
Exploring the Most Common Passwords in Singapore: Trends, Implications, and Security Tips
Passwords are essential for protecting your online accounts, yet many people still use weak, easy-to-guess passwords. Our study on the most common passwords in Singapore reveals some surprising trends. Understanding these patterns can help highlight the importance of using strong, secure passwords. In this blog post, we will explore the top passwords used in Singapore, discuss their security implications, and provide tips for creating robust passwords to enhance your online safety. Dive in to learn how you can better protect your digital assets.
Singapore Password List
Password lists help us understand how people create and use passwords. These lists include common words, phrases, and combinations people use as passwords. Security experts use them to improve safety, while hackers use them to find weak passwords.
We analyzed the UK password list previously and now focus on Singapore. Our research examines Singapore’s top 250 passwords from the dataset srwordlist_sg_250.txt. This list shows how often each password is used. By studying these patterns, we can identify weak passwords and learn how to create stronger ones.
Exploring the Singapore Password List
The list we compiled for Singapore is organized by how often each password is used. The most frequently used password, ‘123456’, appeared 12,392 times, while ‘qwerty’ showed up 860 times. Here’s a look at the top 10:
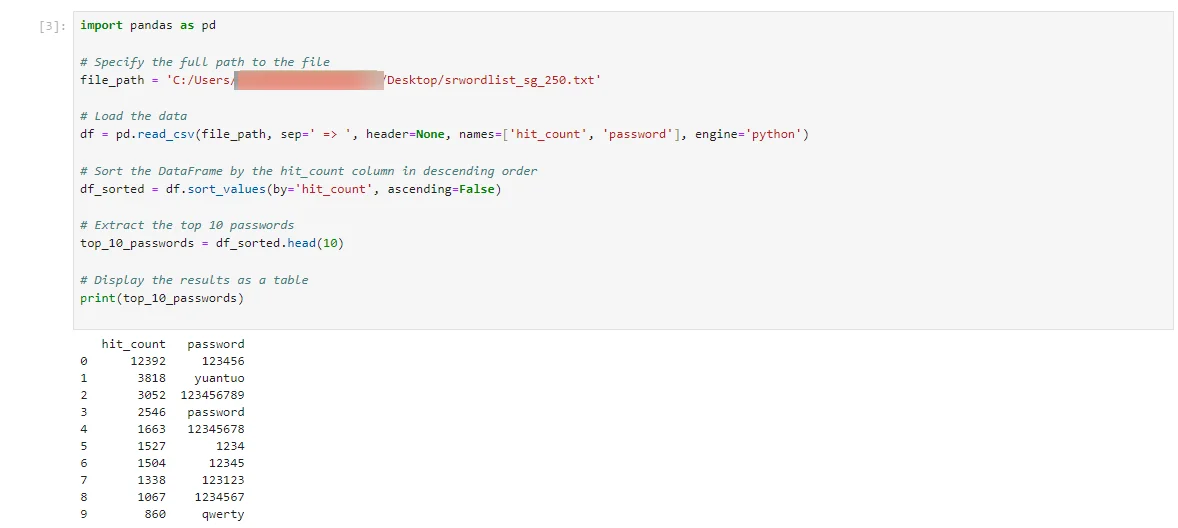
Top 10 passwords from the list
- 123456 is popular globally, including in the US, UK, and Singapore.
- Singapore-specific passwords like yuantuo are unique to the region.
- Common passwords like password, 123456789, and 12345678 are also widely used in Singapore.
- Short, easy-to-remember passwords like 1234, 12345, and 123123 are more common in Singapore.
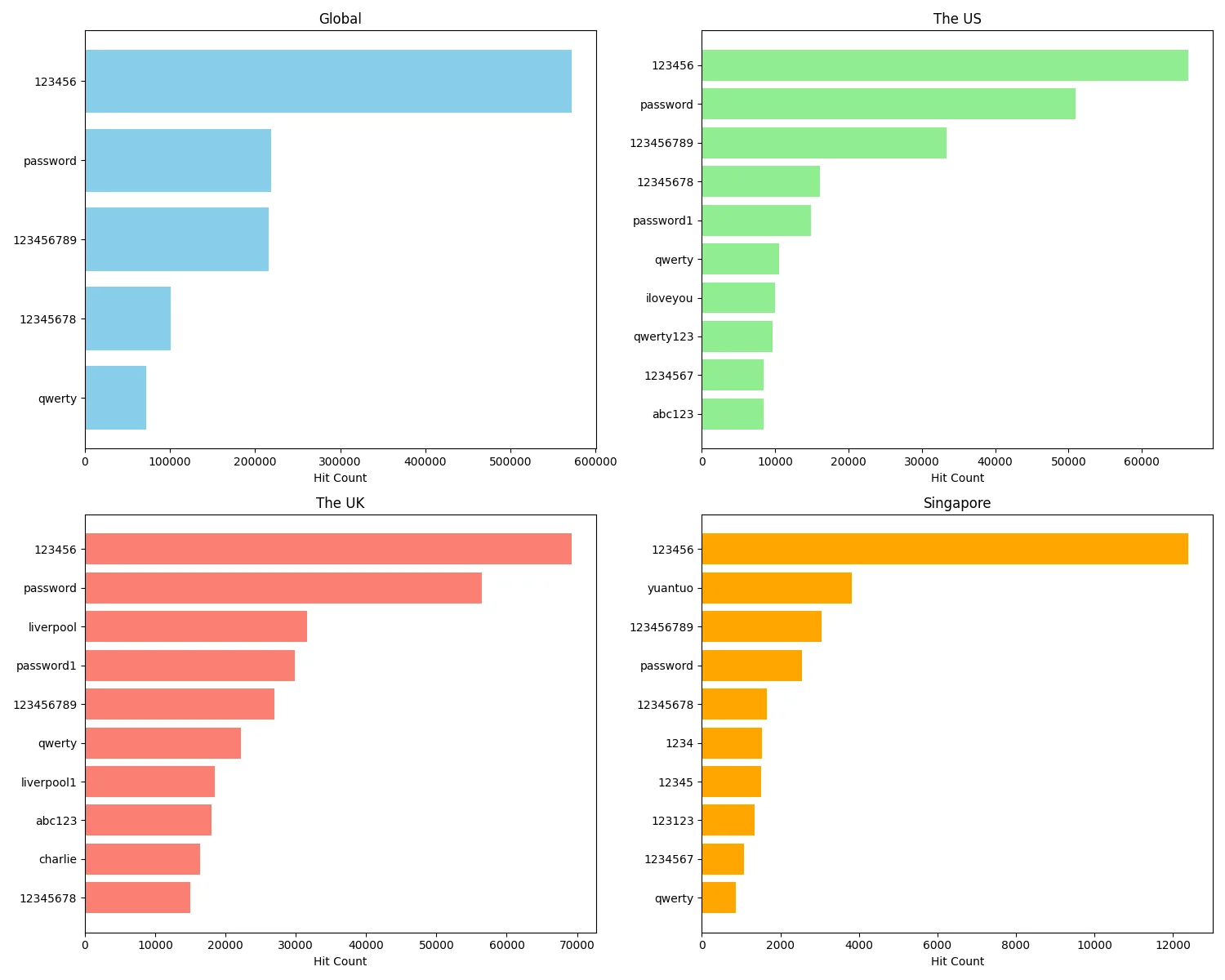
Global, UK, US, and Singapore password trends
The presence of a unique password like “yuantuo” highlights regional influences in password choices, which is less common in other regions. This suggests that cultural factors can play a significant role in password creation. Despite global awareness campaigns about strong passwords, many users still opt for simple, easy-to-remember passwords. This trend underscores the ongoing need for robust password education and the implementation of stronger security measures, such as multi-factor authentication, to protect against cyber threats.
NIST Guidelines
The National Institute of Standards and Technology (NIST) outlines specific guidelines to ensure robust password creation. These guidelines typically suggest the following for strong passwords:
- The password should be at least 8 characters long (though longer is always better).
- It should include a mixture of letters and numbers.
- Both uppercase and lowercase letters should be used.
- Special characters should be incorporated to increase complexity.
To assess the strength of passwords in our Singapore list, we assigned scores based on these guidelines. Each password received one point for meeting a guideline. If a password was shorter than 8 characters, it received a score of zero regardless of other criteria.
We used the following Python code in a Jupyter Notebook to calculate these scores and derive new attributes from our dataset:
# A function to calculate the score and parameters for each password
def calculate_score_and_parameters(password):
score = 0
uppercase = 0
lowercase = 0
numbers = 0
symbols = 0
# If password has less than 8 characters, return 0 for all parameters
if len(password) < 8:
return pd.Series({‘score’: 0, ‘uppercase’: 0, ‘lowercase’: 0, ‘numbers’: 0, ‘symbols’: 0})
# Check if password contains uppercase letters, lowercase letters, numbers, and symbols
if any(char.isupper() for char in password):
score += 1
uppercase = 1
if any(char.islower() for char in password):
score += 1
lowercase = 1
if any(char.isdigit() for char in password):
score += 1
numbers = 1
if any(not char.isalnum() for char in password):
score += 1
symbols = 1
return pd.Series({‘score’: score, ‘uppercase’: uppercase, ‘lowercase’: lowercase, ‘numbers’: numbers, ‘symbols’: symbols})
# Calculate the score and parameters for each password
new_columns = df[‘password’].apply(calculate_score_and_parameters)
df = pd.concat([df, new_columns], axis=1)
display(df)
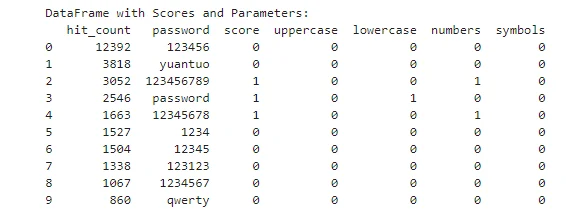
List of passwords based on the set parameters
Our analysis revealed that many passwords in the Singapore list are shorter than 8 characters, resulting in a lower average score. The average score of all passwords was 0.45. When excluding passwords shorter than 8 characters, the average score improved to 1.43 out of 4.
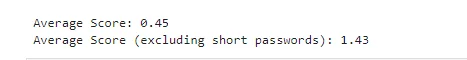
The average scores of the passwords
Singapore’s average password strength is slightly weaker than that of other regions. The US had an average score of 1.5, while the UK had a score of 1.71 out of 4. This suggests that there is room for improvement in password practices in Singapore.
Password Parameters Score Distribution
From our analysis, we found that 70% of the passwords in the Singapore list scored zero, indicating that they did not meet any of the strength parameters. Conversely, only a small percentage managed to satisfy some of the parameters.
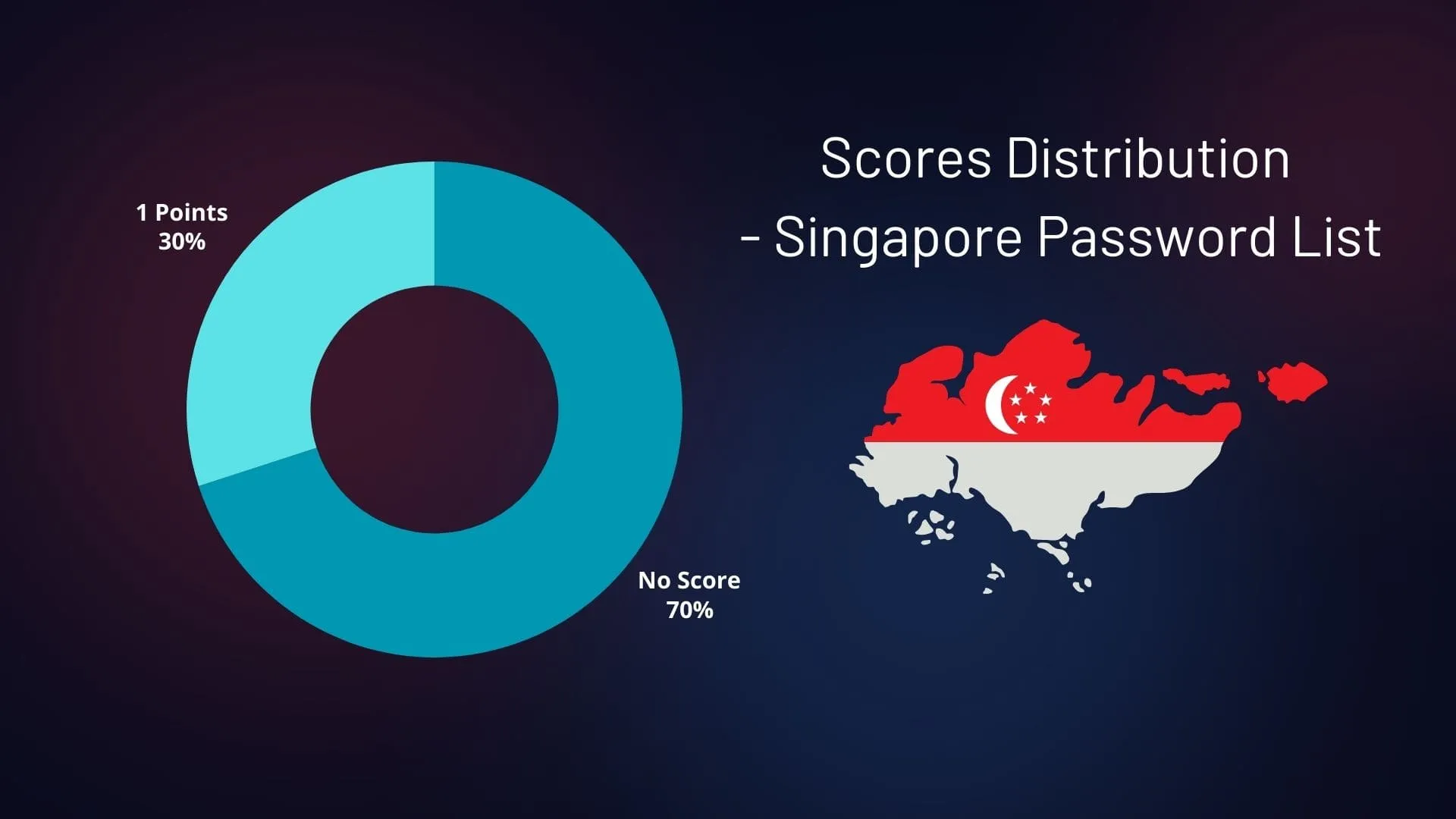
Distribution of the Scores – Singapore Password List
When we break down the parameters, we find that none of the passwords included uppercase letters, lowercase letters, or symbols. Only a few passwords, about 30%, incorporated numbers.
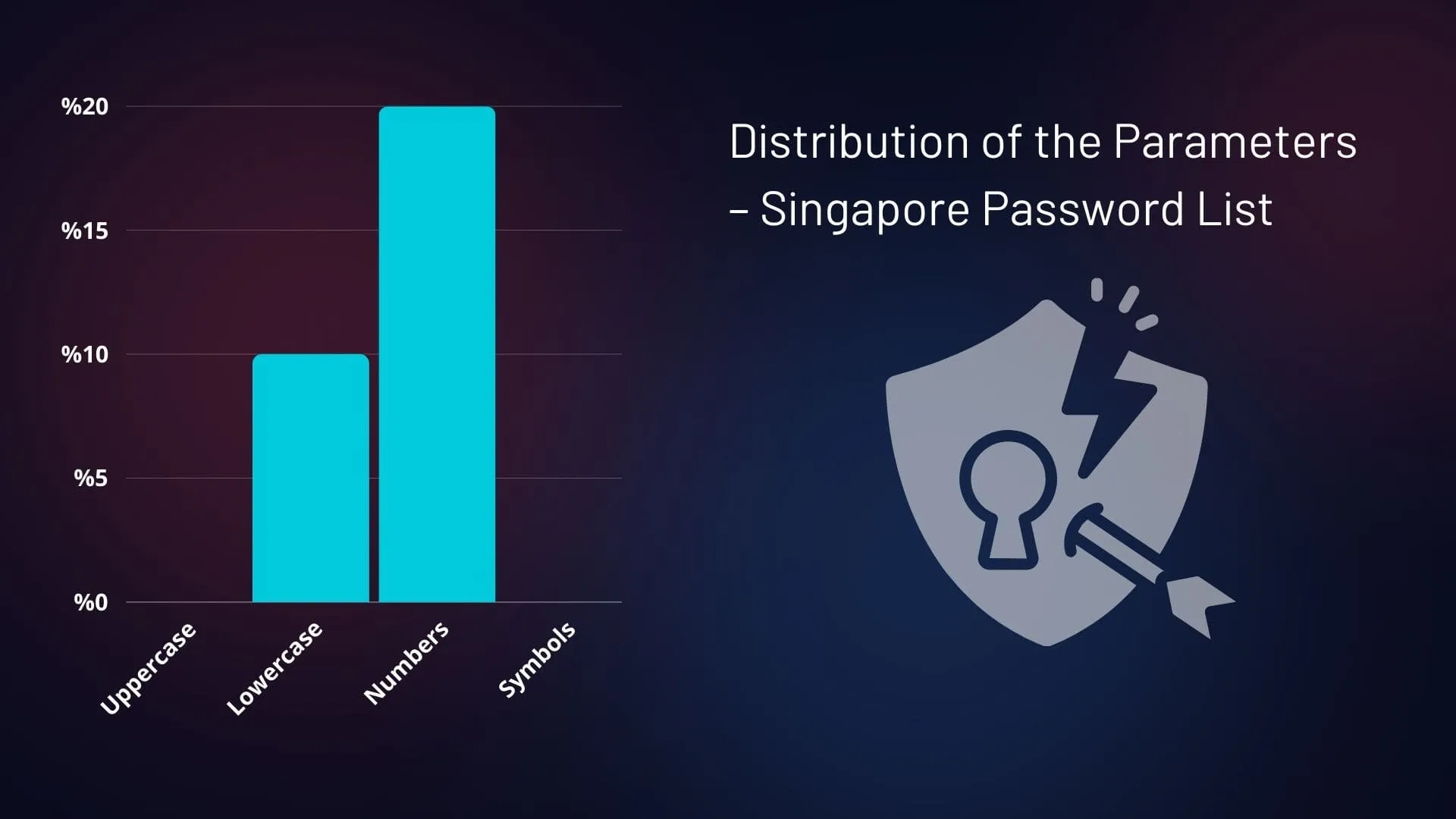
Distribution of the Parameters – Singapore Password List
These findings highlight a significant need for improved password practices in Singapore.
When breaking down the parameters, the statistics are even more telling. None of the passwords included uppercase letters, lowercase letters, or symbols. Only a small portion of the passwords, around 20%, included numbers, indicating minimal complexity.
Password Length Distribution Analysis
import matplotlib.pyplot as plt
# Calculate the length of each password
df[‘password_length’] = df[‘password’].apply(len)
# Specify the groups for password lengths
groups = [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14]
# Group passwords based on their length
passwords_grouped = df.groupby(pd.cut(df[‘password_length’], bins=groups, right=False)).size()
# Plot the distribution of password lengths
plt.bar(range(len(passwords_grouped)), passwords_grouped, align=’center’, tick_label=[f'{i}’ for i in groups[:-1]])
plt.xlabel(‘Password Length’)
plt.ylabel(‘Frequency’)
plt.title(‘Distribution of Password Lengths’)
plt.show()
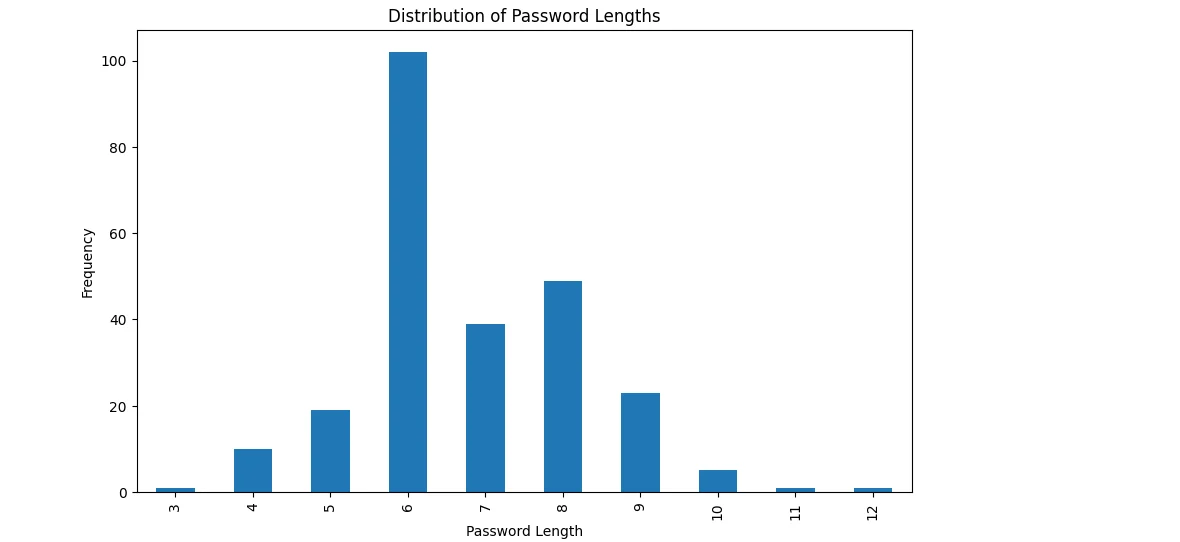
Passwords Lengths Distribution
The bar chart shows that the most common password length is 6 characters, with over 100 occurrences. Passwords of 7 and 8 characters also appear frequently, while very short (3-5 characters) and longer (10-12 characters) passwords are rare. This suggests a preference for shorter passwords, which can be less secure.
Understanding password length distribution helps organizations spot trends, like the common use of short, guessable passwords. This knowledge enables proactive enforcement of robust password policies.
Conclusion
After examining the Singapore password list, it’s clear that many passwords used to protect sensitive information, such as emails, are dangerously weak. While this data doesn’t represent all password usage in Singapore, it provides a troubling snapshot of passwords exposed in breaches.
Weak passwords remain a significant threat. It’s crucial to remember that even the strongest passwords can be compromised if not properly managed, particularly through the threat of stealer logs.
The analysis revealed that many commonly used passwords lack the necessary complexity to withstand even basic attacks. Passwords such as “123456” or “password” are still prevalent, highlighting a significant gap in user awareness regarding secure password practices. Cultural factors can sometimes lead to passwords that seem unique but are still easily guessable due to their simplicity and lack of variation.
In our parameter scoring system, “yuantuo” scored zero points. It did not contain uppercase letters, numbers, or symbols and it was shorter than 8 characters. This lack of complexity makes it easier to crack despite its perceived strength.
Choosing secure, unique passwords and enabling two-factor authentication are essential steps for maintaining good password hygiene. Additionally, platform security and vigilance against stealer logs are crucial.
SOCRadar Account Breach Check
SOCRadar’s Account Breach Check service effectively addresses the risks we’ve identified. This service helps you determine whether your personal or professional email accounts have been compromised in a data breach. It’s an invaluable tool for staying ahead of potential threats and ensuring your data remains secure against cybercriminals.
SOCRadar Threat Hunting Module
Moreover, SOCRadar’s Threat Hunting module offers advanced capabilities to detect and neutralize threats before they cause harm. This tool sifts through extensive volumes of data, including stealer logs, to identify compromised credentials and other sensitive information. By proactively addressing these threats, organizations can significantly enhance their security posture.



































