
Deep Web Profile: Karakurt Extortion Group
Karakurt has extorted sensitive data from nearly 40 different organizations within a year, a Russian-originated cybercriminal organization. So what is the cause of the group’s “success,” and who are they?
Karakurt: A Ransomware Gang or a Leak Group?
Karakurt is a recently emerged threat actor who is believed to have close connections with the pro-Russian ransomware group Conti. Karakurt prioritizes data exfiltration & extortion attacks over ransomware than their close relatives. In June 2021, the group claimed the domain Karakurt[.]group Karakurt[.]tech. Up to September 2021, there were no recorded attacks or updates from the group’s website.
Although the exact first attack date is not known, Karakurt has inevitably been attacking multiple victims since September 2021. It’s been seen that the payment addresses Karakurt sends to its victims are the same as some of the Conti’s. Furthermore, Karakurt mainly targets western organizations from different industries, just like Conti.
Karakurt can be described as a financially motivated cybercriminal group that targets especially western corporations regarding these victims’ variety and geological distribution.
Contrary to their common similarities with Conti, Karakurt does not encrypt data or take control of the victim’s system. Instead, they threaten the target corporation with the data stolen and demand a ransom is paid. This technique can be considered more effective than ransomware regarding the reduced amount of work due to not encrypting data and extra payment channels due to possible leak sales in the future.
Considering the recent intelligence, the Karakurt group started choosing their victims on dark web marketplaces by buying compromised credentials, initial access brokers, and email handles to perform spear-phishing to gain initial access. So, Karakurt usually chooses targets that other threat actors have already hacked. After the necessary privilege escalation, they extort sensitive data and demand ransom money from the organization.
Paying the ransom would not guarantee the safety of the stolen information since the data can be sold in the black market after the ransom anyway.
The headlines below show examples of data extortion by Karakurt.
A Data Breach Incident by Karakurt

In a data breacher group blog monitored by SOCRadar, a new alleged database sale is detected for an e-commerce company. In January 2022, Karakurt posted how and why the company was hacked. They pointed out that there were multiple vulnerabilities and the total incompetence of IT and Security departments and that basic passwords haven’t been changed for years.
As stated in the post, they took everything more or less valuable, like their whole intellectual property, GitHub repositories, user databases (including emails, names, addresses, and much more), and more than 80 million user entities. Also, they mentioned that if the company had continued to ignore the attack and the group itself, they would have started selling all the sensitive information they obtained on the dark web.
Another Mega Data Breach by Karakurt

In addition to the e-commerce company hack, in December 2021, victims of another data breach are allegedly announced to belong to various industries, such as construction equipment, design & attachments, technology & art, and advertising services. 1330 GB of data was leaked, including the clients’ database. Also, they threatened the victim companies about what they could do in case of a failed negotiation.
A Recent Data Breach
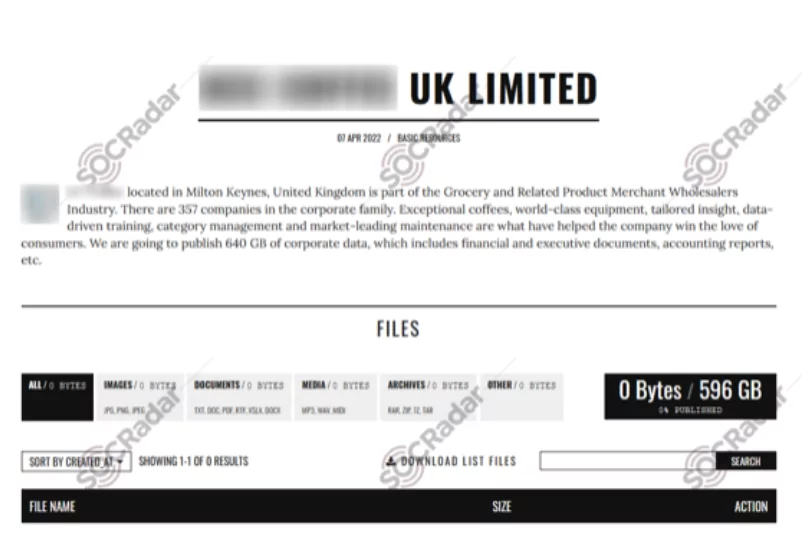
In April 2022, on the Karakurt data breacher group website, a new data breach victim from a British coffee industry was allegedly announced along with their whole corporate family. The website states that exceptional coffees, world-class equipment, tailored insight, data-driven training, category management, and market-leading maintenance are the company’s main critical points of interest. Karakurt would publish more or less 640 GB of corporate data, including financial and executive documents and accounting reports.
To sum up the information above, Karakurt has published data extorted on its website while exposing its victim. If the ransom is not paid within the deadline, the data is either published or sold to potential buyers on the dark web.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.

































