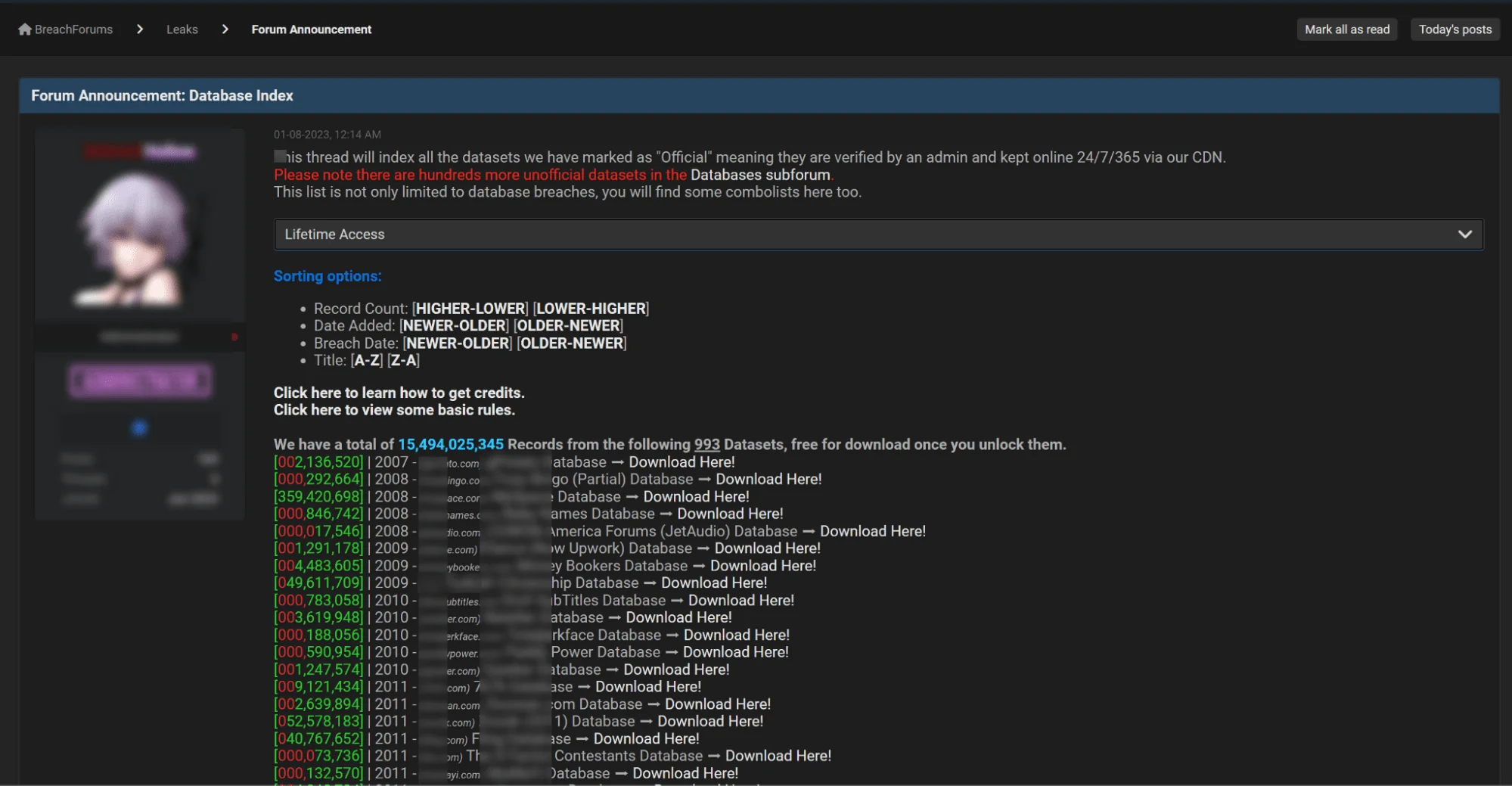
BreachForums’ database index
The nature of these collections allows threat actors easy access to sensitive information, often without significant barriers once the datasets are unlocked. The records include both verified, official breach data and unverified, unofficial collections, covering a broad spectrum of information types—such as emails, usernames, passwords, and personal details. This extensive data pool simplifies the process for cybercriminals to execute phishing campaigns, identity theft, and other malicious activities, even with older data that might otherwise seem irrelevant.
The structured cataloging of breach data also ensures that these records can resurface and be used repeatedly, posing a continuous security threat. Old breaches, which may have faded from public concern, remain highly exploitable in new contexts when revived on these forums. This persistent risk underscores the importance of continuous monitoring of hacker forums and implementing robust data protection strategies to defend against the sustained impact of both recent and historic data leaks.
Detecting Repeated Data Breaches with SOCRadar Threat Hunting
Identifying repeated data breaches is essential for understanding the persistence and distribution of sensitive information across the Dark Web. A recent example involves a threat actor claiming to have breached Griffin Capital’s database, allegedly containing 218,000 rows of data, including emails, names, phone numbers, IP addresses, and sales records. Following this claim, we used the SOCRadar Threat Hunting module to conduct an in-depth search across Dark Web sources.
Threat actor’s post listing Griffin Capital’s data from a previous leak.
SOCRadar XTI, an Extended Threat Intelligence platform, empowers users to track emerging threats by leveraging a vast repository of data gathered by skilled analysts and automated systems. Using word-based searches in the Threat Hunting module, the SOCRadar team was able to comb through extensive big data collections, including Indicators of Compromise (IoC), personal data exposures, and marketplace records.
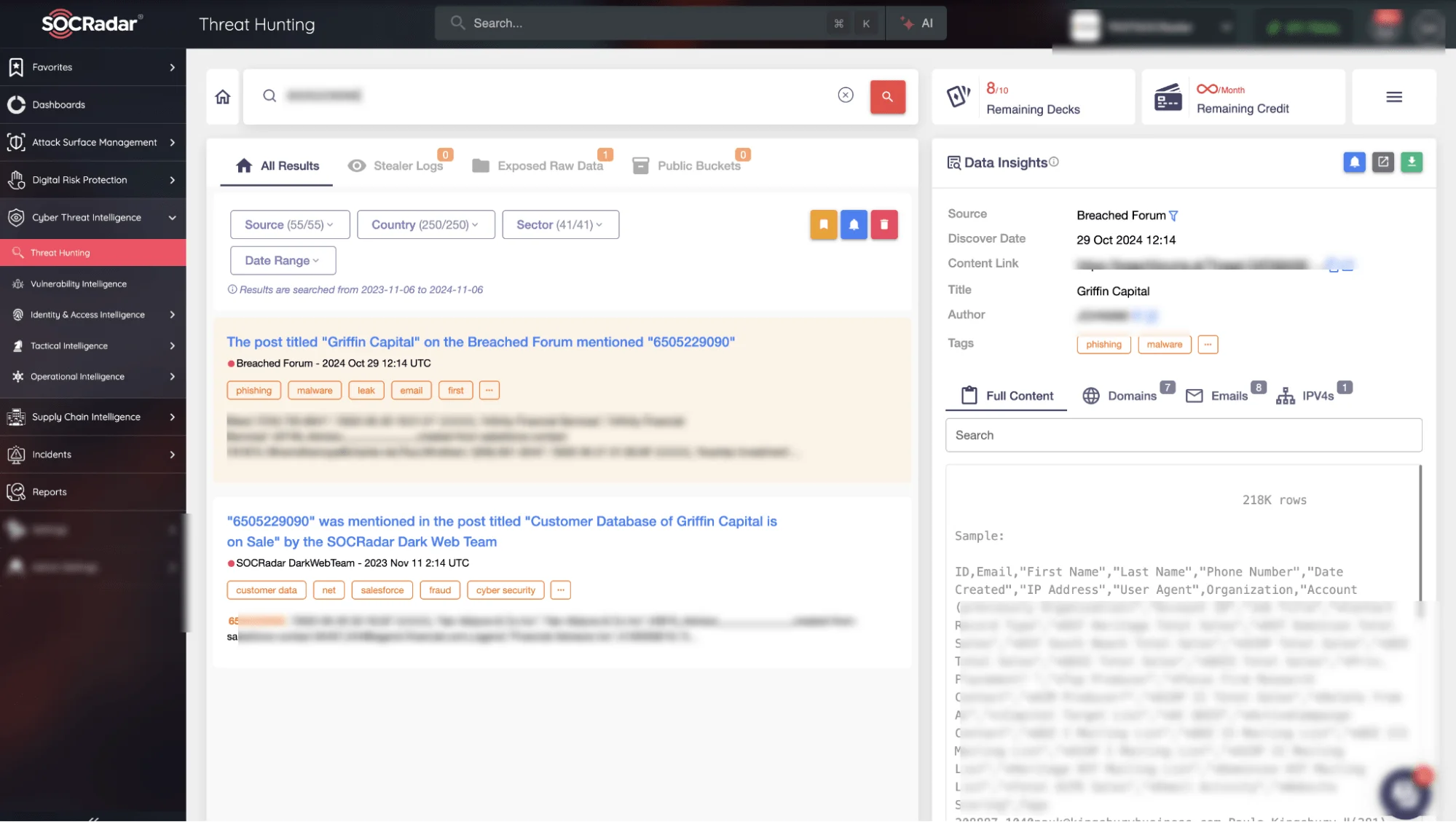
SOCRadar Threat Hunting module
The search revealed that this dataset had been previously posted on another hacker forum on November 11, 2023, a finding detected by the SOCRadar Dark Web team. This confirms that the claimed Griffin Capital data was not a new breach but a reappearance of previously leaked information.
In Summary
Monitoring data circulation by threat actors on the Dark Web is a vital part of cybersecurity strategy. Cross-platform activity, extended risk windows, evolving identities, and persistent legacy threats all underscore the importance of multi-layered and continuous monitoring. The examples discussed highlight the effectiveness of threat intelligence tools in identifying the recurrence and circulation of breached data. In conclusion, proactive threat intelligence helps organizations bolster their defenses, minimizing potential damage and maintaining a stronger security posture.