
Exmatter Tool Provides a New Strategy for Extortion
Data exfiltration malware Exmatter, previously associated with the BlackMatter ransomware gang, now has data corruption capabilities. This could signify a new strategy ransomware affiliates may use in the future.
Although BlackMatter affiliates have been using Exmatter since at least October 2021, this is the first time the malicious tool has been detected with a harmful module.

How Do Attackers Utilize Exmatter?
When the files are successfully copied to the actor-controlled server in the extortion phase, they are queued to be processed by an Eraser class.
To corrupt the first file, a randomly sized section at the beginning of the second file is read into a buffer and then written at the start of the first file.
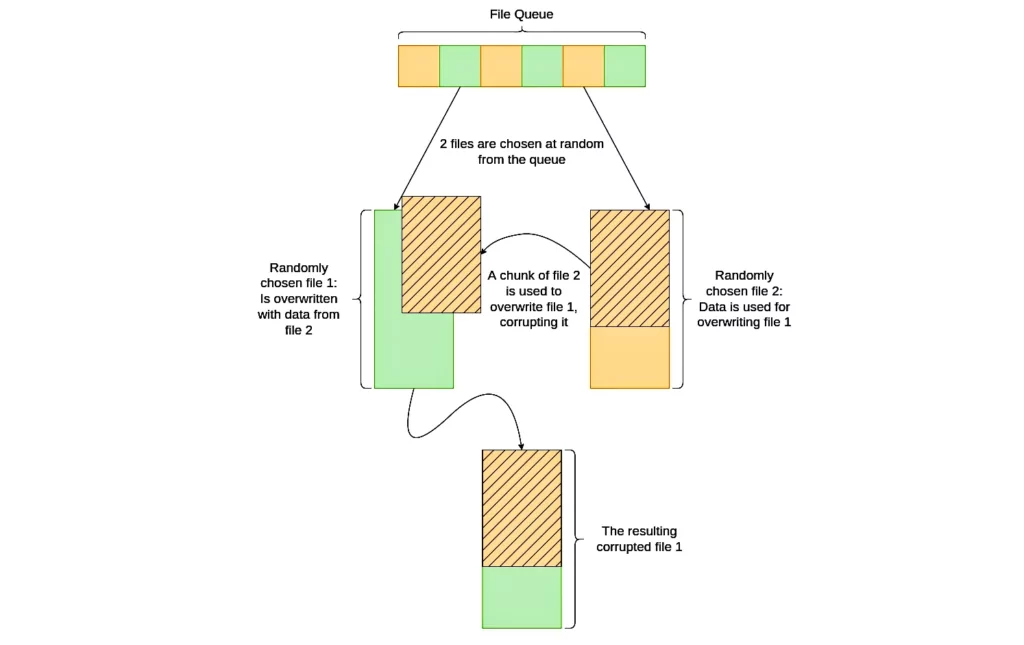
This method could be part of an attempt to avoid ransomware or wiper heuristic-based detection, which may be triggered when using randomly generated data.
The Tool is Still Under Development
Researchers found that Exmatter’s data destruction capabilities are probably still in development.
Due to the lack of a mechanism for clearing the corruption queue, some files may be repeatedly overwritten before the program ends, while others may never have been chosen.
The Erase function, which creates instances of the Eraser class, does not appear to be fully implemented and improperly decompiles.
The section length of the second file, which is used to replace the first file, is randomly chosen and might be as little as one byte long.
Ransomware Landscape Could Change
Most ransomware operations are run as RaaS (ransomware-as-a-service), and affiliates are required to give the developer of the encryption tool a specific percentage of their profit. This strategy establishes the independence of ransomware affiliates from developers because it does not require encryptors and allows affiliates to keep the developer’s share of profit. Additionally, it prevents losing revenue due to flaws that let victims utilize free decryptors.
Researchers believe this new data corruption feature is a significant improvement over previous ransomware attacks, and it is anticipated that many threat actors will switch to this strategy.

































